Collocating method for preventing attack of network, method and apparatus for preventing attack
A network and message technology, applied in the field of communication, can solve problems such as failure and large resources, and achieve the effects of reducing pressure, limited consumption, and preventing specific types of message attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
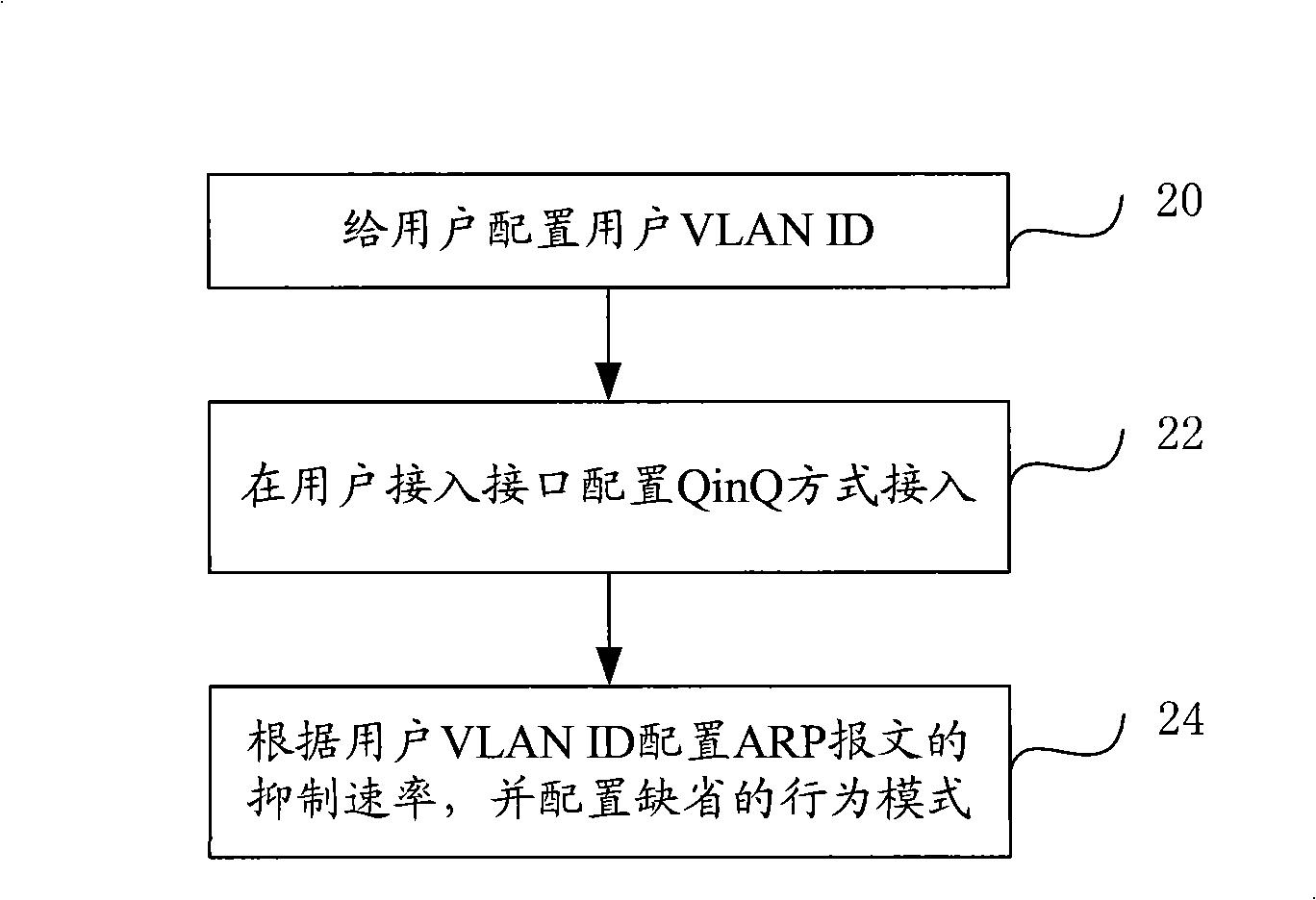
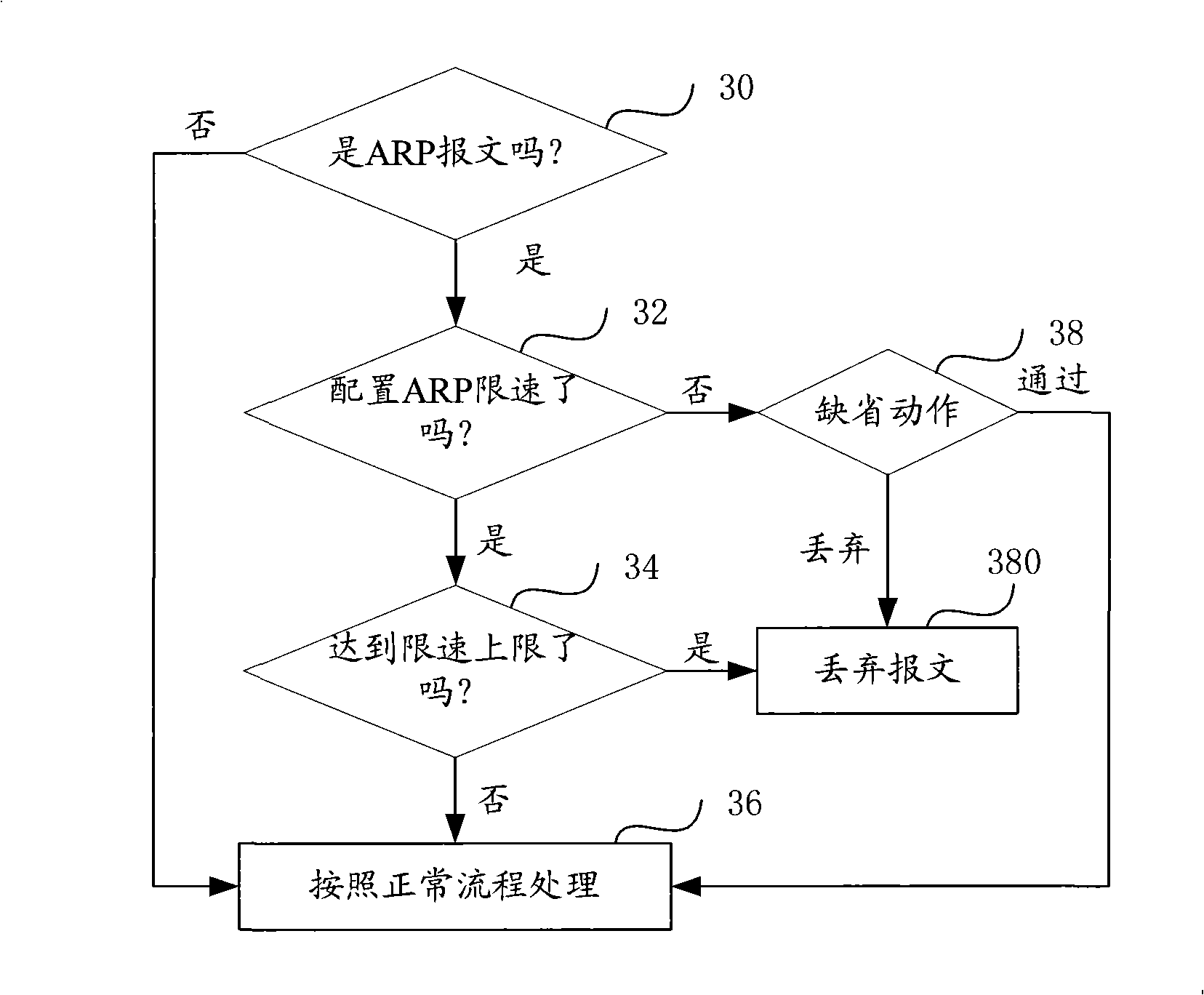
[0014] The implementation process of the present invention will be described below in combination with specific embodiments.
