Identity authentication method based on S/Key system
An authentication method and one-time technology, applied in the field of identity authentication, can solve the problems of S/Key system defects, S/Key system cannot resist decimal attacks, easy to be illegally intercepted, etc., to avoid decimal attacks, high security, improve safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
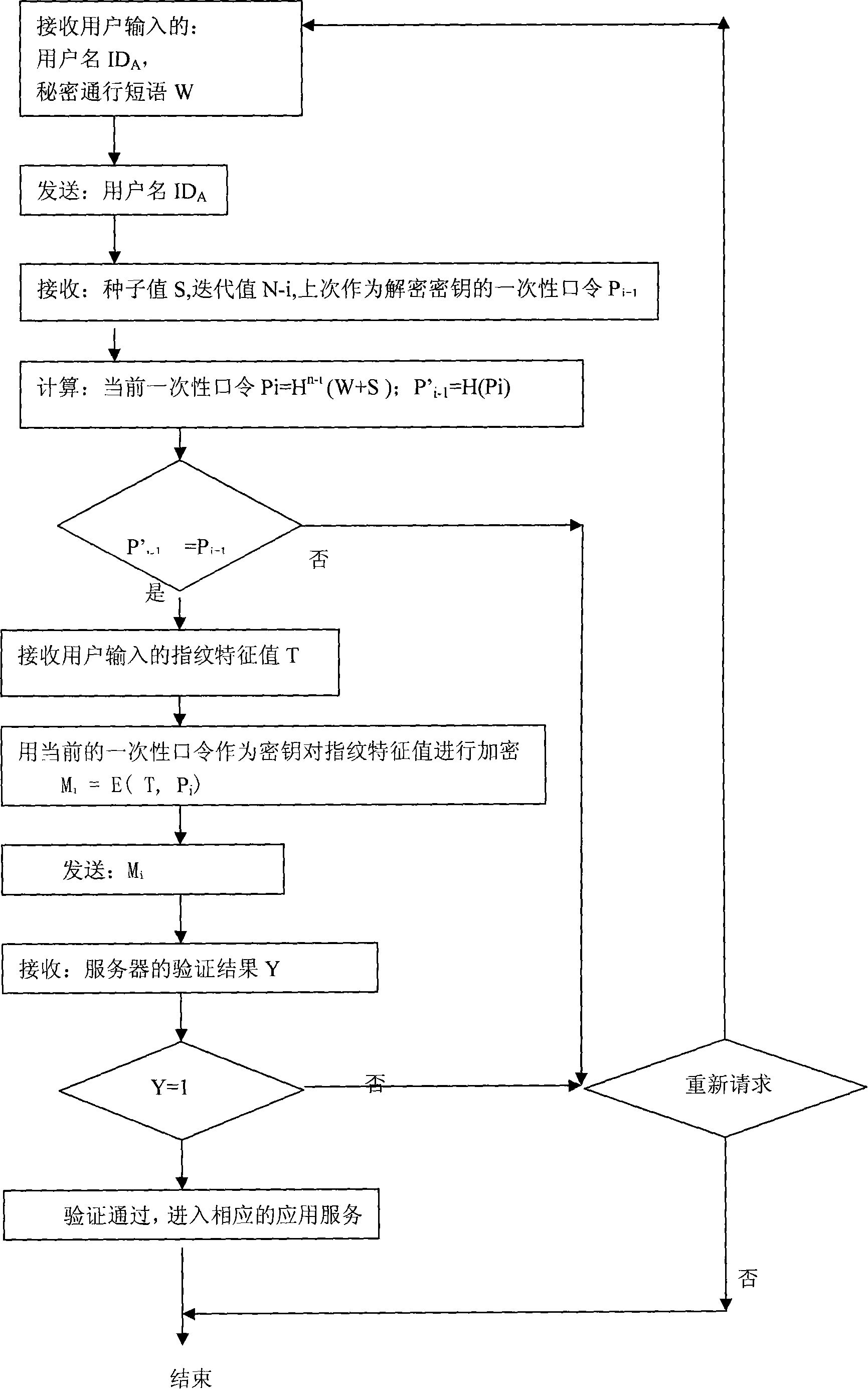
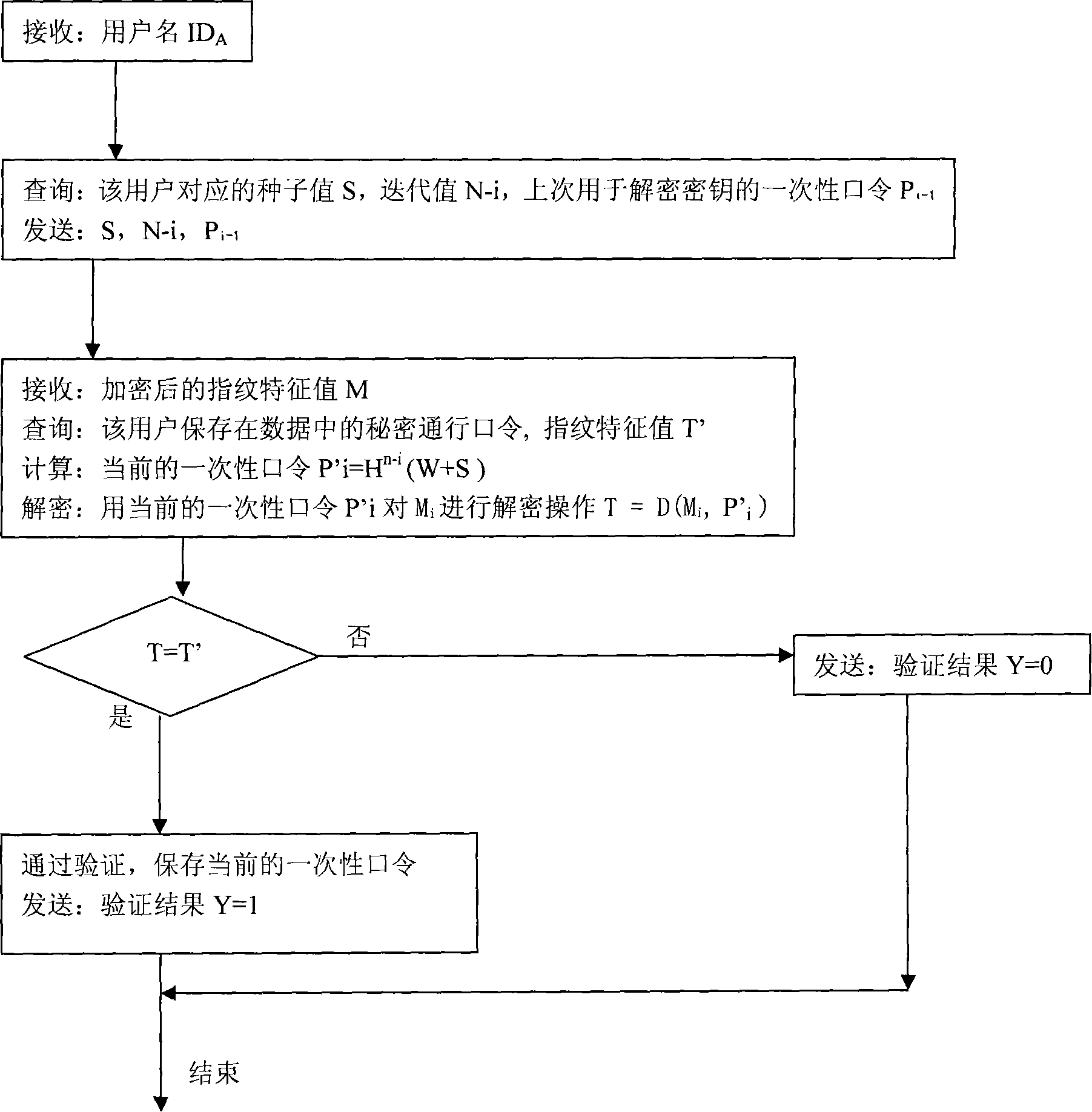
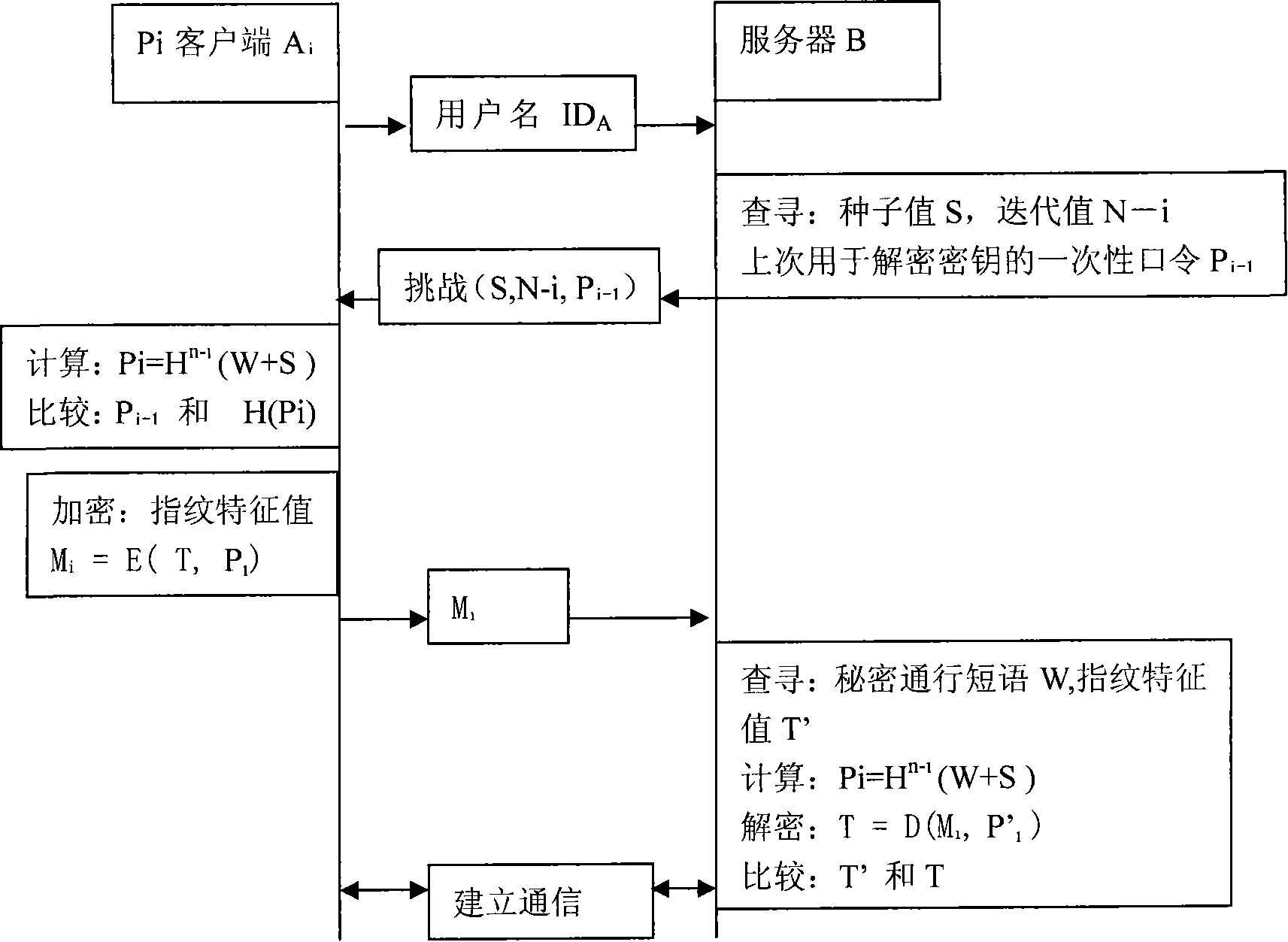
[0031] A two-way identity authentication method based on the combination of a one-time password of the S / Key system and biometric identification comprises the following steps:
[0032] (1) The client user sends an identity authentication request to the server;
[0033] User ID A ;
[0034] (2) The server sends a response message to the client according to the username sent by the client:
[0035] The server sends the iteration value N, the seed value S and the one-time password P used to decrypt the biometric value during the last authentication to the client i-1 ;
[0036] (3) The client calculates the current one-time password according to the current iteration value N-i, the seed value S, and the secret passphrase W. Calculated as follows:
[0037] P i =H N-i (W+S);
[0038] (4) The client saves the current password P i , and for the current password P i Perform another hash operation, calculated as follows:
[0039] P' i-1 =H(P i );
[0040] The client will P...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com