Ghash method and structure for parallel computation in Galois counter mode
An arithmetic method, Galois's technology, applied in the direction of encryption device with shift register/memory, etc., can solve the problem of high hardware cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
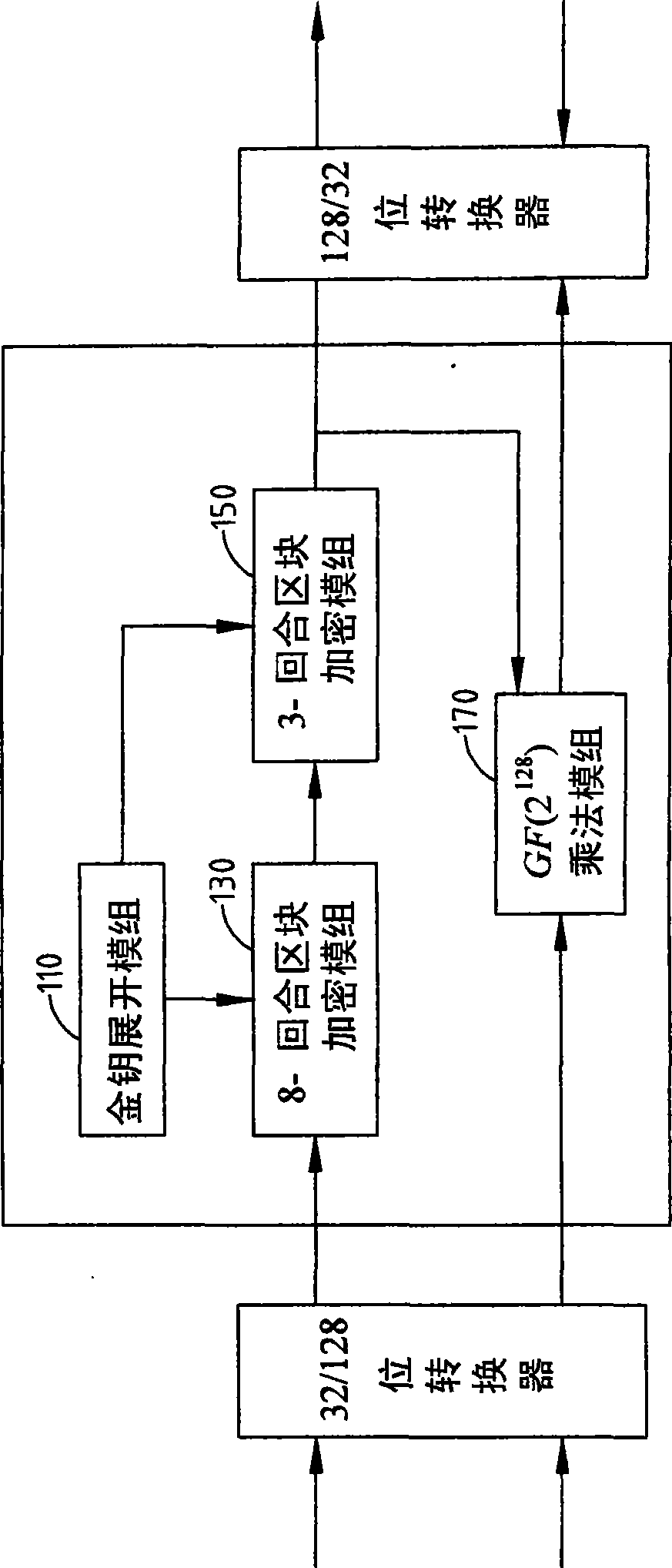
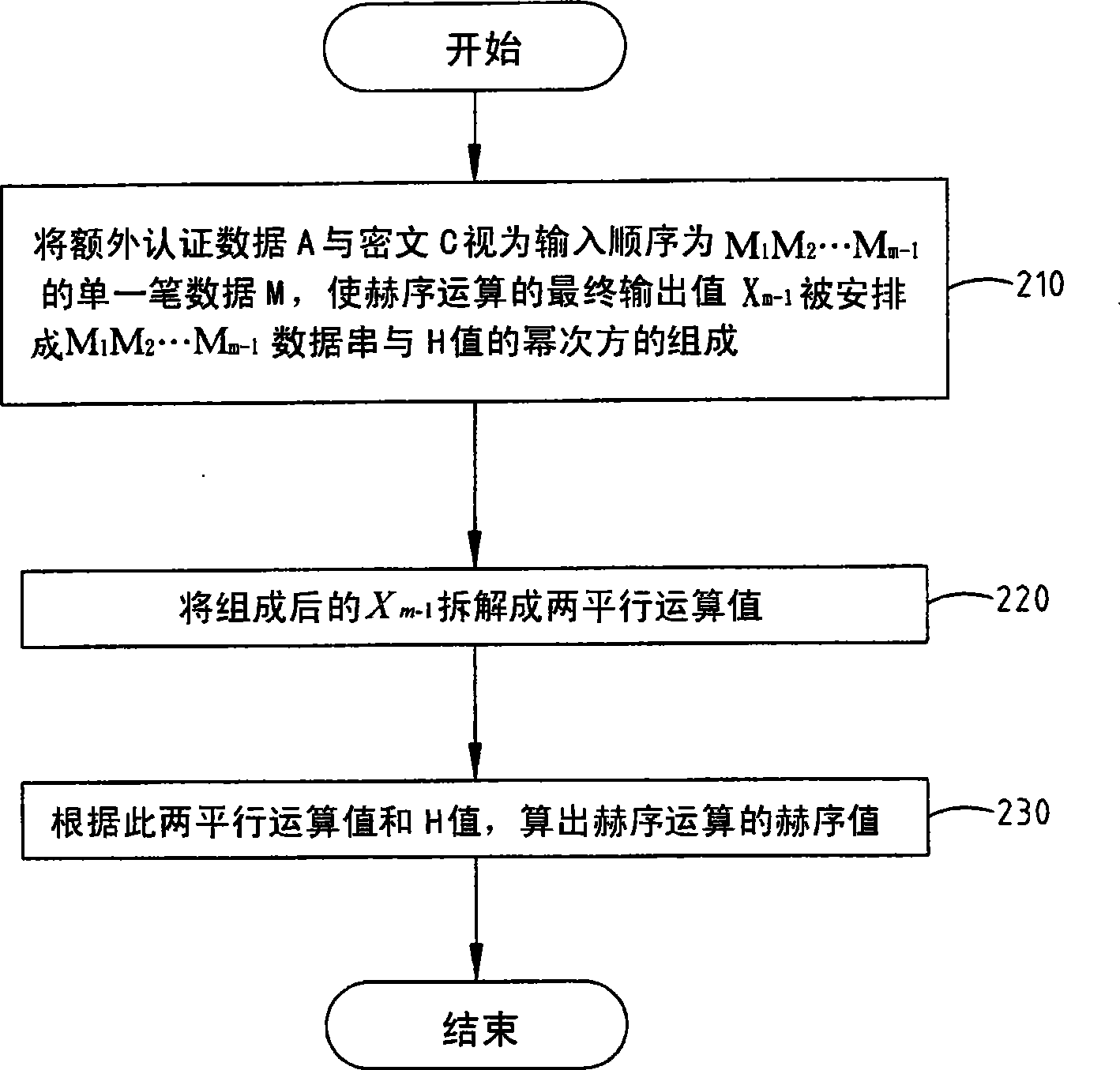
