Service flow switching method and apparatus
A technology for business traffic and traffic switching, which is applied in the network field to ensure normal transmission and improve reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
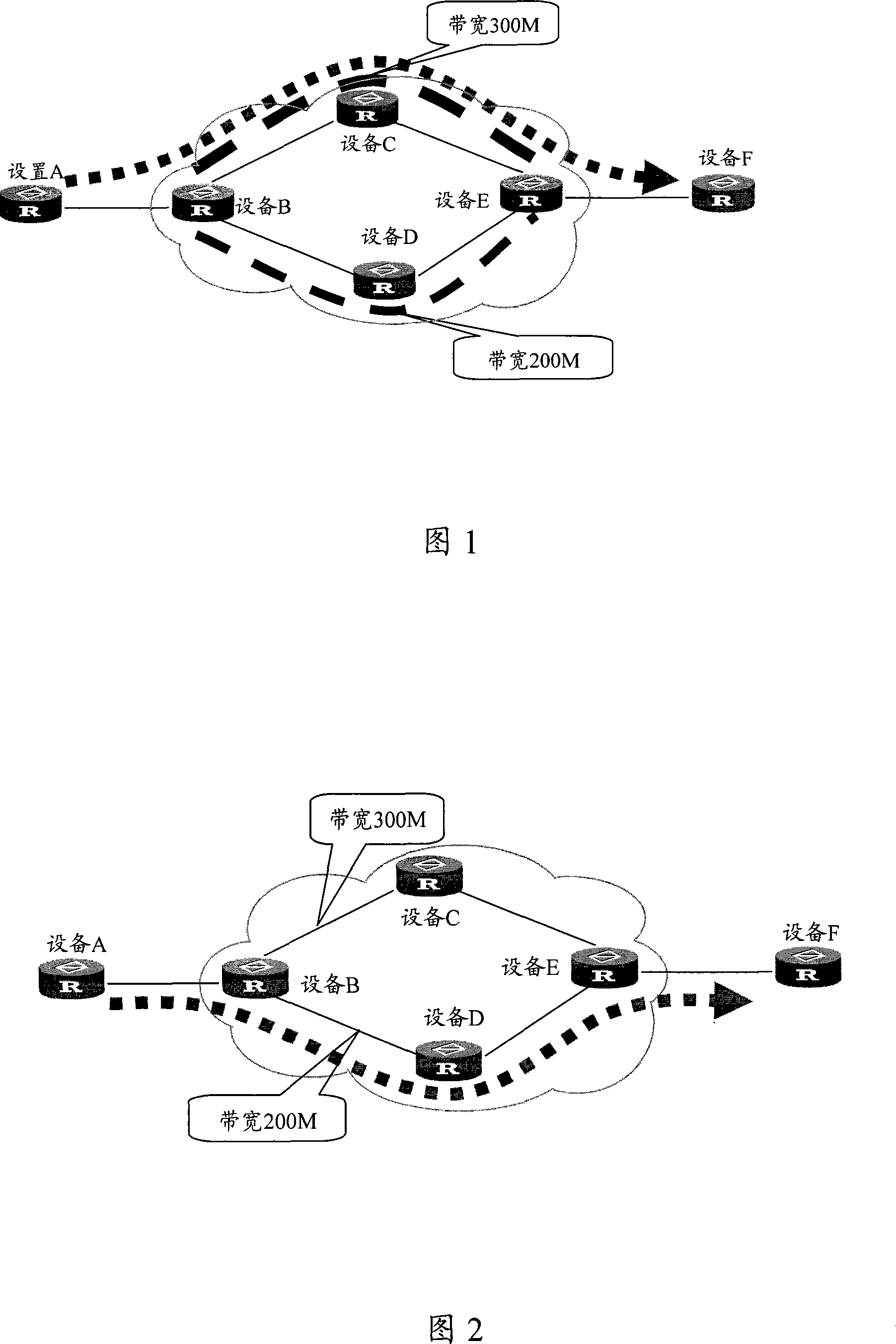
[0030] Referring to Figure 2, in the IP network, there are two routes from device B to device F, where the bandwidth of the B-C-E link is 300M, and the bandwidth of the B-D-E link is 200M. When the routing protocol generates a route, select the link with a bandwidth of 300M as the active link, and the link with the bandwidth of 200M as the backup link.
