Method used in key consultation of USB KEY audio ciphering and deciphering device
A key negotiation, encryption and decryption technology, which is applied in the field of key negotiation of USBKEY audio encryption and decryption devices, can solve problems such as adverse effects, network call monitoring, and encryption security cannot be guaranteed, so as to improve anti-destructive capabilities and ensure encryption strength Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
[0025] The USB KEY audio device of the present invention is connected with the host computer.
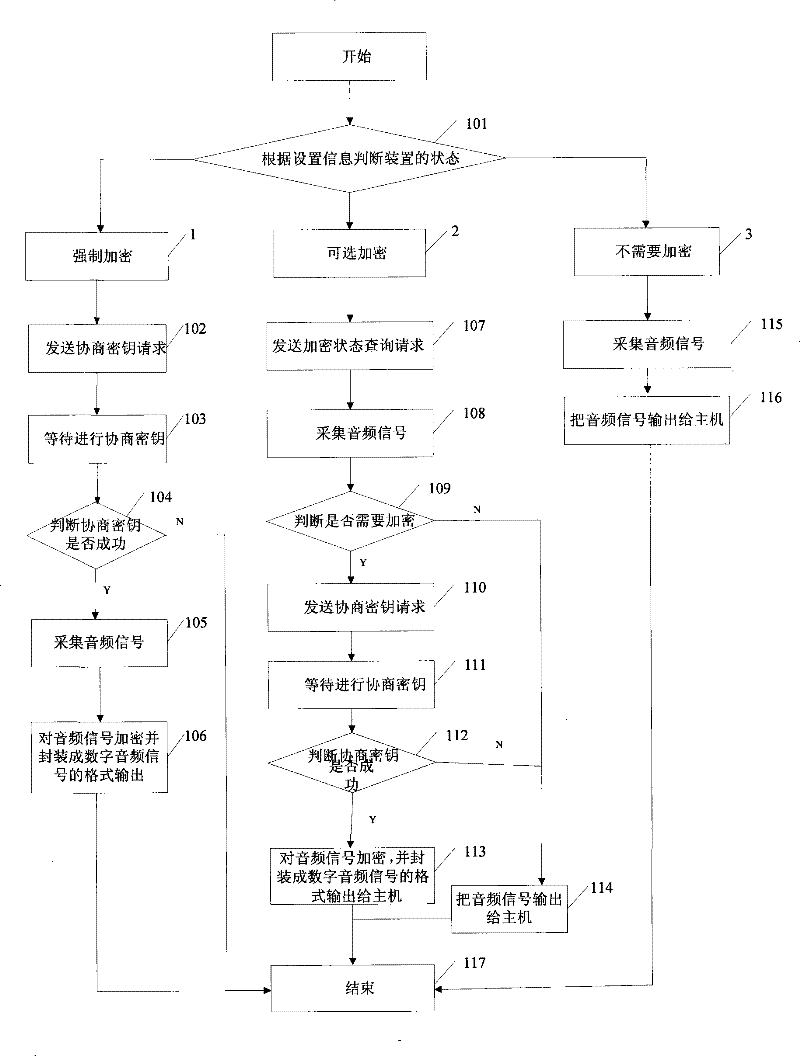
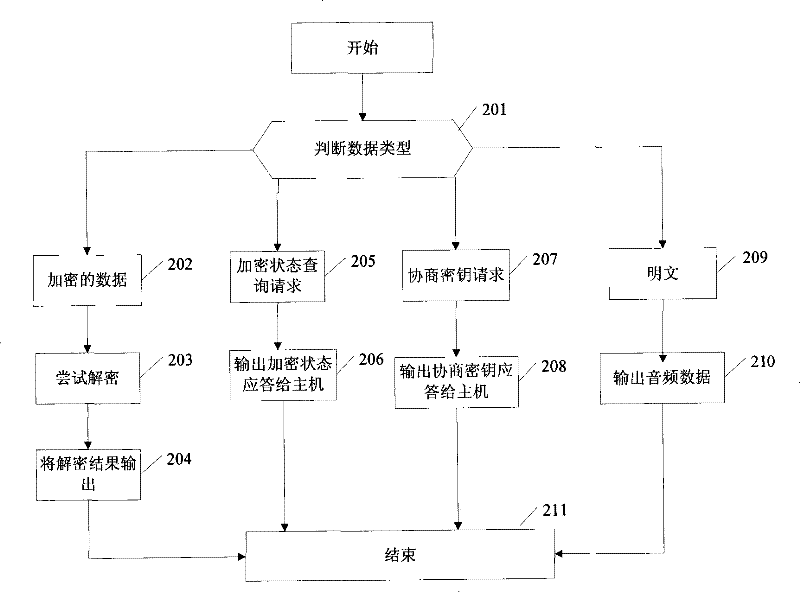
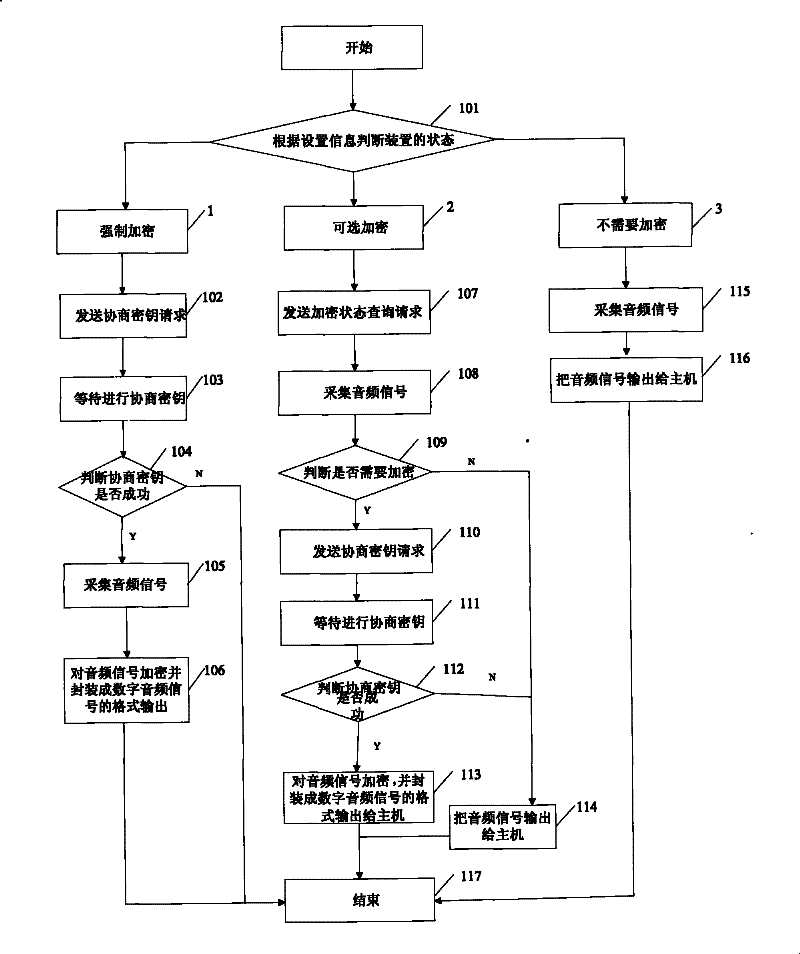
[0026] In the solution provided by the present invention, the existing USB KEY audio device is improved, and three modes can be manually set on the device: mandatory encryption, optional encryption and no encryption. A key and algorithm for encrypting and decrypting data during negotiation, a random number generation algorithm and various algorithms for encrypting and decrypting audio signals are provided in the device. In particular, the algorithm used in the negotiation can be a symmetric algorithm or an asymmetric algorithm, that is to say, the strength is higher, and the algorithm for encrypting and decrypting the audio signal should be a symmetric algorithm, and each algorithm has an identification ID.
[0027] figure 1 Among them, when preparing to c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com