Triple authentication method based on block cipher
A block cipher algorithm and re-authentication technology, which is applied in the field of triple authentication based on block cipher algorithm, can solve problems such as not adapting to application requirements, and achieve the effects of improving security strength, improving security performance, and increasing security strength
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
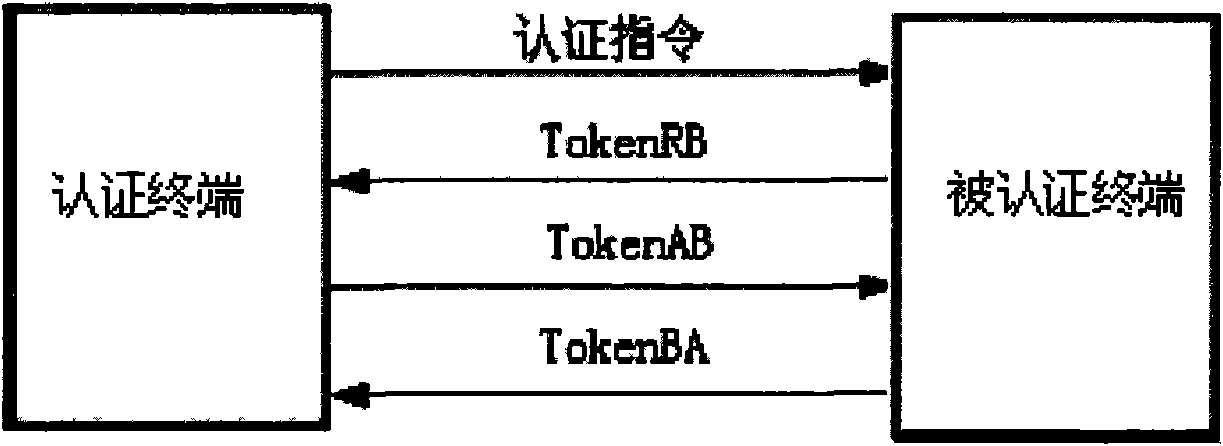
[0026] see figure 1 and combine figure 2 As shown, the specific implementation details of the present invention will be illustrated through the triple authentication process of the non-contact logical encryption card using the DES (Data Encryption Standard) algorithm.
[0027] The DES algorithm is a public block cipher algorithm selected by the Federal Information Processing Standard of the US federal government. The entry parameters of the DES algorithm have three Key, Data and Mode. Among them, Key is 8 bytes and 64 bits in total, which is the working key of the DES algorithm; Data is also 8 bytes and 64 bits, which is the data to be encrypted or decrypted; Mode is the working mode of DES, divided into encryption or Decrypt two.
[0028] figure 2 It is a non-contact logical encryption card using an embodiment of the present invention, the non-contact logical encryption card 100 includes:
[0029] RF component 110, used for receiving and sending a radio frequency (RF) ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com