Hierarchical type mobile internet security monitoring and protecting system
A mobile Internet and security monitoring technology, applied in the field of layered mobile Internet security monitoring and protection system, can solve problems such as unsatisfactory solutions, no end-to-end security countermeasures, and lack of overall solutions, so as to ensure business Safety and information security, and the effect of improving safe operation and management capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
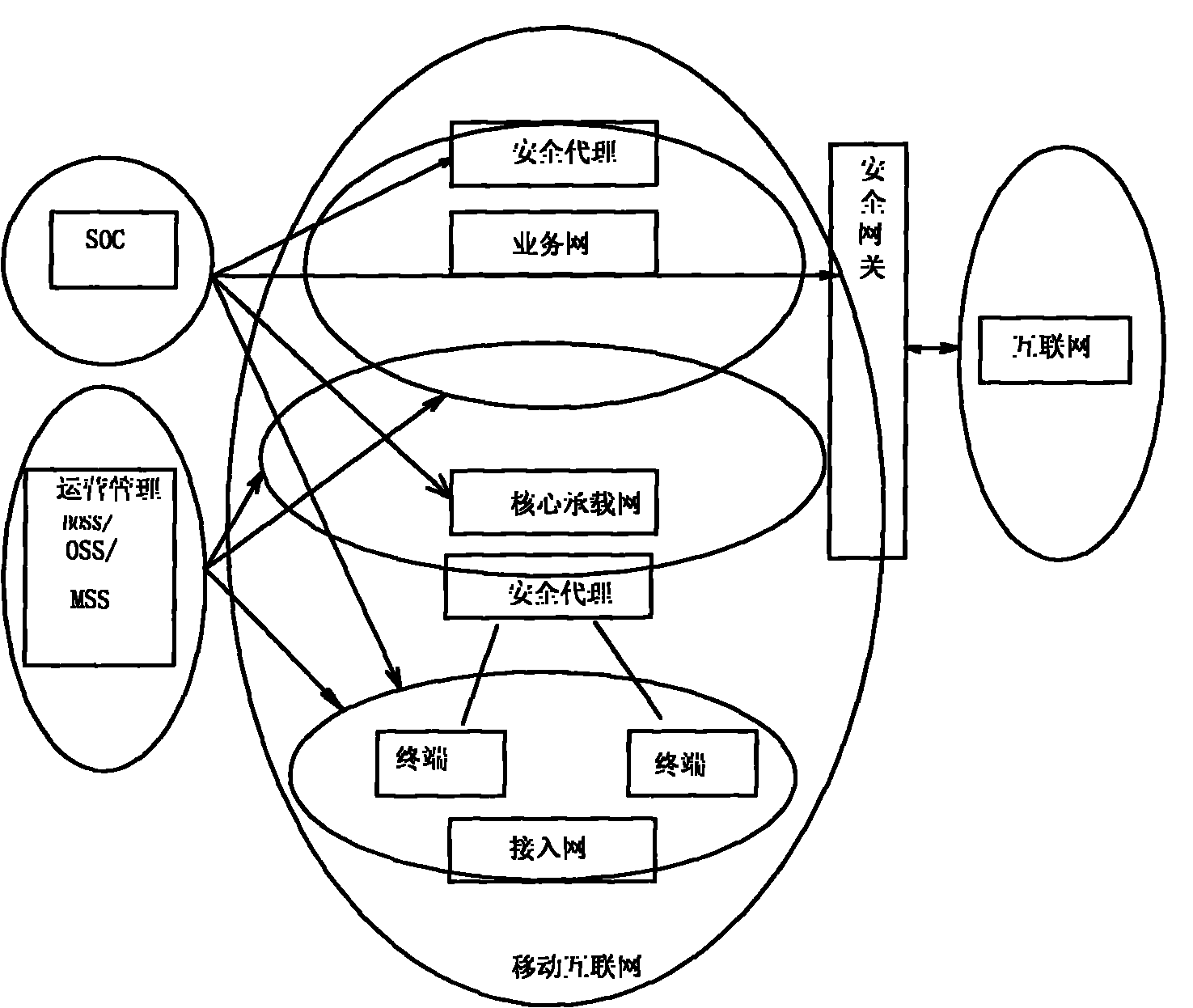
