BIOS-based computer security protection method and system
A computer security and protection system technology, applied in computer security devices, computing, instruments, etc., can solve problems such as inability to achieve effective protection and unprotected computer systems.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
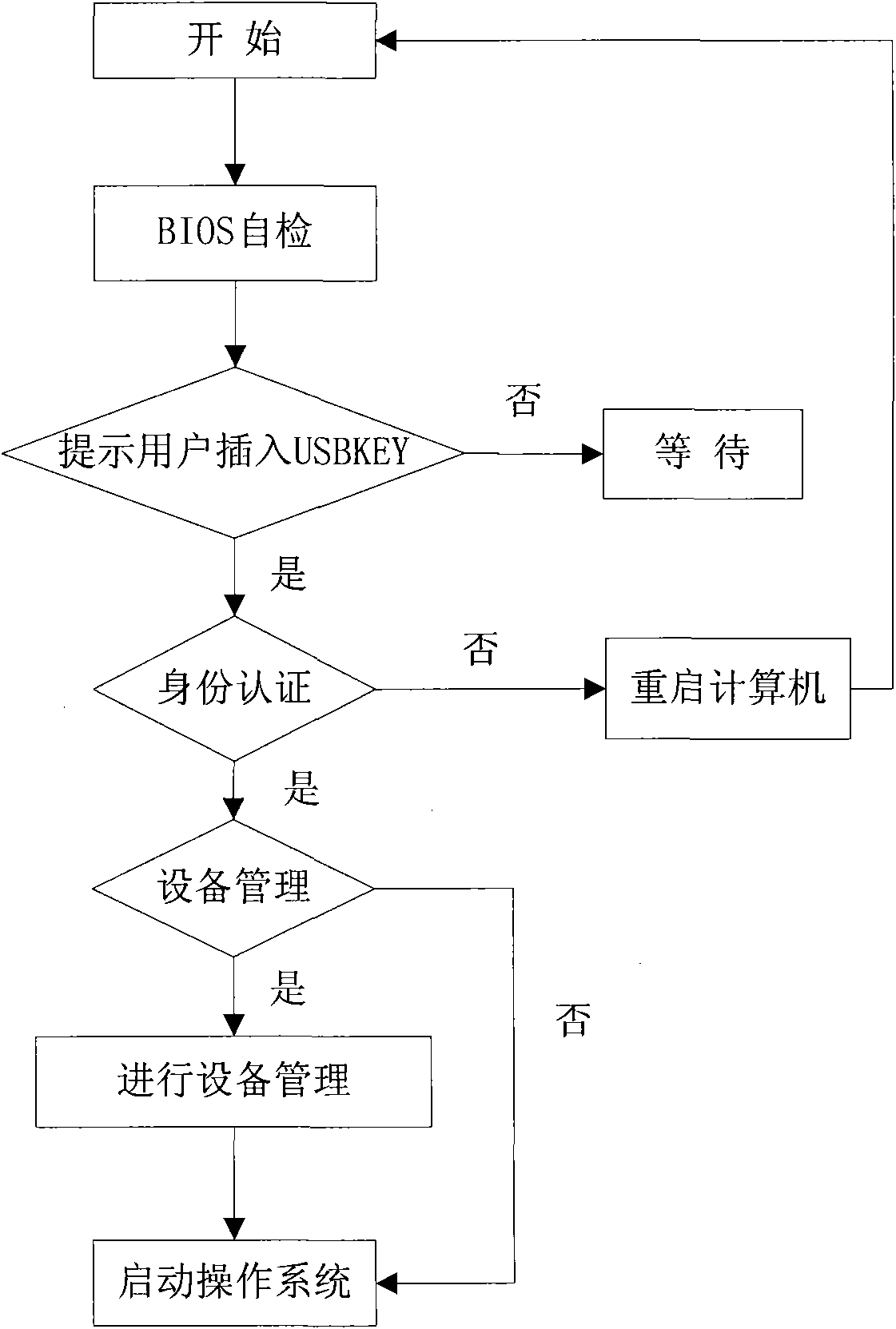
[0048] figure 1 It is a flowchart of a specific embodiment of the inventive method, as shown in the figure, the specific implementation process of the inventive method is as follows:
[0049] Insert the USBKEY identity authentication function module complying with the BIOS format into the BIOS; start the computer and complete the BIOS self-check; then the BIOS calls the USBKEY identity authentication function module, first detects whether the USBKEY is inserted into the interface of the computer, and if so, performs USBKEY identity authentication, Otherwise prompt the user to insert the USBKEY.
