Script injection attack detection method and system
A script injection attack and detection method technology, which is applied in the field of computer networks, can solve problems such as unclean data cleaning, difficulties in deployment and implementation, and incorrect presentation of Web content, so as to improve detection accuracy, comprehensiveness and accuracy of detection , to overcome the effect of higher false positives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
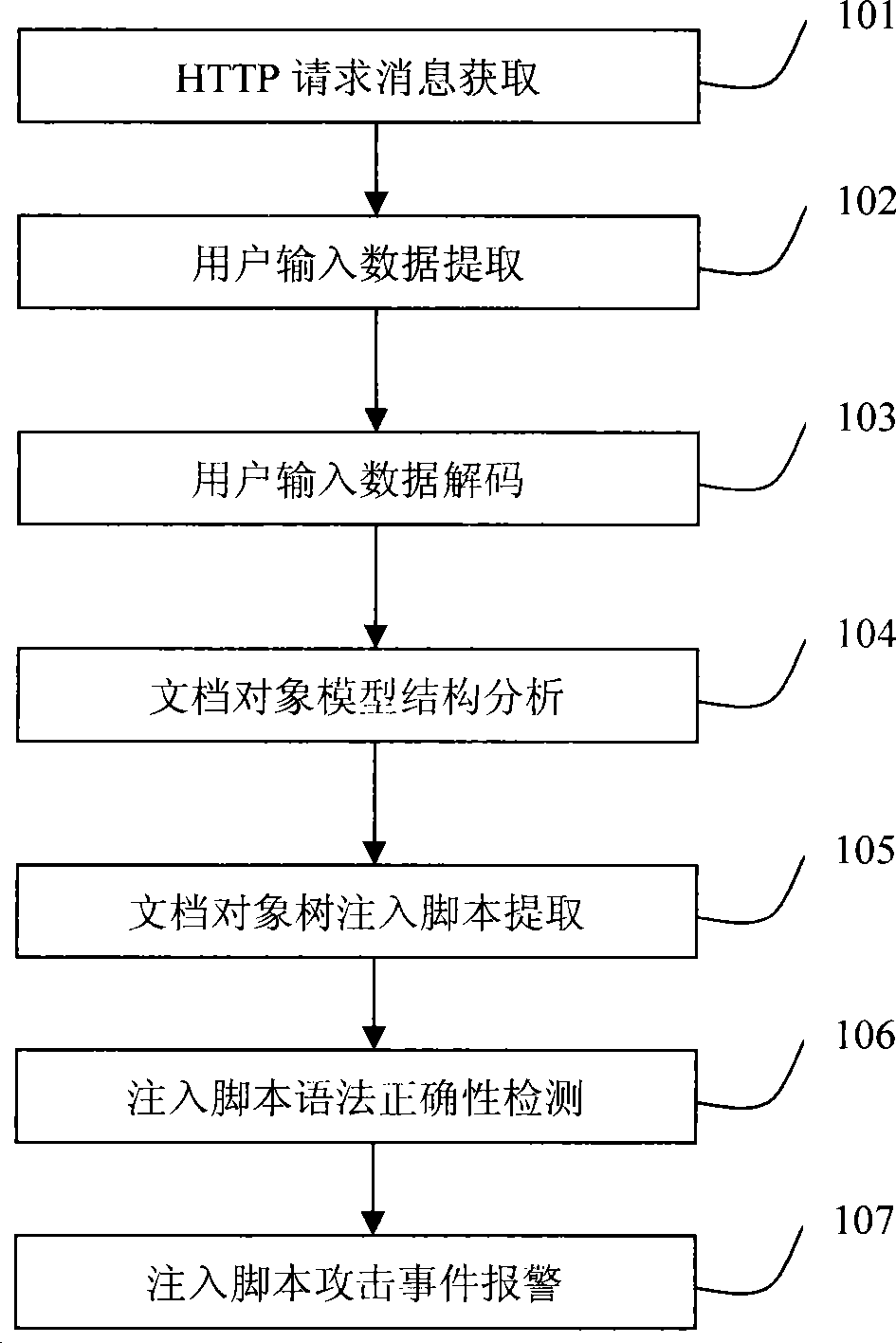
[0047]如附图1所示,本发明所述的脚本注入攻击检测方法包括HTTP请求消息获取101、从HTTP请求中提取用户输入数据102、对用户输入数据进行数据解码103、对解码后的用户输入数据进行文档对象模型结构分析104、从文档对象模型树中提取全面提取注入脚本105、对提取的注入脚本进行语法正确性检测106以及产生脚本注入攻击报警事件107等步骤。
[0048]本发明所述的HTTP请求消息获取步骤101包括但不限于以下三种方式:
[0049]1)HTTP代理方式;
[0050]2)Web服务器内嵌方式;
[0051]3)被动获取方式。
