Method for extracting worm features and device therefor
A feature extraction and worm technology, applied in the field of worm feature extraction methods and devices, can solve the problems of poor accuracy and low worm feature accuracy, and achieve the effects of improving accuracy, reducing human resource investment and reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
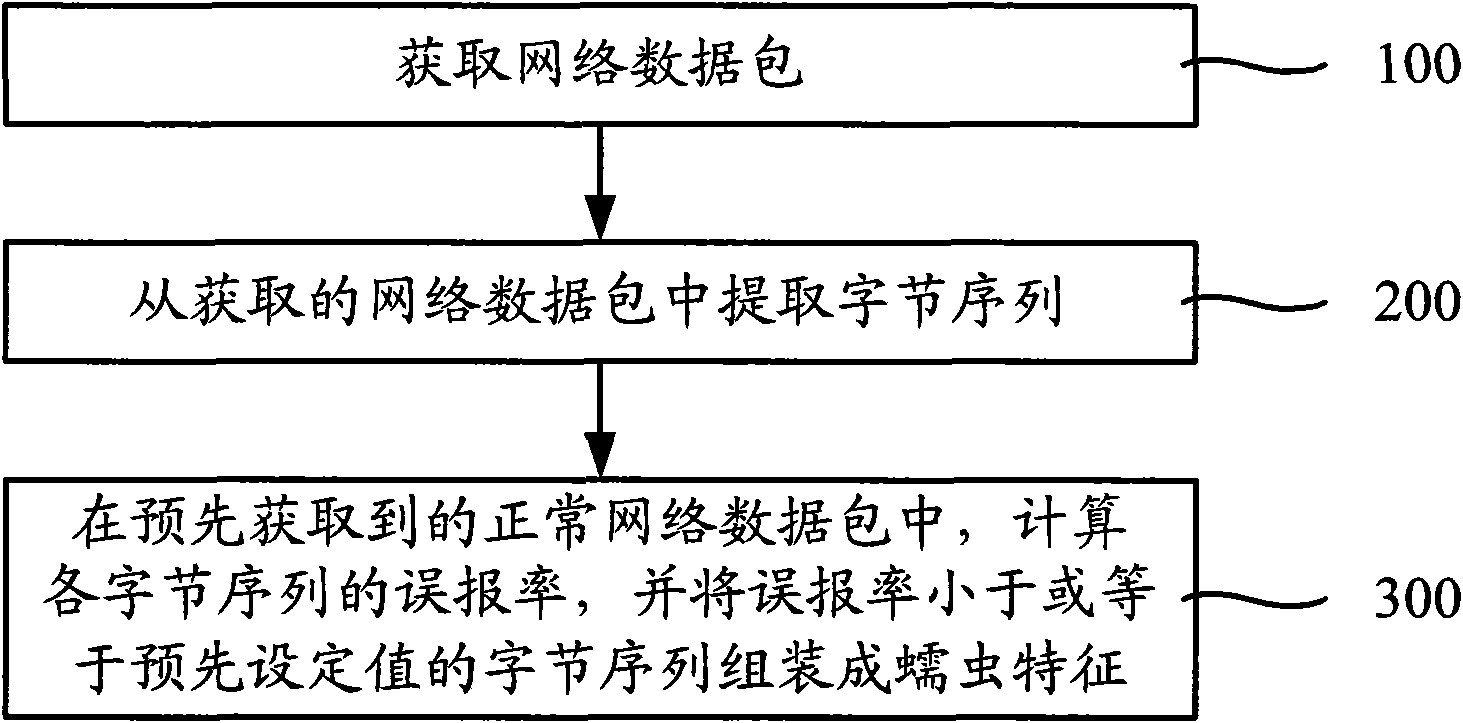
[0032] figure 1 It is a flow chart of the worm feature extraction method provided by the first embodiment of the present invention. The method can be realized by a worm feature extraction device, and the worm feature extraction device can be composed of hardware or software, or a combination of software and hardware. The method of this embodiment specifically includes the following steps:
[0033] Step 100, obtaining network data packets;
[0034] Step 200, extract the byte sequence (token) from the obtained network data packet;
[0035] Step 300, in the pre-acquired normal network data packets, calculate the false alarm rate of each byte sequence, and assemble the byte sequence with the false alarm rate less than or equal to the preset value into a worm feature, wherein the false alarm rate is the probability that a normal network packet containing a byte sequence appears in all normal network packets.
