Computer, payment system and method thereof for realizing on-line payment
A payment system and online payment technology, applied in the direction of payment system structure, calculation, data processing applications, etc., can solve the problems of high cost, cumbersome operation steps, and business changes can only be handled at the bank counter, so as to improve the security level and facilitate Internet User Effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
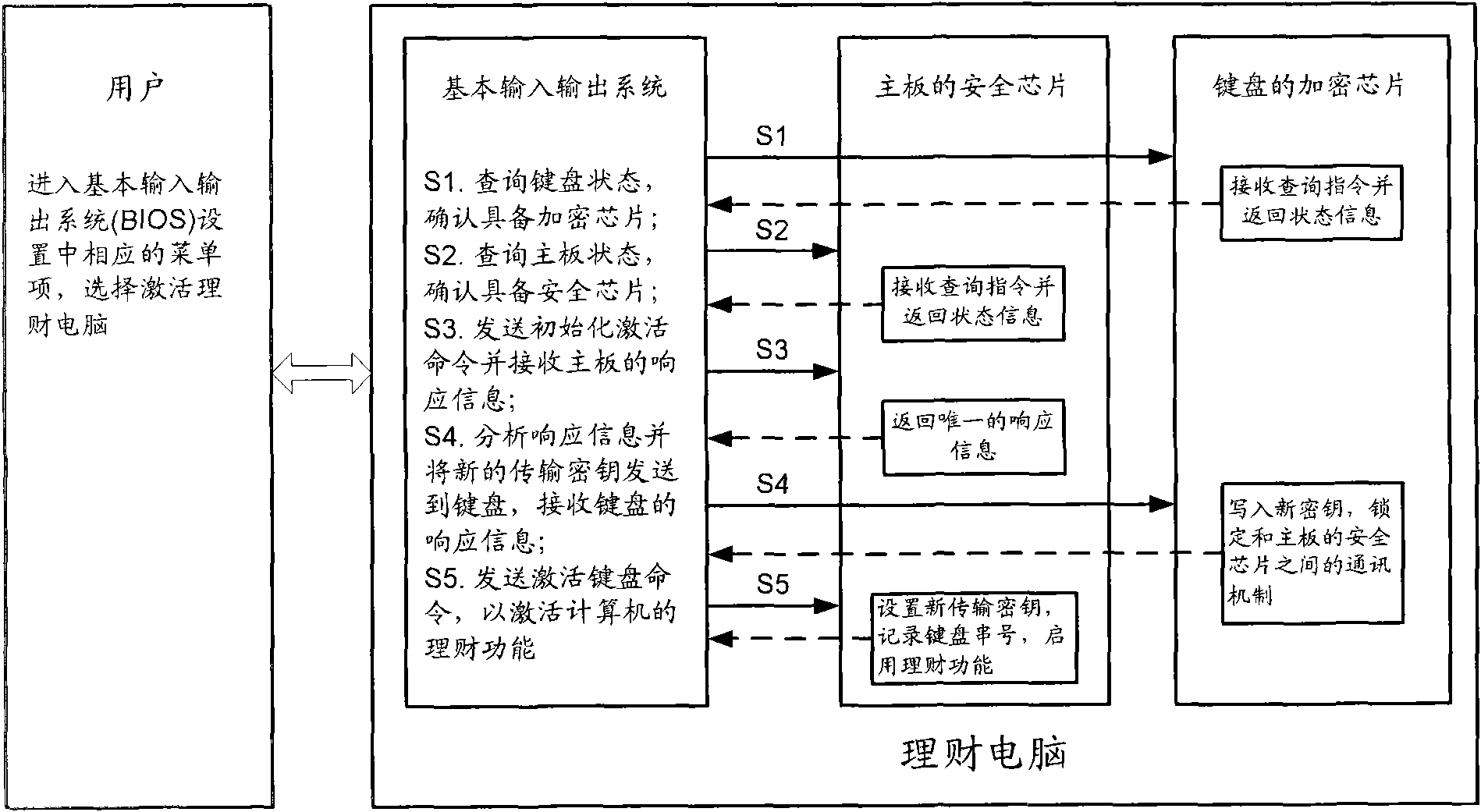
[0060] The specific implementation manners of the present invention will be described in further detail below with reference to the accompanying drawings.
