Tunnel configuration method, virtual access node, virtual edge node and system
A virtual access and virtual edge technology, which is applied in transmission systems, digital transmission systems, data exchange through path configuration, etc., can solve problems such as waste of resources and low utilization of tunnels, and achieve normal results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
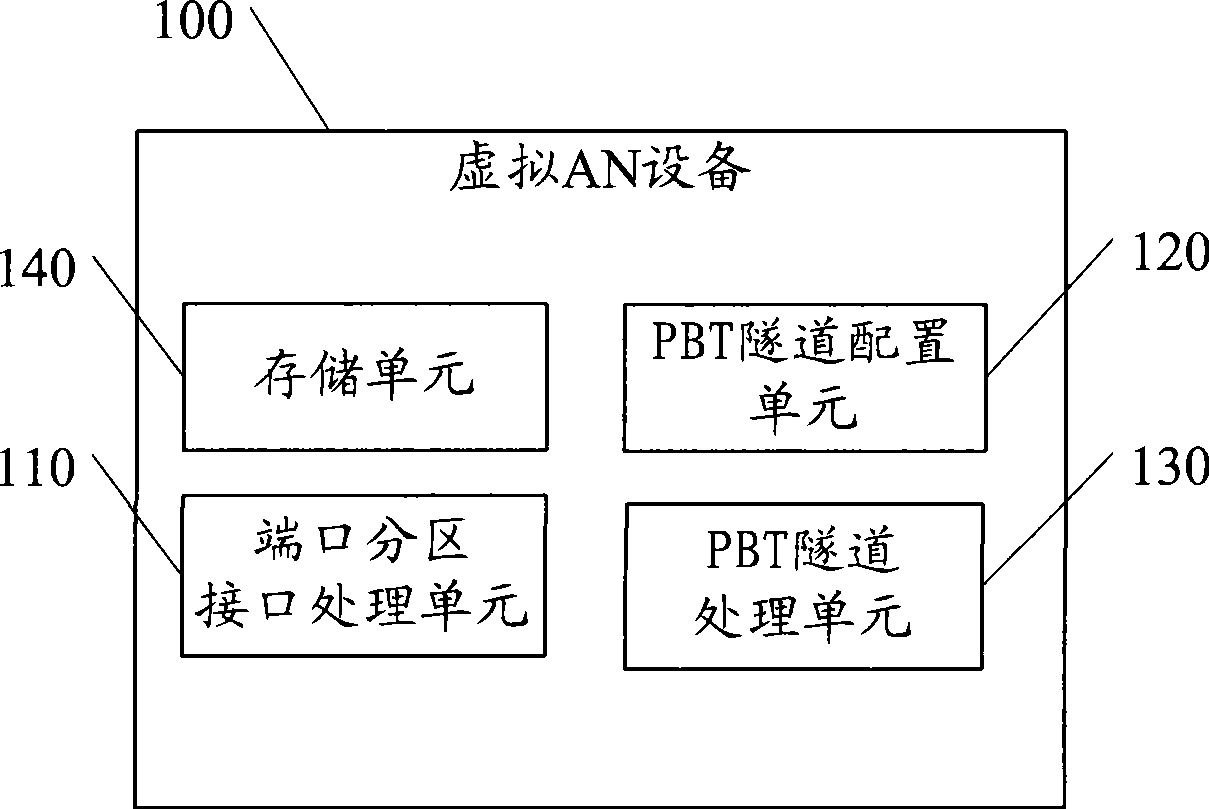
[0055] Embodiment 1, a virtual AN device 100 supporting PBT, the schematic structure is as follows figure 1 As shown, it includes: a port partition interface processing unit 110, a PBT tunnel configuration unit 120, a PBT tunnel processing unit 130 and a storage unit 140;
[0056] The port partition interface processing unit 110 is configured to receive or send data packets from the port corresponding to the virtual MAC address stored in the storage unit;
[0057] The PBT tunnel configuration unit 120 is configured to configure the forwarding table corresponding to the PBT tunnel label between the virtual access node and the edge node through the L2C protocol, where the PBT tunnel label includes: Virtual MAC address, VLAN and the MAC address of the edge node;
[0058] The PBT tunnel configuration unit 120 is further configured to configure, through the L2C protocol, a forwarding table corresponding to the PBT tunnel label between the virtual access node and the virtual edge n...
