Method for performing strategy identification and control by using user service identification (USID)
A user service and identification technology, applied in the field of mobile communication, can solve the problems of consumption, consumption of resources, multi-computing and storage resources, etc., and achieve the effect of saving computing resources, reducing workload, and network intelligence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
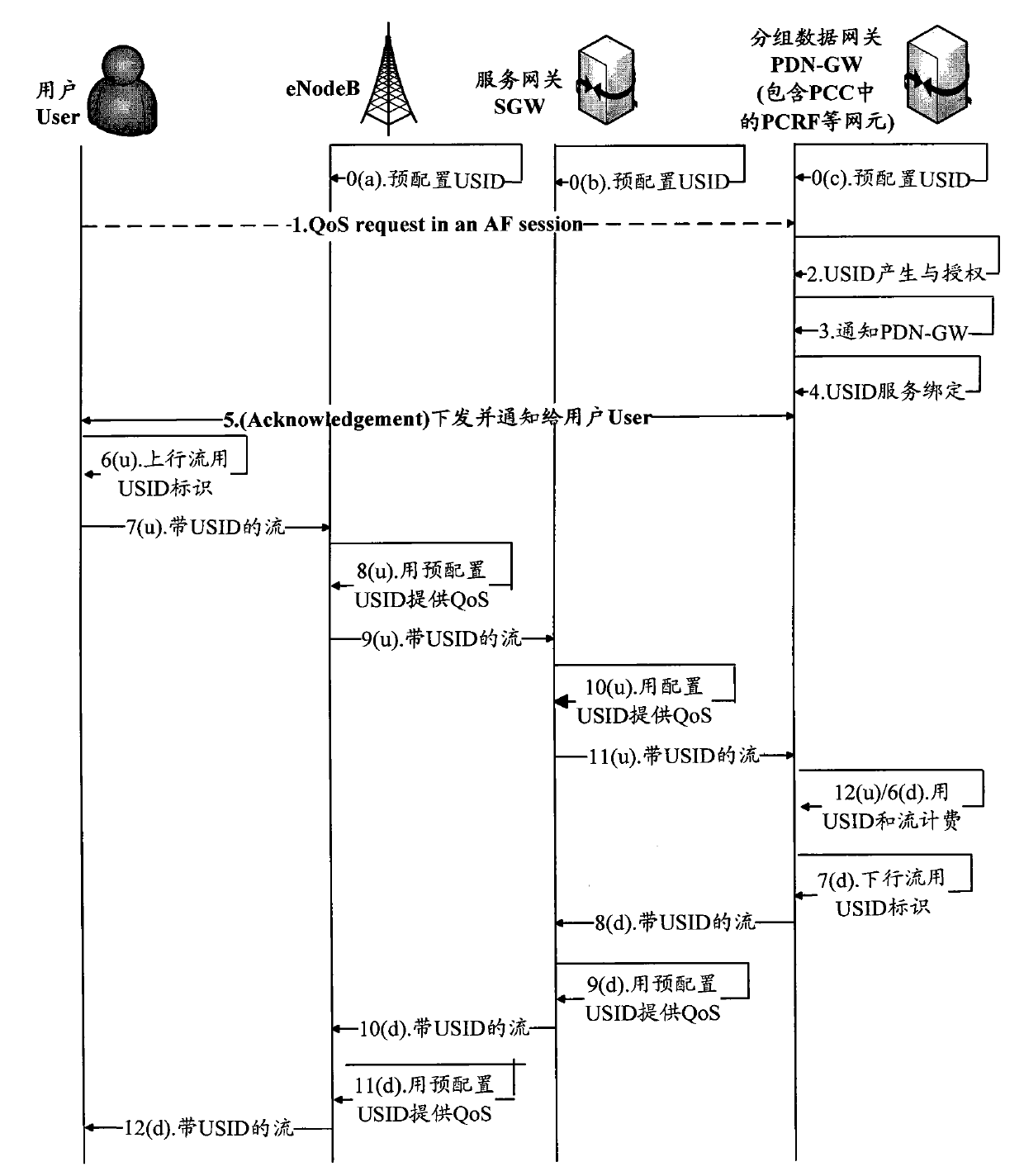
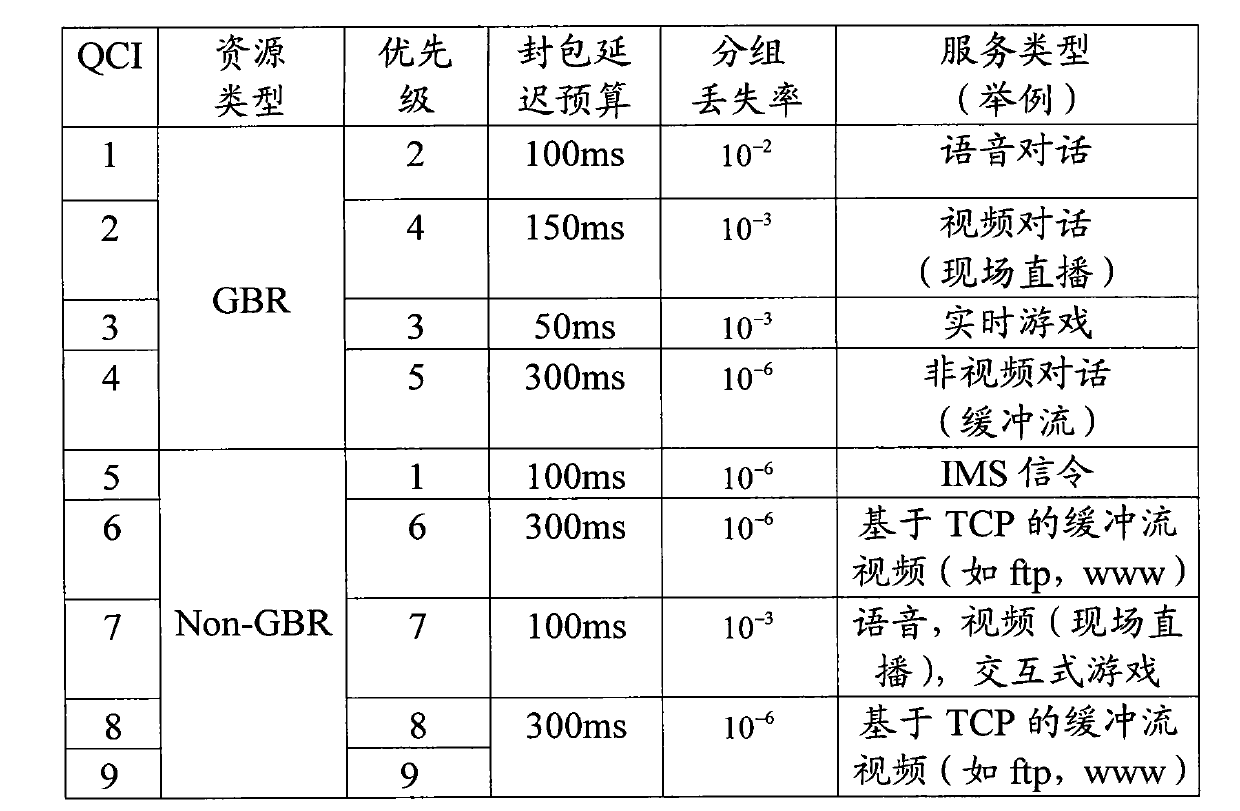
[0041] As an all-IP system, EPS adopts IP protocol in all network elements. Compared with the traditional IPv4, IPv6 has many advantages, including rich address resources, enhanced mobile functions and extended QoS features. For all network elements in the EPS, it is very simple to set the USID in IPv6; and it will solve the crosslayer (crosslayer) problem in the existing EPS system. QoS and billing information are collected at the IP layer, rather than at the GPRS tunnel protocol layer, radio bearer control layer and mobile IP layer.
