Security method and system as well as correlative pairing enciphering system thereof
A technology of a security method and a security system, which is applied in the field of security methods and systems, and can solve problems such as damage to the correctness of information accessed by the user terminal
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
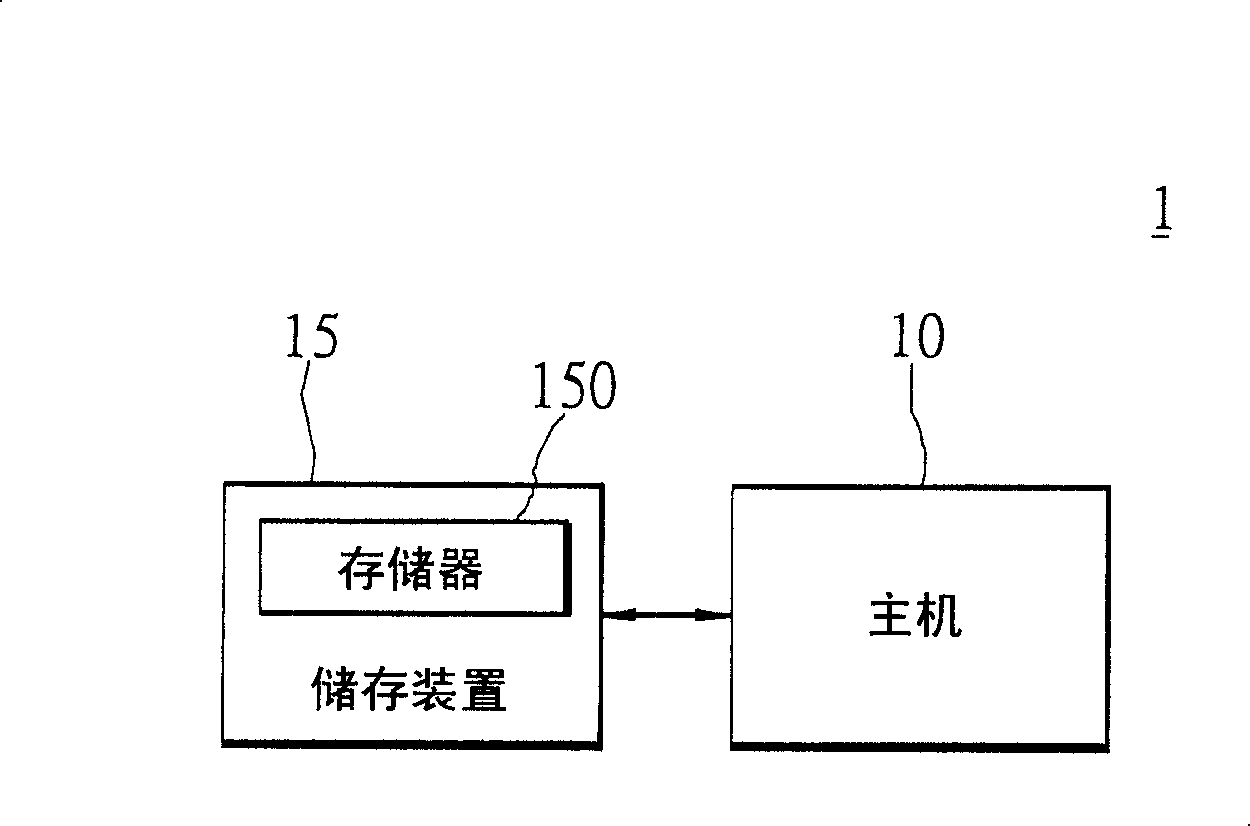
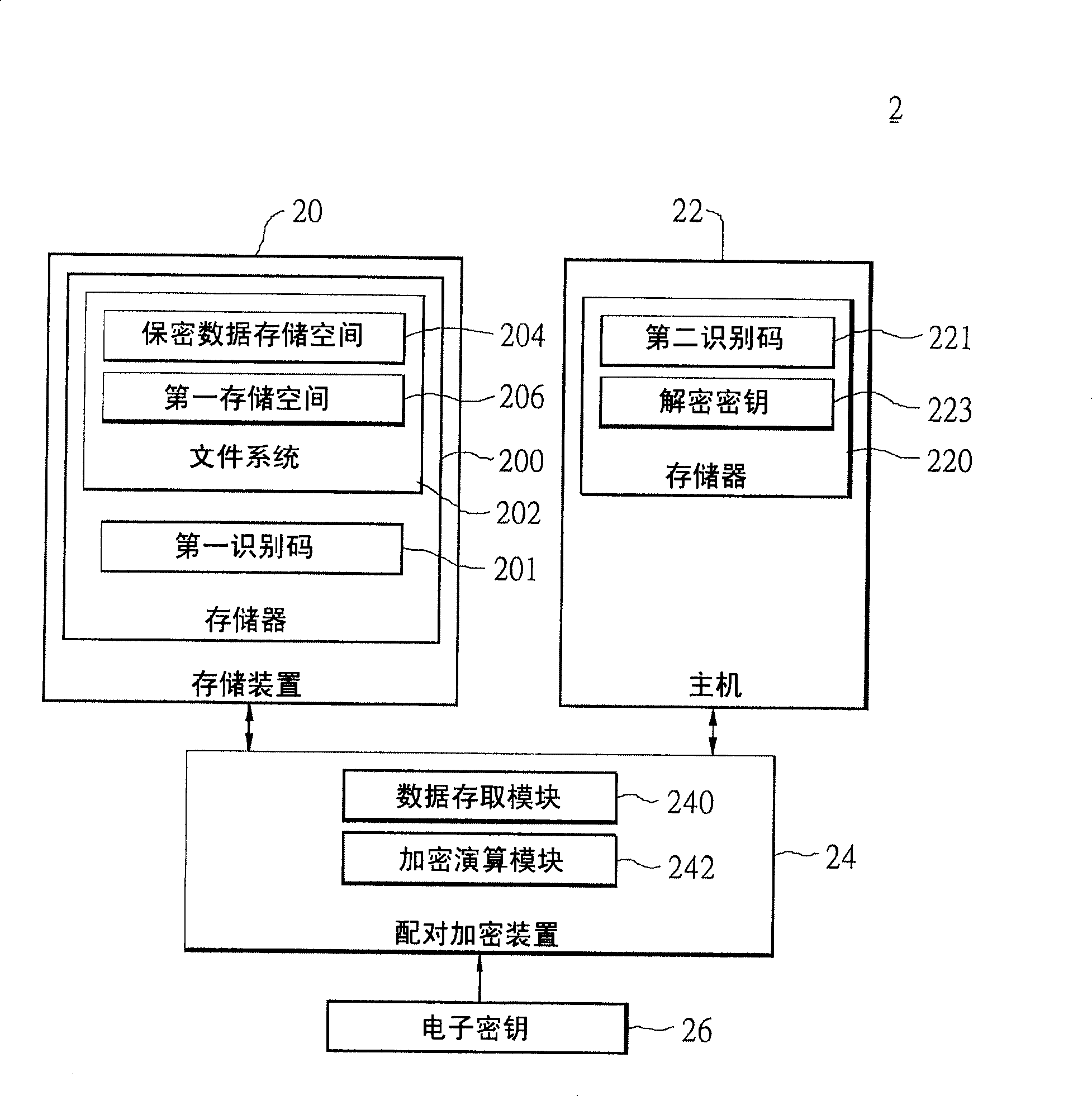
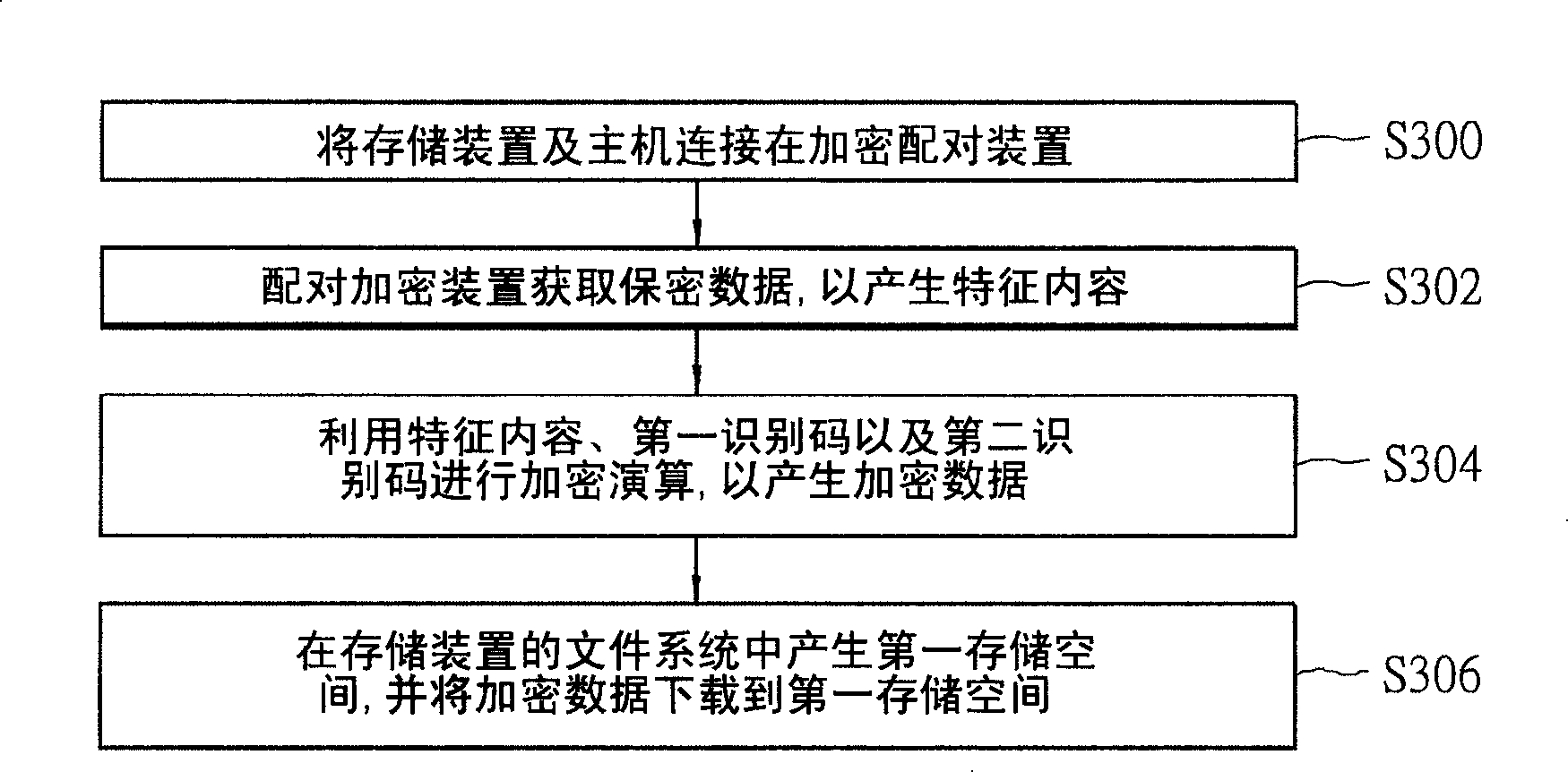
[0047] First, see figure 2 , which is a schematic diagram of the system architecture of the pairing encryption system 2 of the present invention. Such as figure 2 As shown, the pair encryption system 2 includes a storage device 20 , a host 22 and a pair encryption device 24 . The storage device 20 stores confidential data and is configured to be paired with the host 22 . The purpose of this pairing is to limit the use authority of the confidential data of the storage device 20 , and the client can only access the confidential data of the storage device 20 through the host 22 . The host 22 here is an electronic product, such as a personal digital assistant, a wireless communication device, a digital camera, a digital video player, and a GPS navigation system. The storage device 20 refers to a large-capacity storage medium, including flash memory cards of various specifications. The storage device 20 is pluggably connected to the host 22 , and the host 22 accesses and uses t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com