Status detection method, apparatus and system of dynamic host configuring protocol
A dynamic host configuration and status detection technology, applied in the field of communication, can solve the problem that the DHCP endpoint cannot know the status of the peer, and achieve the effect of maintaining management and expanding application scenarios
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
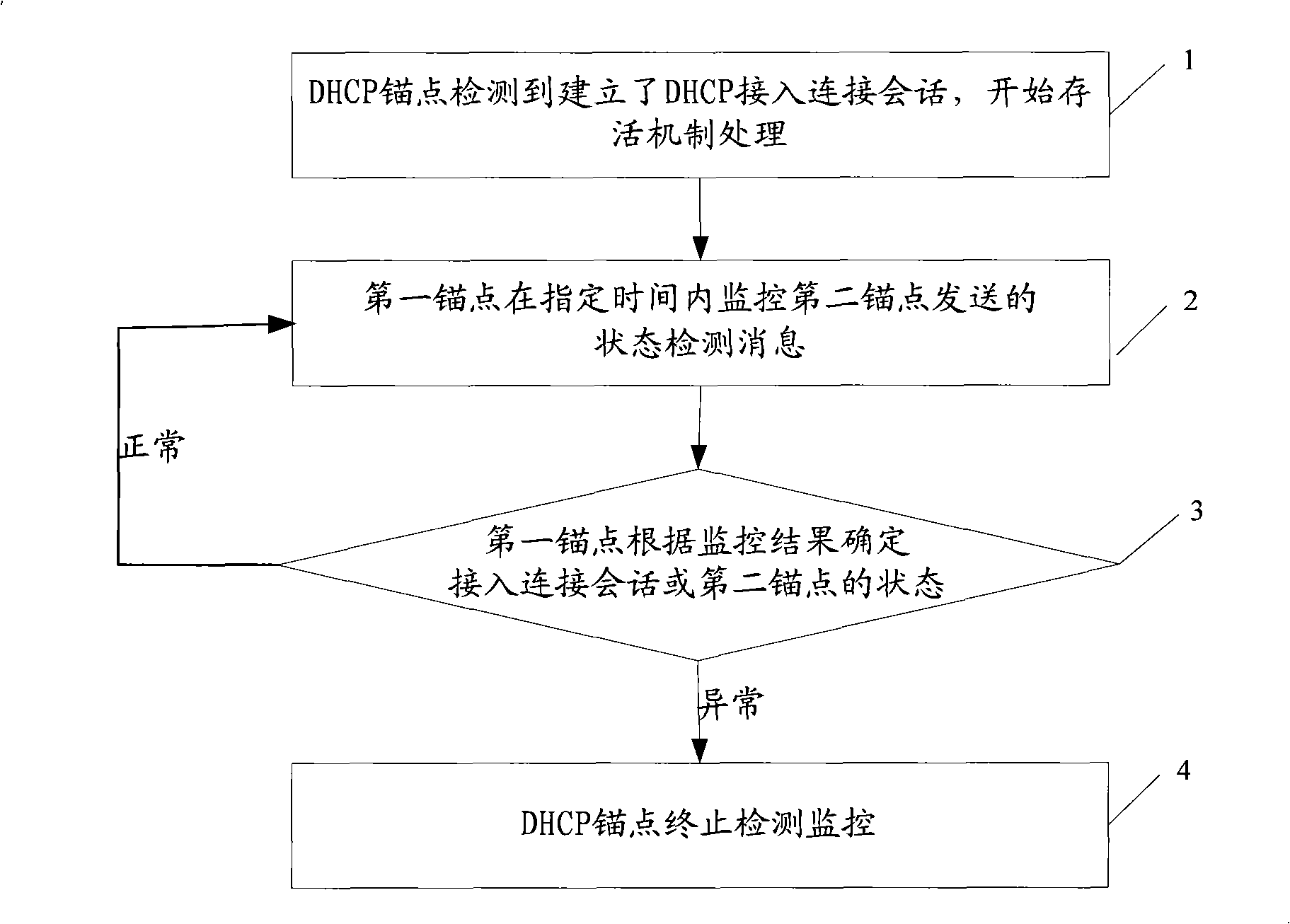
[0068] Embodiment 1 is that the DHCP anchor point at one end detects the state of the opposite end anchor point through a two-way message, that is, by sending a detection request message and receiving a detection response message to detect the state of the opposite end anchor point, which can be called single-ended two-way detection. Figure 4 For the specific flow chart, Figure 5 The schematic diagram of the corresponding process includes the following steps:
[0069] Step 1: The user terminal accesses the network through DHCP, and establishes a DHCP access connection session;
[0070] The user terminal obtains the right to access the network through the access authentication by using the DHCP, and / or obtains the network configuration parameters including the network address by using the DHCP.
[0071] Step 2: The DHCP anchor with the survival mechanism detects that the user terminal has completed access to the network through DHCP (after the access connection session is es...
Embodiment 2
[0084] Embodiment 2 is that the receiver’s DHCP anchor judges the status of the peer end by receiving the sender’s anchor detection message, which can be called single-ended unidirectional detection. After the detection message of the anchor point of the party, if it is judged that the detection message is valid, indicating that the state of the anchor point of the sender is online, the T3 duration indication is set, and the next round of detection is continued. Specific steps such as Figure 6 As shown, the corresponding schematic diagram of the process is shown in Figure 7 shown, including the following steps:
[0085] Step 1: The user terminal accesses the network through DHCP, and establishes an access connection session;
[0086] The user terminal obtains the right to access the network through the access authentication by using the DHCP, and / or obtains the network configuration parameters including the network address by using the DHCP.
[0087] Step 2: The first anc...
Embodiment 3
[0099] Embodiment 3 is a method for both ends to mutually confirm the state of the opposite end. By combining Embodiment 1 and Embodiment 2, after one end receives the other end detection request message, if the message is valid, it can be determined that the other end is online, then Sending a detection response message, after the other end receives the detection response message, if the message is valid, it can determine that the end that sent the response message is online, which can be called double-ended one-way detection. The specific steps are not repeated here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com