Method for establishing security association and communication network system
A security association and communication network technology, applied in the field of establishment of security association, can solve problems such as no suitable method for relay station and network security association, inapplicability, and many security keys, so as to ensure security and ease of use Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 approach
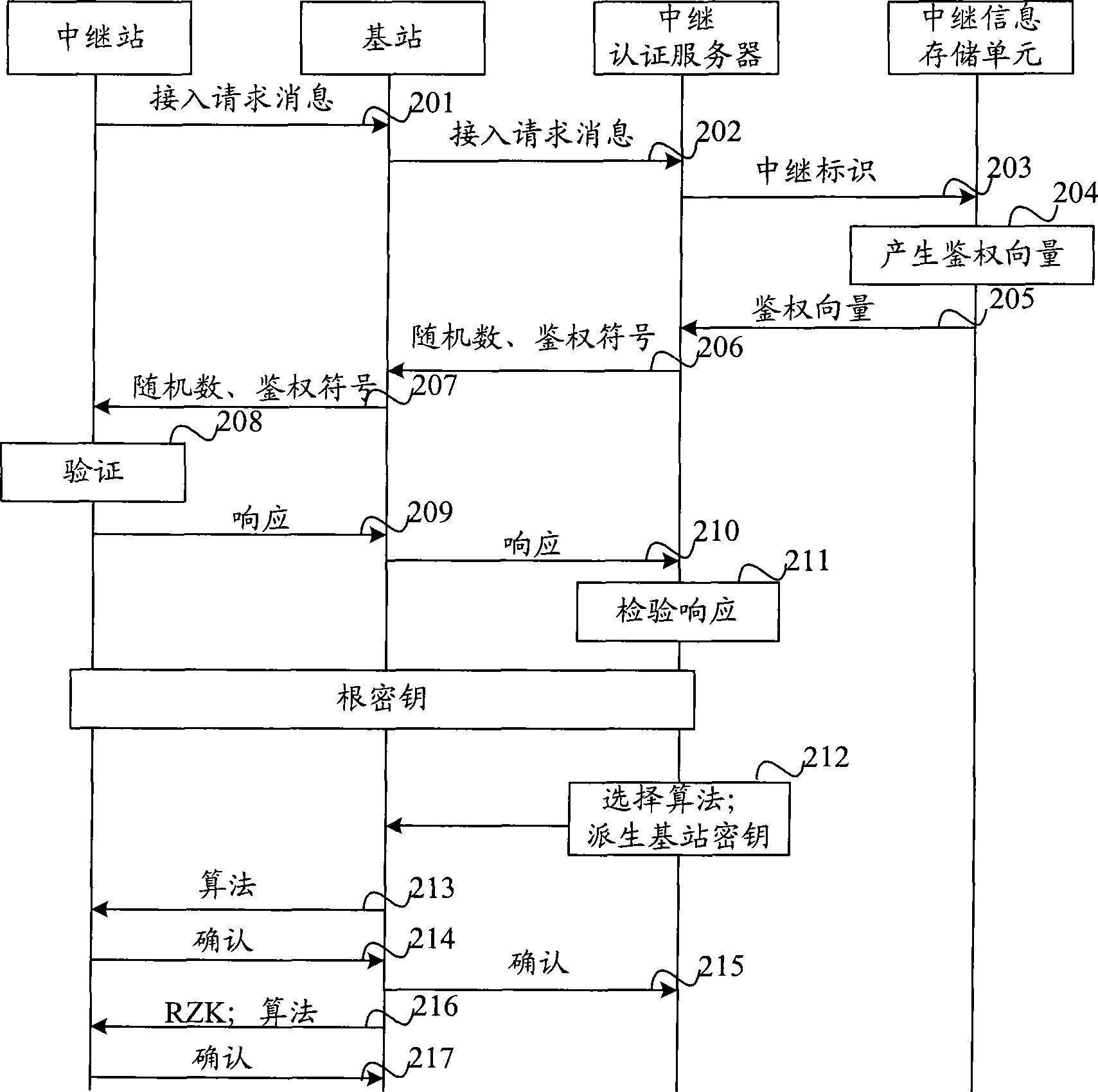
[0019] refer to figure 2 , introducing the first embodiment of the present invention, regarding a method for establishing a security association, this method is preferably applicable to LTE and its evolved systems. In this method, the relay station informs the network-side entity of its own capability information, and the network-side entity can be a functional entity or a physical entity. The network-side entity may include a base station, a relay authentication server, and a relay information storage unit. Both the relay authentication server and the relay information storage unit are located in the network-side entity, and they can exist independently or coexist in a network node as a logical unit. above; in the follow-up process, the network-side entity establishes a security association according to the capability information of the relay station, and the specific process includes:
[0020] Step 201: the relay station sends an access request message to the base station,...
