Method for guaranteeing transmission quality of security monitoring data in wireless local area network
A technology for data transmission quality and security monitoring, applied in network traffic/resource management, wireless communication, electrical components, etc., can solve problems such as congestion, flow interruption, packet loss, etc., achieve optimal utilization, improve transmission quality, reduce delay and The effect of packet loss rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
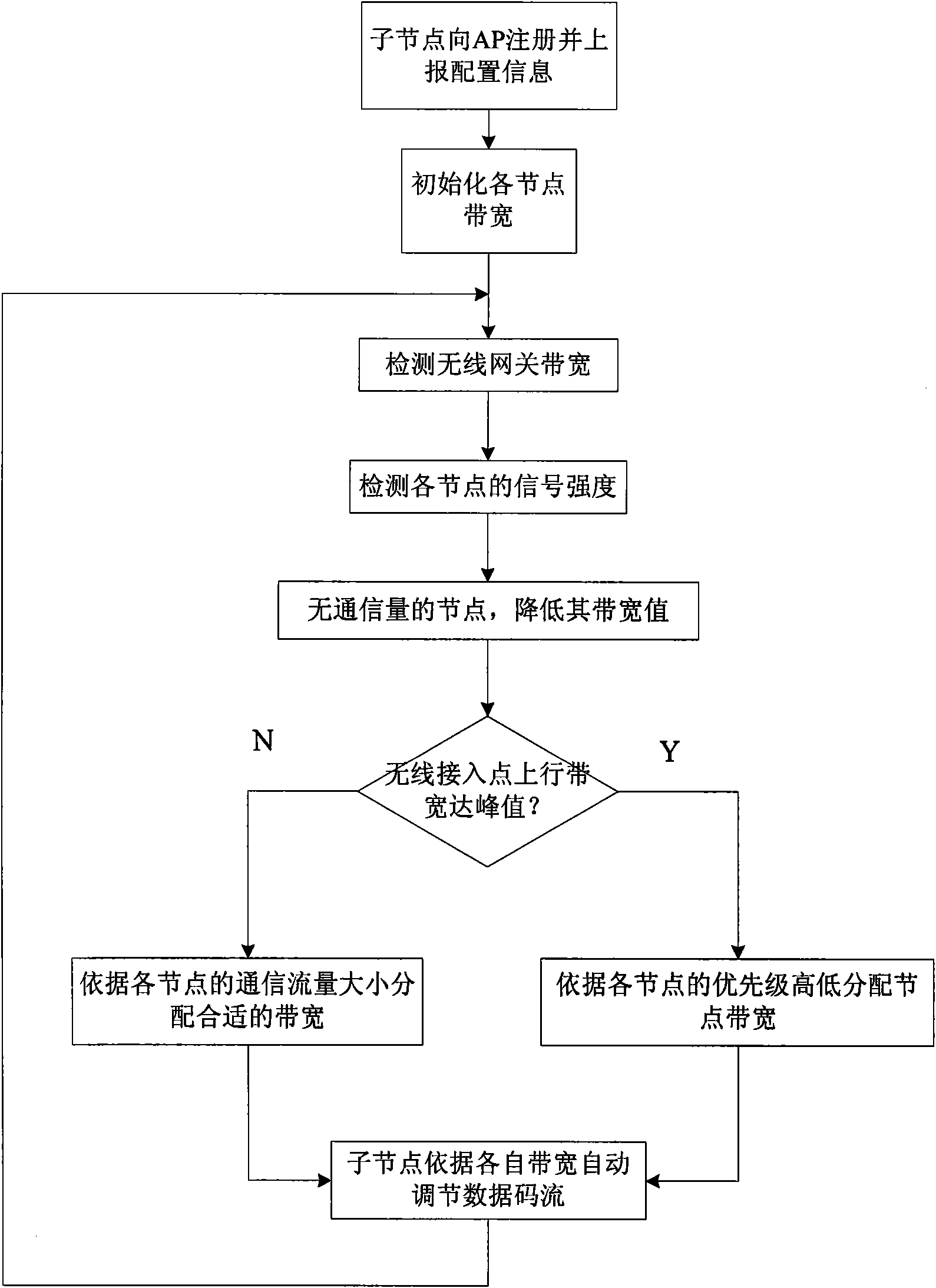
[0038] Such as figure 1 As shown, the method for realizing security monitoring data quality assurance in a wireless local area network includes the following steps:
[0039] 1. After power on, the wireless node completes registration with the AP, and at the same time reports node configuration information to the AP, such as node priority, node total code stream size, etc. The total code stream size of a node refers to the code stream size allowed by the node, that is, the maximum code stream of the node, which can be used for the access point to set the initial bandwidth of each node.
[0040] 2. The AP detects the signal strength of each node, and calculates the peak communication rate of each node during each communication with the node; when setting the bandwidth of each node for the first time, set the node according to the saved node configuration information table and bandwidth configuration strategy. Fixed bandwidth; the variables in the node configuration information table...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com