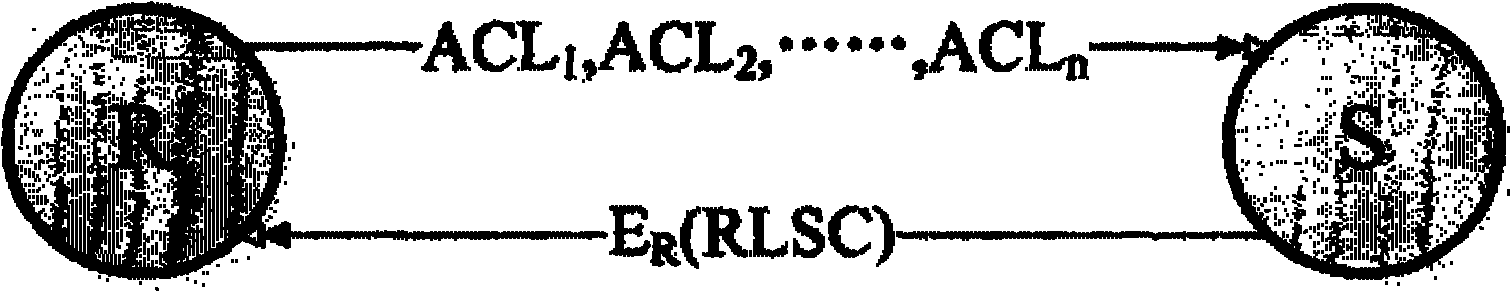Method for guaranteeing security of single-transceiver time-slot type distribution CR MAC (Cognitive Radio Multiple Access Control) protocol
A technology of time slot and protocol security, which is applied in the direction of security devices, electrical components, wireless communication, etc., and can solve problems such as no implementation plan given
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The technical solutions of the present invention are further described below with reference to the accompanying drawings.
[0036] When the sender S wants to send data to the receiver R, both parties first generate a random number R respectively S and R R and use the respective H x1 Calculate your own random number n times to get the final value and , where n is large enough. Afterwards, both parties exchange their respective public key certificates and final values. and , for H x1 Validation of all forward values. Public key certificates are only delivered on RC channels.
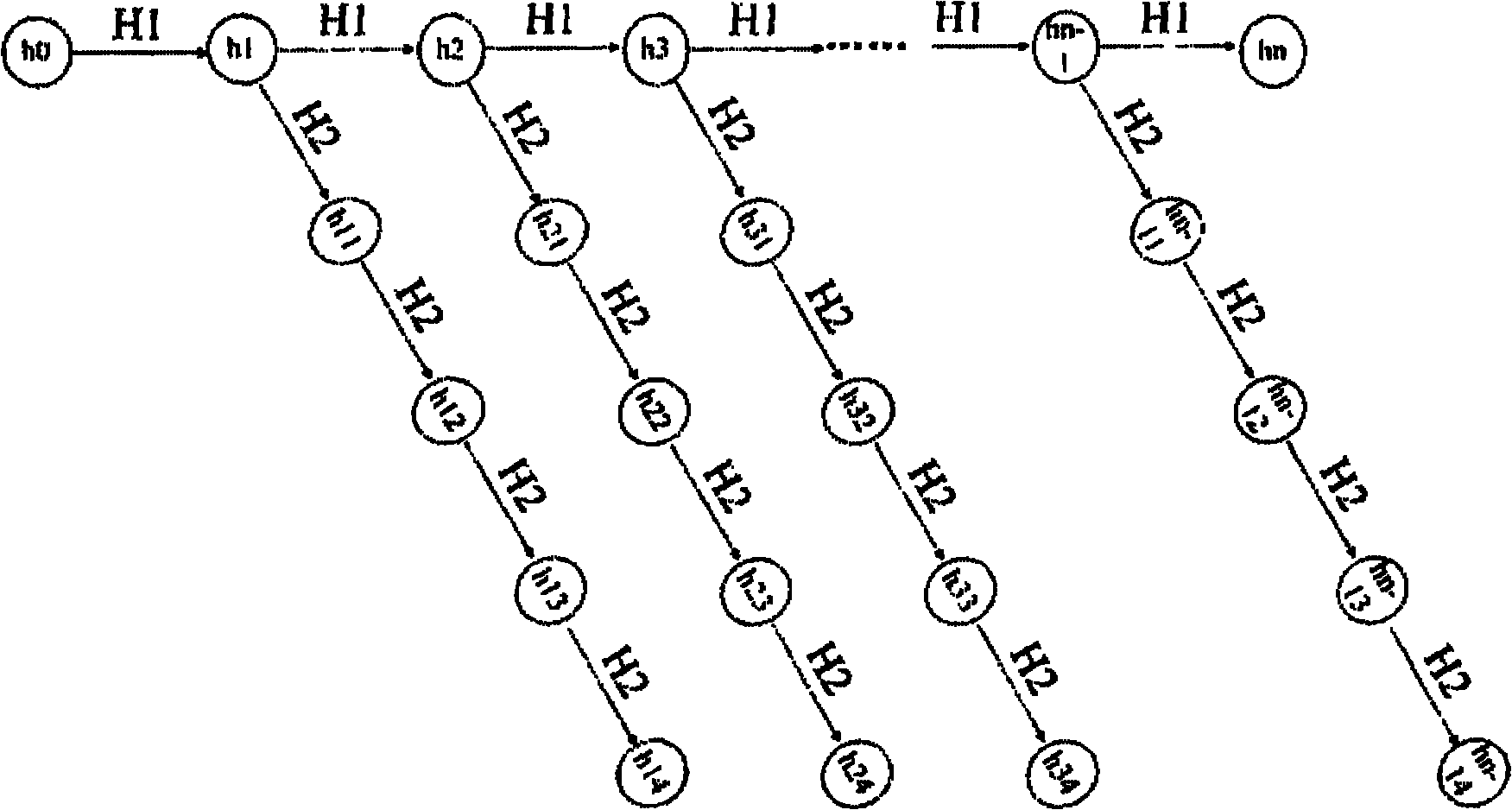
[0037] Before exiting the current channel for the ith time, S and R will and Encrypted and exchanged with the other party's public key, where is to use H x2 right Calculate the final value after m times, where m is large enough. The above process as image 3 shown.
