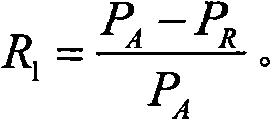Trust management system based trusted reconstructing method of IP routing protocol
A technology of trust management and IP routing, which is applied in the field of communication, can solve problems such as blind trust and vulnerability of routing protocols to security vulnerabilities
Inactive Publication Date: 2010-11-17
BEIJING UNIV OF POSTS & TELECOMM
View PDF3 Cites 22 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
The correct operation of the OSPF protocol depends entirely on the trust of neighboring routers and their information, but this trust is blind, routers will inevitably spread accidental or premeditated wrong routing information, and the routing protocol itself is vulnerable to attack security breach
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
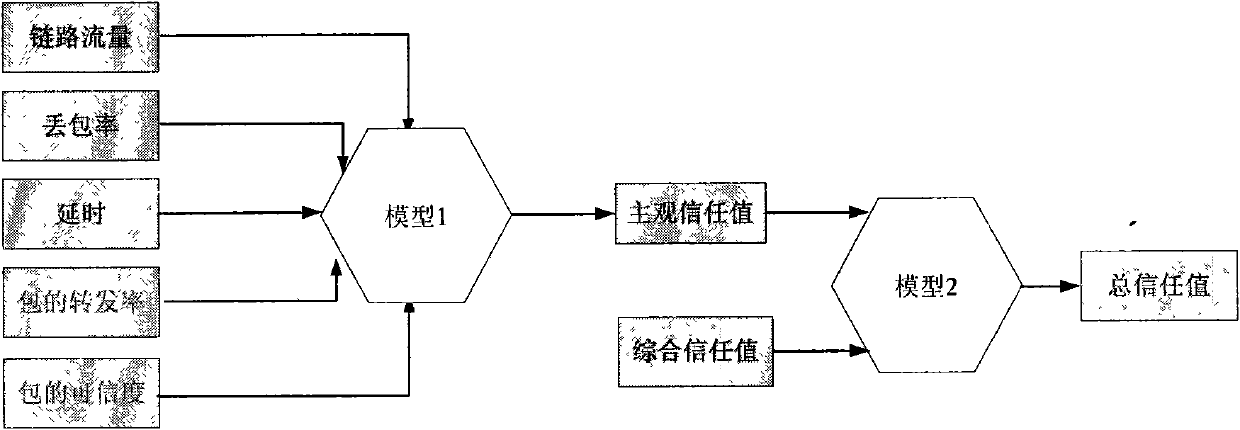
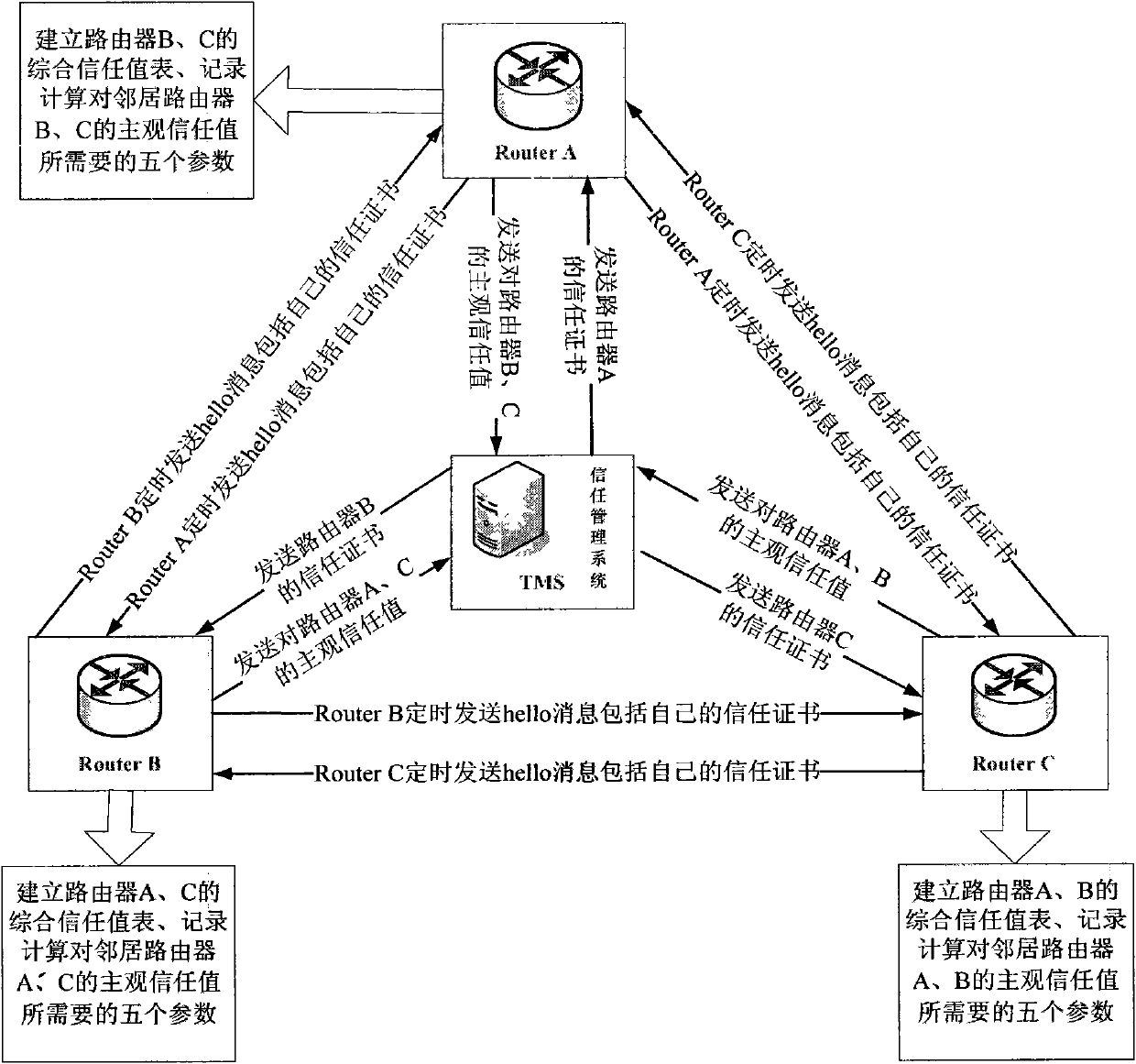
The invention discloses a trust management system based trusted reconstructing method of an Open Shortest Path First (OSPF) routing protocol, which comprises the following steps of: (1) before each router is added into a network, registering to the trust management system, and sending corresponding trust certificates to the routers by the trust management system, the trust certificates including comprehensive trust values of the routers and each being calculated according to safe parameters and configuration parameters of the routers and all the subjective trust value of the neighbor router to the routers by the trust management system; (2) transferring the trust certificates among the routers through hello information, wherein an adjacency relation is not established for the router without the trust certificate, all the routers in the network are ensured to have own trust certificates; (3) each router calculating the subjective trust value of the neighbor router based on network real time parameters including link flow, packet loss probability, retardation, transmission rate of the packet and reliability of the packet, during an interactive work with the neighbor router, calculating a total trust value of the neighbor