Method and device for realizing VPN automatic penetration by utilizing detection mechanism
An automatic and mechanism-based technology, applied in the field of network information security, can solve problems such as IPSecVPN cannot be established, IPSecVPN communication abnormalities, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] See attached Figure 5 Shown: Establish a virtual private network from Beijing to Tianjin, the network is composed of Beijing security gateway equipment and Tianjin security gateway equipment, the IP address of Beijing network security equipment is 212.218.85.1, and the IP address of Tianjin network security equipment is 218.202. 2.1. The service ports known to exist in this network are 80, 22, 1273, and 1083 respectively.
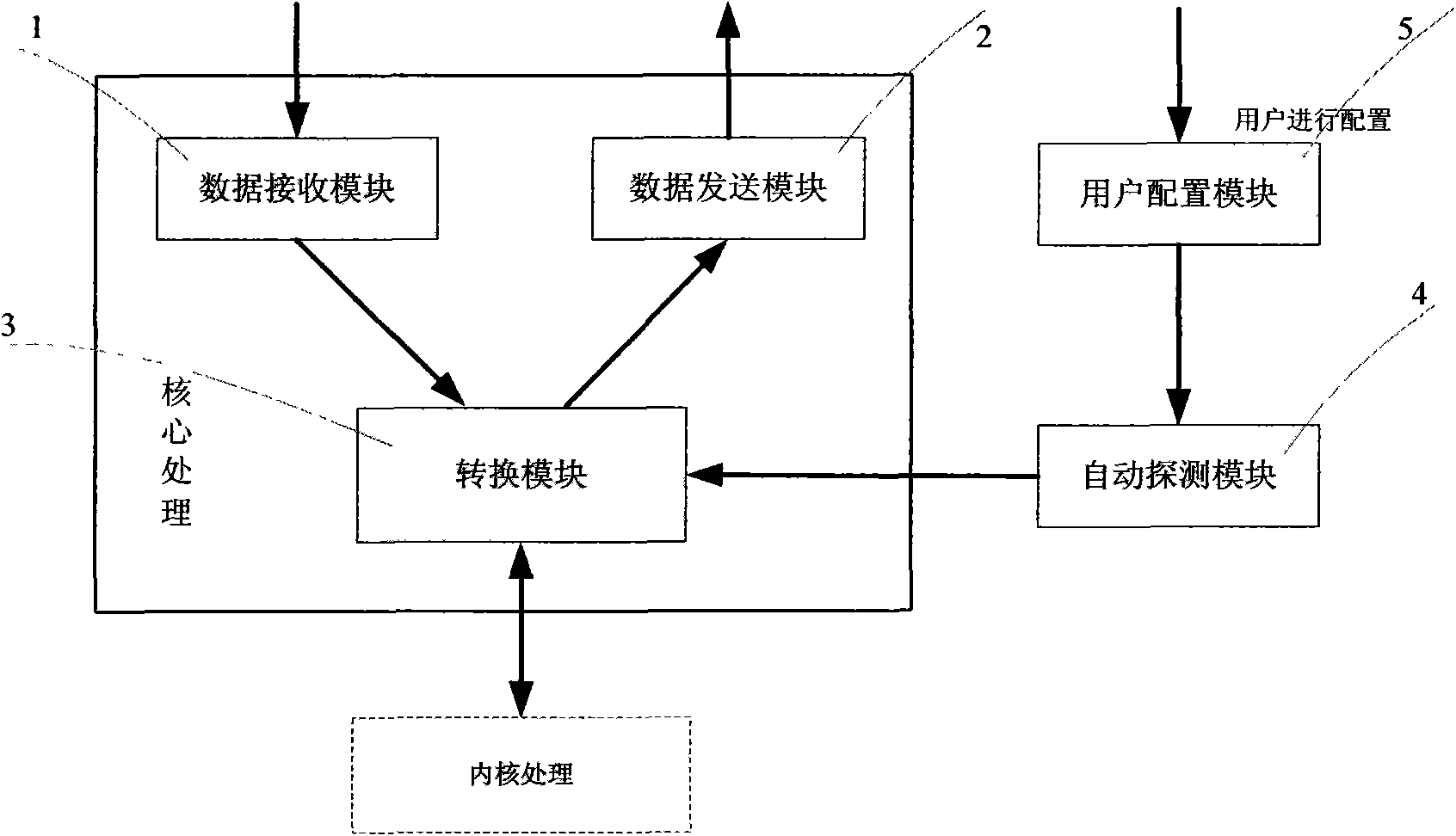
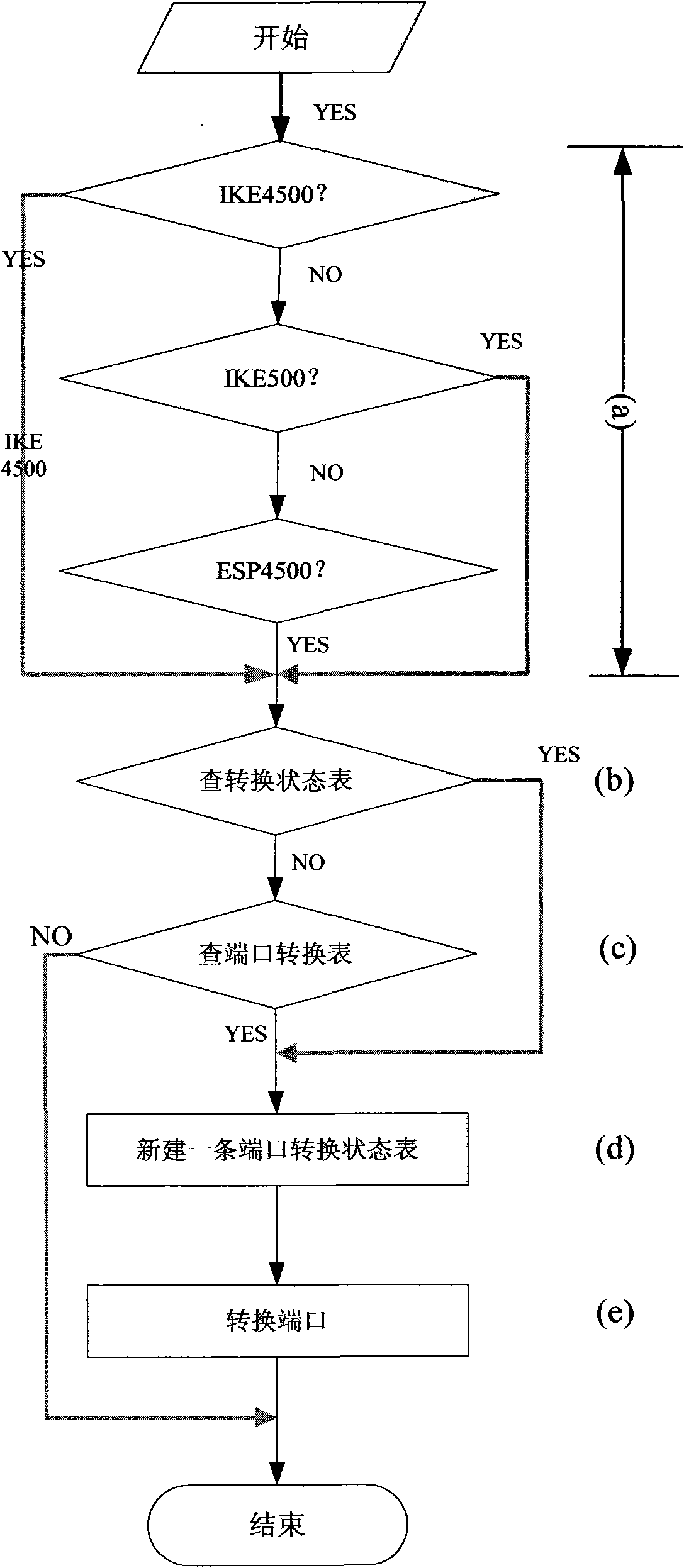
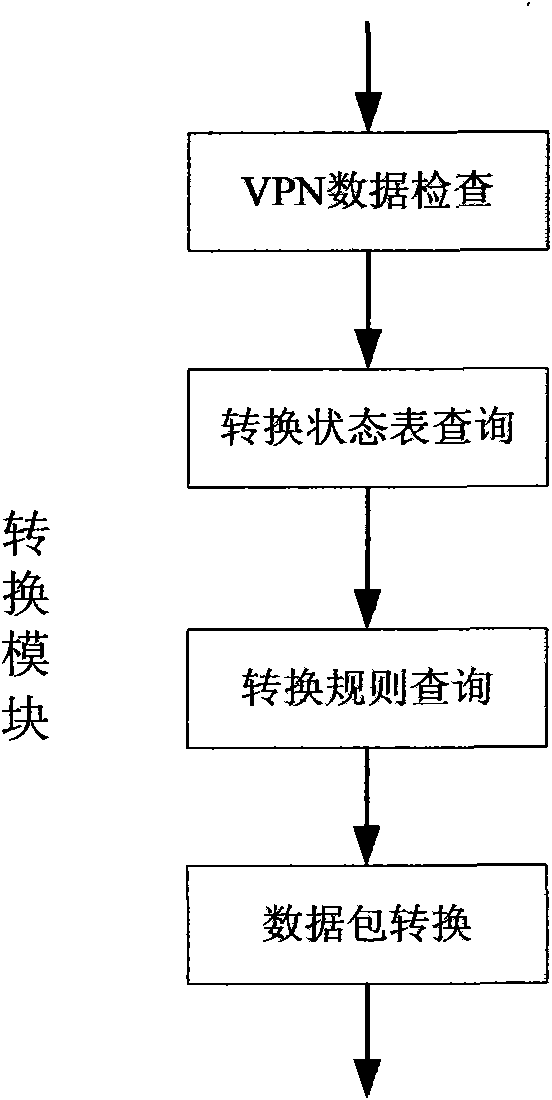
[0037] Both the Beijing security gateway equipment and the Tianjin security gateway equipment are computer equipment containing multiple network cards, in which an operating system that supports network forwarding and IPSEC encryption and decryption processes runs. And install the computer program files needed to realize the technical solution of the present invention in the operating system. The flow of the computer program is attached figure 2 as shown,
[0038] In the work of the above-mentioned system, the steps of using the detection mecha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com