Parallel computing method capable of expanding precision Logistic chaotic sequence
A logistic equation and chaotic sequence technology, applied in the field of network security and data security, can solve problems such as the difficulty of parallel algorithm design tasks, the decline of dynamic characteristics of chaotic systems, and the difficulty of parallel program design.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
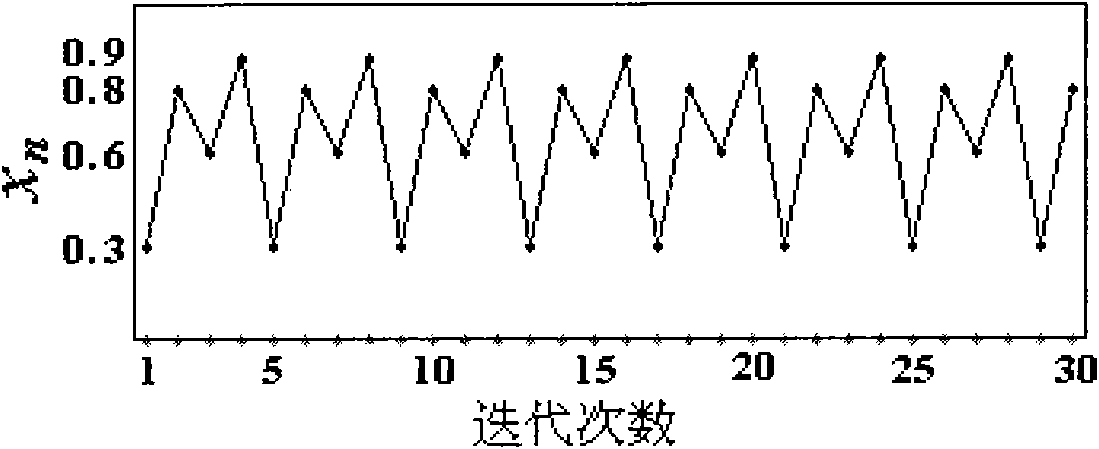
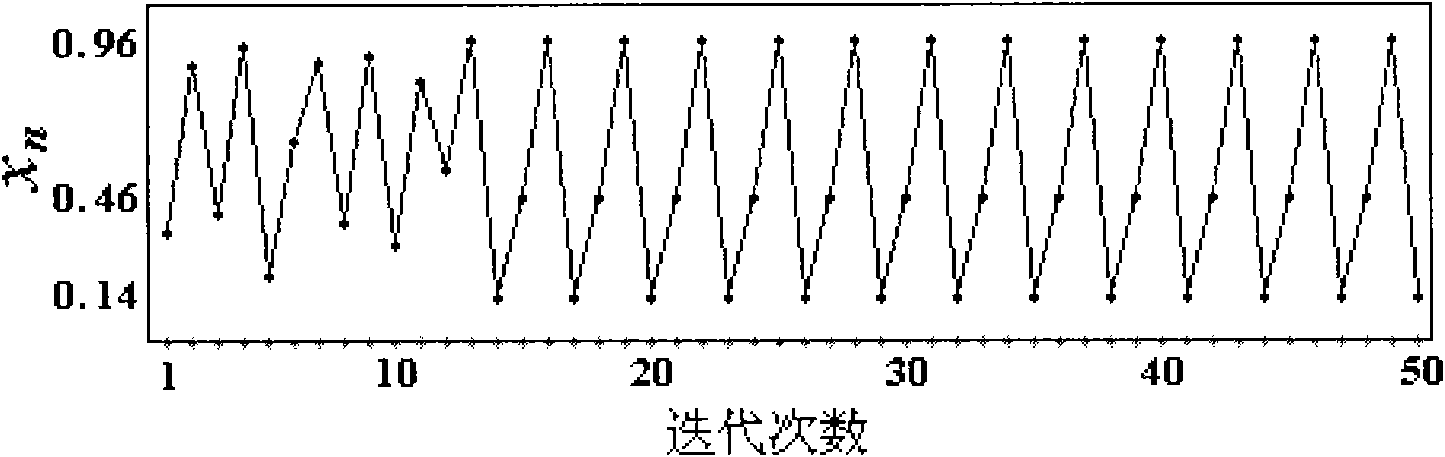
Examples
example 1
[0085] Example 1: Implementation based on Message Passing Interface (MPI) and modular design.