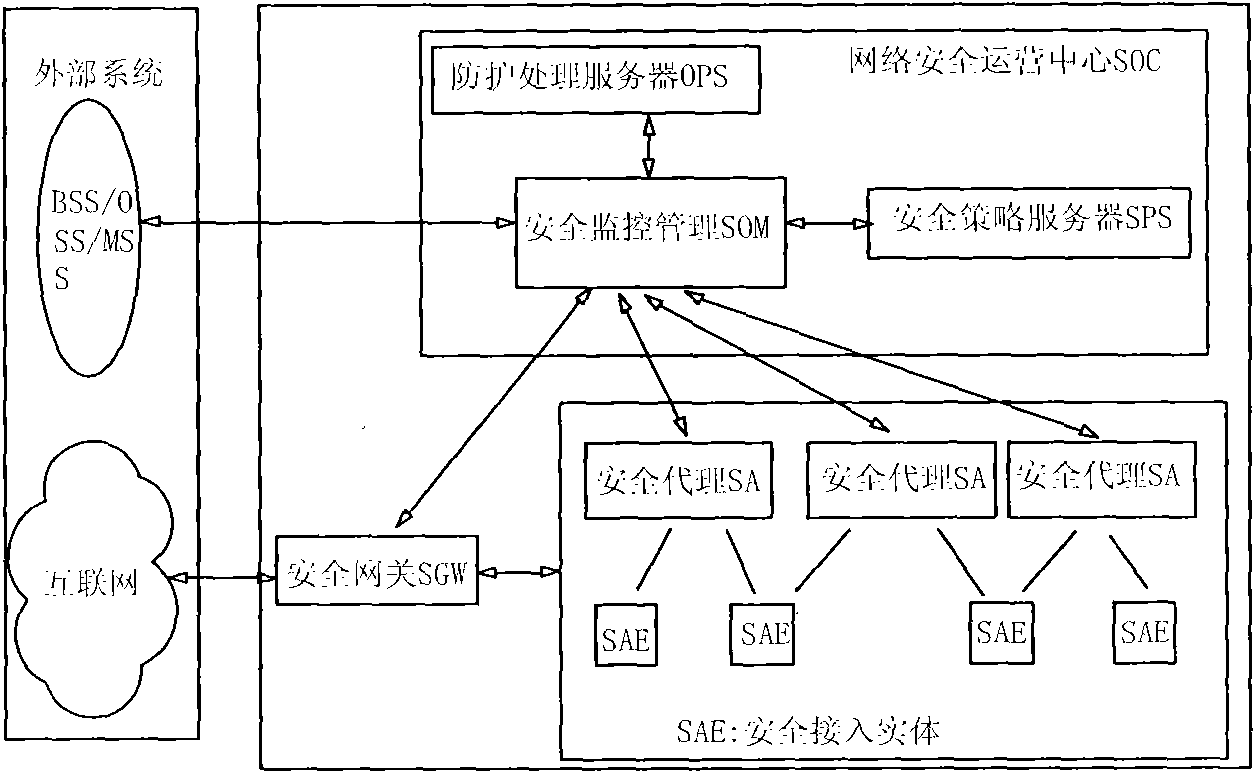
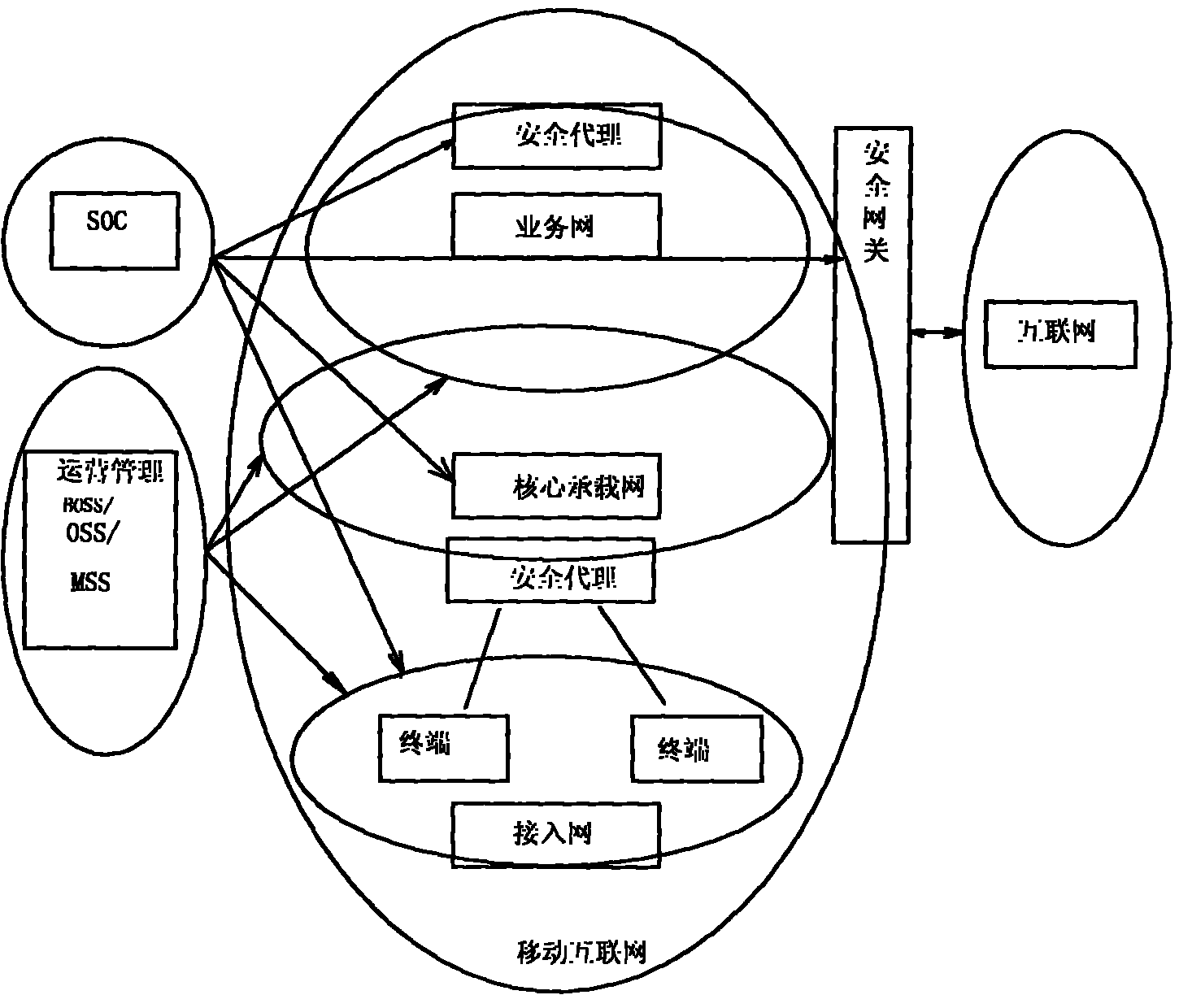
[0020] The layered mobile Internet security monitoring and protection system of the present invention will be described in detail below with reference to the accompanying drawings.
[0021] The layered mobile Internet security monitoring and protection system of the present invention includes a modular system structure of three levels and four basic functional groups, so that the entire monitoring and protection system has flexible deployment, strong scalability, convenient upgrade, and complete end-to-end Features such as deep protection. It can be adapted to all levels of mobile Internet from terminal, access network, core network to service network, and can be used to build a complete security monitoring and protection system;
[0022] The intelligent performance of each module ensures that it has a strong security monitoring autonomy function, and can monitor and protect the operating process and resource objects within its jurisdiction according to its own configuration. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com