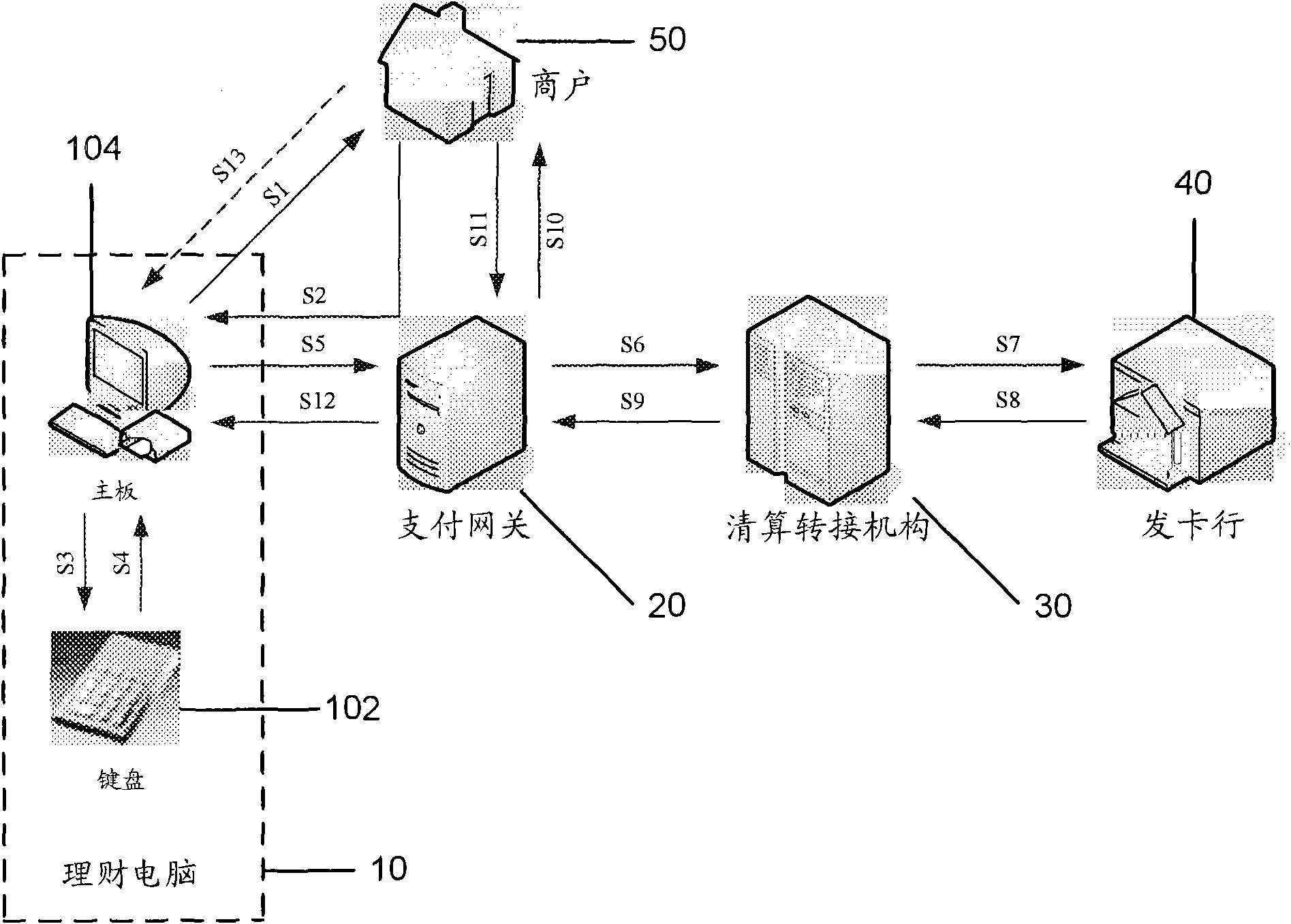
[0061] figure 1 It shows a schematic flow chart of realizing online payment based on the wealth management computer in the present invention. Here, the wealth management computer refers to a home computer with an online payment function. Those skilled in the art should understand that, figure 1 Not only can it represent the structural composition of the payment system of the present invention, but it can also illustrate the specific flow chart of the payment system for online payment.
