Method for protecting data of memory mechanism
A storage device and data protection technology, which is applied in the direction of data error detection and response error generation, can solve the problems of memory waste, money and memory waste, and occupation, so as to improve reliability and improve The effect of using capacity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
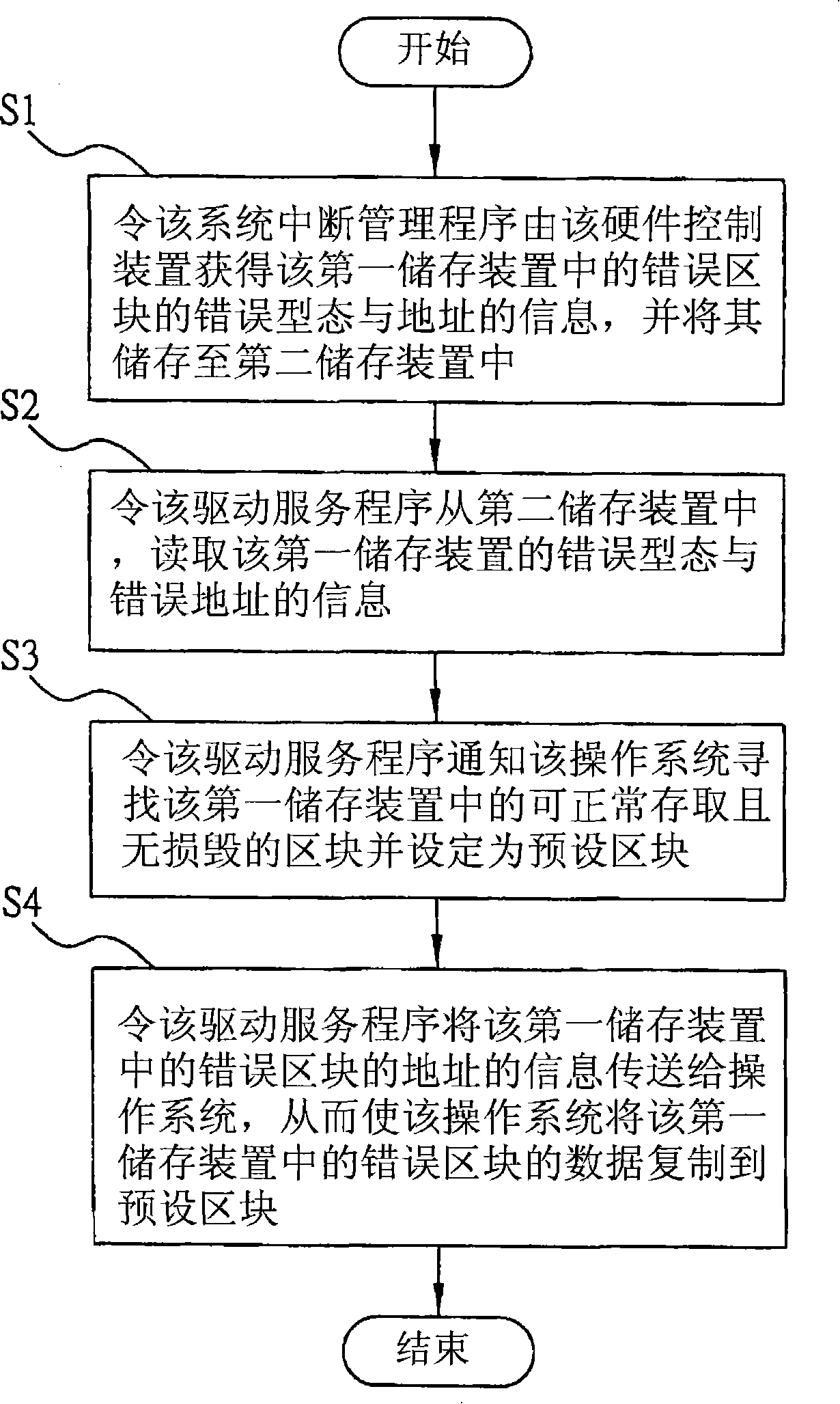
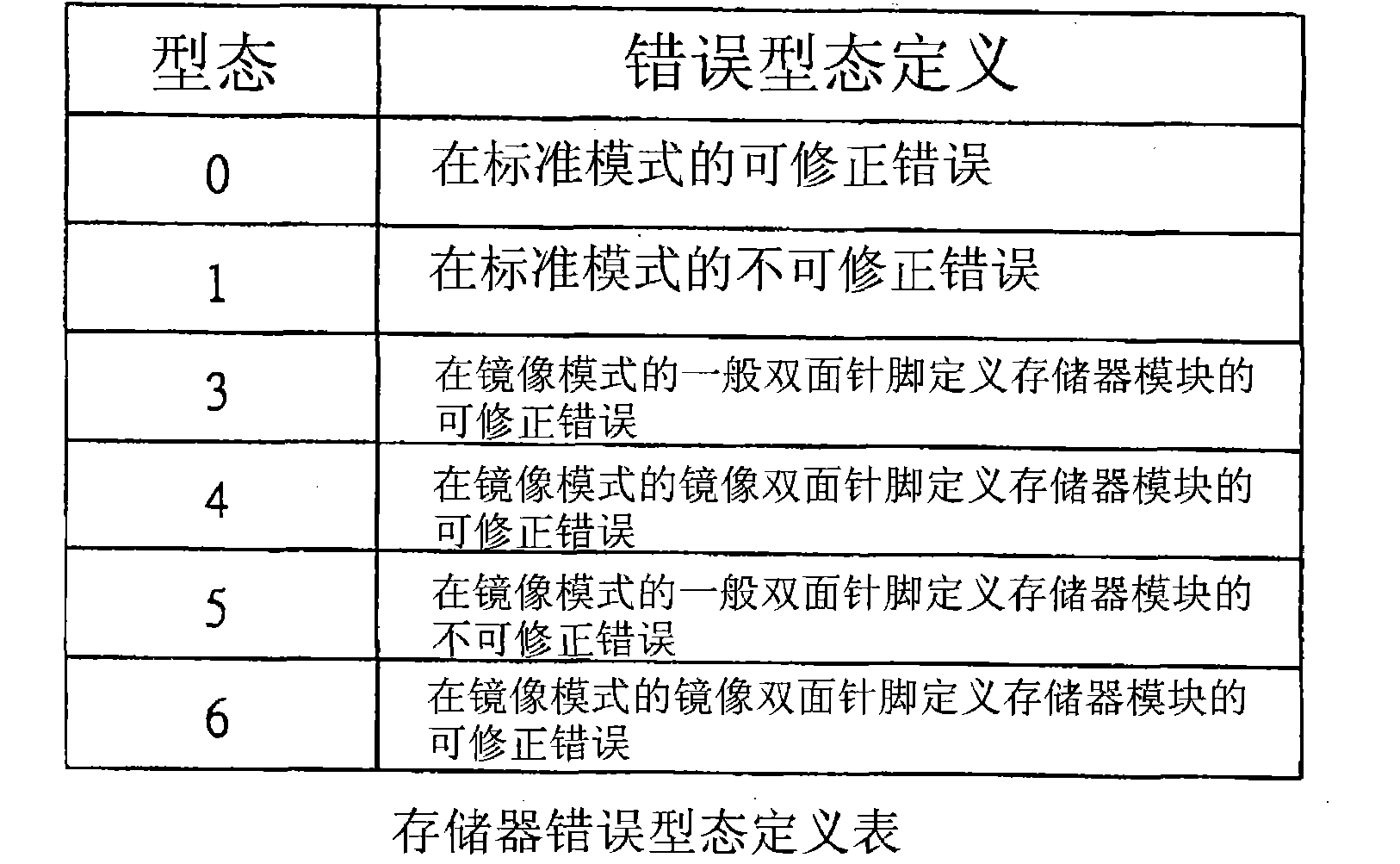
[0025] The implementation of the present invention is described below through specific examples, and those skilled in the art can easily understand other advantages and effects of the present invention from the content disclosed in this specification.