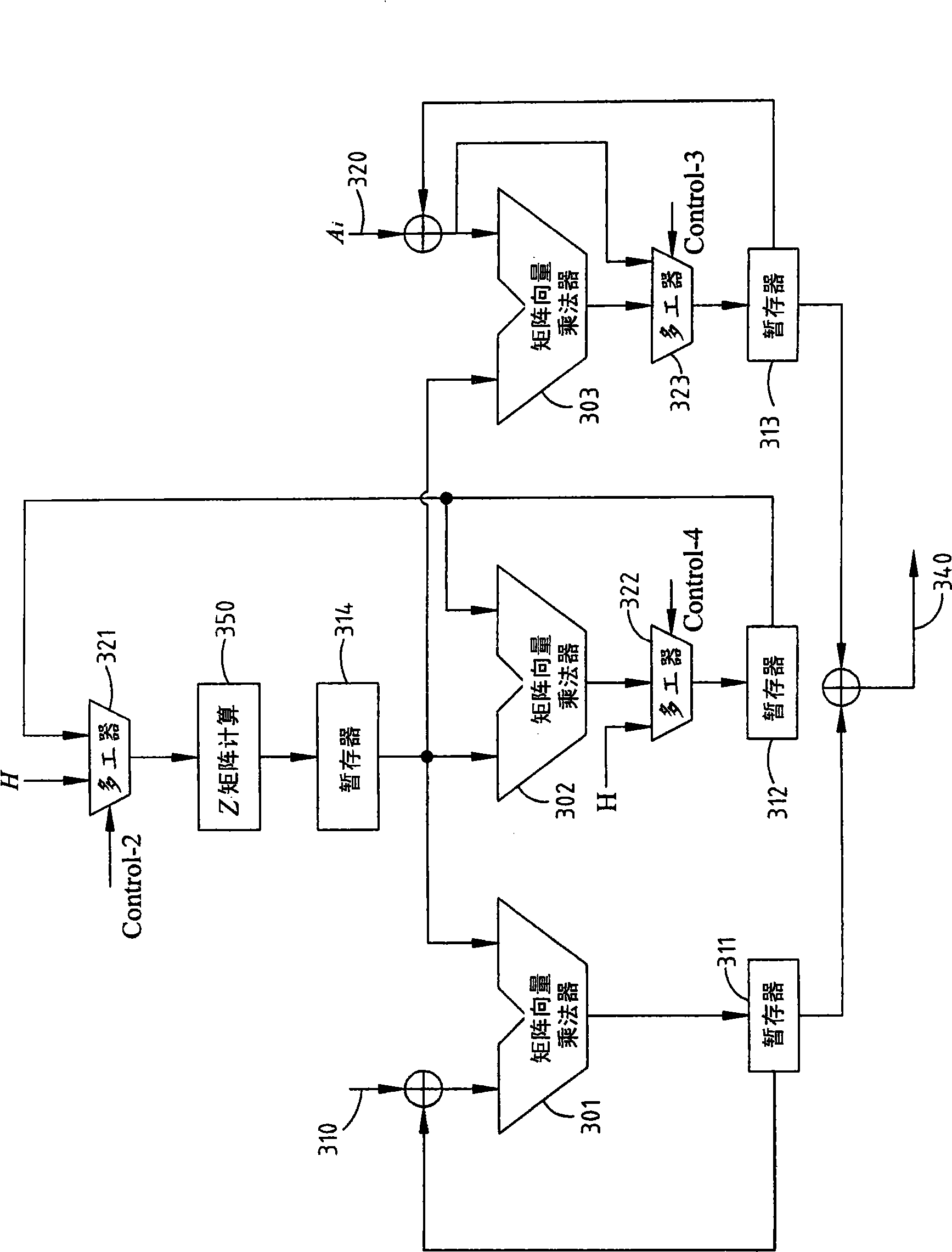
[0042] The GHASH function in formula (1) has three inputs, and these three inputs are the additional authentication data A, the ciphertext C, and the HASH key value H defined in the GCM specification. If not using A i 、C iand len(A)‖len(C), these three inputs, that is, additional authentication data A, ciphertext C, and HASH key value H, are all regarded as a single piece of data M, for the convenience of expressing at the same time Also set the total length of the data as m-1, m is an integer greater than 1, then the output X of the i-th step of the GHASH operation function in the formula (1) i can be reformulated as follows.
[0043] X i = 0 fori = 0 ( X ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com