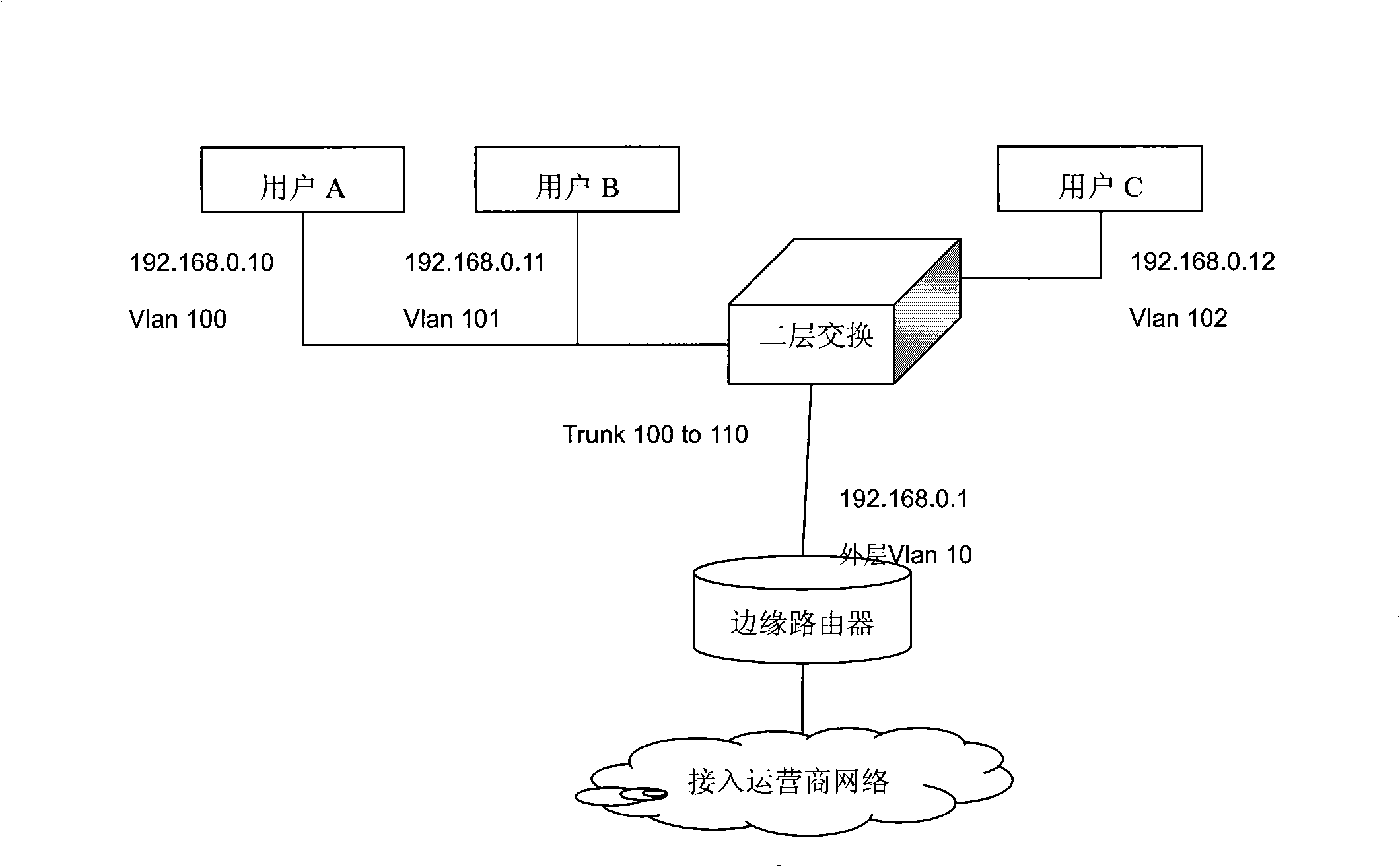
[0015] In the IEEE 802.1Q standard, the Ethernet frame format is modified, and a 4-byte 802.1Q Tag is added between the source MAC address (Source Address) field and the protocol length / type field (Length / Typee), which uses The 12 bits identify different VIDs (Virtual Local Area Network Identifier, virtual local area network identifier), as shown in the shaded message field in Table 1.
[0016]
[0017] Table 1 802.1Q-based VLAN frame format
[0018] With the continuous expansion of the network scale, 4K VLAN IDs can no longer meet the current networking applications. In order to achieve more user access, various manufacturers have launched their own solutions, and QinQ is one of them. QinQ is to add an 802.1Q tag in addition to the original 802.1Q tag, and use two layers of VLAN ID to identify a user, that is, 802.1Q in 802.1Q, and add a layer of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com