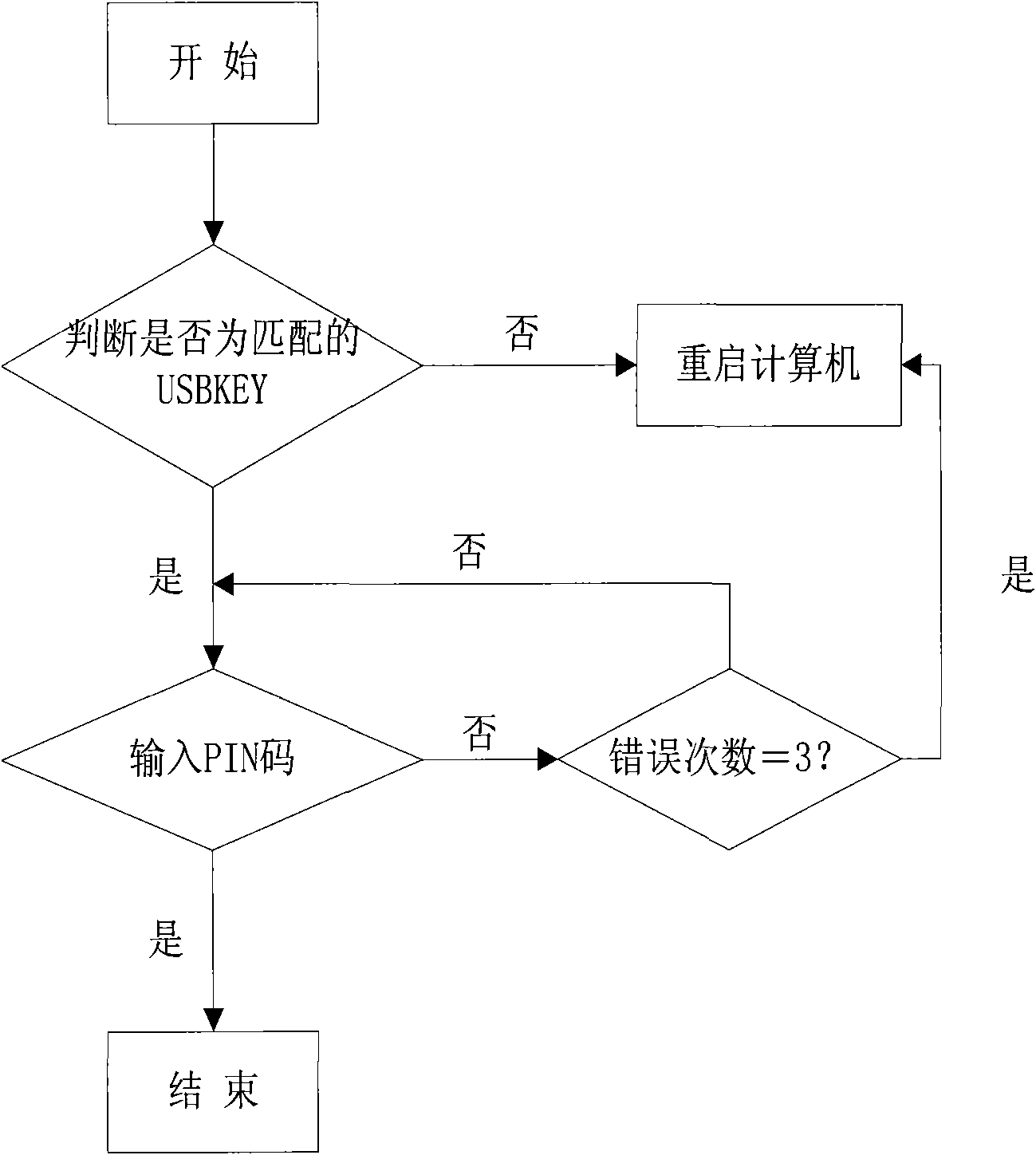
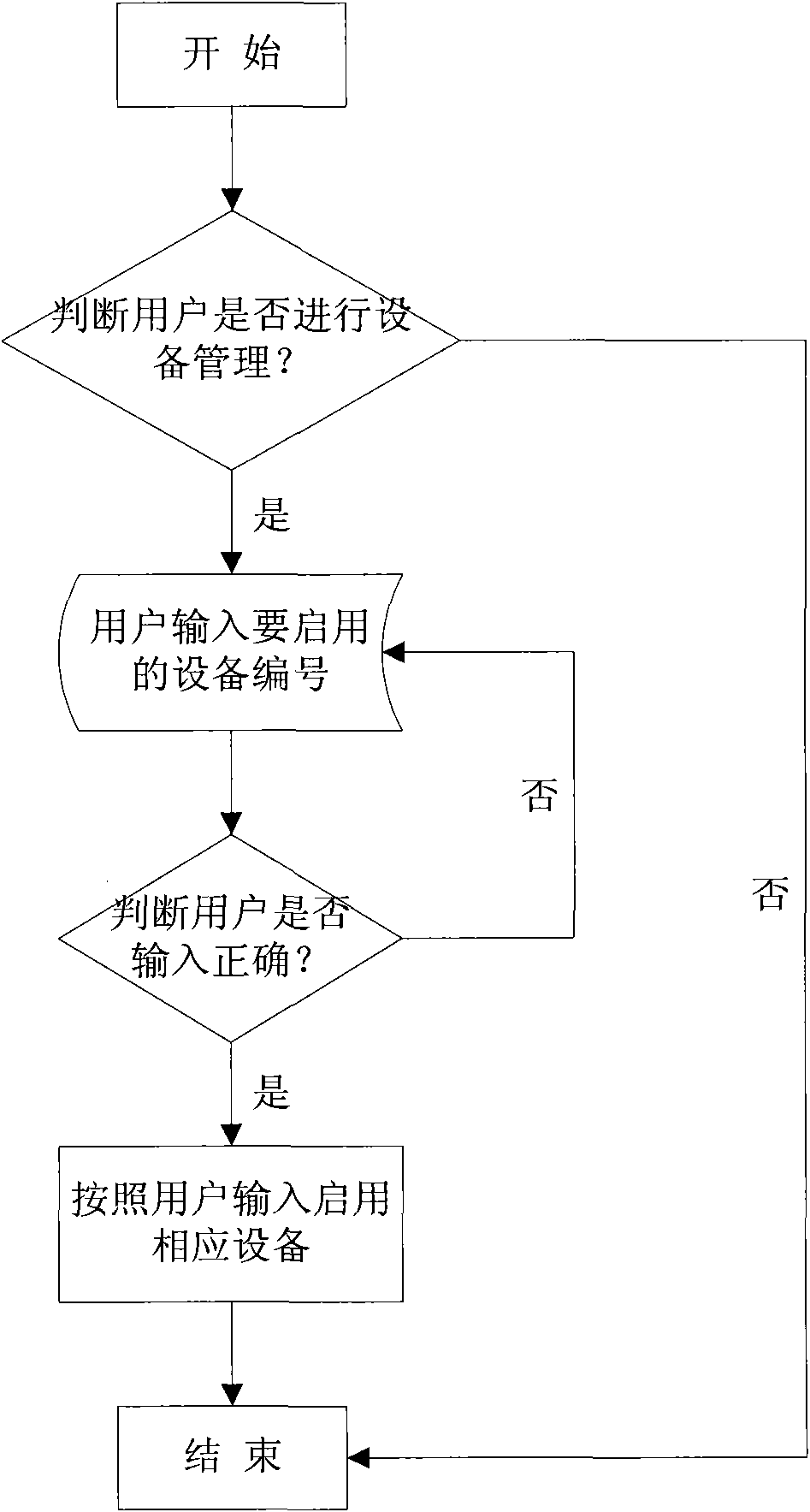
[0050] After the USBKEY identity authentication is successful, enter the device management menu, and load the operating system after the device management operation is completed; if the USBKEY identity authentication fails, it is prevented f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com