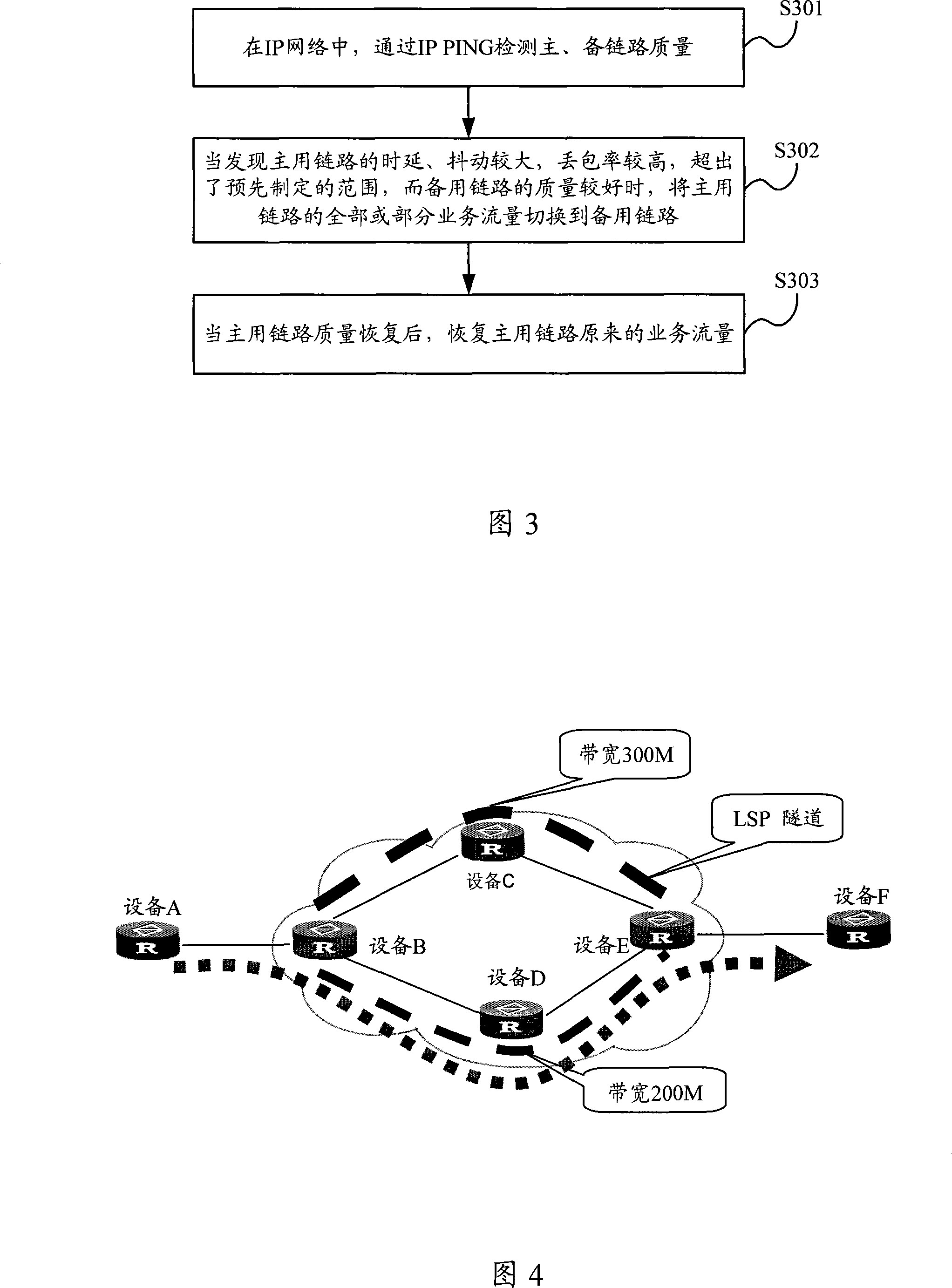
[0031] Then, referring to Figure 3, the methods for implementing service traffic switching include:
[0032] S301, at the device B, through the IP packet Internet exploration (PING, Packet Internet Groper), that is, using the Internet Control Message Protocol (ICMP, Internet Control Message Protocol) response (ICMP Echo) and its response to test a certain network in the IP network Whether the device is reachable, to detect the quality of the main and standby links, regularly collect the delay, jitter, packet loss rate and other related parameters of the main and standby links, and generate the database of the main and standby ...
