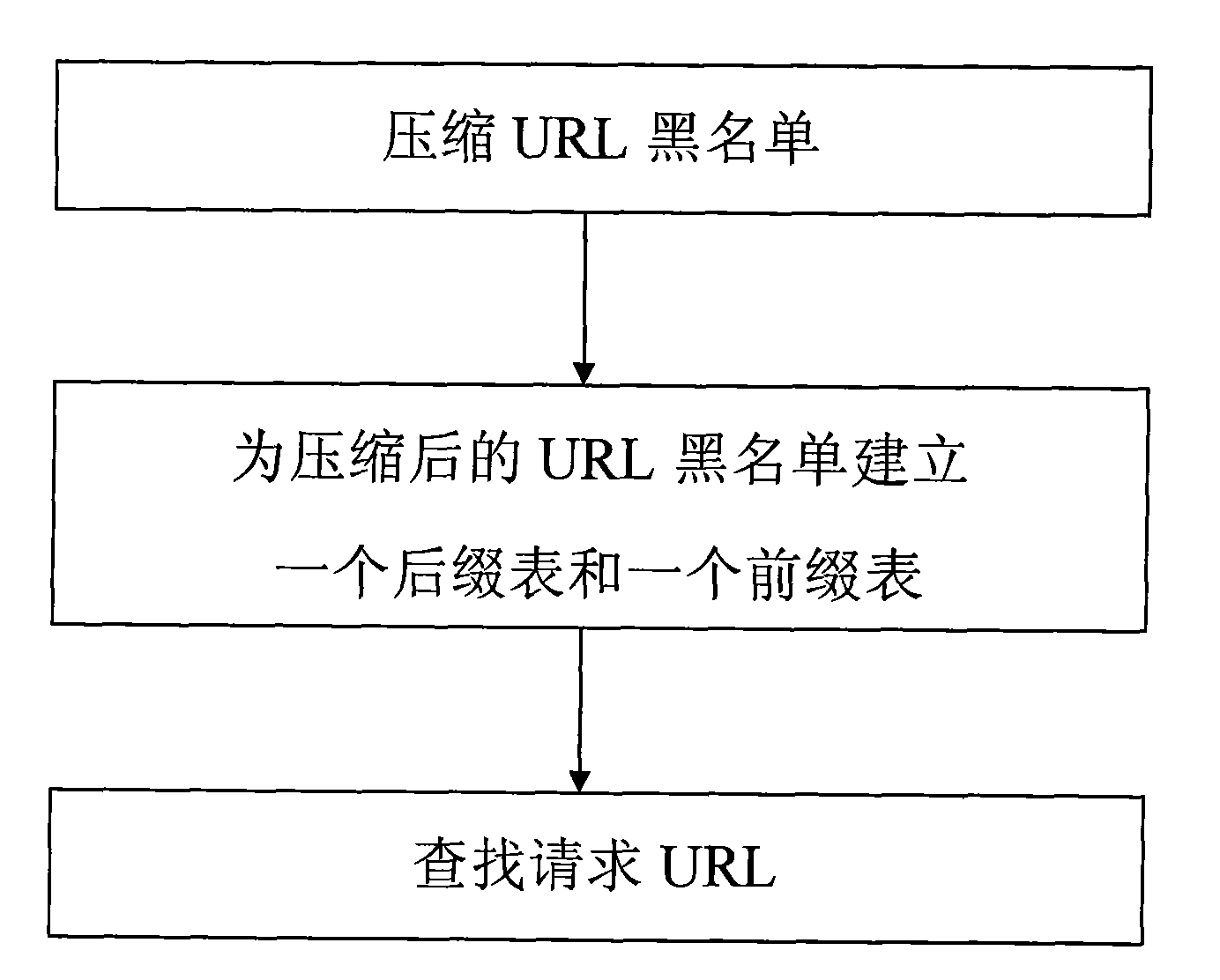
URL lookup method for URL filtering system
A technology of filtering system and establishing method, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as large storage space, search efficiency constraints, etc., and achieve the effects of high storage efficiency, fast search speed, and convenient and effective control.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0076] Example 1: The request URL is: "http: / / network.cs.bit.edu.cn / research / projects / ", the specific search steps are as follows:
[0077] Step (1): Use the compression step in step 1 to compress the request URL into a string of (c / 8)*n bytes. In this example, c=32, n=3, so "http: / / network.cs.bit.edu.cn / research / projects / " is compressed into a 12-byte string 0x2336F04B57EB50C25C93B3A4;
[0078] The 2nd step: (c / 8)*n=12, m=4, the value of (c / 8)*n is not less than m, go to the 3rd step;
[0079] Step (3): B=2, m=4, using the hash function used in step 2 to set up the suffix table, the calculated hash value h=61515;
[0080] Step (4): B'=2, using the hash function used in step 2 to establish the prefix table, the value of the calculated "URL prefix" is 9014;
[0081] The 5th step: h=61515, the URL (0x2336F04BA4698DB2) pointed to by the SUFFIX[h] pointer is not empty, go to the 6th step;
[0082] Step (6): h=61515, the value of the URL (0x2336F04BA4698DB2) pointed to by the SU...
example 2
[0085] Example 2: The request URL is: "http: / / www.sina.com.cn / ", the specific search steps are as follows:
[0086]Step (1): Use the compression step in step 1 to compress the request URL into a string of (c / 8)*n bytes. In this example, c=32, n=1, so "http: / / www.sina.com.cn / " is compressed into a 4-byte string 0x24BCB313;
[0087] The 2nd step: (c / 8)*n=4, m=4, the value of (c / 8)*n is not less than m, go to the 3rd step;
[0088] Step (3): B=2, m=4, using the hash function used in step 2 to set up the suffix table, the calculated hash value h=45843;
[0089] Step (4): B'=2, using the hash function used in step 2 to establish the prefix table, the value of the calculated "URL_prefix" is 9404;
[0090] Step (5): h=45843, the URL (0x24BCB313) pointed to by the SUFFIX[h] pointer is not empty, go to step (6);
[0091] Step (6): The value of the URL (0x24BCB313) pointed to by the SUFFIX[h] pointer in the prefix table PREFIX is equal to "URL_prefix". Compare the URL (0x24BCB313) p...
example 3
[0092] Example 3: The request URL is: "http: / / www.baidu.com / ", the specific search steps are as follows:
[0093] Step (1): Use the compression step in step 1 to compress the request URL into a string of (c / 8)*n bytes. In this example, c=32, n=1, so "http: / / www.baidu.com / " is compressed into a 4-byte string 0x171BC50D;
[0094] The 2nd step: (c / 8)*n=4, m=4, the value of (c / 8)*n is not less than m, go to the 3rd step;
[0095] Step (3): B=2, m=4, using the hash function used in step 2 to set up the suffix table, the calculated hash value h=50445;
[0096] Step (4): B'=2, using the hash function used in step 2 to establish the prefix table, the value of the calculated "URL_prefix" is 5915;
[0097] Step (5): h=50445, the URL pointed to by the SUFFIX[h] pointer is empty, report "not found", and end the process.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com