Security isolation and monitoring management method of USB mobile storage media
A mobile storage medium, monitoring and management technology, applied in the direction of internal/peripheral computer component protection, etc., can solve the problem of unable to solve the problem of safe collection of external data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The method of the present invention is described in detail below with reference to the accompanying drawings.
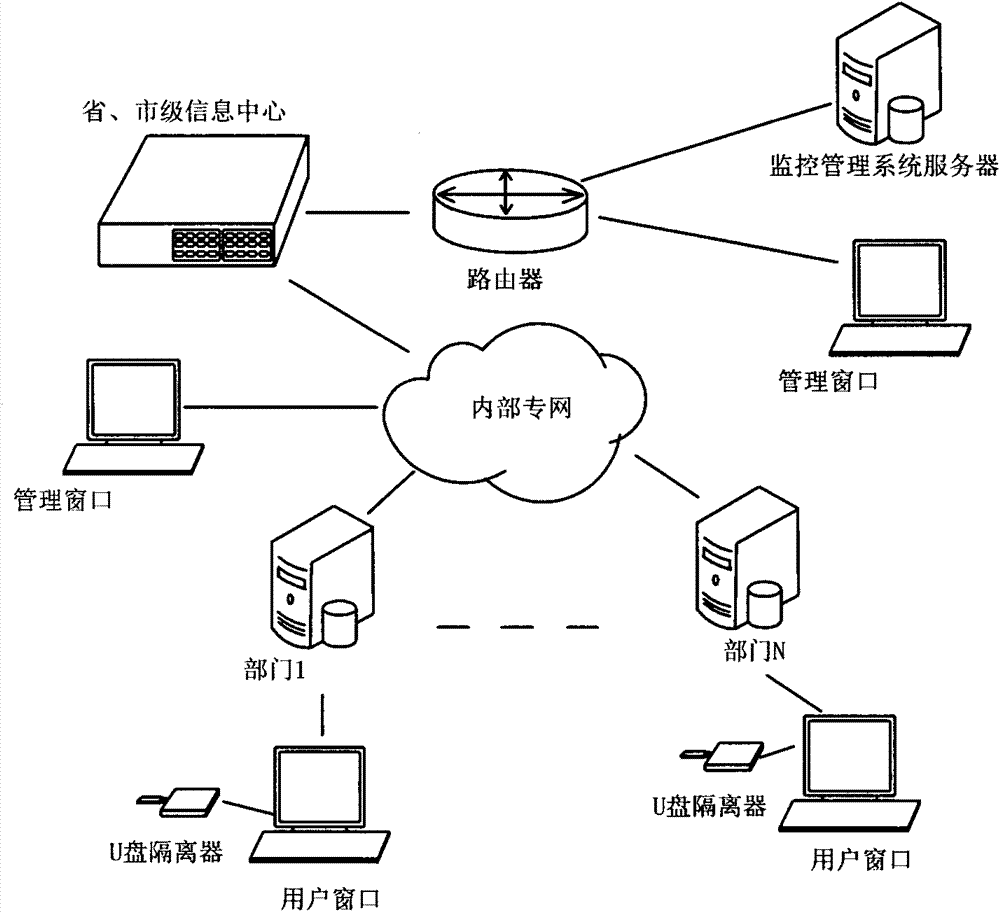
[0023] The method of the present invention, system network topological structure is referring to accompanying drawing 1, deploys a monitoring and management system server in the internal network, as the management center and the database center of the system of the present invention, the administrator can log in this system server by browser, to equipment Configure and manage with personnel, the server provides web service interfaces to the client program, and the client program communicates and exchanges data with the server by calling these interfaces. The client program is also connected with the monitoring and management system through the internal private network.