[0052]基于HTTP代理的HTTP请求获取方式包括:1)在Web用户网络端部署客户端HTTP代理来截获发往Web服务器的所有HTTP请求消息;2)在Web服务器端部署HTTP代理,截获发往其后台被保护Web服务器的所有HTTP请求。
[0053]基于Web服务器内嵌方式是指通过为特定Web服务器软件模块添加第三方插件方式来获取所有将被该Web服务器软件处理的HTTP请求消息。比如,对于Apache服务器软件,可通过Apache服务器软件开放的API接口开发第三方插件,在Apache服务器软件正式处理该HTTP请求前,通过扫描该HTTP请求来检测是否为一个脚本注入攻击;对于Microsoft的Internet信息服务器(InternetInformation Server,IIS),可以通过其开放的过滤器插件API编写一个拦截和检测HTTP请求消息的过滤插件。
[0054]被动方式获取HTTP请求消息是指以被动方式收集本网络内所有与HTTP协议相关的网络数据包,或者以被动方式收集流经监听设备的所有与HTTP协议相关的网络数据包,经网络数据包碎片处理、TCP数据流重组和HTTP协议分析等步骤获取HTTP请求消息。这种被动获取HTTP请求消息的模式比较适合于入侵检测系统(Intrusion Detection System,IDS)和入侵防御系统产品(Intrusion Protection System,IPS);
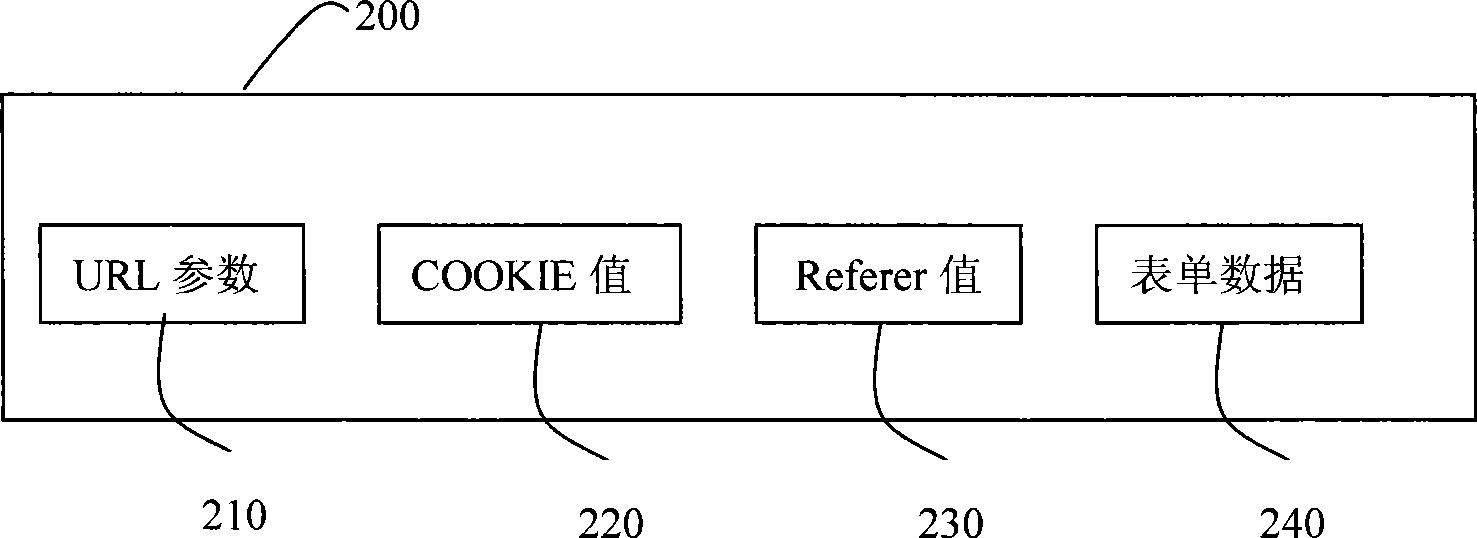
[0055]在获取到HTTP请求消息之后,下一步执行从HTTP请求消息中提取所有用户输入数据步骤。如附图2所示,本发明所述的脚本注入攻击检测方法在提取用户输入数据时是提取HTTP请求消息200中的以下4个协议域值:URL参数210、CO...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com