Signcryption scheme based on elliptic curve cryptography
一种椭圆曲线加密、椭圆曲线的技术,应用在智能卡领域,达到减小数据开销的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
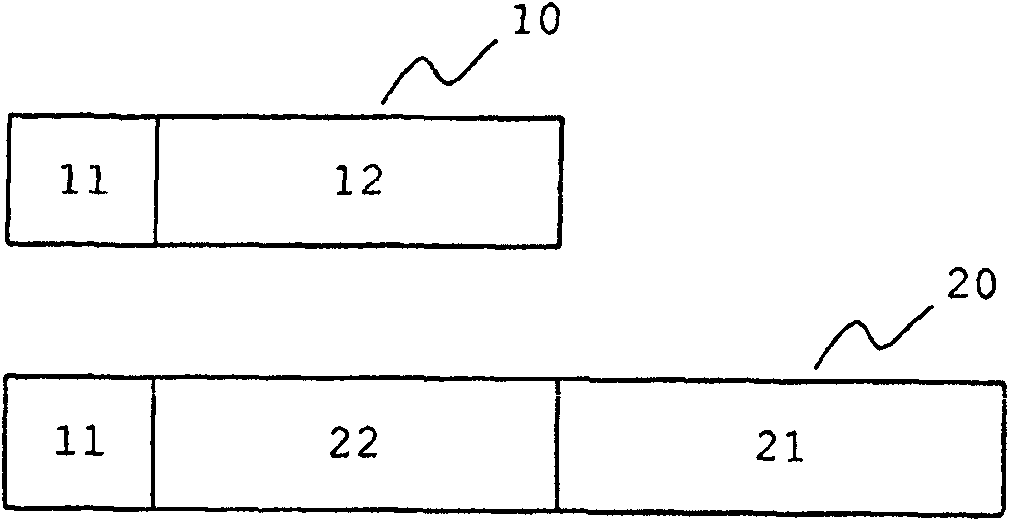
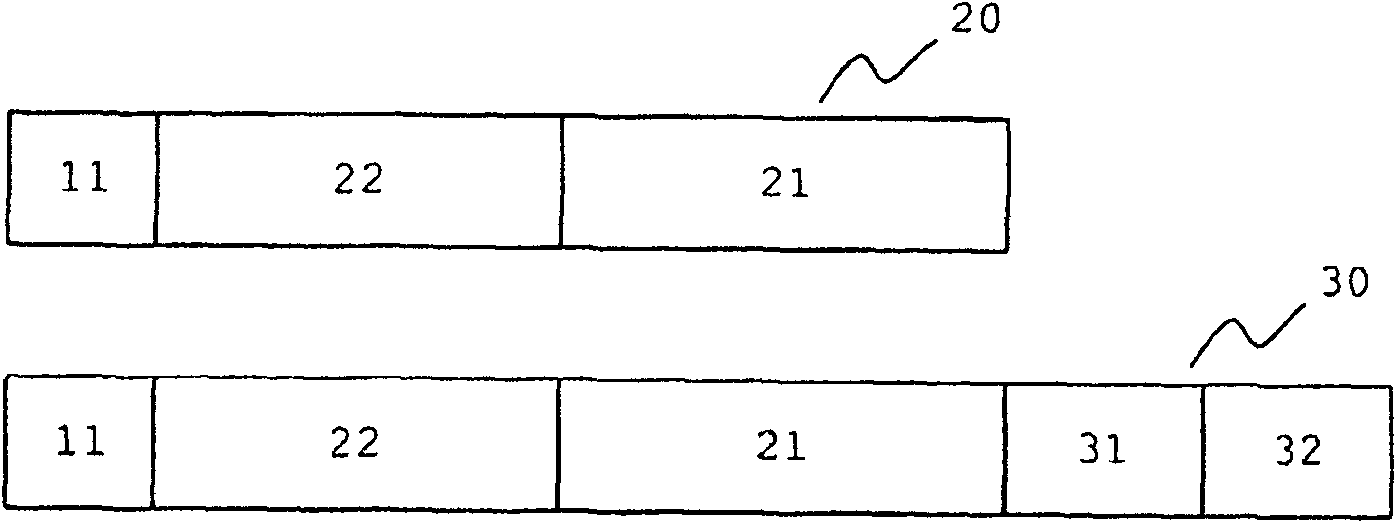
[0039] Figure 1A and 1B shows the application of ECIES ( Figure 1A ) and ECDSA ( Figure 1B ) prior art examples of ECM or EMM before and after.
