Method and system for generating cryptographic key
A key generation and key technology, applied in the field of communication, to achieve the effect of strengthening security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
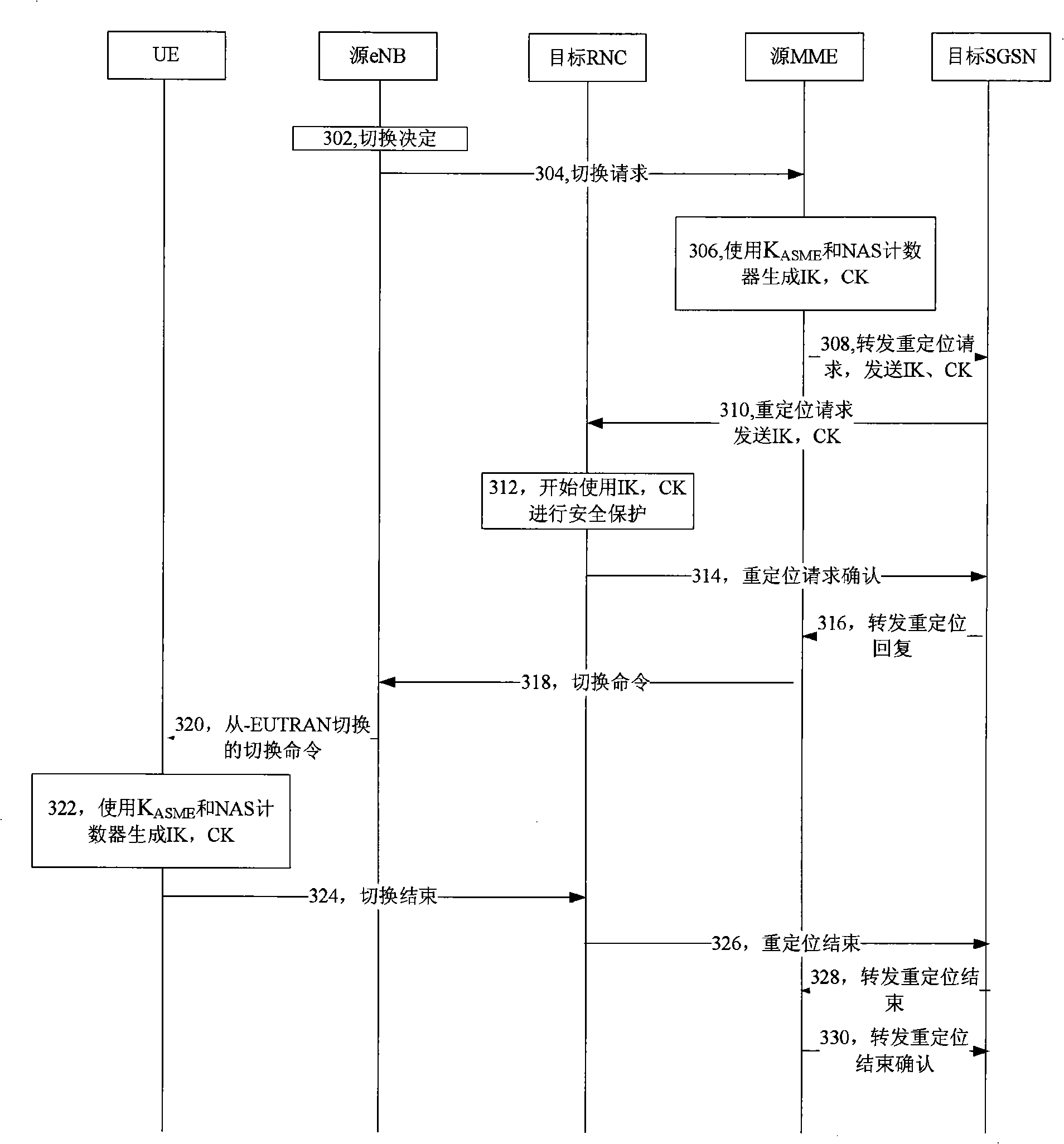
[0040] image 3 It is a signaling flowchart of a key generation method according to Embodiment 1 of the present invention. This embodiment shows a flowchart of a key generation method for UE handover from E-UTRAN to UTRAN, including the following steps:
[0041] Step 302, the source eNB makes a handover decision.
[0042] Step 304, the source eNB sends a handover request to the source MME.
[0043] Step 306, after receiving the handover request, the source MME uses K ASME And NAS counter, generate IK, CK.
[0044] Step 308, the source ME forwards the relocation request to the target SGSN, and sends IK and CK at the same time.
[0045] Step 310, the target SGSN sends a relocation request to the target RNC (Radio Network Controller), and at the same time sends IK and CK.
[0046] Step 312, the target RNC starts to use IK and CK.
[0047] Step 314, the target RNC sends a relocation request confirmation to the target SGSN.
[0048] Step 316, the target SGSN forwards the relo...
Embodiment 2
[0058] Figure 4 It is a signaling flowchart of a key generation method according to Embodiment 2 of the present invention, and this embodiment shows a signaling flowchart of a key generation method according to a preferred embodiment of the present invention. Such as Figure 4 As shown, this embodiment shows a flowchart of a key generation method for UE handover from E-UTRAN to GERAN, and this embodiment includes:
[0059] In step 402, the source eNB initiates a handover decision.
[0060] Step 404, the source eNB sends a handover request to the source MME.
[0061] Step 406, the source MME uses K ASME and the value of the NAS counter generate IK, CK.
[0062] Step 408, the source MME forwards the relocation request to the target SGSN, and sends IK and CK to the target SGSN at the same time.
[0063] Step 409, the target SGSN uses IK, CK to generate Kc.
[0064] In step 410, the target SGSN sends a packet domain switching request to the target BSS, and sends Kc at the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com