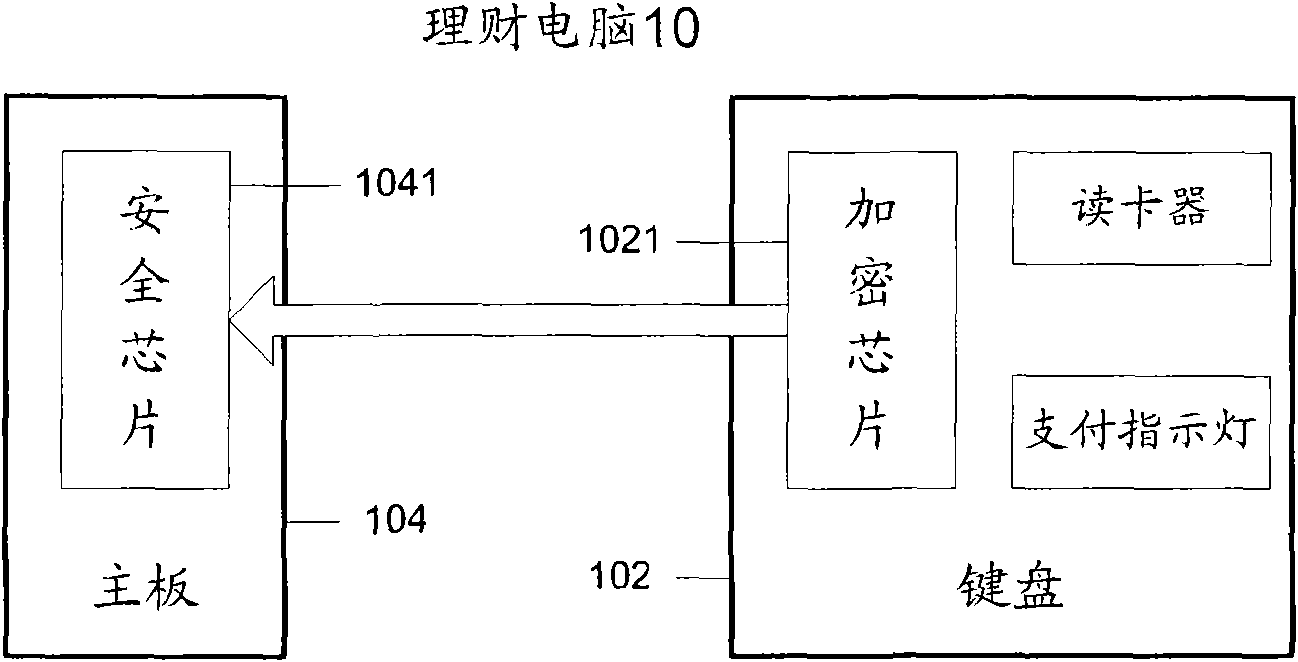
[0062] refer to figure 1 , the payment system includes: a wealth management computer 10 of a network user, a payment gateway 20 , a clearing transfer agency 30 , a card issuing bank 40 , and an online merchant 50 . Among them, the network user is a user of the card issuing bank and China UnionPay, holds a UnionPay card and is the owner ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com