Method and system for realizing safe bifurcation call session in IP multimedia subsystem
A technology for calling sessions and calling parties, applied in transmission systems, digital transmission systems, secure communication devices, etc., and can solve the problems that media streams cannot be encrypted and protected, no key negotiation mechanism is provided, and no real processing volume is solved. Achieve the effect of alleviating storage computing requirements, reducing computing processing capacity requirements, and reducing computing processing pressure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
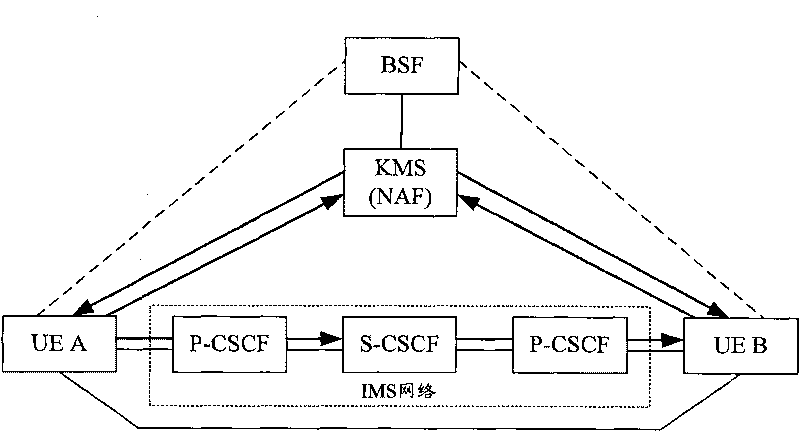
[0075] The KMS in this article does not specifically refer to a certain device, but is a general term for a trusted third party used to implement key management and distribution.
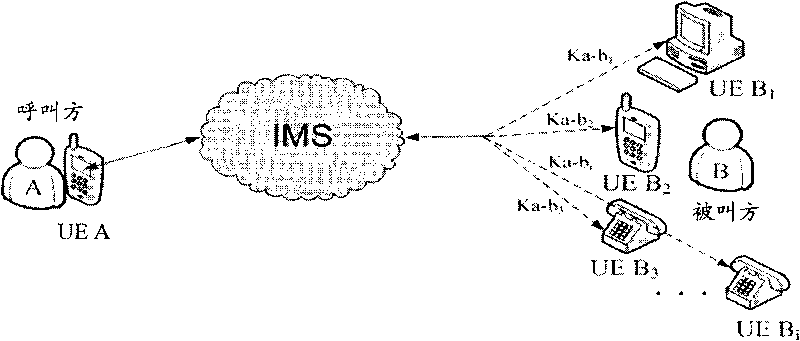
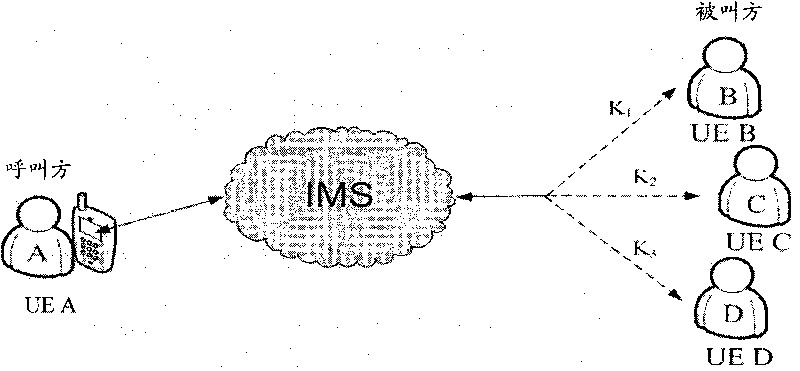
[0076] Figure 4 The flow chart of the method for realizing safe bifurcation call session of the present invention, as Figure 4 Shown, the inventive method comprises the following steps:
[0077] Step 400: the calling party and each called party respectively authenticate with the KMS and obtain their respective shared keys with the KMS.
[0078] The two parties in the call establish a secure trust relationship with KMS through GBA or other methods; through the establishment of the trust relationship between the two parties in the call and KMS, the two parties in the call also establish a mutual trust relationship, that is, a shared key. The specific implementation of this step belongs to the technical means commonly used by those skilled in the art, and will not be repeated here. A shared key is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com