Safety access method of wireless metropolitan area network
A wireless metropolitan area network and secure access technology, applied in key distribution, can solve the problems of paralysis of the wireless metropolitan area network, low load capacity of base station BS, and increased computing burden of base station BS, so as to avoid resources, improve load capacity, avoid denial of service) attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The typical wireless metropolitan area network technology is IEEE802.16 standard at present. Therefore, the present invention will be described below taking IEEE802.16 as an example, however, the present invention is not limited to be based on the IEEE802.16 standard, and the present invention is applicable to wireless metropolitan area network technologies including the IEEE802.16 standard.
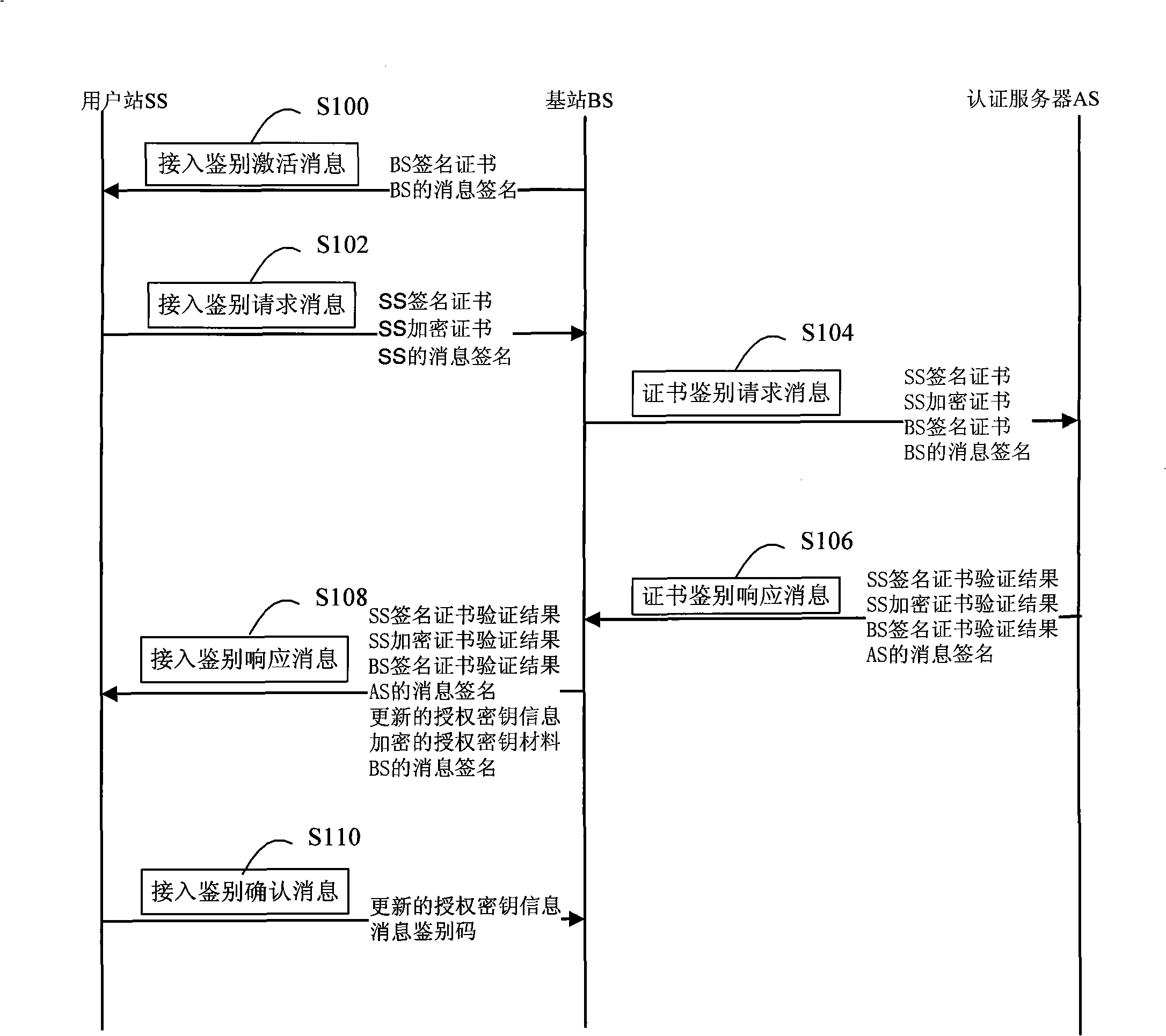
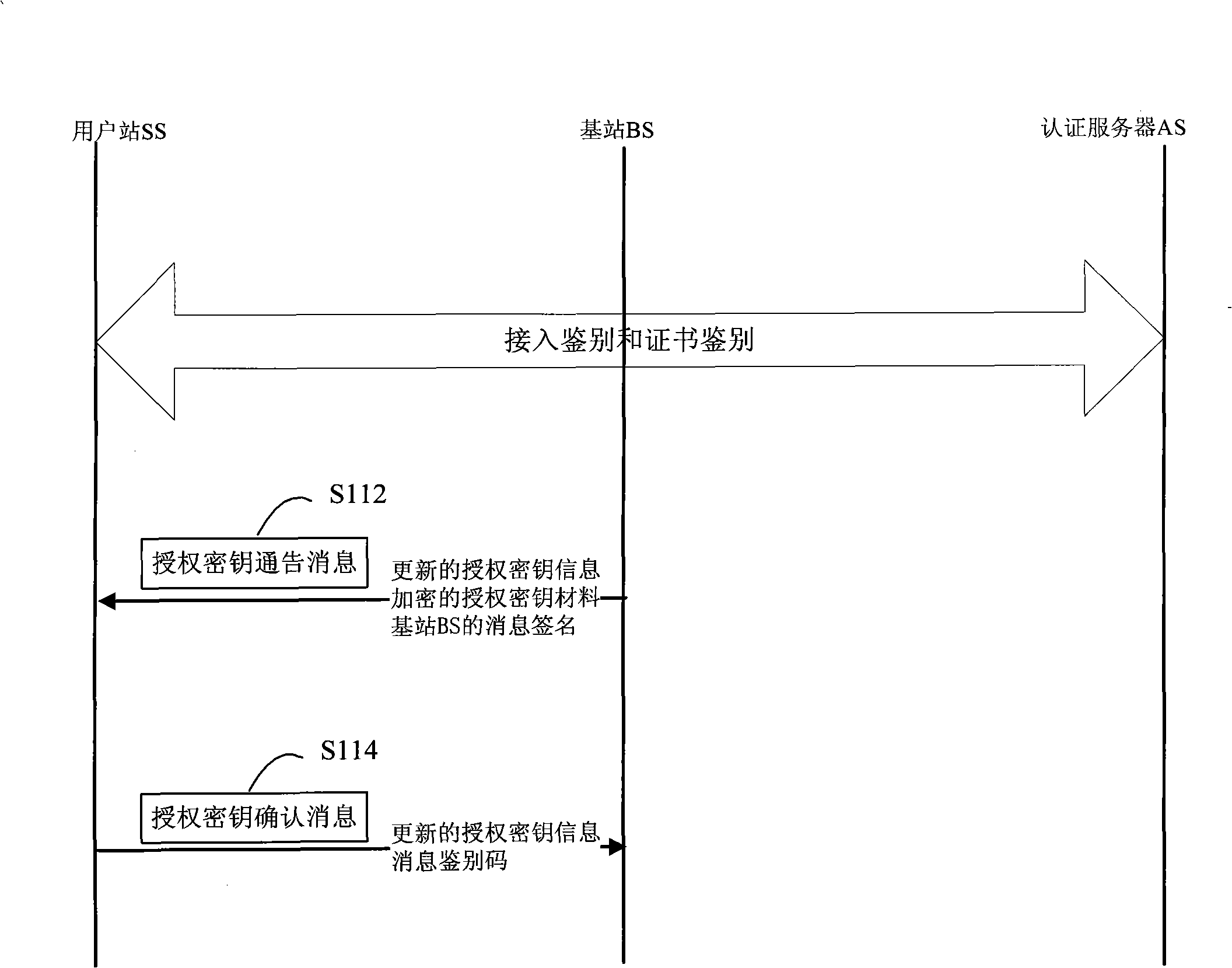
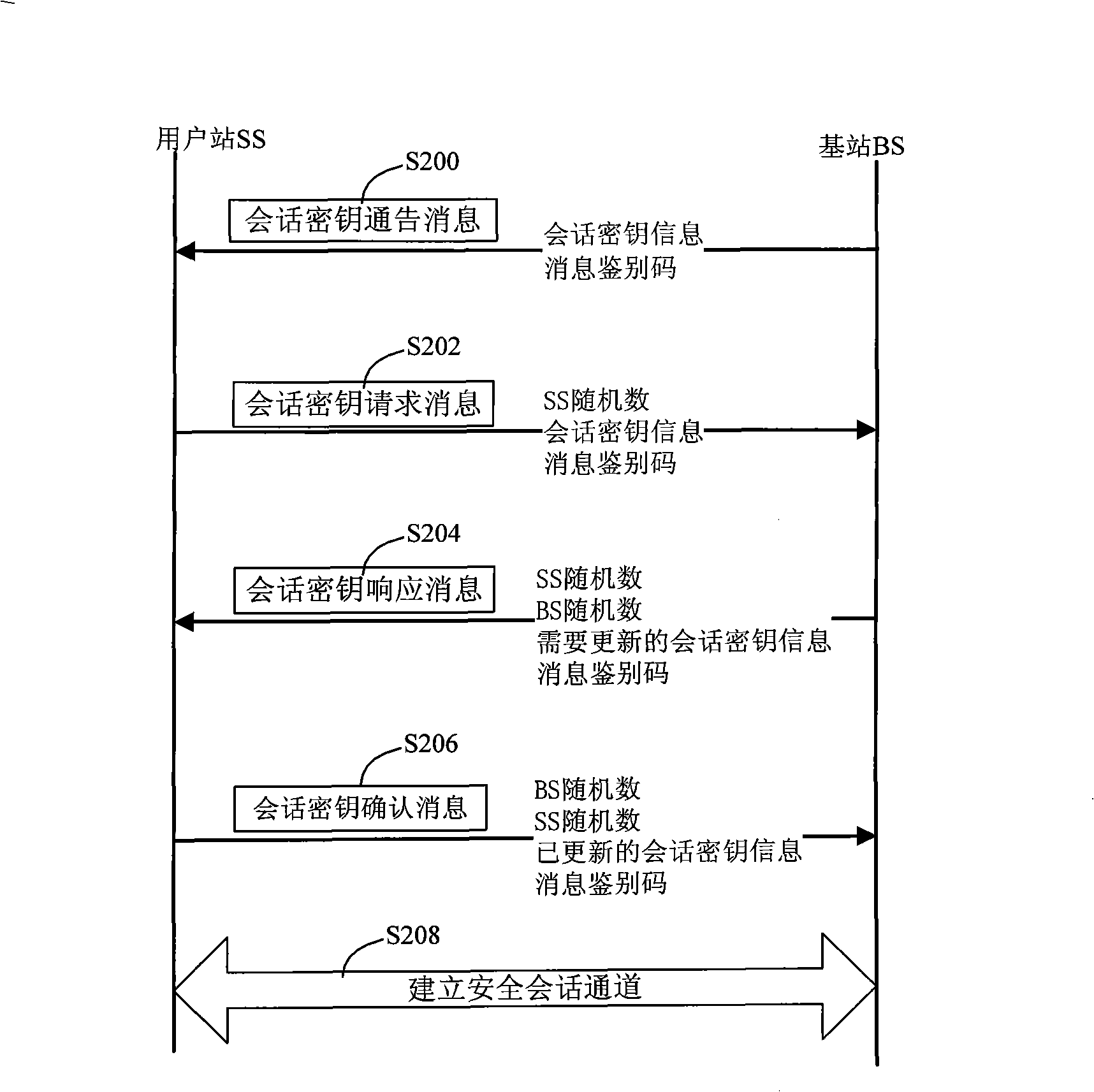
[0025] According to the IEEE802.16 standard, the communication process of the subscriber station SS and the base station BS in the wireless metropolitan area network includes steps such as synchronization, initial ranging, capability negotiation, authorization authentication, key negotiation, and registration. The present invention relates to the steps of authorization authentication and key agreement, that is, the safe access processing flow provided by the present invention is located after the capability negotiation of IEEE802.16 and before the registration step.
[0026] The s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com