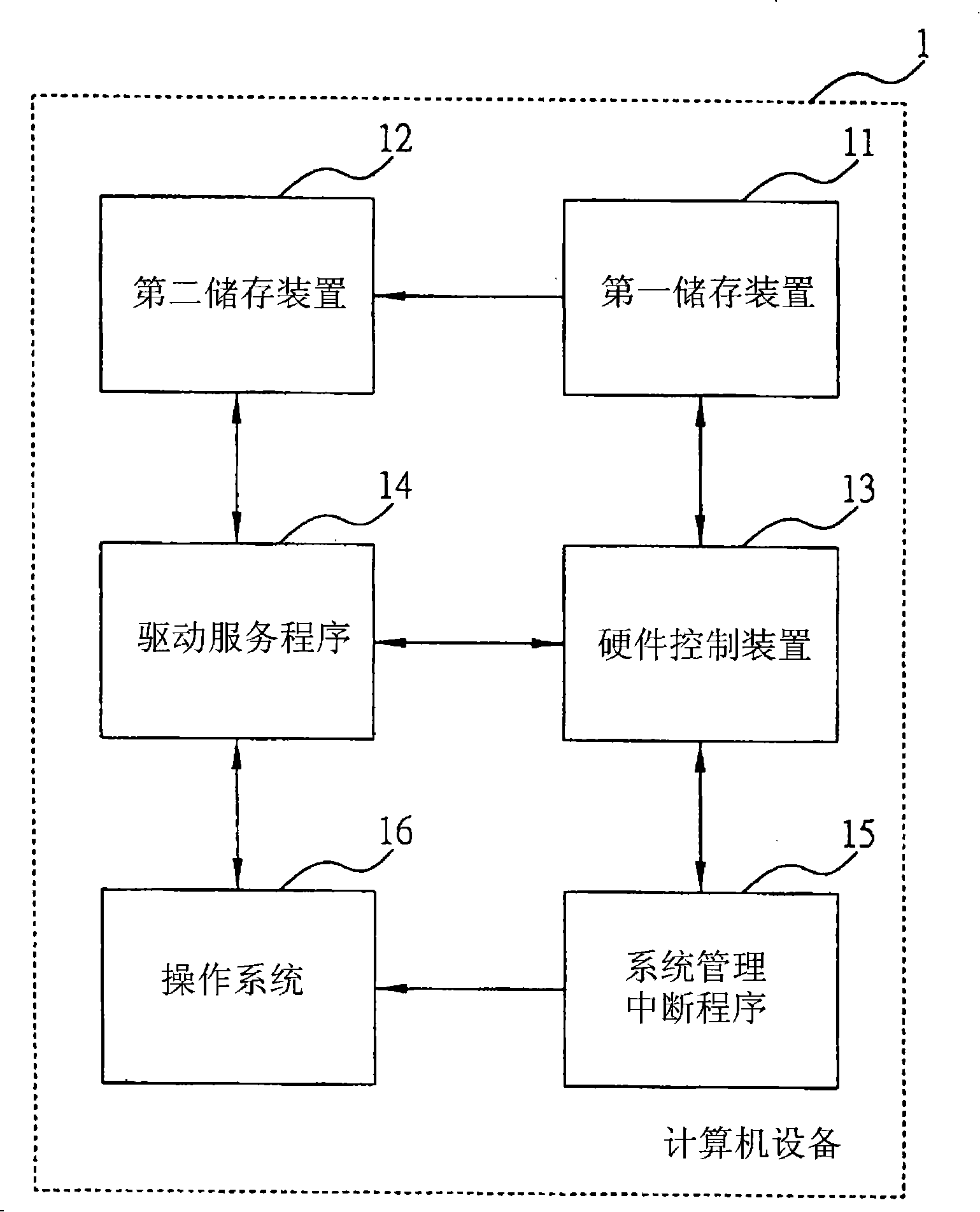
[0026] see figure 1 , which is a schematic block diagram of the corresponding basic structure of the data protection method of the storage device of the present invention. As shown in the figure, the computer equipment 1 is composed of a first storage device 11, a second storage device 12, a driver service program 14, and a hardware control device. 13. A system management interrupt program 15 (System Manage Interrupt; SMI) and an operating system 16 are used to provide the basic framework corresponding to the data protection method of the storage device of the present invention. What needs to be explained here is that the computer equipment 1 applying the data protection method of the storage device of the present invention has...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com