no. 3 approach
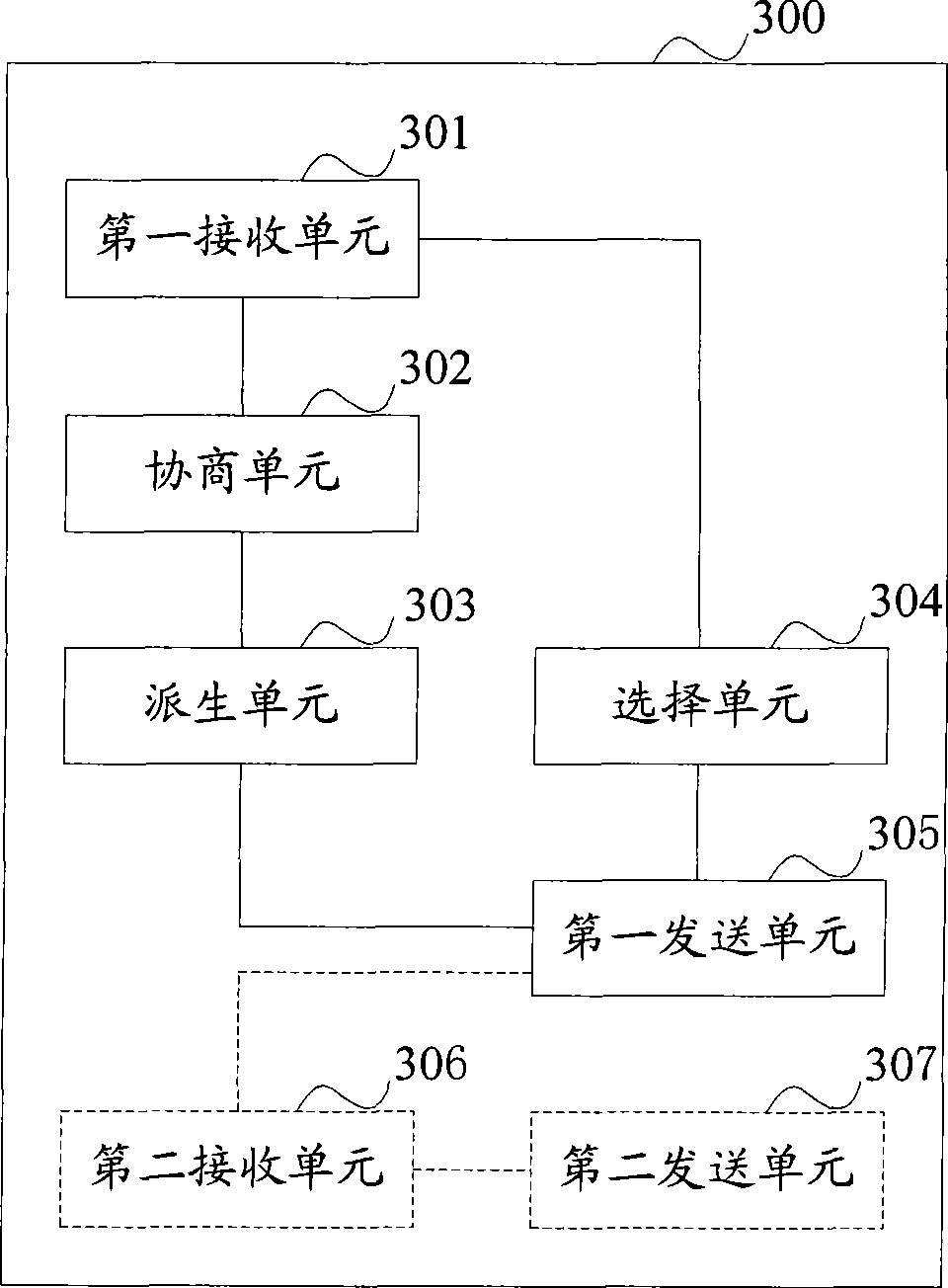
[0050] The third embodiment of the present invention is introduced below. Regarding a communication network, refer to image 3 , the communication network system 300 includes: a first receiving unit 301, configured to receive an access request message sent by a relay station, where the access request message includes relay station capability information;
[0051] a negotiating unit 302, configured to negotiate a shared root key with the relay station;
[0052] The derivation unit 303 is configured to derive the base station key according to the shared root key obtained by the negotiation unit 302 .
[0053] A selection unit 304, configured to select a security algorithm according to the relay station capability information obtained by the first receiving unit 301;
[0054] The first sending unit 305 is configured to send the security algorithm selected by the selecting unit 304 to the relay station, and use the base station key obtained by the deriving unit 303 for protection...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com