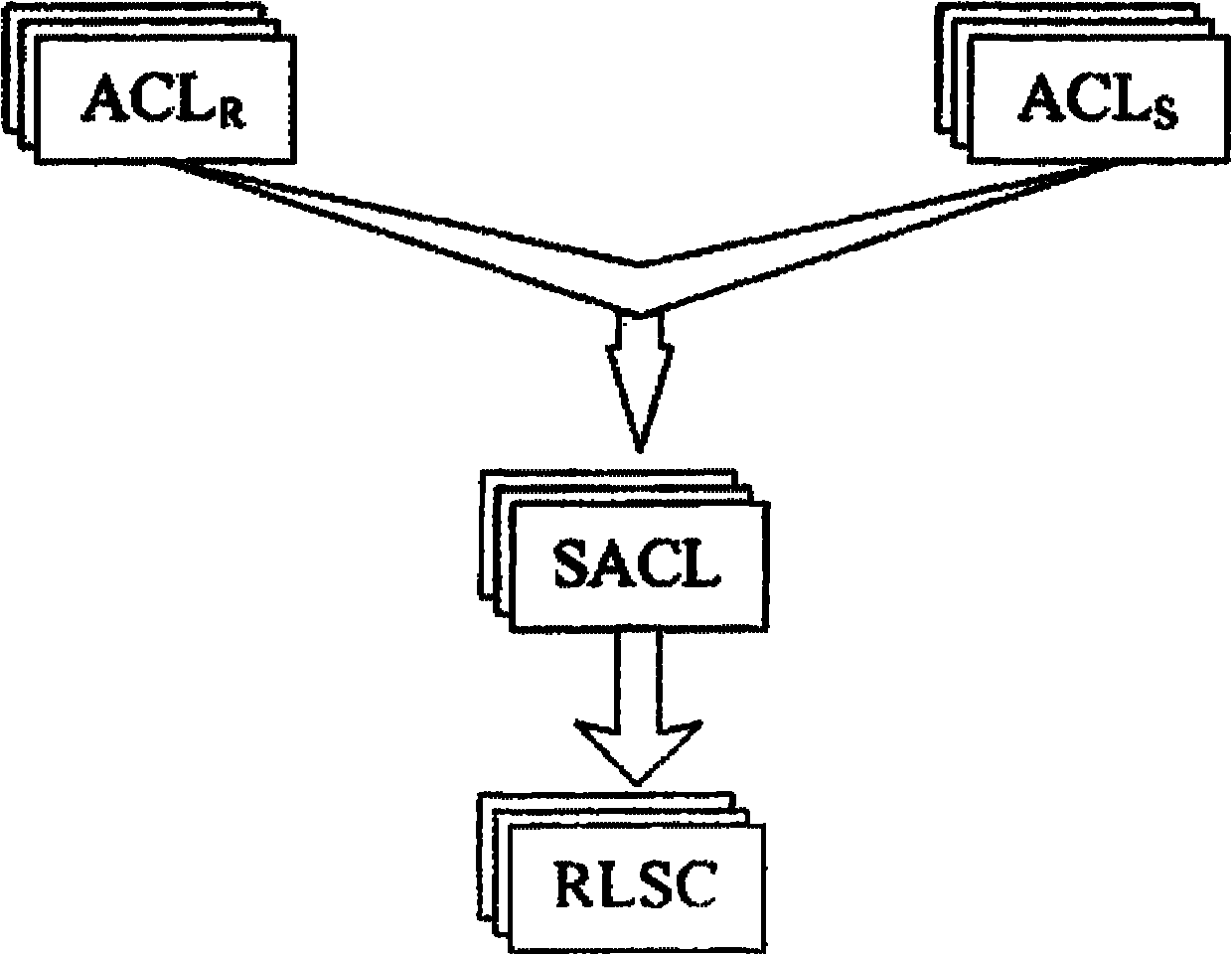
[0038] During data transmission, R periodically sends its own ACL information to S. When the primary user appea...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com