Bidirectional authentication method and system based on symmetric encipherment algorithm
A technology of symmetric encryption algorithm and two-way authentication, which is applied in the field of two-way authentication method and system based on symmetric encryption algorithm, and can solve the problems of inappropriate and high-performance electronic tags with low performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
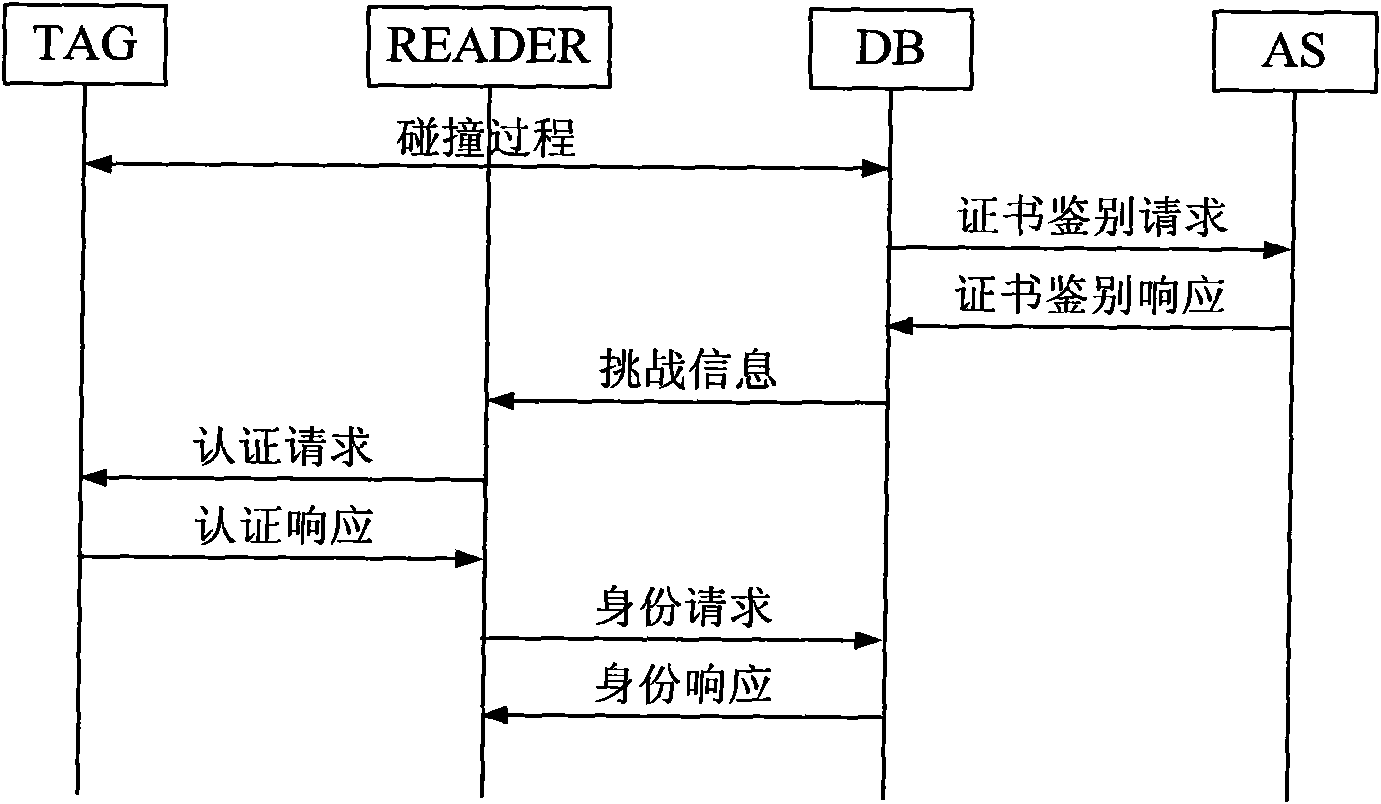
[0071] see figure 1 , the present invention provides a two-way authentication method based on a symmetric encryption algorithm, the method comprising:
[0072] 1) Collision process: the grouping is completed jointly by the reader-writer READER, the electronic tag TAG and the electronic tag application system database DB. First, the READER selects an electronic tag TAG from multiple associated electronic tags TAG through the collision protocol, and then sends its own digital certificate CERT_R and the selected tag PID information to the electronic tag application system database DB.
[0073] 2) Certificate authentication request: After the collision process is completed, when the electronic tag application system database DB obtains the information sent by the READER, it constructs and sends a certificate authentication request group to the authentication server AS, and the group is sent by the electronic tag application system database DB. sent to the authentication server AS...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com