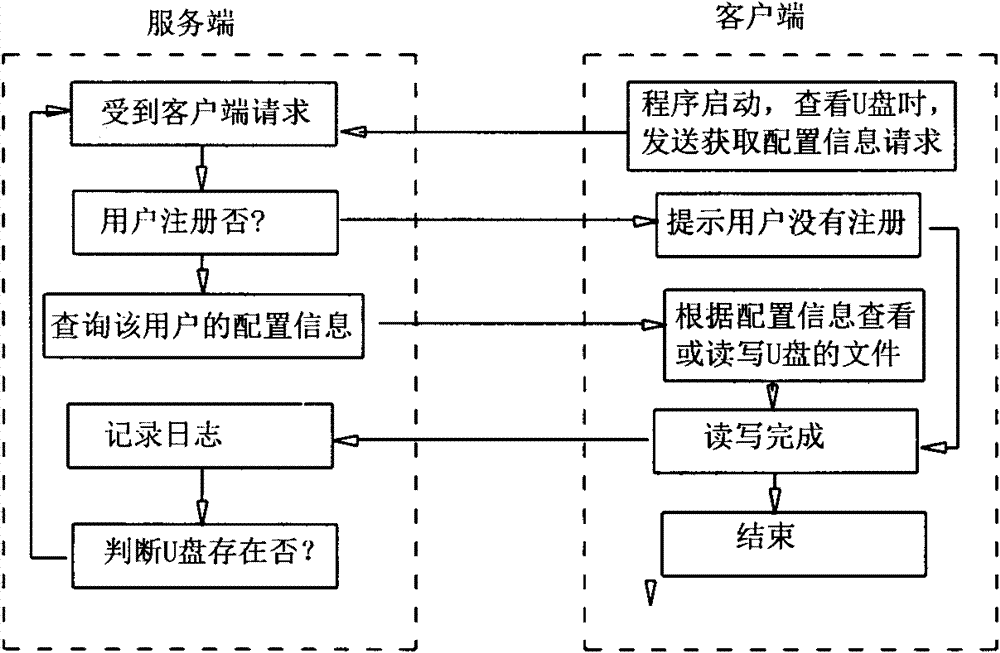
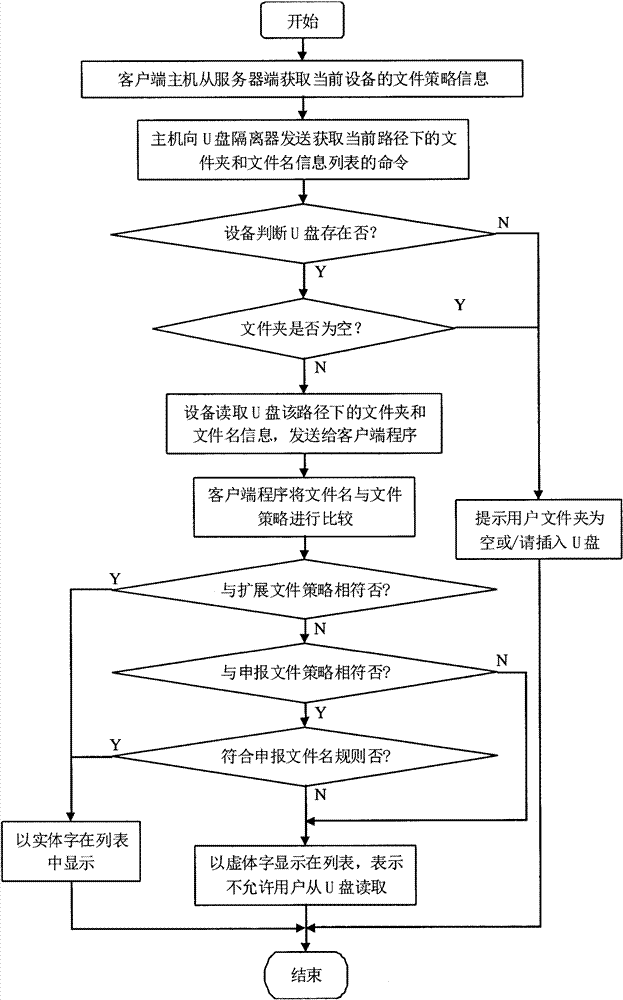
[0024] The workflow of the system can be found in the appendix figure 2 And attached image 3 , first, the client program requests the server to obtain information such as the file security...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com