A method and device for enhancing network security
A network security and network technology, applied in the field of network security, can solve problems such as system danger, control system confusion, wireless devices without security verification means, etc., to achieve the effect of enhancing security and preventing illegal devices from accessing the network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
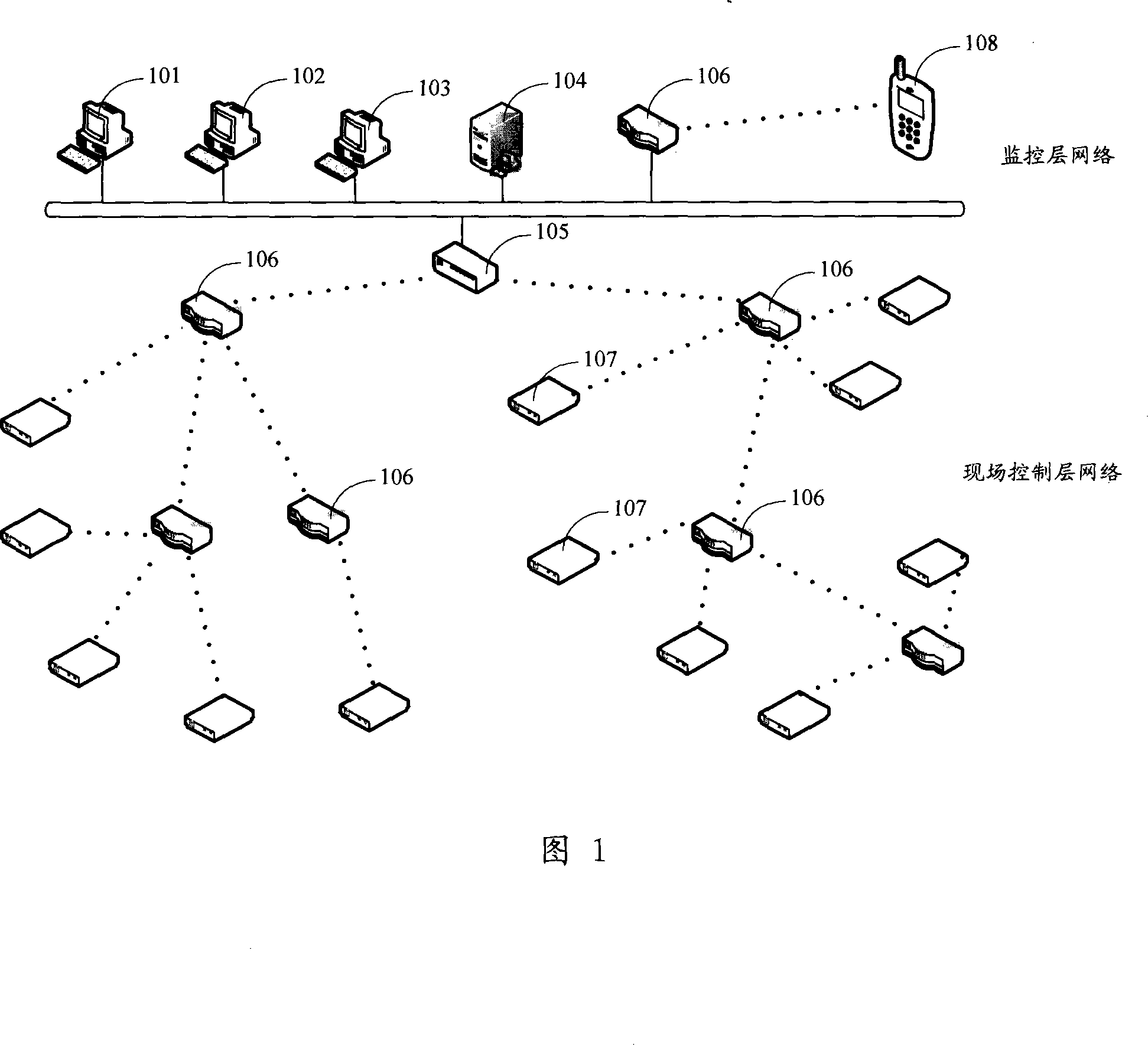
[0040] A method for strengthening network security disclosed in the embodiment of the present invention can be detected when a device is connected to a wireless network. After the connection is established, it can continue to check whether any illegal device has joined the connected device. At the same time, it is also possible to further improve the security of the network by encrypting the transmitted data in the wireless network, and monitor the access rights of the equipment to comprehensively realize the security of network access, so as to prevent the network from being destroyed by illegal equipment. .
