Command generation device
An instruction generation and instruction technology, applied in computer security devices, instruments, electronic digital data processing and other directions, can solve the problems of invalidation, tampering, tampering and verification processing, and achieve great effect, prevent illegal analysis and tampering. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0161] The processing system in Embodiment 1 according to the present invention will be described.
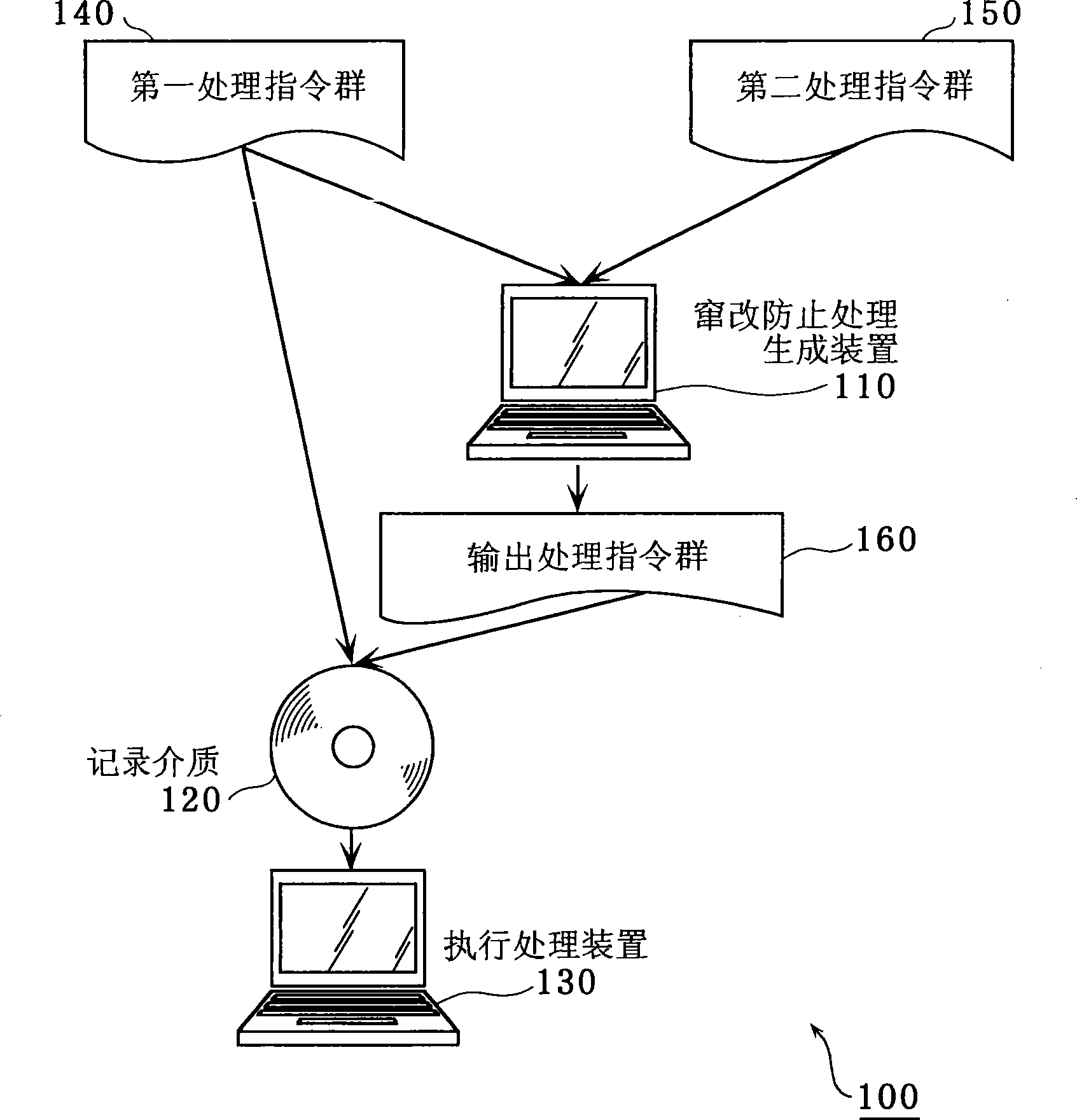
[0162] image 3 is a configuration diagram of the processing system in Example 1.
[0163] The processing system 100 in this embodiment includes a tamper prevention processing generating means (command generating means) 110 , and an execution processing means 130 .