[0040] The invention is typically applied to conditional access systems where EMMs and ECMs are transmitted in signcrypted form. The invention is not limited to application in conditional access systems, and can be used in any system where data is signcrypted.
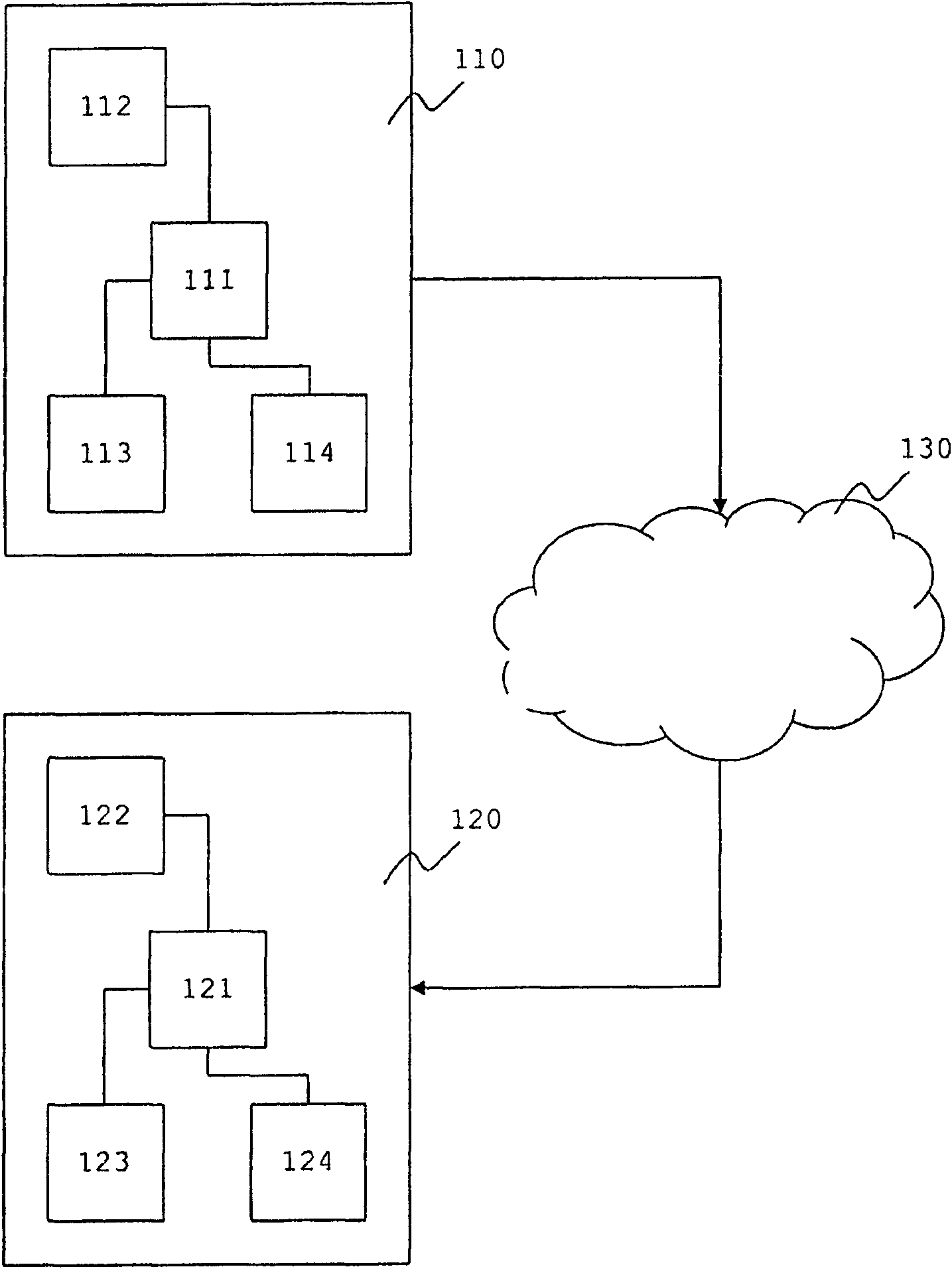
[0041] exist figure 2 , a typical conditional access system 100 is shown. figure 2 Only the main elements involved in signcryption are shown, other elements not shown may be part of the conditional access system 100 . In the conditional access system 100 , the headend system 110 transmits the signcrypted EMM and the signcrypted ECM to the smart card 120 through the broadcast network 130 . The smart card 120 is for example located in a set-top box (not shown) for receiving and forwarding the sign-encrypted EMM / ECM to the smart card 120 . although figure 2 Only o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com