[0041] Various monitoring implementation modes of the present invention will be further described in detail below in conjunction with the accompanying drawings.
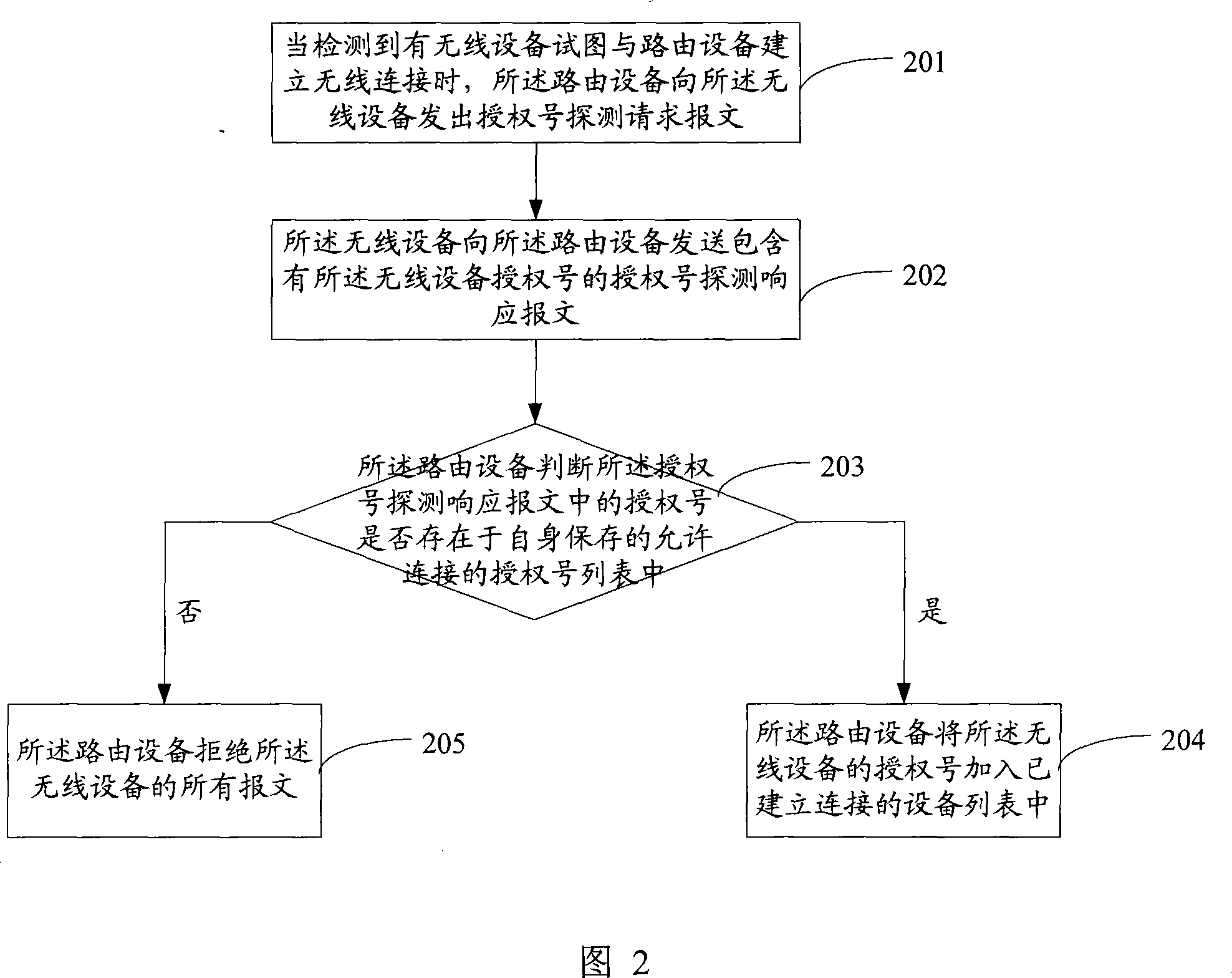
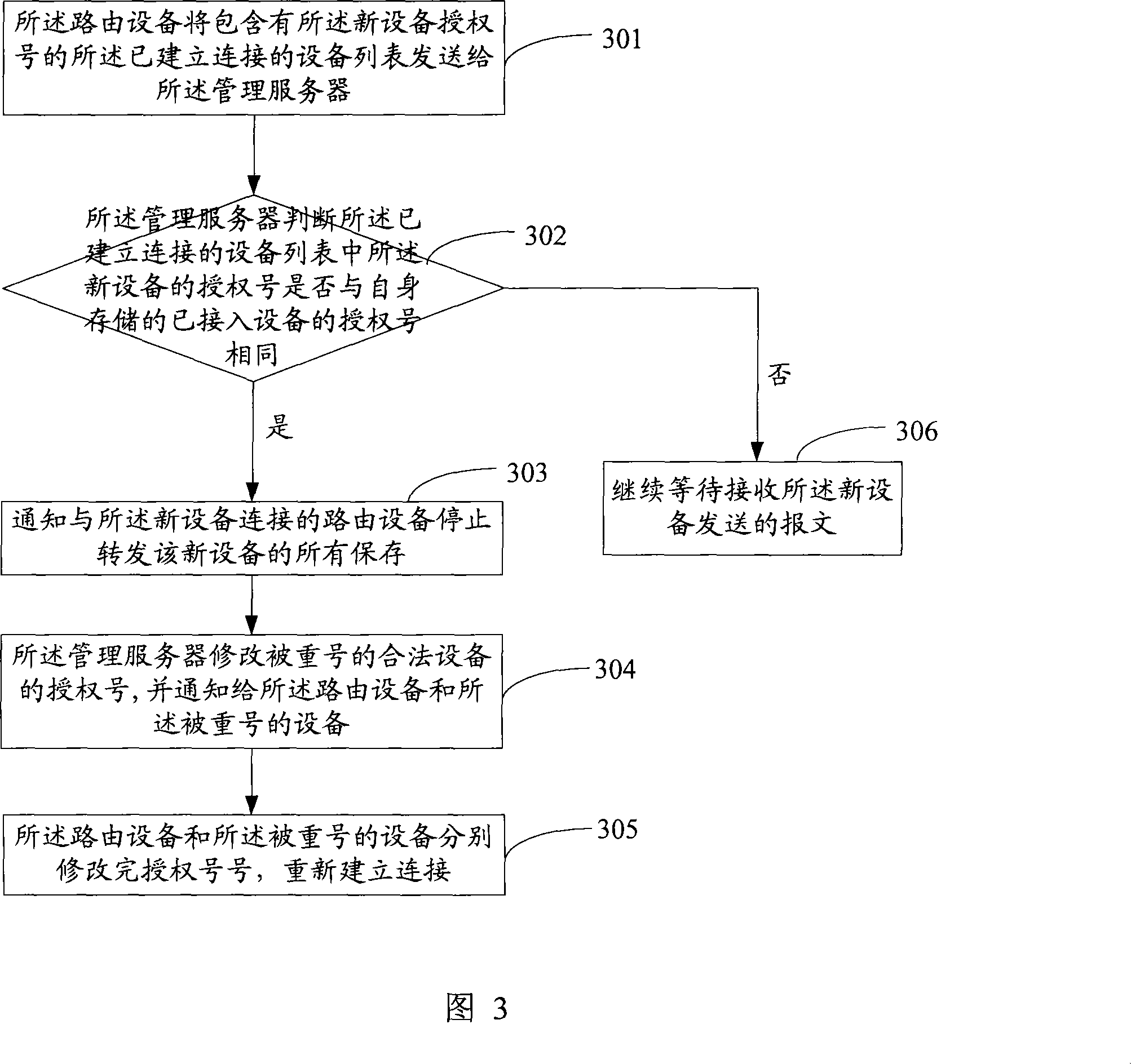
[0042] An embodiment of a method for establishing a connection of a wireless device disclosed in the present invention, this embodiment maintains a list of authorization numbers allowed to access on the routin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com