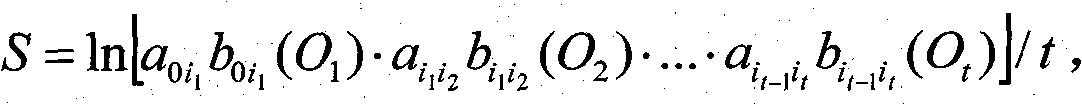Method for recognizing and tracking application based on keyword sequence
A keyword sequence and application identification technology, applied in special data processing applications, instruments, electrical digital data processing, etc., can solve problems such as tracking of limited protocol status
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described below in conjunction with the accompanying drawings.
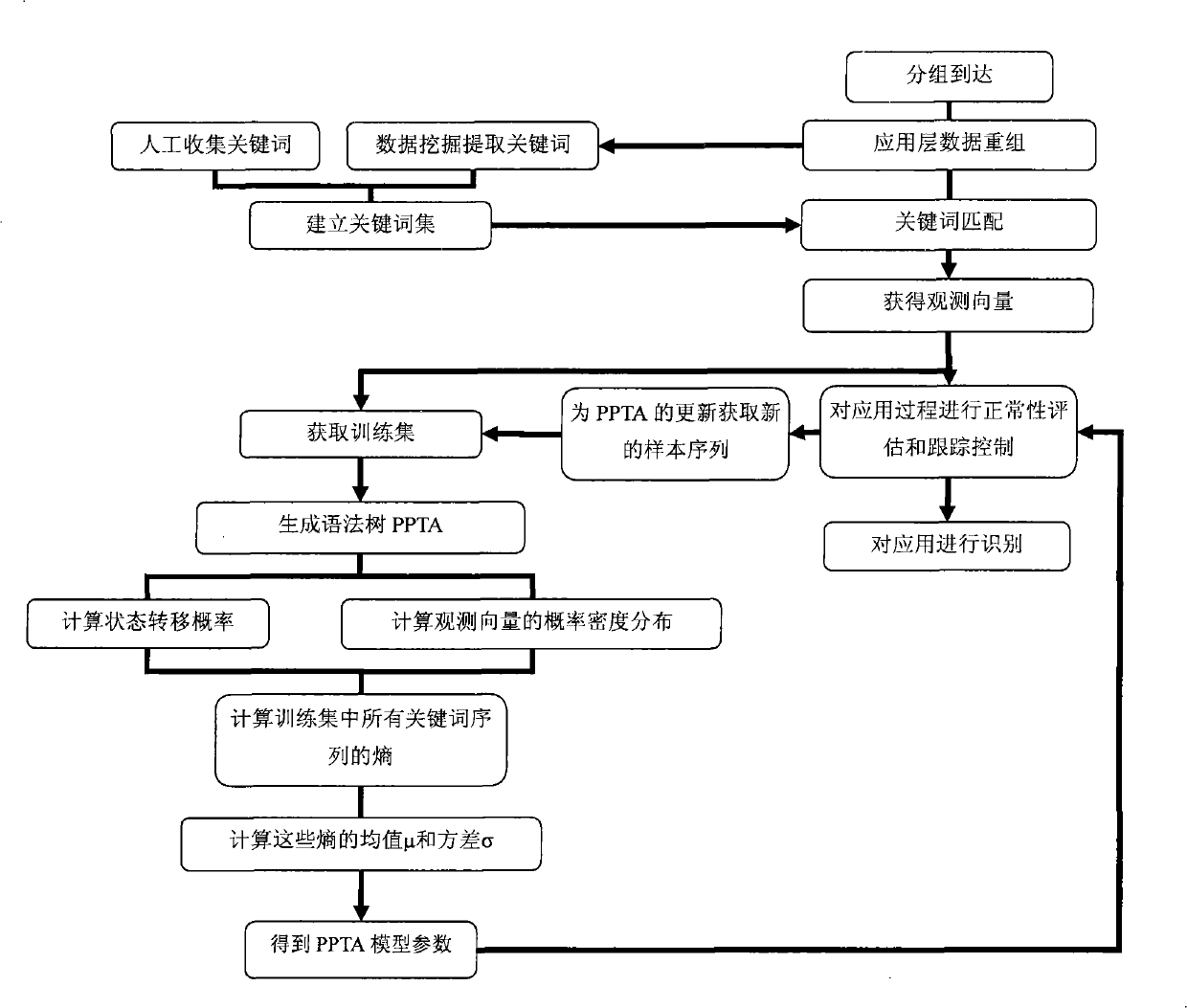
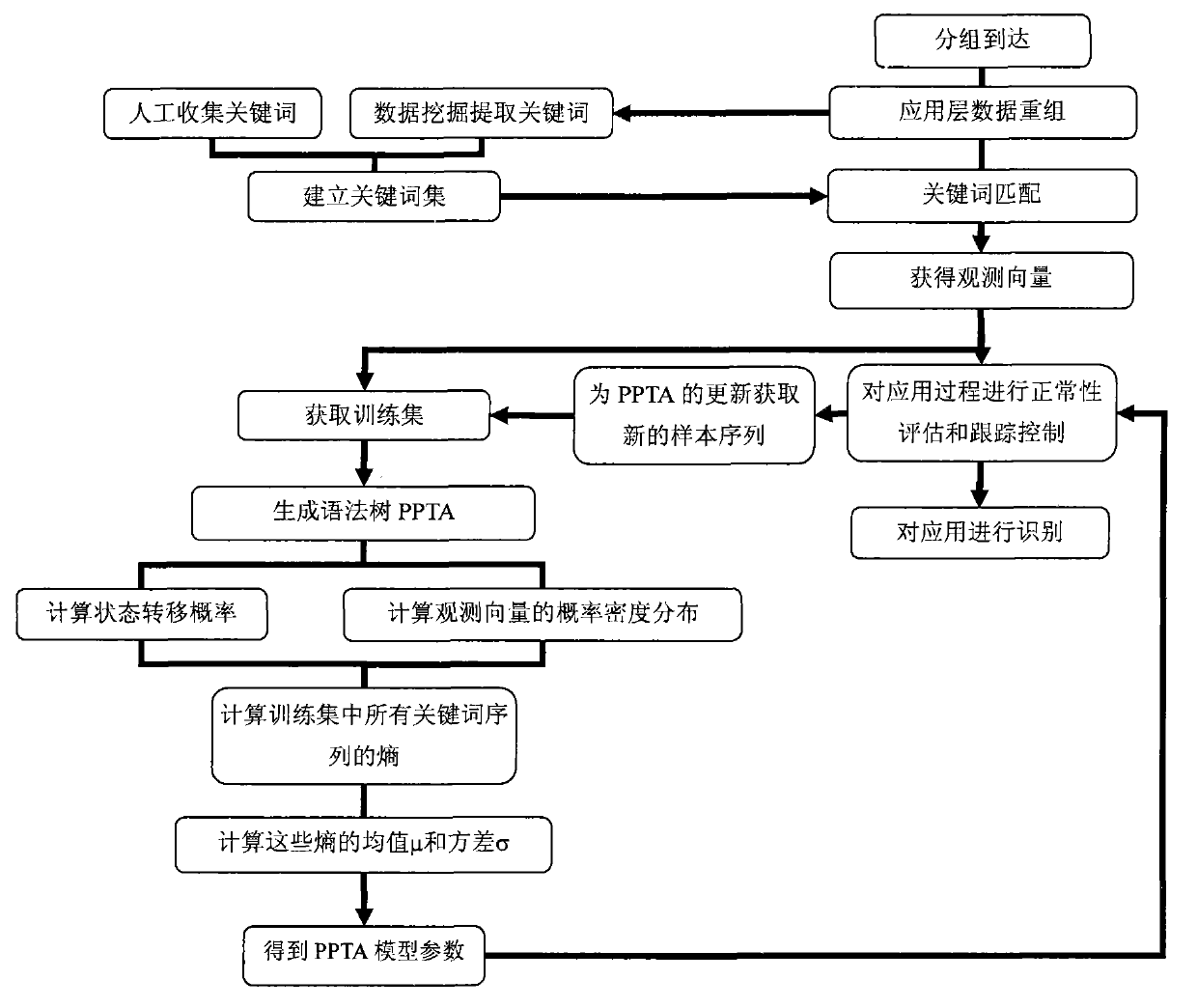
[0025] The invention is attached figure 1 As shown, the application is identified and the application process is tracked by collecting the keyword sequence of the application layer. Specific steps are as follows:
[0026] 1. Build a keyword set
[0027] The keyword may be a specific character, a character string, or a logical relationship between complex characters represented by a regular expression, or an identifiable character string feature in the application layer data. Methods for establishing keyword sets include:
[0028] a) Manual collection: By consulting standard documents or analyzing application layer data collected on the network, find keywords and key features of known application layer protocols to obtain keyword sets;
[0029] b) Automatic collection: through data mining of known or unknown application layer data collected on the network, frequentl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com