router by using the comprehensive trust value and the subjective trust value of the neighbor router, and modifying a metric field of a link-state announcement Router_LSA packet as the total trust value and synchronizing a link-state data base;(4) modifying a Dijkstra algorithm, using a reciprocal of the total trust value between the routers as the parameter for the arithmetic computation, selecting the router with higher trust value to generate a shortest path tree, and forming a trust routing list; (5) periodically reporting the subjective trust value of the neighbor routers to the trust management system by each router, simultaneously obtaining the parameter required for computing the subjective trust value, updating the trust certificate of each router at fixed time, and eliminating the router with the overdue trust certificate out of the network to maintain the topological structure of the whole network.
Description
technical field The invention relates to the field of communication technology, in particular to a trusted transformation method of an IP routing protocol based on a trust management system. Background technique The widespread use of the Internet poses a huge challenge to the security protection of information. Routing protocols are used to distribute information about network topology among routers, and routers find the best route according to the topology information, and realize the forwarding of various data packets in the network. Whether the routing information is correct or not seriously affects the efficiency of message transmission in the network, and can even affect the message so that it cannot reach the destination, and even cause the entire network to be paralyzed. A secure routing protocol is one of the important factors to ensure network security, so the security transformation of routing protocols has become one of the current research hotspots. OSPF proto...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Applications(China)
IPC IPC(8): H04L12/56H04L29/06H04L45/02H04L45/74
Inventor 孙斌谷利泽郑世慧杨榆陈波郭玲玲李道丰钮心忻
Owner BEIJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com