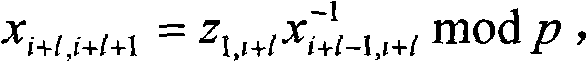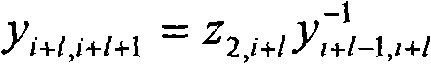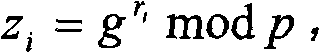Group cipher key generating method, system and apparatus
A group key and device technology, which is applied in the field of network communication, can solve the problems of large storage space, large amount of calculation, and high bandwidth requirements, and achieve the effect of small storage space, fast calculation speed, and low network bandwidth requirements
Inactive Publication Date: 2008-10-22
HUAWEI TECH CO LTD +1
View PDF0 Cites 24 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
In order to solve the problem that the group key negotiation method in the prior art has a large amount of calculation, takes up a large storage space, and requires high bandwidth, the embodiment of the present invention provides a method, system and device for generating a group key
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment 1
Embodiment 2
Embodiment 3
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
In order to solve the problems such as large amount of calculation, more storage space occupation and higher requirements to band width in a group key negotiation method in the prior technology. The invention provides a method of generating a group of secret keys as well as a system and equipment carrying out the method, which belongs to the network communication field. The method comprises the steps that: group members forms a logic ring, system parameters are selected and each member and a neighboring member generate a secret key and an intermediate value shared by the two members and issue the intermediate value; secret keys of other members shared by two members are calculated according to all intermediate values received to generate a group of keys. The system comprises a logic ring forming module, a system parameter selecting module, a message receiving and transmitting module and a group key generating module. The equipment comprises a logic ring forming module, a system parameter selecting module, a D-H public key value calculating module, a shared key generating module, an intermediate value generating module, a message receiving and transmitting module and a group key generating module. The technology provided by the invention solves the problems in the prior technology and is easy to use.
Description
A method, system and device for generating a group key technical field The invention relates to the field of network communication, in particular to a method, system and equipment for generating a group key. Background technique The key to solve group communication security by using multi-party shared group key is the generation and distribution of the group key, which must be exclusive, that is, non-group members cannot obtain the group key. The existing group key management technologies can be divided into two categories: centralized management and distributed negotiation. Compared with the centralized management type, the distributed negotiation group key management technology is suitable for use in occasions where a central control node cannot or cannot be established, such as military Adhoc networks, P2P networks, and confidential video conferences. The existing group key agreement schemes are all based on the discrete logarithm problem over finite fields. The Burmes...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Applications(China)
IPC IPC(8): H04L9/08H04L9/30H04L29/06
Inventor 许春香钟欢刘亚
Owner HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com