Method for enhancing information safety equipment verification safety
An information security and security technology, applied in the field of improving security in the process of obtaining authorization for information security equipment, can solve the problem of increasing the cost by several times or even dozens of times
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
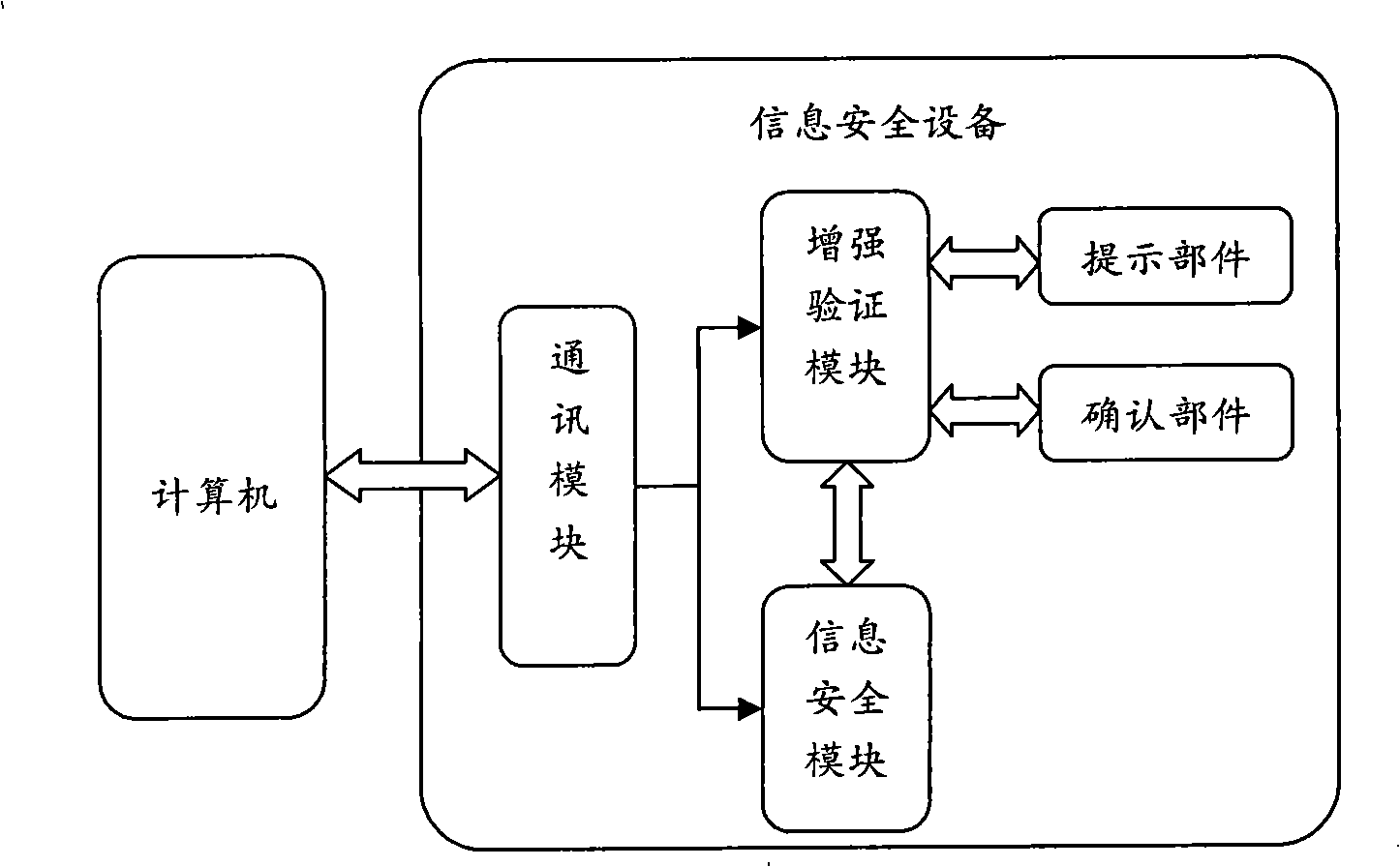
[0032] The information security module described in the present invention is a cryptographic algorithm module in a general information security device, such as using an RSA key for decryption and digital signature. This section is a mature technology in the industry. The communication between the communication module and the computer software is, for example, a USB interface communication module, which is also a mature technology in information security equipment.
