Protection method and system of virtual private LAN (Local Area Network) service (VPLS)
A virtual private and protection system technology, applied in the field of communication, can solve problems such as slow business switching, short-term traffic interruption, interruption, etc., and achieve the effects of improving reliability, shortening switching time, and good protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
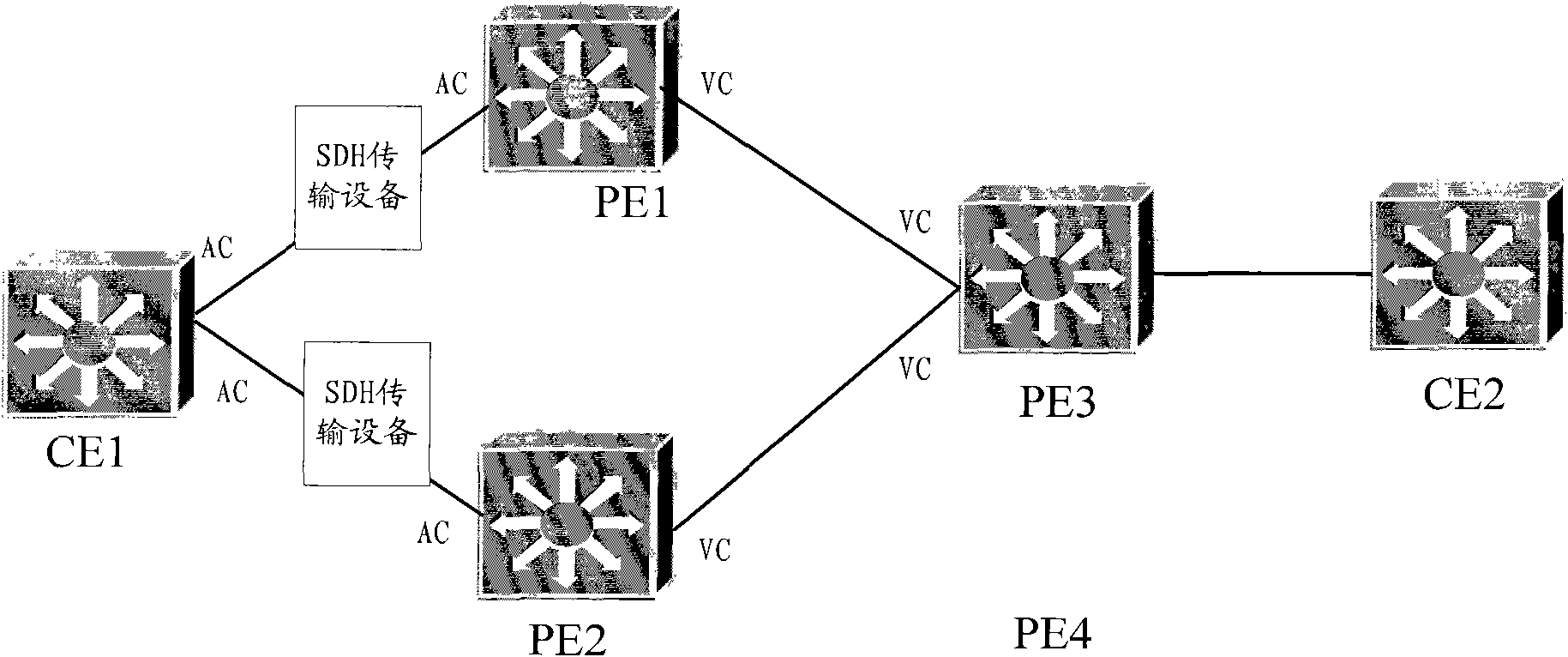
[0040] A typical network structure of a virtual private area network is as follows: figure 1 As shown, it includes user edge equipment CE1, CE2, carrier edge equipment PE1, PE2, and PE3, among which PE1 is the active PE, PE2 is the backup PE, the route from CE1 to PE1 to PE3 is the active route, and the route from CE1 to PE2 to PE3 It is a backup route. When the network is working normally, services are transmitted from CE1 to CE2 via PE1 and PE3.
[0041] CE1 is connected to both PE1 and PE2, which means that CE1 is dual-homed to PE1 and PE2.
[0042]The side where the CE is connected to the PE is called the AC side of the CE, the side where the PE is connected to the CE is called the AC side of the PE, and the side where the PE is connected to the PE is called the VC side of the PE.
