Document authentication method based on interweaving watermark and biological characteristic
A biometric, authentication method technology, applied in the usage of multiple keys/algorithms, electrical components, digital transmission systems, etc., to achieve the effect of preventing denial behavior, accurate and complete
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
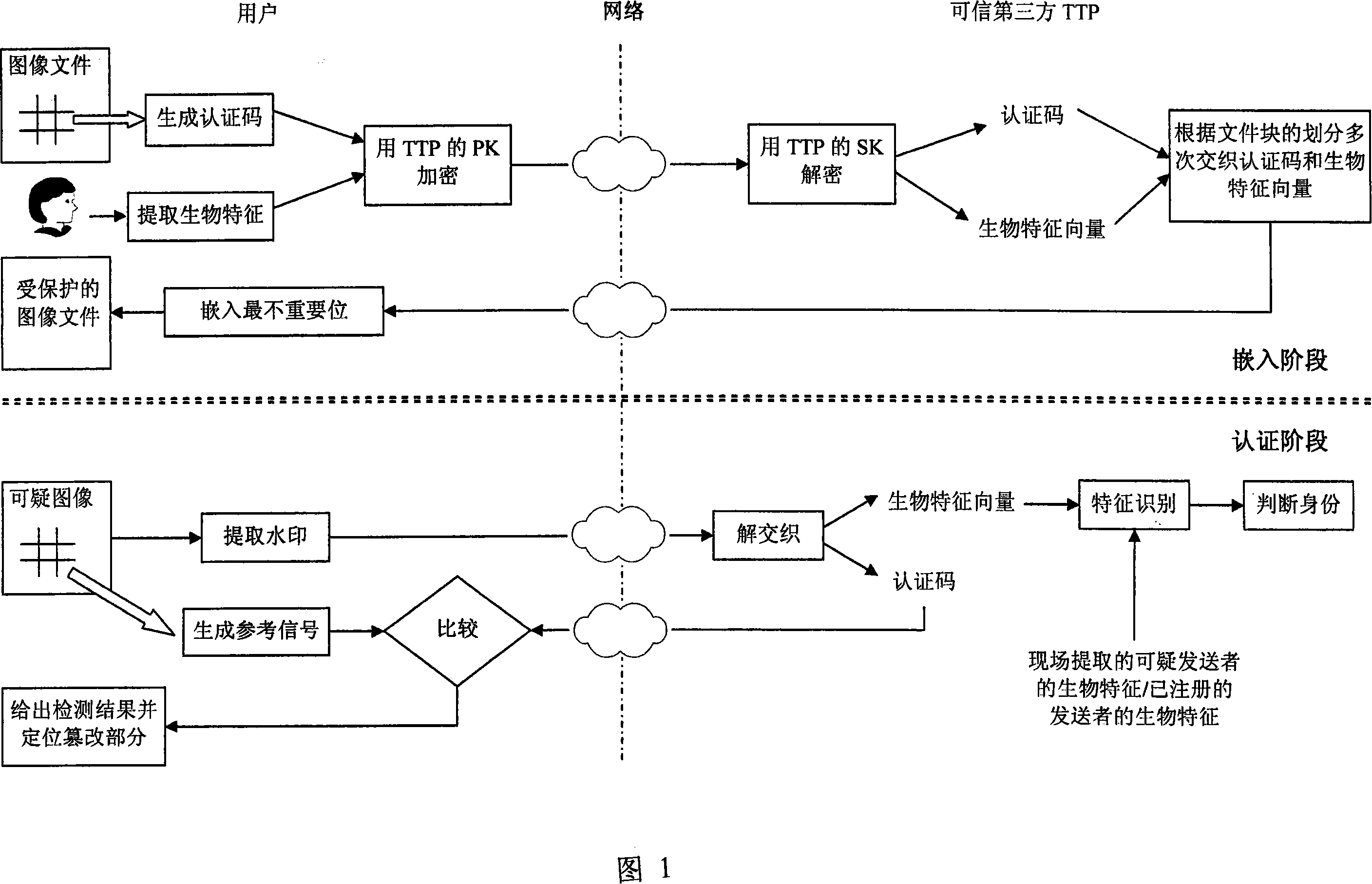
[0045] FIG. 1 will take an image file as an example to explain the present invention in detail. The watermark embedding stage mainly includes the following four steps:
[0046] Step 1: Segmentation of image files
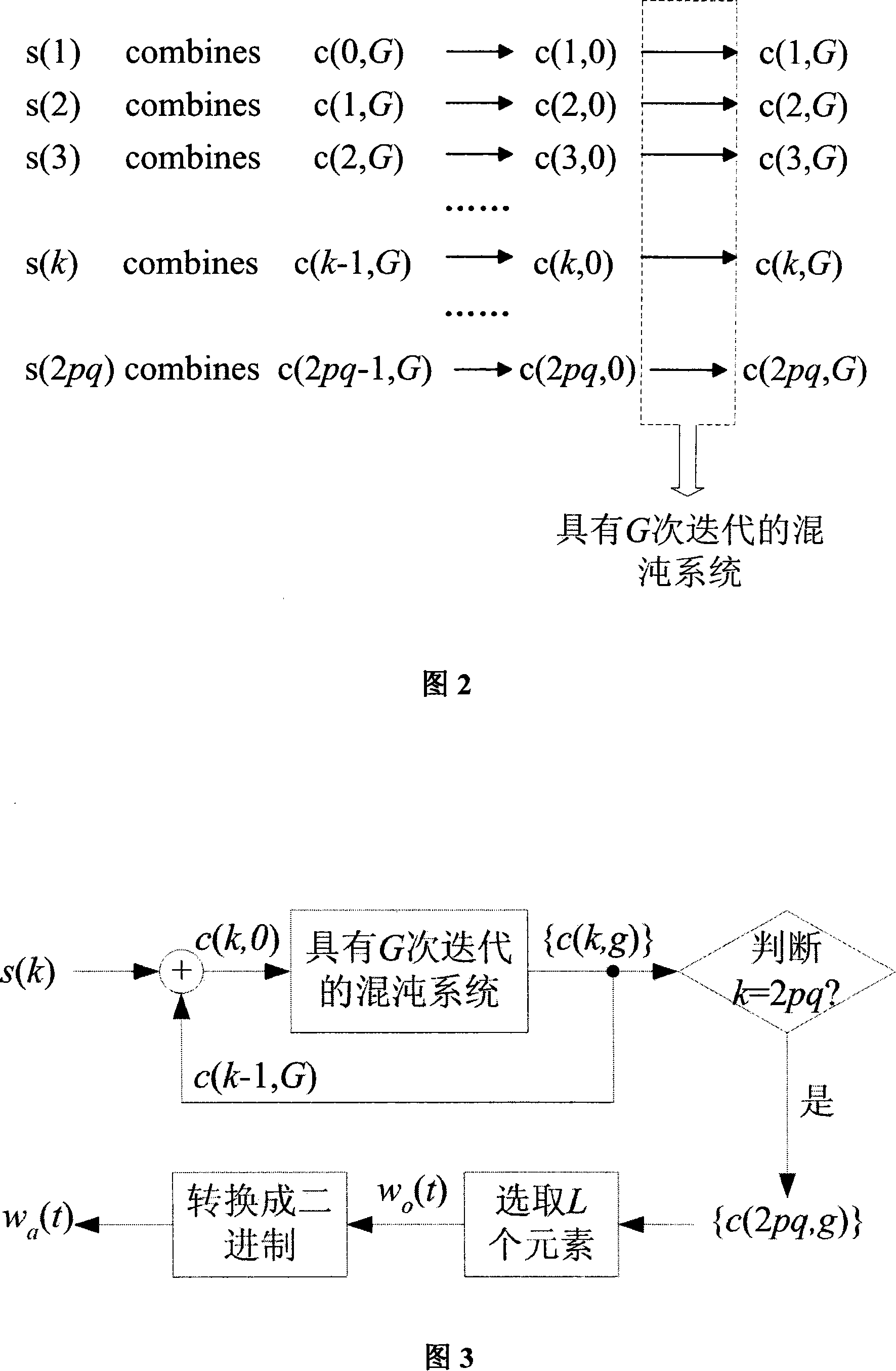
[0047] For an image I of size M×N, it is first divided into non-overlapping image blocks of size p×q. Therefore, the image contains M / p×N / q image blocks, and can be expressed by formula (2),
[0048] I={I x,y (t), 1≤x≤ M / p , 1≤y≤ N / p , 1≤t≤pq} (2)
[0049] Among them, x, y represent the position of the image block in the whole image, and t is used to mark a pixel in the image block.
[0050] Step 2: Construction of authentication code
[0051] In each image block, the authentication code is mainly obtained through some operation of the pixel values of the current image block and its right adjacent block. The constructi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com