Online recognition method for network multi-step attack intension
An identification method and network technology, applied in digital transmission systems, secure communication devices, electrical components, etc., can solve the problems of relying on prior knowledge, difficulty in discovering new attacks, and inability to effectively guarantee real-time performance, and achieve the effect of real-time online detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
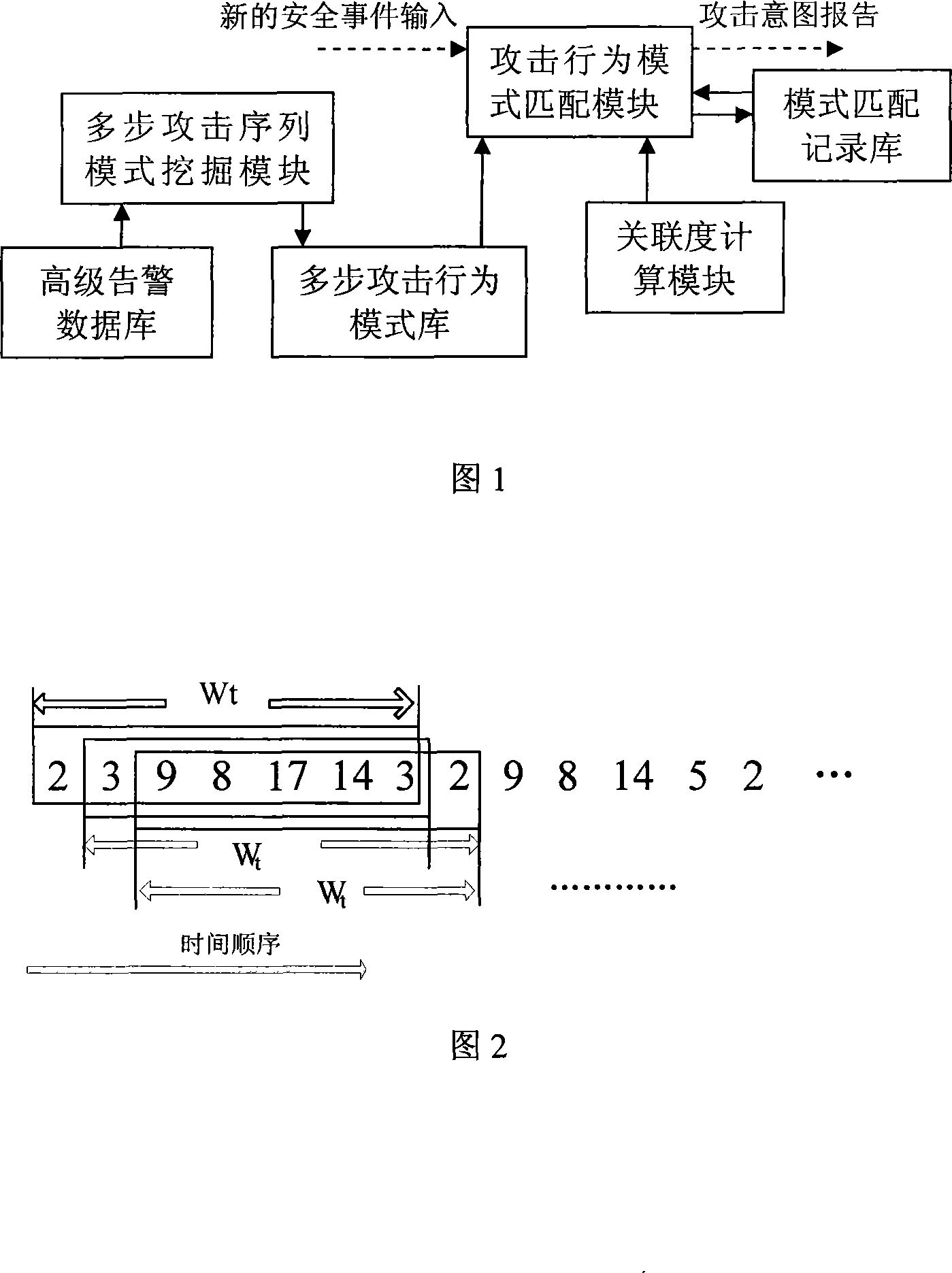
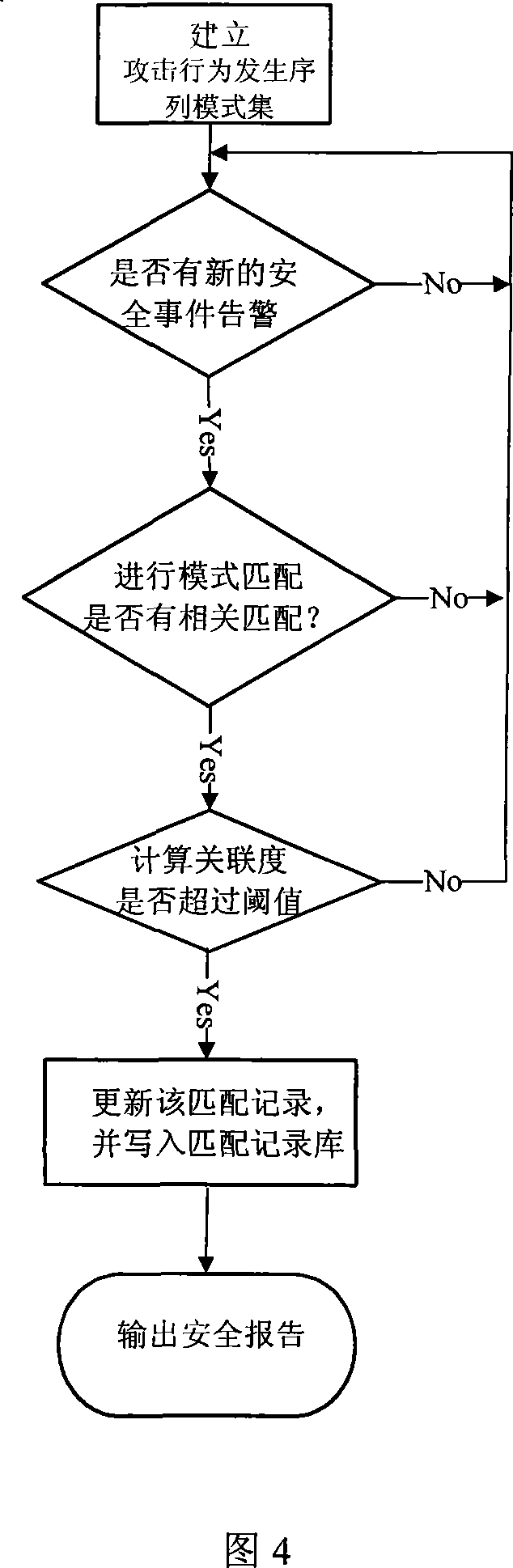
