Method, equipment and network system for synchronizing clock
A technology of clock synchronization and clock server, which is applied in the field of communication, can solve the problems of being vulnerable to attacks and the difficulty of sharing keys to ensure security, so as to achieve the effect of not being easy to attack and improving security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
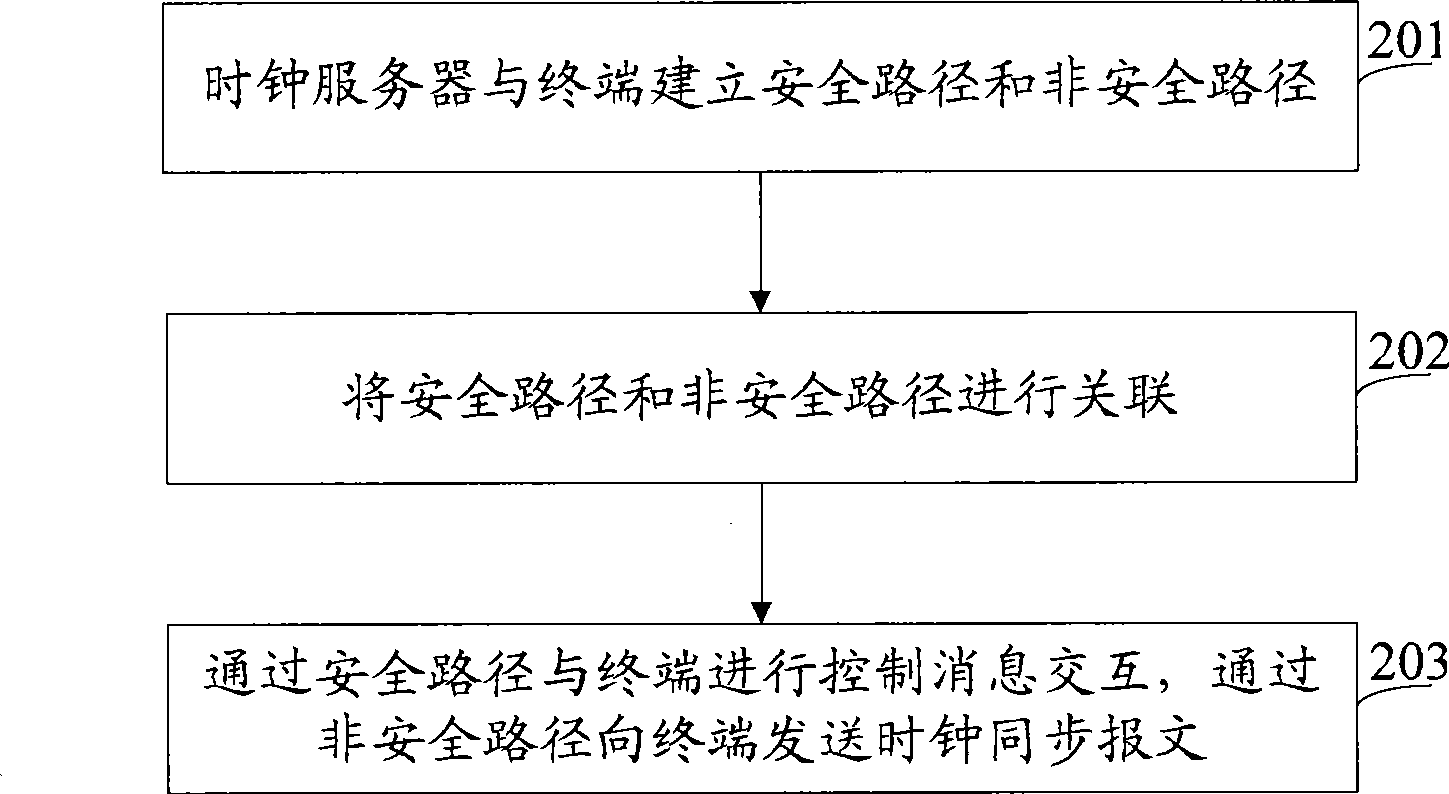
[0111] In this embodiment, when the clock server is deployed in a trusted network and the home gateway is in routing mode, the clock synchronization message is transmitted between the terminal and the clock server through a non-secure path, and the control message is transmitted through a secure path. see Figure 5 , Figure 5 Embodiment 1 of the present invention provides a schematic flowchart of transmitting a clock synchronization message through a non-secure path and a control message through a secure path between a terminal and a clock server. Such as Figure 5As shown, the dotted line represents the change of the service message address when the terminal and the clock server transmit the clock synchronization message through the non-secure path; the solid line represents the change of the service message address when the terminal and the clock server control the message through the secure path. SIP means source IP, DIP means target IP; SPort means source port, DPort me...
