Safety authentication method for service-feeding proxy gateway to service-feeding initiator
A push service and agent gateway technology, which is applied in the directions of public key, network connection, user identity/authority verification of secure communication, etc., can solve problems such as prolonging data transmission and processing time, difficulty, and complicated encryption negotiation process, etc., to achieve Ease of grasp and use, increased safety effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] Below in conjunction with accompanying drawing and embodiment the present invention will be described in further detail:
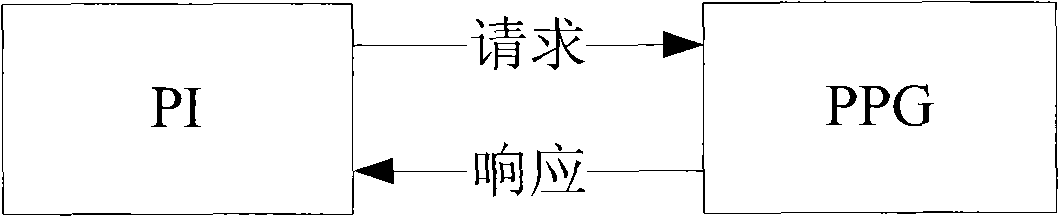
[0028] Such as figure 1 As shown in the interaction diagram between PI and PPG in the present invention, PI sends a PUSH HTTP request, and PPG returns a response message to PI after authentication to inform PI whether the authentication is successful.
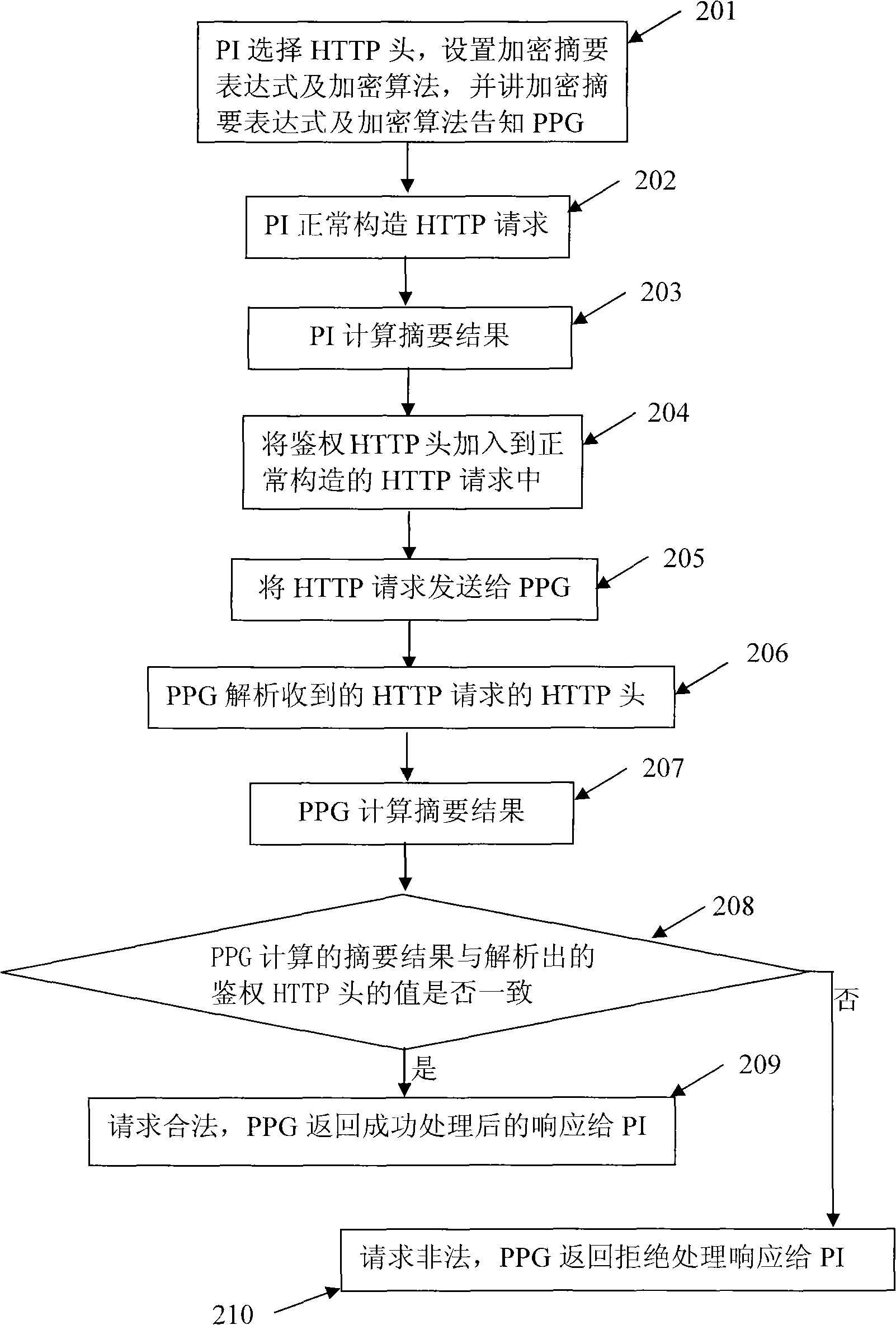
[0029] Such as figure 2 Shown, PPG described in the present invention comprises the following steps to the security authentication method of PID:
[0030] Step 201: PI selects the required HTTP header for encryption, and sets an encryption summary expression and an encryption algorithm. In this embodiment, the MD5 algorithm is selected, and the encryption summary expression and the encryption algorithm are notified to PPG;
[0031] The principle of selecting the HTTP header required for encryption in this step is:
[0032] Do not select the HTTP header used for authentication; do not select the H...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com