[0033] Concrete working method of the present invention is:
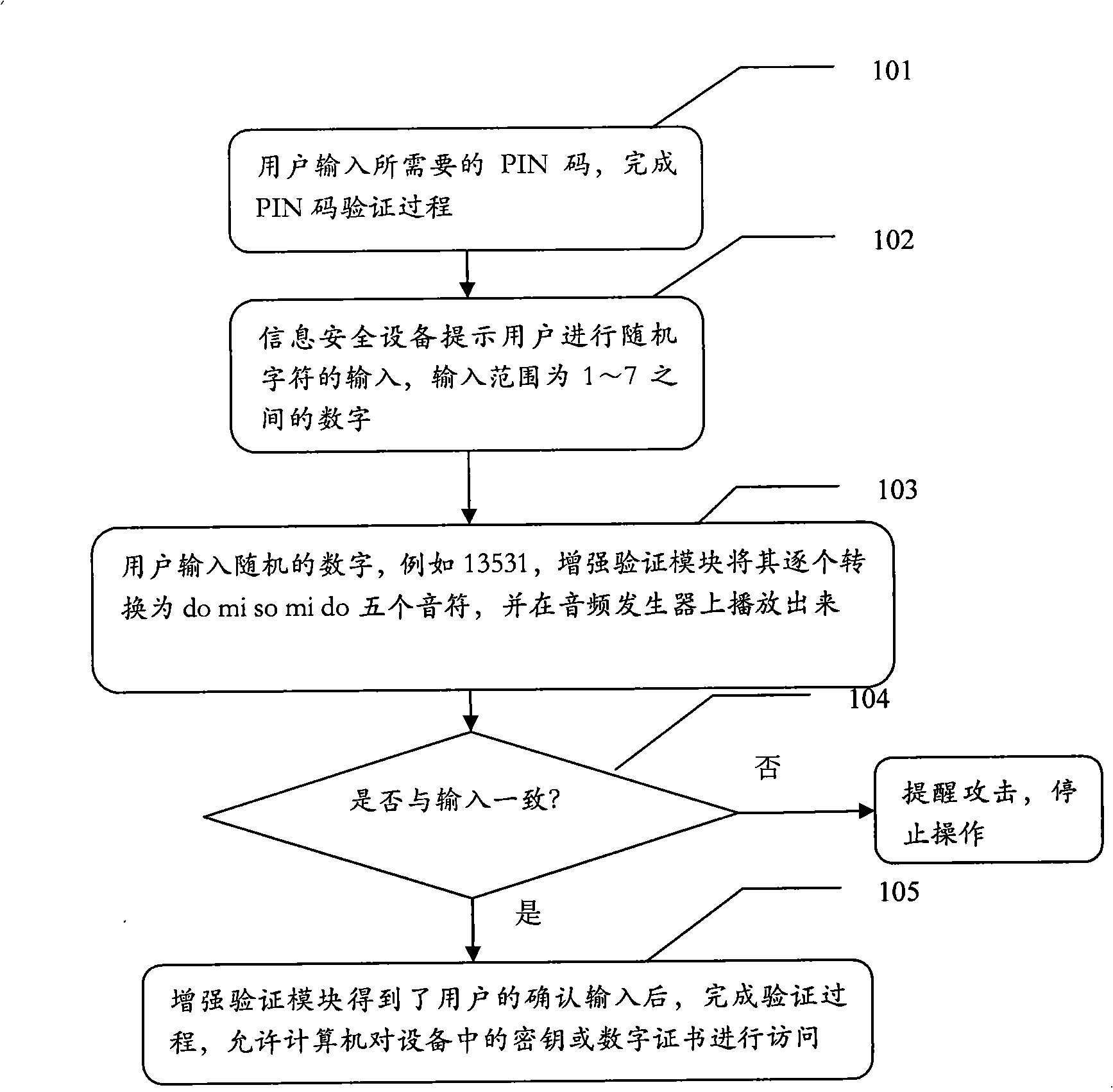
[0034] A: The user enters a random character string on the computer;
[0035] B: The computer transmits the character string input by the user to the enhanced verification module of the connected information security device, and displays it on the prompting part;
[0036] C: The user verifies the information on the pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com