[0086] The implementation steps based on message passing interface (MPI) and modular design are as follows: Figure 4 as shown in:
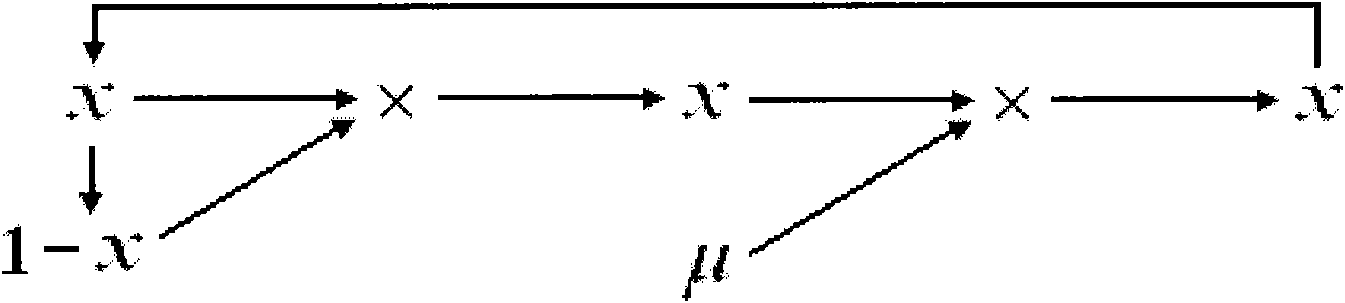
[0087] 1. The initial parameter x of the Logistic equation 0, the μ integer is quantized and stored in a one-dimensional array, set the required precision or specify the number of iterations; the parallel system obtains the information of the currently available slave processors, or specifies the number of slave processors in the parallel system. After MPI initialization using the MPI_Init() function, you can use the MPI_Comm_rank() function to obtain the number of the processor in the parallel system, ie p i . You can use the MPI_Comm_size() function to get the number of processors in the system.
[0088] 2. The first part of the parallel computing algorithm: x=x×(1-x), using the matrix to save the calculation intermediate results, modifying the l...
example 2
[0099] Example 2: Realize the encryption of the image.
[0100] The basic idea of the algorithm based on the scalable precision chaotic random sequence encryption image is to divide the image into several parts (data slices), assuming that the length of the data slice is equal to the number of keys that can be generated by the generated chaotic random sequence. To implement byte encryption, the specific steps are as follows:
[0101] 1. The initial parameter x of the Logistic equation 0 , μ, the number of data slices, etc. can be used as part of the password input by the user. initial parameter x 0 , μ integer quantization saved into a one-dimensional array.
[0102] 2. The first part of parallel computing algorithm: x=x×(1-x);
[0103] 3. The second part of parallel computing algorithm: x=μ×x;
[0104] 4. If the accuracy reaches the number of generated keys, go to step 5; otherwise, go to step 2;
[0105] 5. The obtained chaotic sequence needs to be combined into a ke...
example 3
[0110] Example 3: Network encryption communication model.
[0111] The chaotic encryption algorithm is a symmetric encryption algorithm, that is, the same algorithm is used at the sending end and the receiving end for encryption / decryption.
[0112] The sender and receiver first determine the initial parameter x of the Logistic equation 0 , μ, and the precision or number of iterations, they can be used as part of the password entered by the user. The sending end can encrypt the information to be transmitted, and then transmit it to the other party through the network. After receiving the information, the receiving end performs decryption processing to restore the information.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com