A trusted network connection system based on three-element peer authentication
A network connection and ternary peer-to-peer technology, applied in the field of network security, can solve the problems of inability to verify the validity of AIK certificates, unequal platform integrity assessment, and complex key negotiation process, to simplify key management and integrity Check mechanism, eliminate the need for strong security associations, and enhance the effect of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
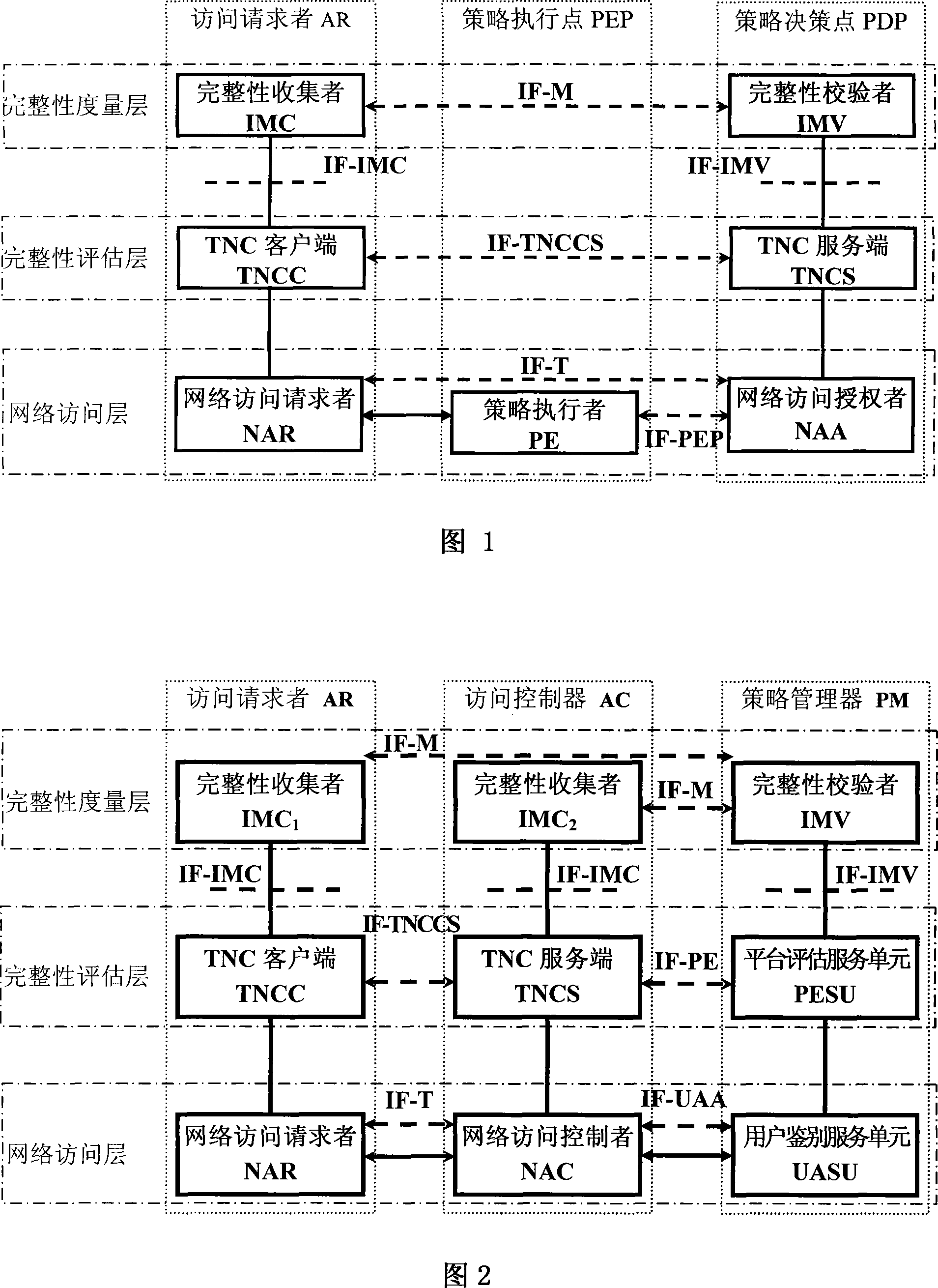
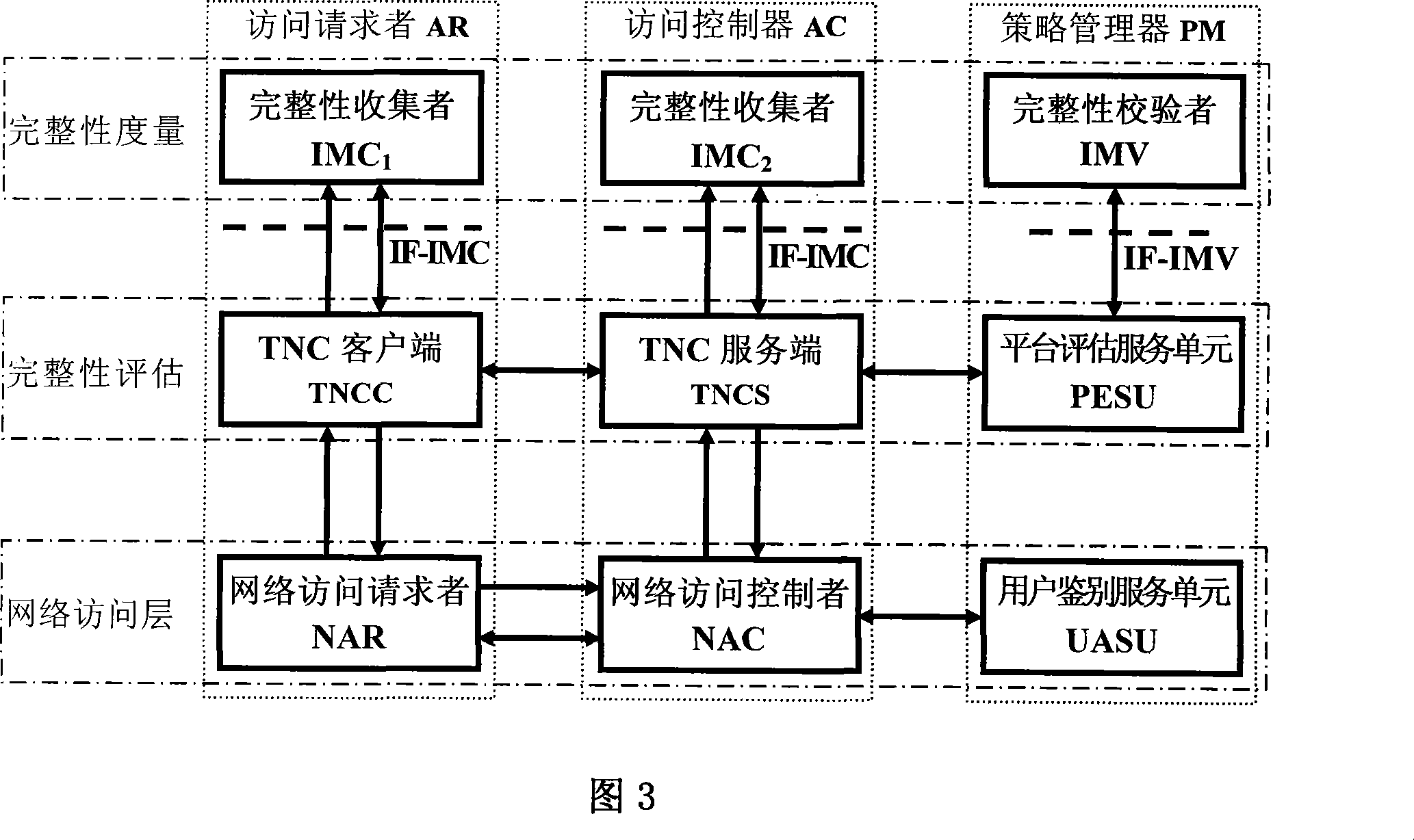
[0043] Referring to Fig. 2, the present invention mainly consists of three logical entities: an access requester AR, an access controller AC and a policy manager PM, which can be distributed anywhere in the network. Access requester AR is also called requester, user station, etc.; access controller AC is also called authentication access controller, base station, access service unit, etc.; policy manager PM is also called authentication server, trusted server, background server Wait. The access requester AR communicates with the access controller AC through the protocol interface network, the access controller AC communicates with the policy manager PM through the protocol interface network, and the policy manager PM communicates with the access requester AR through the access controller AC.
[0044] The access requester AR is mainly composed of the network access requester NAR, the TNC client TNCC and the access requester’s integrity collector IMC 1 constitute. The network ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com