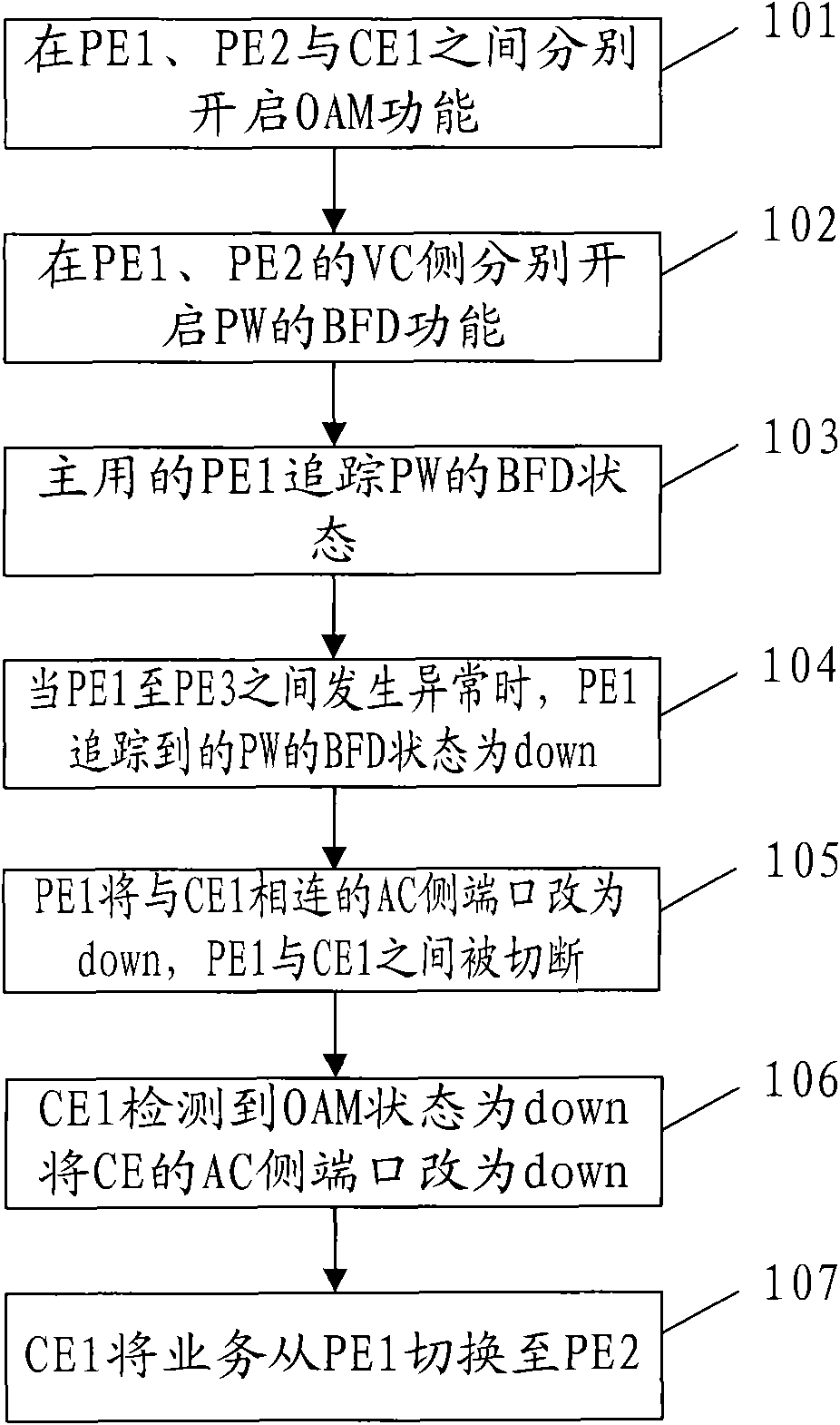
[0043] Such as figure 2 As shown, an embodiment of the above-mentioned VPN service protection method includes the following steps:
[0044] Step 101, enable the OAM function between PE1, PE...