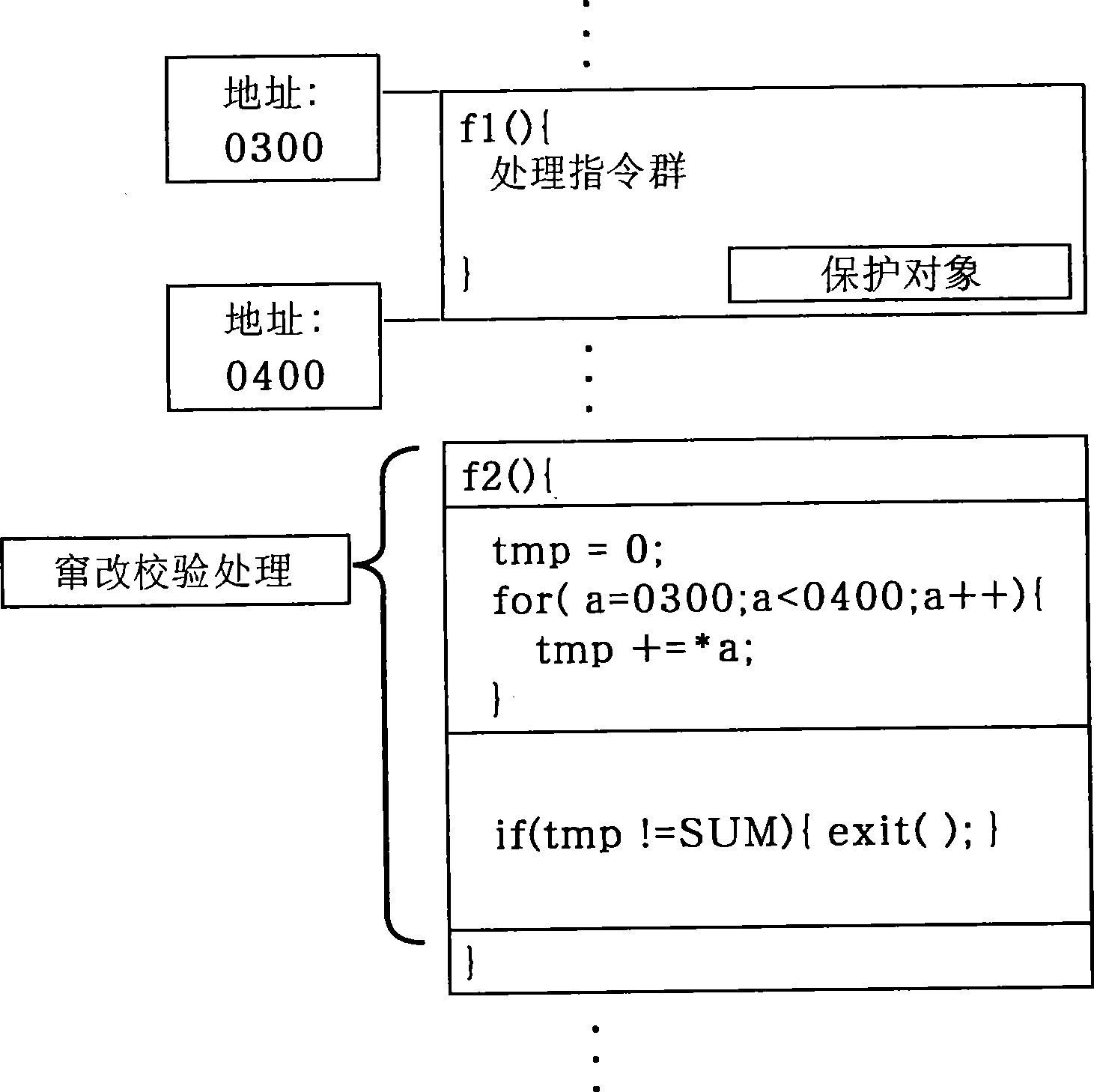
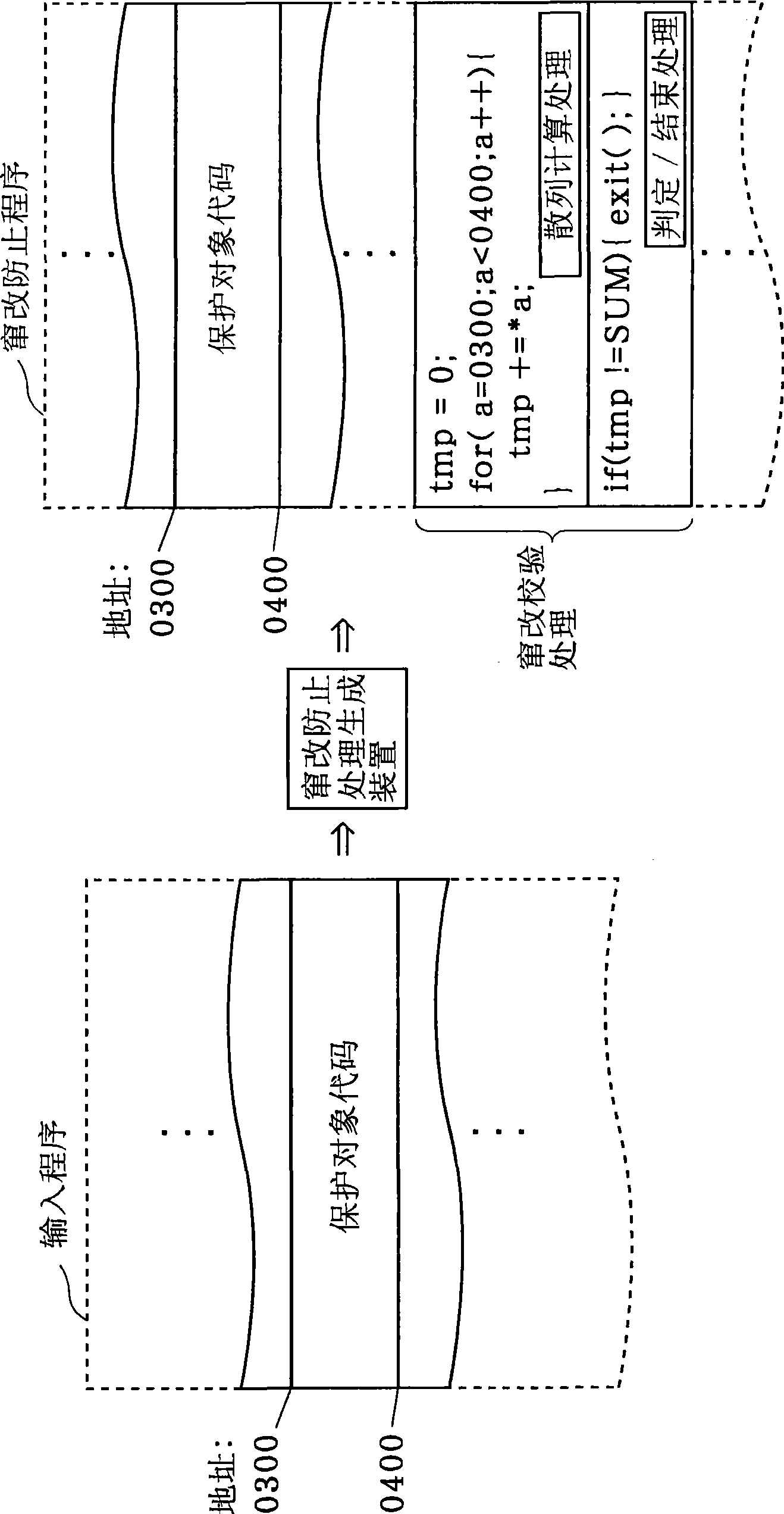
[0164] The anti-tampering processing generation device 110 is a device that generates a program that can reliably protect the protection target code, obtains the first processing command group 140 and the second processing command group 150 as the protection target code, and generates the output processing command group 160 . The anti-falsification processing generation device 110 is configured as an unreadable device, and generates an output processing instruction group 160 by making the second processing instruction group 150 difficult to read. Furthermore, unless otherwise specified, the instruction group in t...
Deformed example 1
[0342] In the above-mentioned embodiment, the variables that are the arguments of the first processing command group 140 are used as the variables for substituting values in the referenced variable value substituting processing command group 310 as they are, but the present invention is not limited thereto. The referenced variable value is substituted into the processing instruction group generation unit 240, the variable name used by the second processing instruction group 150 can be determined, and the following instruction group can be substituted into the processing instruction group 310 as the referenced variable value, the instruction group refers to: An instruction group that performs a process of substituting a random value into a variable with a variable name not used by the second processing instruction group 150 among the variable names held by the reference variable information holding unit 230 . With these configurations, it is possible to make the second process...
Deformed example 2
[0346] In the referenced variable value substitution process command group generation unit 240 , values to be substituted into the referenced variables are randomly determined, however, depending on the substituted value, it may be difficult to analyze the behavior of an unauthorized person. Therefore, the configuration of the falsification prevention process generation device 110 may be configured such that the user designates a substituted value or an estimated value.
[0347] The following instructions, in the Figure 5C Shown is the difficulty of the illegal parser's parsing behavior when the value of the referenced variable "encryptedData" is "0xF022", and the difficulty of the parsing behavior when the value of the referenced variable "encryptedData" is "0xF0001" A specific example of the difference in the degree of difficulty of the analysis behavior of an illegal analysis person.
[0348] Such as Figure 5C As shown, if the value substituted into the referenced var...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com