Firewall strategy-generating method, device and system
A firewall strategy and strategy technology, applied in the transmission system, electrical components, etc., can solve the problems of low accuracy and complicated operation, and achieve high accuracy and simple effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
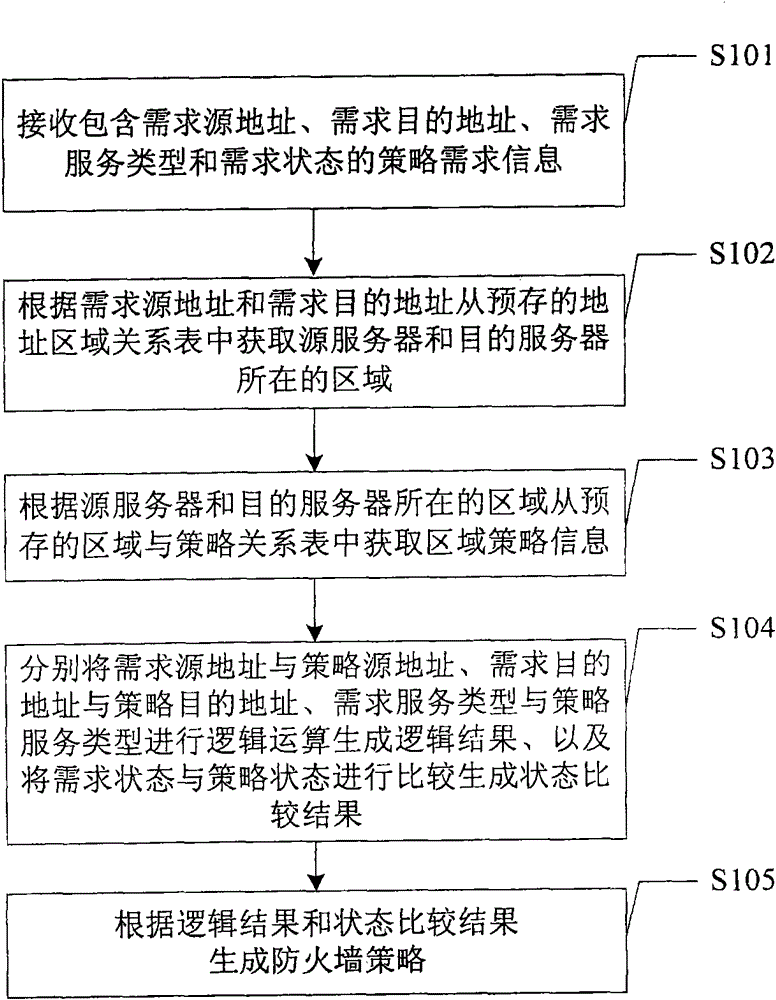
[0044] An embodiment of the present invention provides a method for generating a firewall policy, such as figure 1 As shown, the method includes:
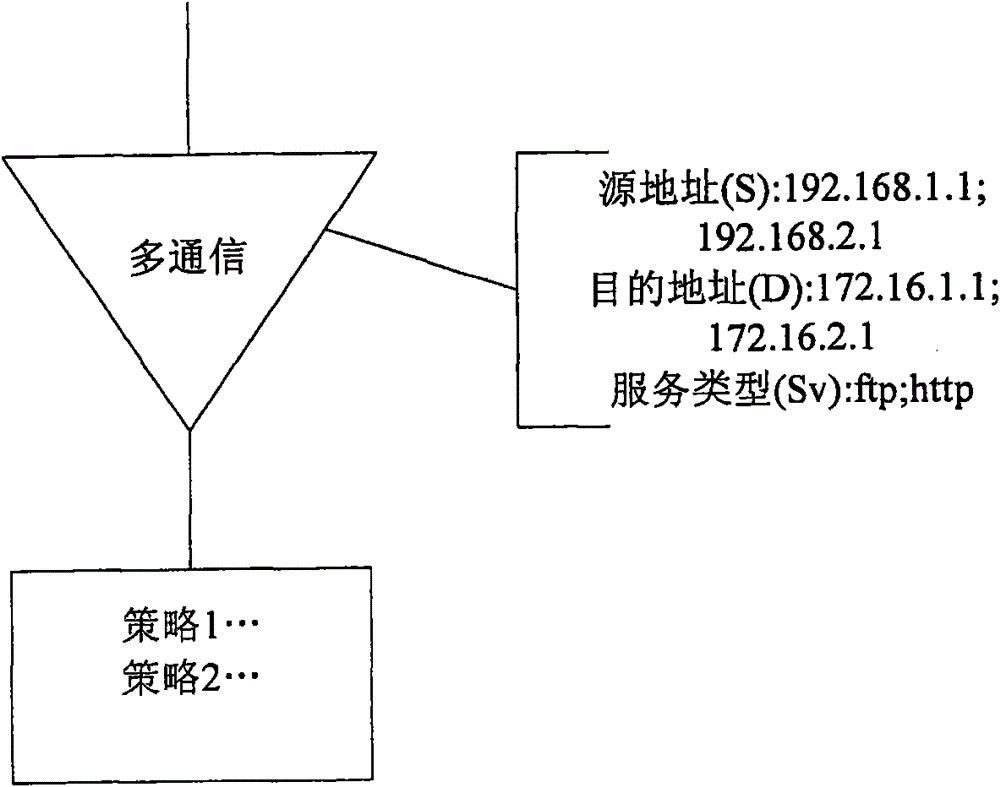
[0045] Step 101, receiving policy demand information including demand source address, demand destination address, demand service type and demand status;
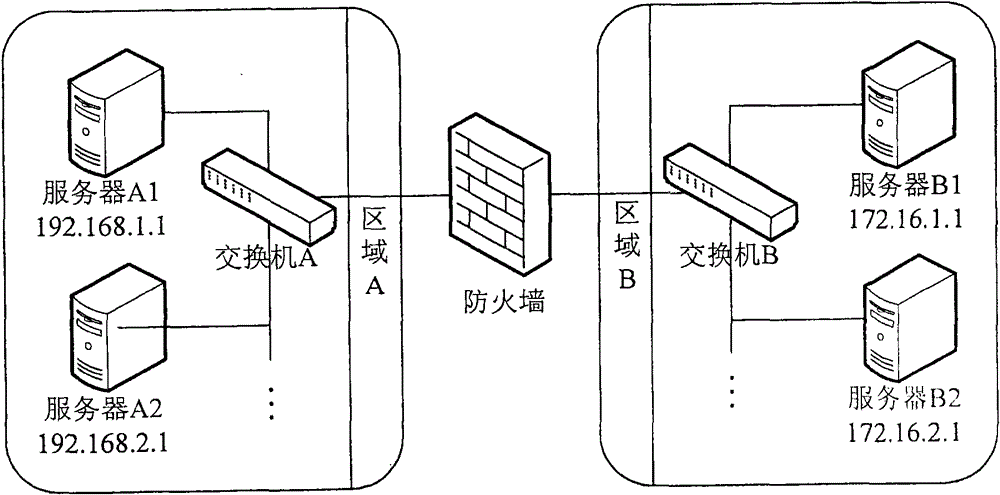
[0046] Step 102, obtain the area where the source server and the destination server are located from the pre-stored address area relationship table according to the demand source address and the demand destination address;
[0047] Step 103, according to the area where the source server and the destination server are located, obtain the area policy information corresponding to the area where the source server and the destination server are located, including the source address of the policy, the destination address of the policy, the type of policy service, and the policy status ;
[0048] Step 104: Perform logic operations on the demand source address and the policy source add...
Embodiment 2
[0125] The embodiment of the present invention also provides a firewall policy generation device, which is preferably used to implement the method in the first embodiment above, such as Figure 6 As shown, the device includes:
[0126] A demand information receiving unit 601, configured to receive strategic demand information including a demand source address, a demand destination address, a demand service type, and a demand status;
[0127] The area obtaining unit 602 is configured to obtain the area where the source server and the destination server are located from the pre-stored address area relationship table according to the demand source address and the demand destination address, wherein the address area relationship table is used to represent the correspondence between areas and addresses relation;
[0128] The area policy obtaining unit 603 is used to obtain the policy source address, policy destination address, policy service type and policy corresponding to the ar...
Embodiment 3
[0142] An embodiment of the present invention also provides a firewall policy generation system, including the firewall policy generation device as described in Embodiment 2, such as Figure 9 As shown, the system adopts a three-layer structure, which consists of presentation layer 1, functional logic layer 2, and data layer 3 from top to bottom. The three-layer structure is described below in order from bottom to top.
[0143] The data layer 3 is responsible for providing the configuration information of the firewall to the functional logic layer 2, which is divided into configuration files 31 and configuration information database 30. The data in the configuration information database is obtained by parsing configuration files in advance.
[0144] The functional logic layer 2 is used to simulate firewall devices according to the firewall configuration information, and provide different functions to the presentation layer 1. The functional logic layer 2 is further divided int...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com