Embodiment 2
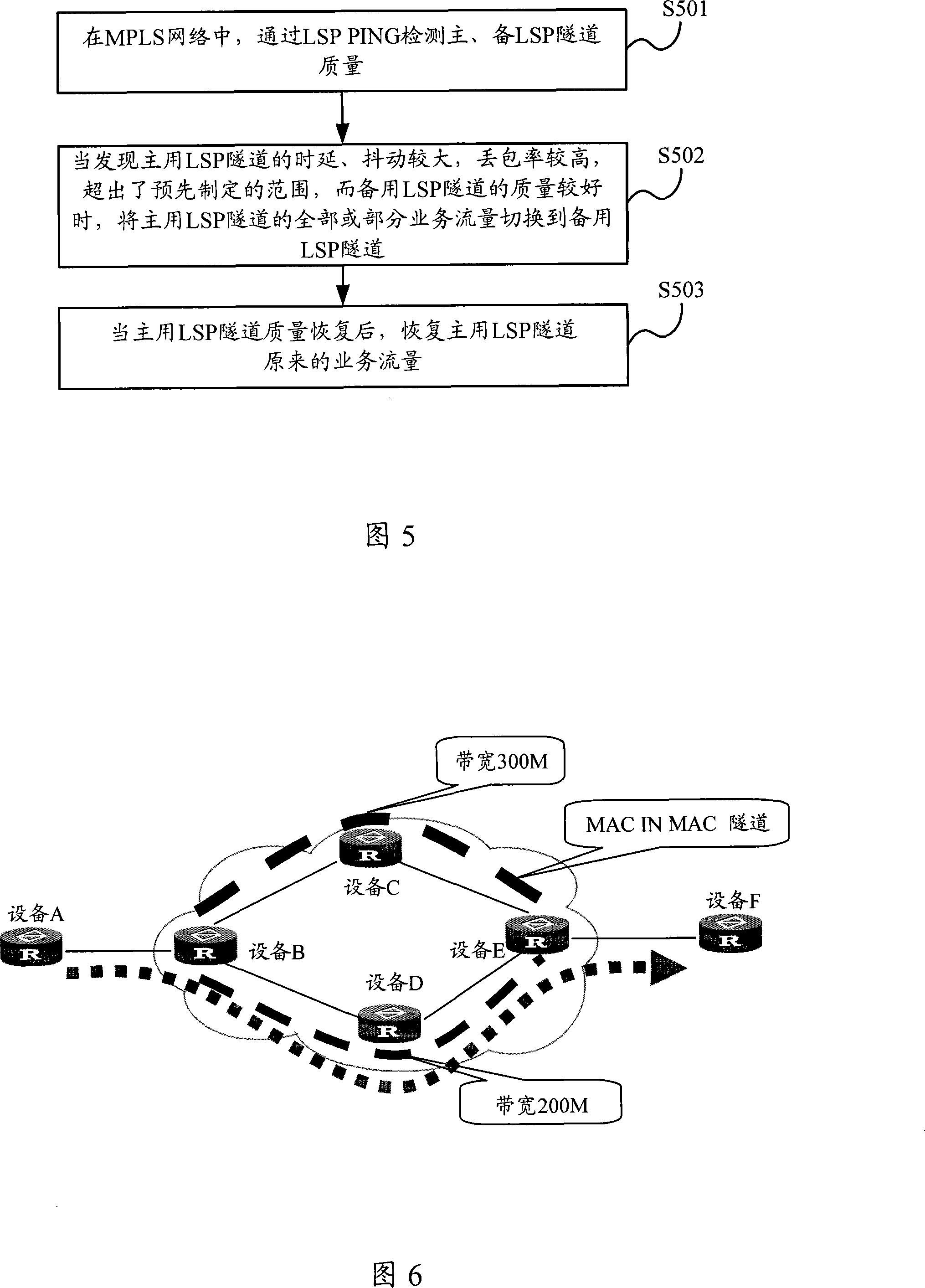
[0038] Referring to Figure 4, in the MPLS network, there are two LSP tunnels from device B to device F. The bandwidth of the B-C-E link is 300M, the bandwidth of the B-D-E link is 200M, and the LSP tunnel with a bandwidth of 300M is the main link. The LSP tunnel with the highest bandwidth is the backup link.
[0039] Then, referring to Figure 5, the methods for implementing service traffic switching include:
[0040] S501. At device B, detect the quality of the primary and secondary LSP tunnels through LSP PING, regularly collect relevant parameters such as time delay, jitter, and packet loss rate of the primary and secondary LSP tunnels, and generate a database of the primary and secondary LSP tunnels.
[0041]S502. Periodically check parameters such as time delay, jitter, and packet loss rate of the active and standby LSP tunnels in the database, and if it is found that the time delay, jitter, and packet loss rate of the active LSP tunnel are relatively high, exceeding the p...
Embodiment 3
[0044] Referring to Figure 6, in the MAC IN MAC network, there are two MAC IN MAC tunnels from device B to device F, where the B-C-E link is 300M, the B-D-E link is 200M, and the MAC IN MAC tunnel with 300M bandwidth is the main link , MAC IN MAC tunnel with 200M bandwidth is the backup link.
[0045] Then, referring to Figure 7, the methods for implementing service traffic switching include:
[0046] S701. At device B, use 802.1ag MAC PING to detect the quality of the primary and backup MAC IN MAC tunnels, regularly collect relevant parameters such as time delay, jitter, and packet loss rate of the primary and backup MAC IN MAC tunnels, and generate primary and backup MAC IN MAC tunnel quality. Database of MAC IN MAC tunnels.
[0047] S702. Regularly check the time delay, jitter, packet loss rate and other parameters of the primary and backup MAC IN MAC tunnels in the database. If it is found that the time delay and jitter of the primary MAC IN MAC tunnel are relatively larg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com