Embodiment 2
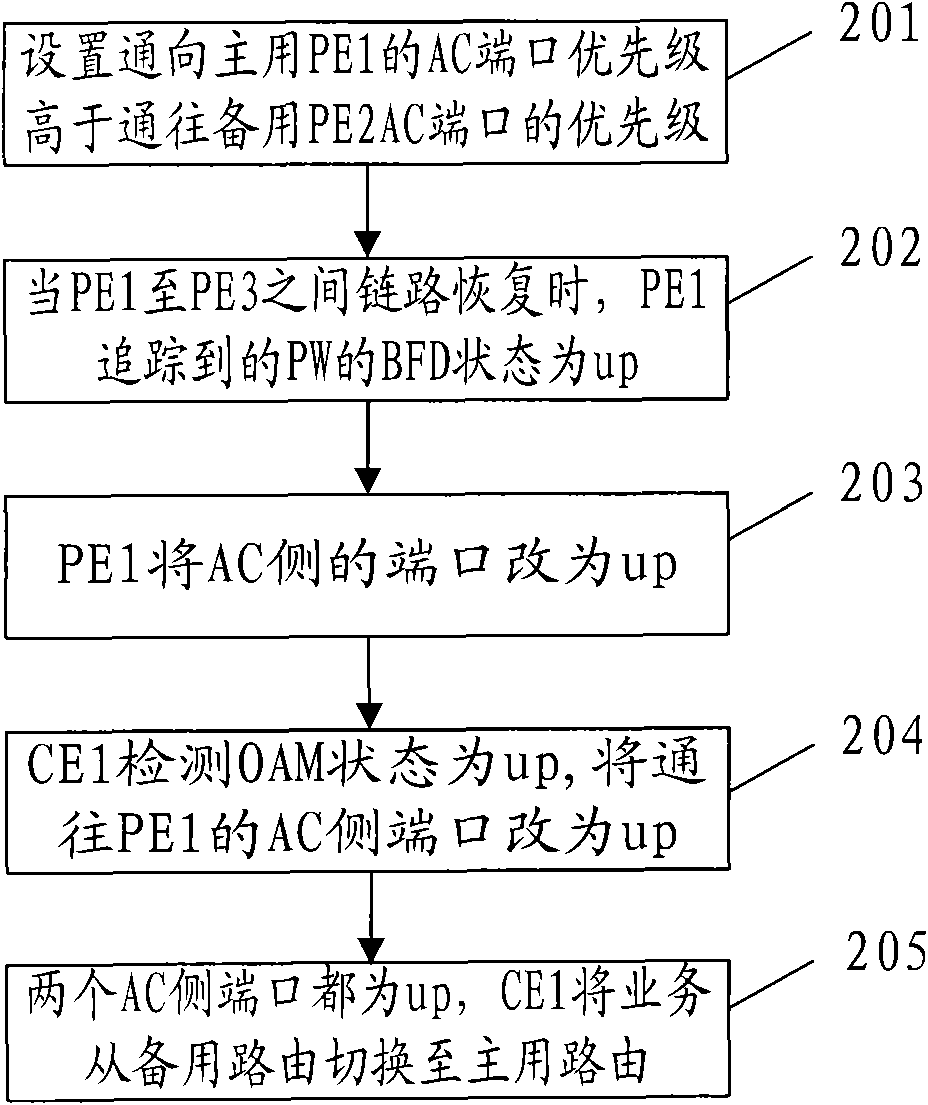
[0057] Such as image 3 As shown, in the virtual private local area network of Embodiment 1, because the link between PE2 and PE3 is abnormal, the service is switched from the active route to the backup route. When the link between PE2 and PE3 is restored, generally Next, the service needs to be switched to the active route by the backup route, at this time, an embodiment of the protection method of the virtual private network comprises the following steps:
[0058] Step 201, setting the priority of the AC port of CE1, the priority of the AC port leading to the active PE1 is higher than the priority of the AC port leading to PE2.
[0059] Step 202, when the link between PE1 and PE3 of the active route is restored, the BFD state of the PW tracked by PE1 is up.
[0060] In step 203, PE1 changes the state of the port on the AC side to up.
[0061] In step 204, CE1 detects that the OAM state is up, and changes the state of the port on the AC side leading to PE1 to up.
[0062] ...
Embodiment 3
[0064] Such as Figure 4 As shown, in the virtual private local area network in Embodiment 1, the user can also set it so that when the service is switched from the active route to the standby route, the service will not be switched to the active route even if the active route is restored. Only when the standby route fails, the service is switched to the active route. At this time, an embodiment of the protection method of the virtual private local area network comprises the following steps:
[0065] Step 301, setting the priority of the AC port of CE1, the priority of the AC port leading to the active PE1 is equal to the priority of the AC port leading to PE2.
[0066] In step 302, the service runs on the backup route, and the active route is restored, that is, the link between PE1 and PE3 is restored, and the BFD state of the PW traced by PE1 is up.
[0067] In step 303, PE1 changes the state of the port on the AC side to up, and the link between CE1 and PE1 returns to norm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com