[0036] In this embodiment, firstly, the network data packets must be...
no. 2 example
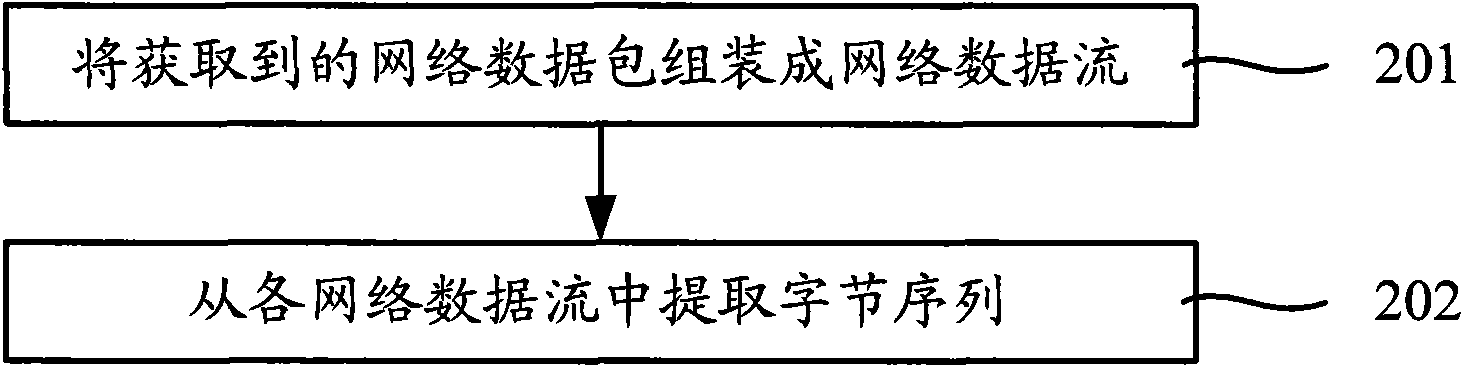
[0044] figure 2 It is a flowchart of byte sequence extraction in the worm feature extraction method provided in the second embodiment of the present invention. This embodiment can be based on the above-mentioned first embodiment. In this embodiment, step 200 specifically includes the following steps:
[0045] Step 201, assembling the acquired network data packets into a network data stream;
[0046] Step 202, extract byte sequences from each network data stream.
[0047] Assemble the network data flow, that is, shape the network data packets according to the set shaping rules. When a worm spreads, it often does not send out a single network packet, but multiple network packets. The exact worm characteristics or byte sequences may be scattered in multiple network packets, so it is necessary to connect multiple network packets as one Only by analyzing the network data flow can the accuracy of extracting worm features be improved.
[0048]The setting shaping rules for assemb...
no. 3 example
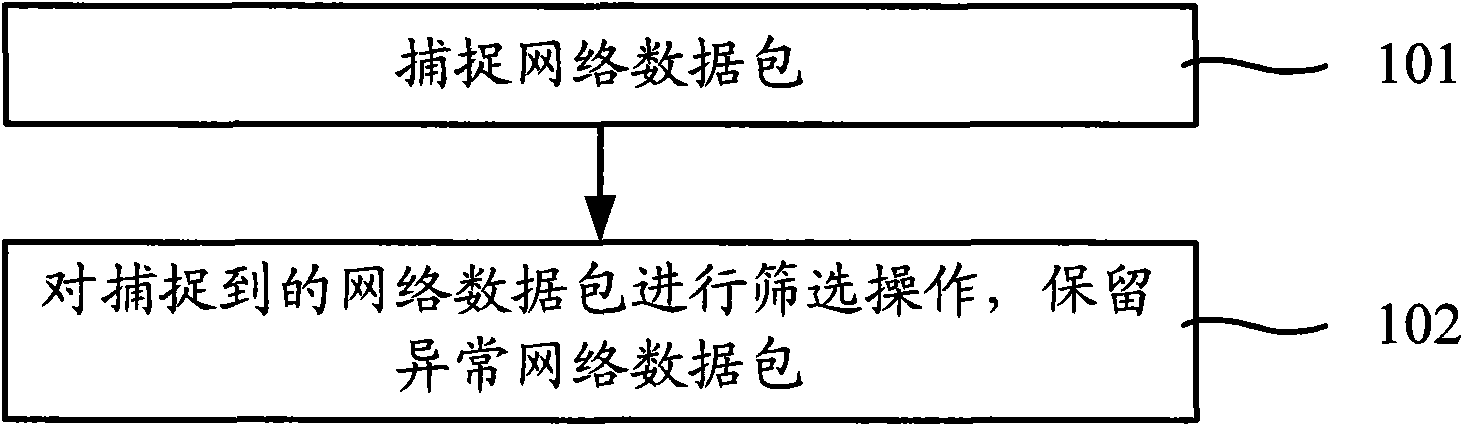
[0051] image 3 It is a flow chart of capturing network data packets in the worm feature extraction method provided by the third embodiment of the present invention. This embodiment can be based on the above-mentioned embodiments, and the operation of obtaining network data packets in step 100 can be specifically:
[0052] Step 101, capturing network packets;
[0053] Step 102, performing a screening operation on the captured network data packets, and retaining abnormal network data packets.
[0054] It may be to capture network data packets within a set period, and the captured network data packets usually include normal network data packets and abnormal network data packets. The concept of normal network data packets is as described above, and the rest of the network data packets can be regarded as abnormal network data packets.
[0055] The above-mentioned screening of network data packets is not a necessary step, but it has significant advantages. It can reduce the numbe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com