Operating method of log system
An operation method and log technology, applied in the computer field, can solve problems such as no hook, uncontrollable, and inconvenient troubleshooting, and achieve the effects of saving resources, increasing controllability, and reducing call overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
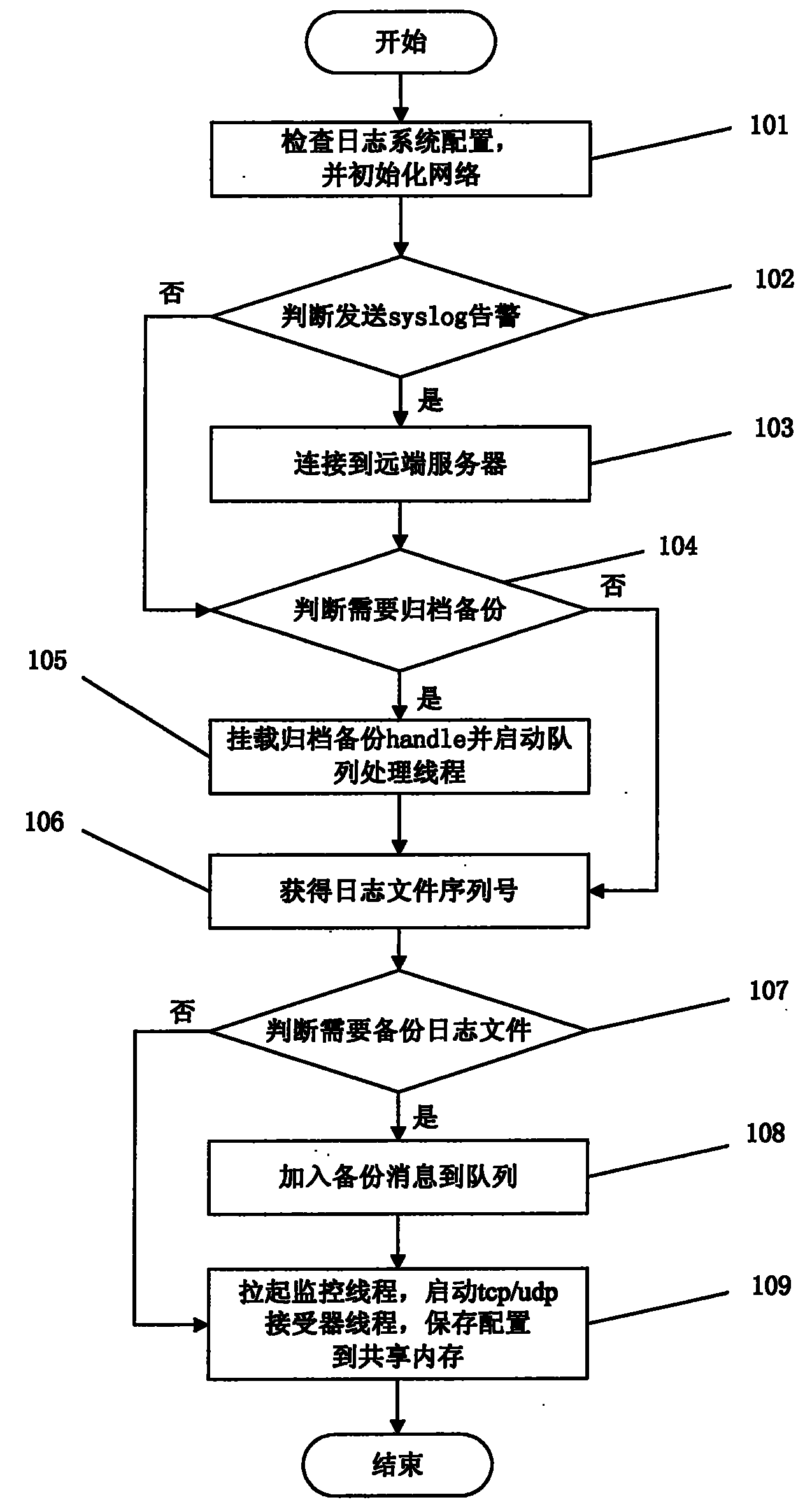
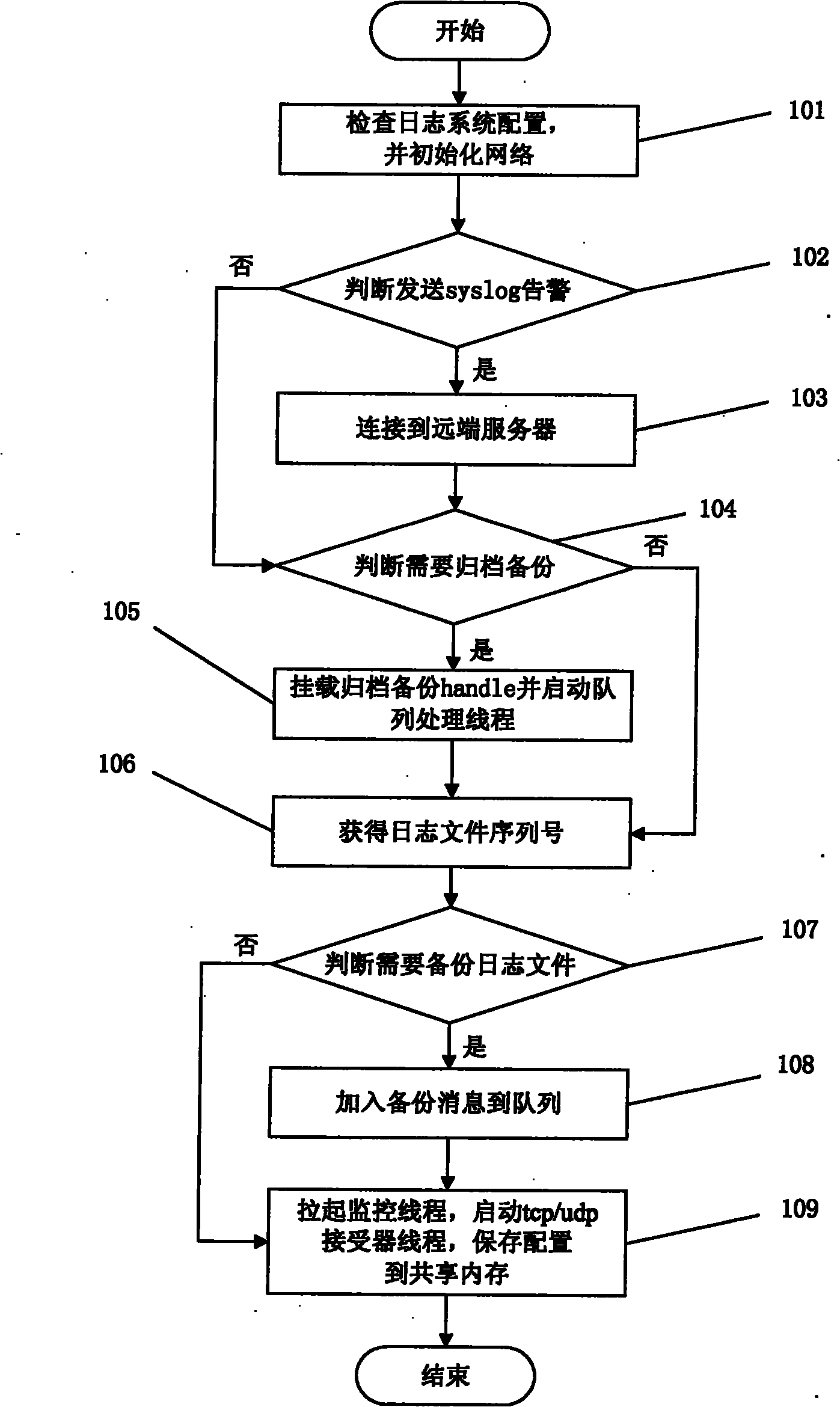
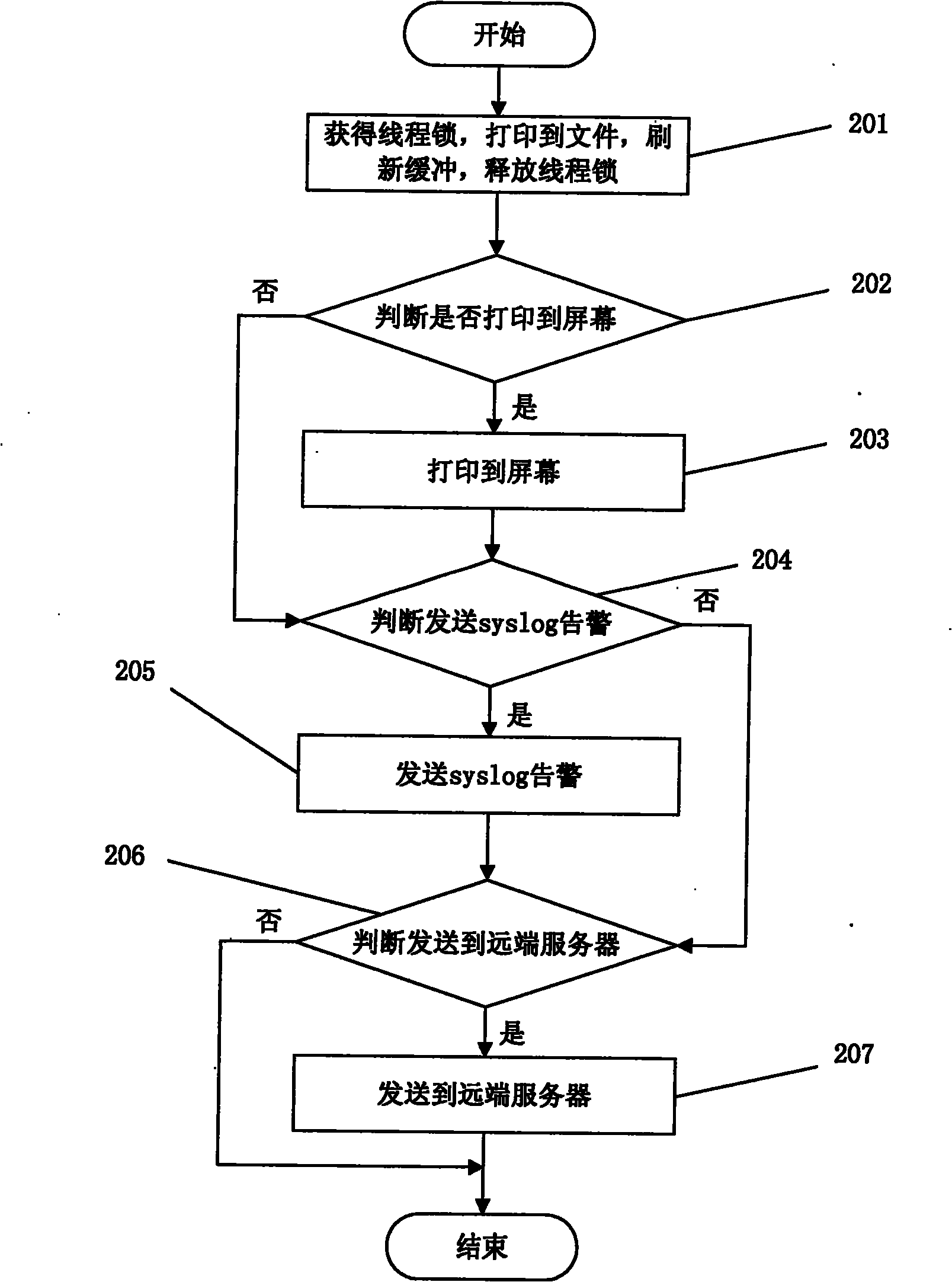
[0039] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and through specific implementation methods.
[0040] This log system is developed with C++, using the OOD design method, the interface is small and complete, the encapsulation is good, the members are as private as possible, and it has certain fault tolerance and intelligence. Easy to develop and easy to maintain. The log function borrows from the mainstream log system, and on this basis, it is simplified (removing the callback function, lexical analysis, and layout), and at the same time, it adds functions that it does not have (periodic backup, backup when the log file is switched, log when the system starts Backup; the log file generation cycle is more detailed, divided into years, months, weeks, days, hours, and minutes; the log level is more detailed, subdivided from the common 5-level log to 8-level log, and is compatible with syslog; obj...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com