Embodiment 2
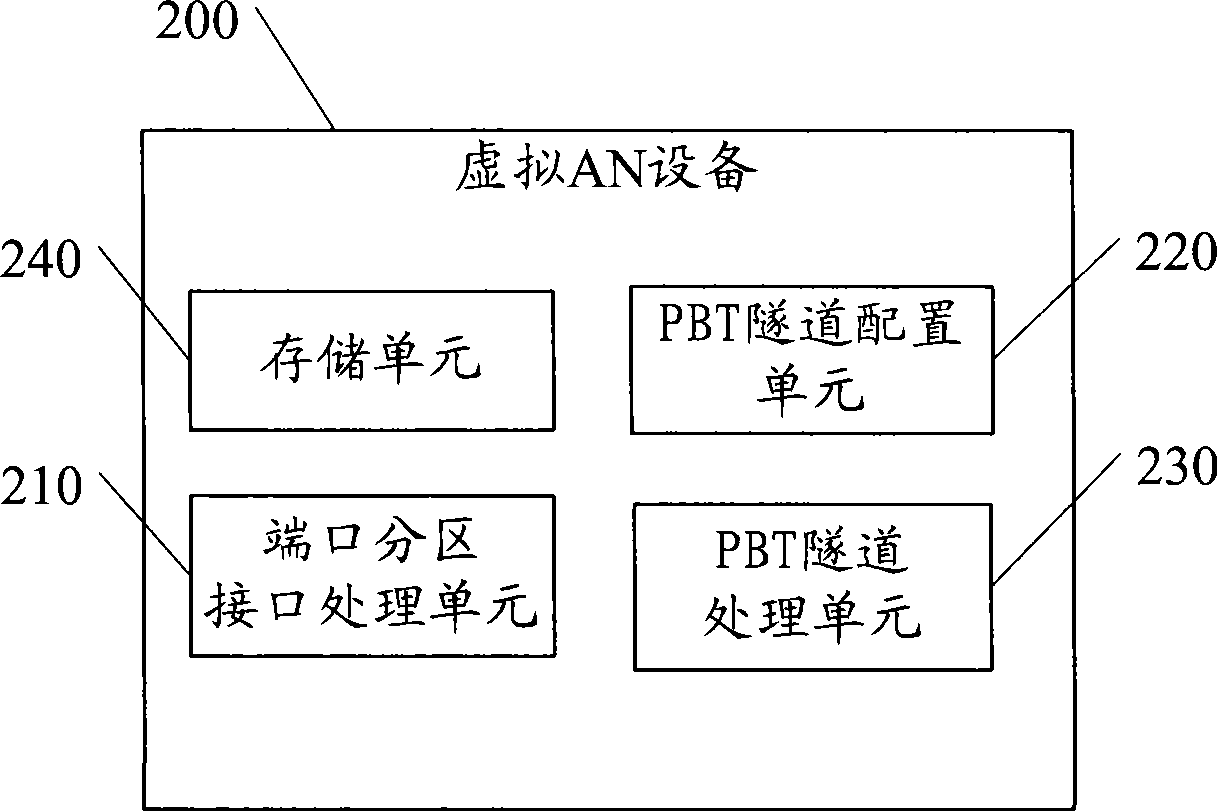
[0062] Embodiment 2, a virtual AN device supporting PBT, the schematic diagram is as follows figure 2 As shown, it includes: a port partition interface processing unit 210, a PBT tunnel configuration unit 220, a PBT tunnel processing unit 230 and a storage unit 240;
[0063] The port partition interface processing unit 210 is configured to receive or send data packets from the port corresponding to the virtual MAC address stored in the storage unit 240;
[0064] The PBT tunnel configuration unit 220 is configured to configure, through the L2C protocol, a forwarding table corresponding to the PBT tunnel label between the virtual access node and the edge node, where the PBT tunnel label includes: Virtual MAC address, VLAN and the MAC address of the edge node;
[0065] The PBT tunnel configuration unit 220 is further configured to configure, through the L2C protocol, a forwarding table corresponding to the PBT tunnel label between the virtual access node and the virtual edge no...