Embodiment 2
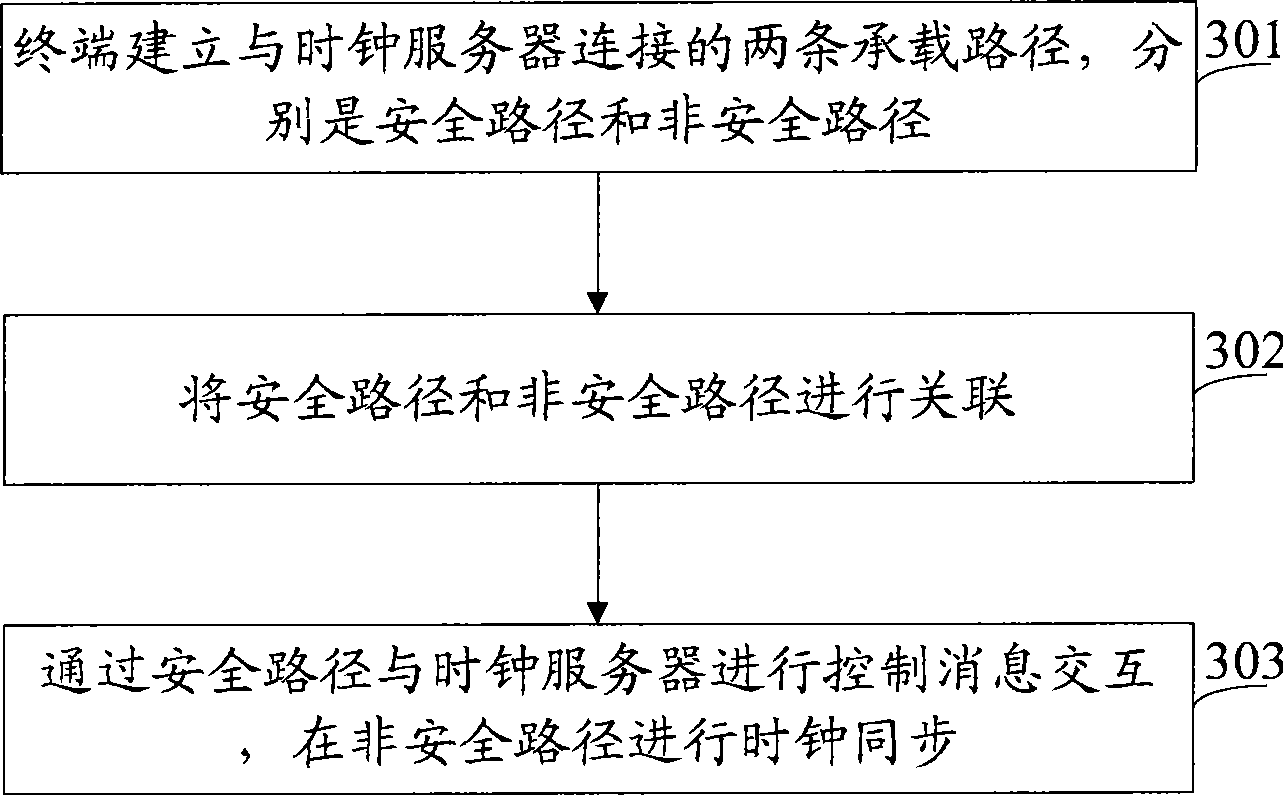
[0120] see Figure 6 , Figure 6 It is a schematic flowchart of a method for realizing clock synchronization security provided by Embodiment 2 of the present invention. Such as Figure 6 As shown, in this embodiment, the clock synchronization message is sent in a unicast manner, the dotted line indicates the process performed on the non-secure path, and the solid line indicates the process performed on the secure path. The process of this embodiment may include:
[0121] (1) The terminal establishes a security path with the security gateway, thereby realizing the establishment of a security path between the terminal and the clock server.
[0122] Wherein, the security path between the clock server and the terminal can be established by adding a logical interface, such as an IPSec tunnel; or by adding a physical link, such as a dedicated signaling link. In this embodiment, an IPSec tunnel is taken as an example to establish a secure path between the terminal and the clock s...
Embodiment 3
[0183] see Figure 7 , Figure 7 It is a flowchart of a method for implementing clock synchronization provided by Embodiment 3 of the present invention. Such as Figure 7 As shown, in this embodiment, the clock synchronization message is sent in a multicast manner, the dotted line indicates the process performed on the non-secure path, and the solid line indicates the process performed on the secure path. The process of this embodiment may include:
[0184] (1) The terminal establishes a security path with the security gateway, thereby realizing the establishment of a security path between the terminal and the clock server.
[0185] Wherein, the security path between the clock server and the terminal can be established by adding a logical interface, such as an IPSec tunnel; or by adding a physical link, such as a dedicated signaling link. In this embodiment, an IPSec tunnel is taken as an example to establish a secure path between the terminal and the clock server.
[018...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com