[0020] First of all, it is necessary to mine the multi-step attack sequence pattern set from the historical security event alarm database. The attack behavior sequence pattern set includes multiple feature sequences, and each feature sequence reflects the multi-step attack relationship between features, which provides a pattern matching basis for attack recognition, as follows:
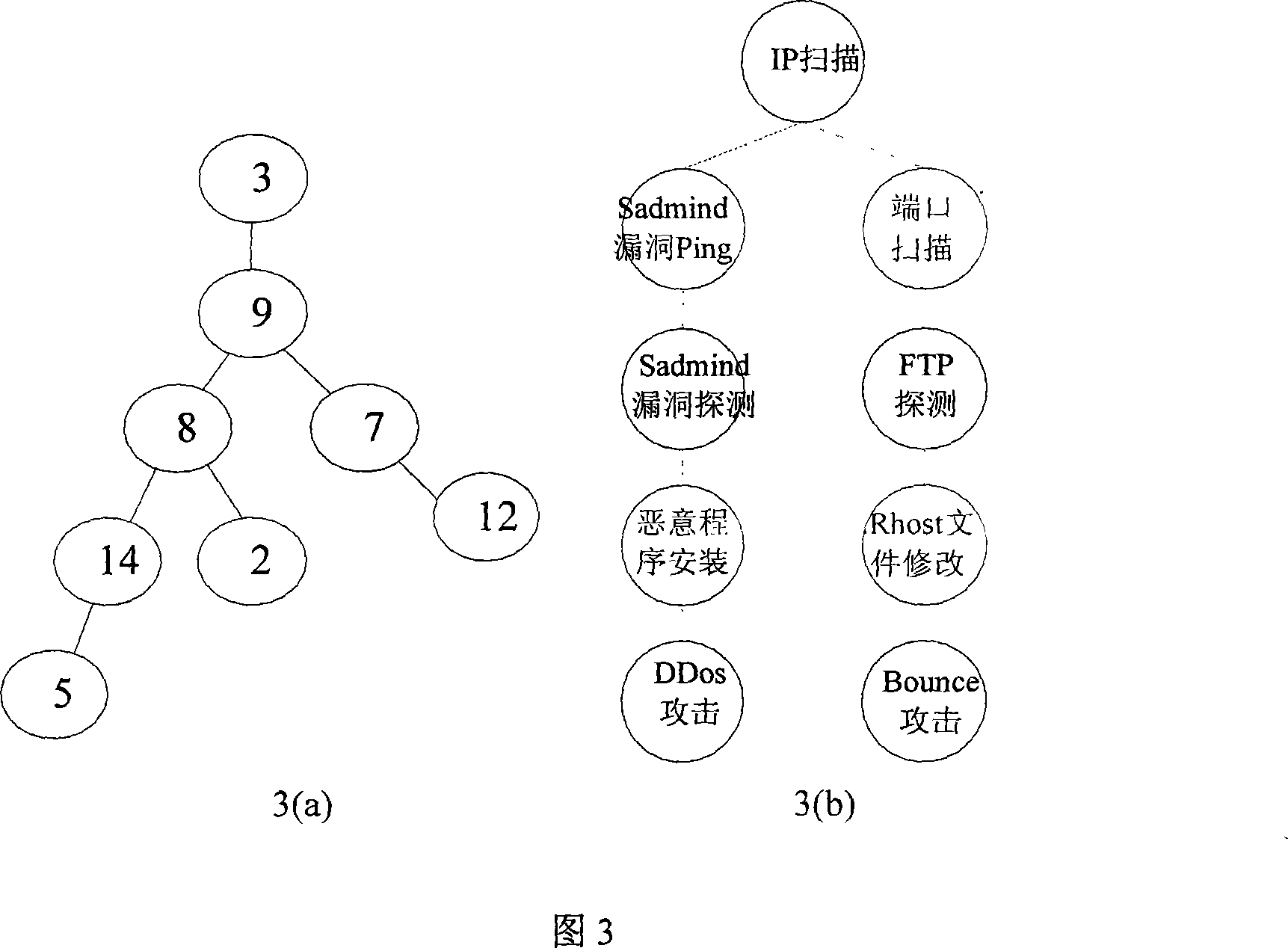
[0021] 1. Extract the attack behavior characteristic SID in each historical security event alarm, sort according to the time of occurrence, and construct a global attack sequence.
[0022] 2. Use the attack scenario time window W T Divide the global attack sequence into multiple candidate attack sequences.
[0023] Attack scenario time window (attack scenario time window) W T The meaning of is: the time interval of multi-step attack, that is, the entire time period from the occurrence of the first multi-step attack step to the completion of the last multi-step attack step. suppose a 1 and a l are...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com