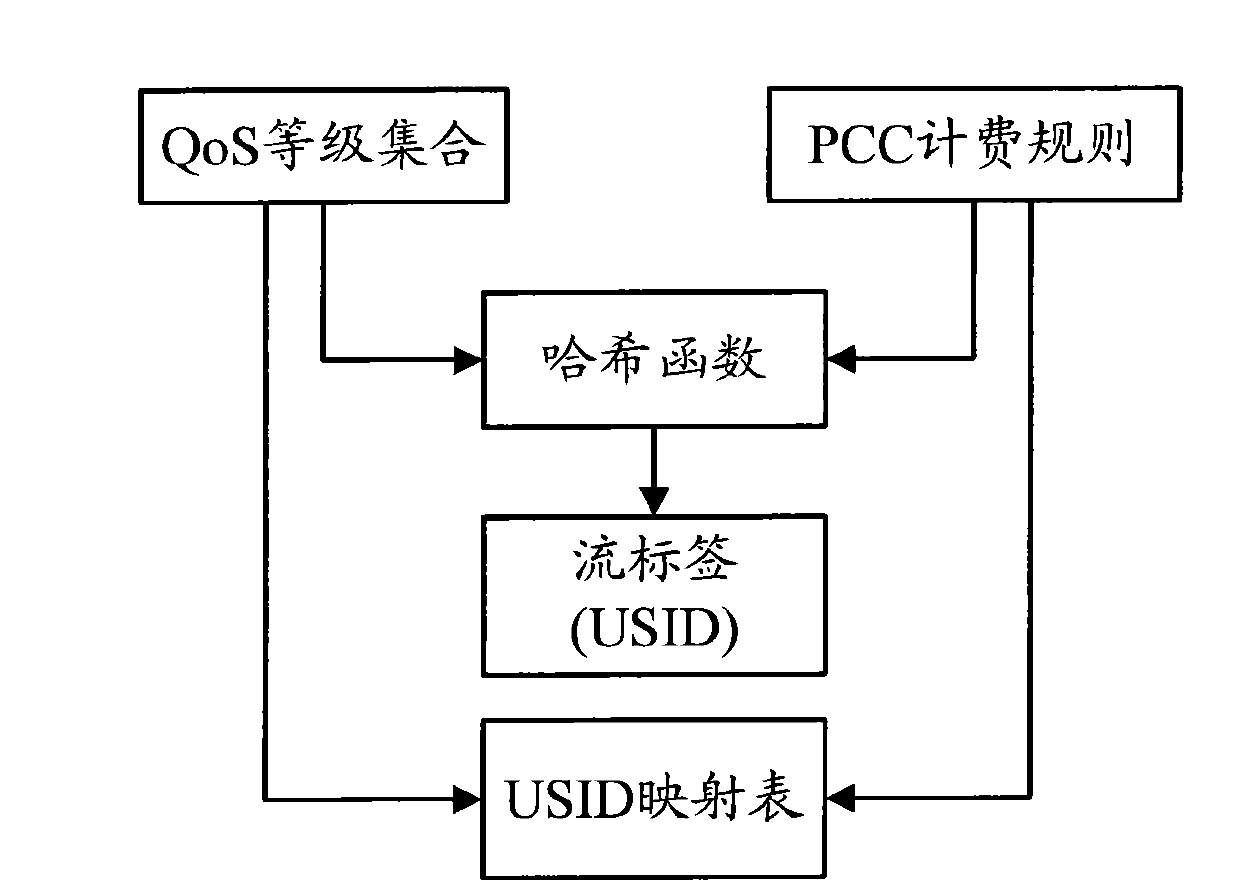
[0042] The method of the present invention using USID to implement policy identification and control in EPS is to replace the bearer identification with the flow label field in the IPv6 data packet header, that is,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com