Embodiment 5
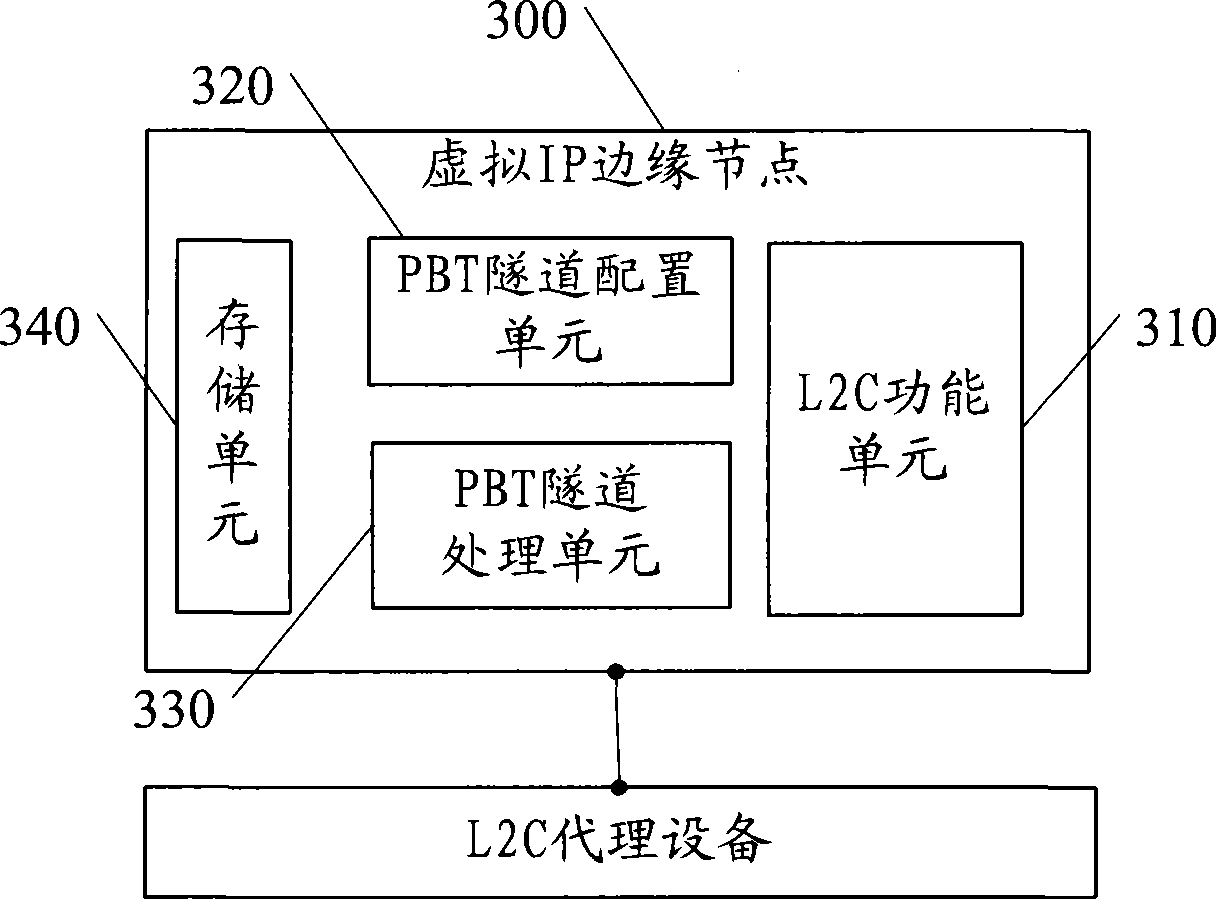
[0089] Embodiment 5 is a system for configuring a PBT tunnel. In this embodiment, the technical solution of Embodiment 4 of the present invention is described in detail with reference to specific application examples.
[0090] The structure diagram is as Figure 5 shown, including:
[0091] access node 510 and IP edge node 520;
[0092] The access node 510 includes multiple virtual ANs, virtual AN1˜virtual ANn;
[0093] The IP edge node 520 includes an L2C functional unit 521 ; an edge node PBT tunnel processing unit 522 .
[0094] Each virtual AN consists of a port zone interface processing unit 511 , a PBT tunnel configuration unit 512 and an ANPBT tunnel processing unit 513 .
[0095] The L2C functional unit 521 interacts with the PBT tunnel configuration unit in each virtual AN to establish a PBT tunnel;
[0096] The PBT tunnel is established between the AN PBT tunnel processing unit 513 of each AN and the corresponding edge node PBT tunnel processing unit 522 on the e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com