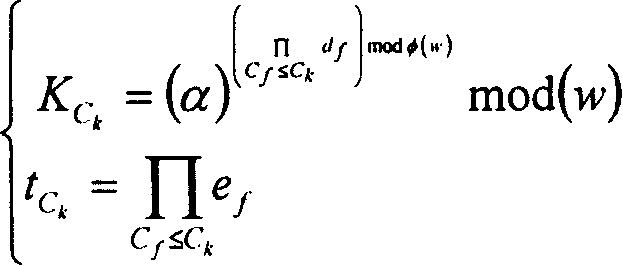A L4 encryption method of double group of encrypted authorization management system
A technology of authorization management and encryption method, which is applied in key distribution, can solve the problem of serious communication burden, achieve the effect of reducing communication burden and communication overhead, reducing the amount of information, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
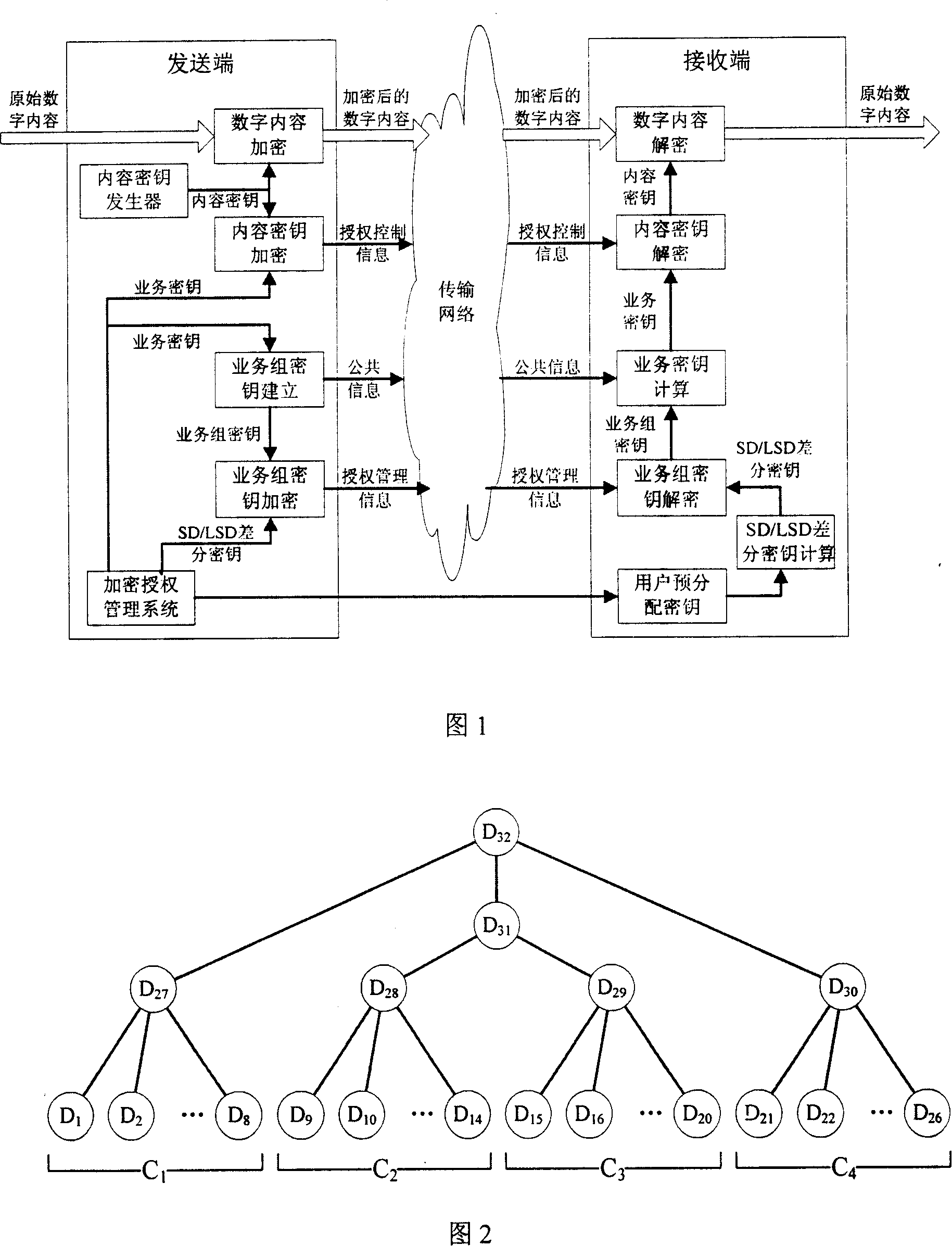
[0020] Below in conjunction with accompanying drawing and specific embodiment the present invention is described in further detail:
[0021] Before the method of the present invention is described in detail, a broadcast encryption (broadcast encryption) technology and a subset difference / hierarchical subset difference mechanism are briefly described first. Broadcast encryption technology refers to a key management mechanism that uses only one-way channels and can authorize and deauthorize any subset of large-scale users without two-way handshake communication. In 2001, D.Naor, M.Naor and Lotspiech jointly proposed a new broadcast encryption mechanism: Subset Difference (Subset Difference) method, referred to as NNL mechanism or SD mechanism. The subset differential mechanism establishes a key tree with all clients as leaf nodes. In this key tree, node v i and v j (where v i is v j The difference subset of ancestor nodes) is set by S i,j said, S i,j ={u|u∈S i , uS j}. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com