Method and system for detecting abnormal service behaviors
A business system and anomaly detection technology, applied in the field of information security, which can solve the problems of cumbersome security configuration rules, missed attack behaviors, and inability to formulate reasonable security configuration rules.
Inactive Publication Date: 2010-12-01
BEIJING VENUS INFORMATION TECH +1
View PDF0 Cites 59 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
This solution can detect some abnormal business behaviors, but it has the following deficiencies: First, relying on managers to formulate a complete set of security configuration rules is too cumbersome. Once an attack behavior not included in the rules occurs, it will lead to Secondly, some attack behaviors cannot be found from one or several database access behavior records, such as the modification frequency of a certain access record within 24 hours, and it is impossible to formulate reasonable security configuration rules for this type of attack behavior , detect by analyzing one or several database access records
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
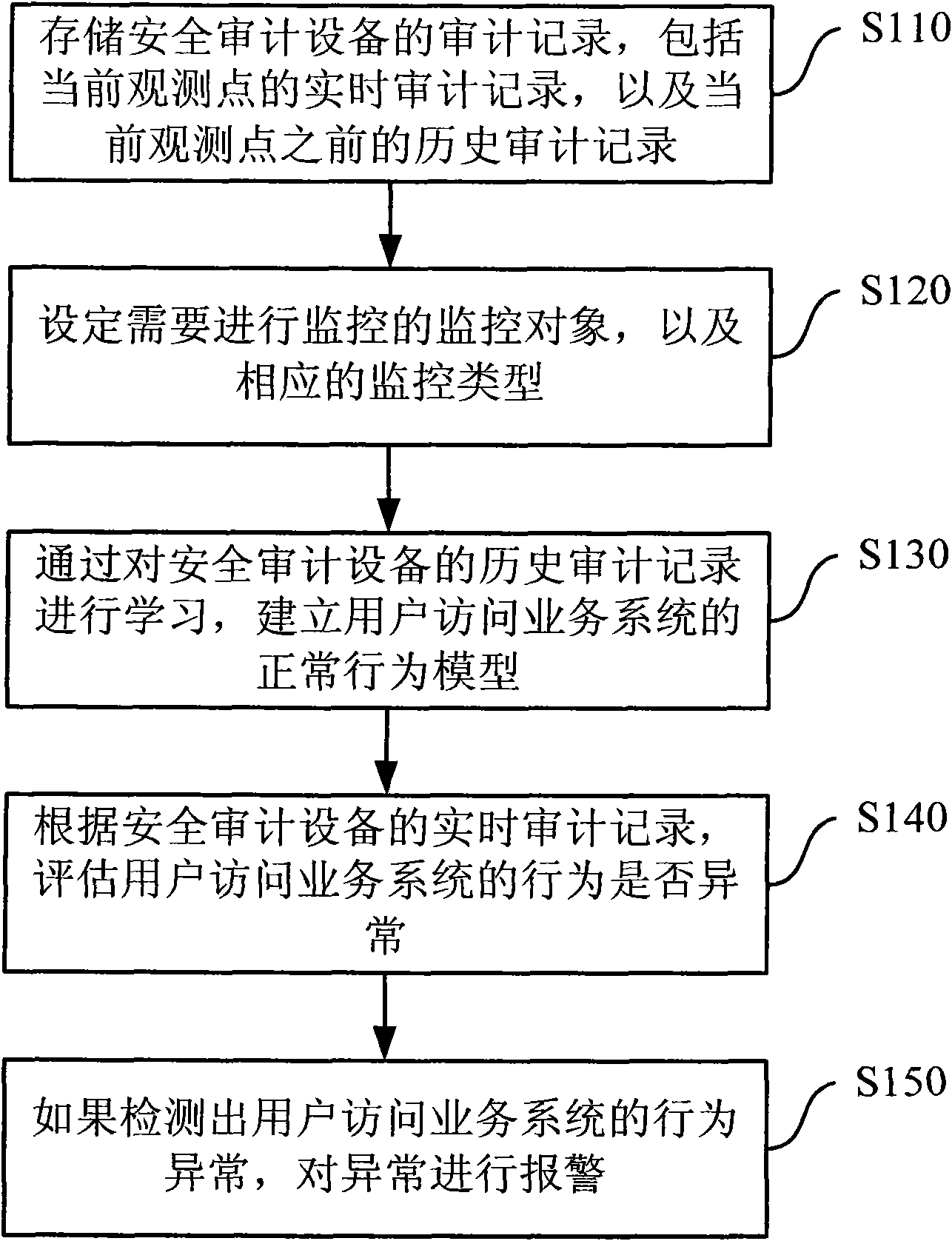
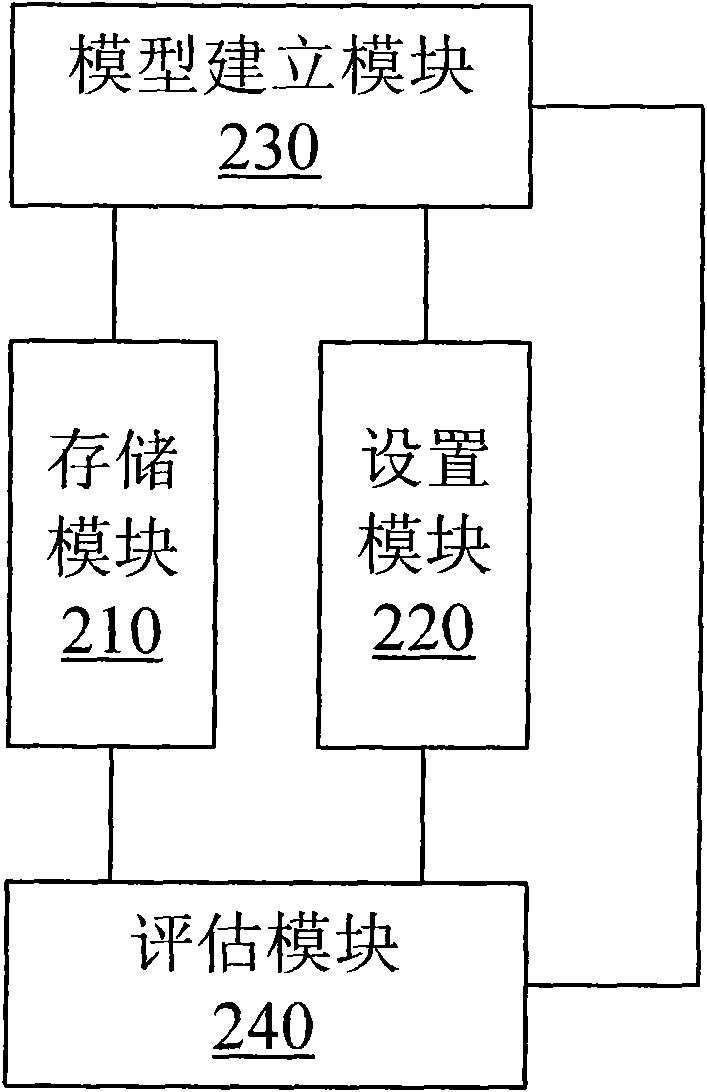
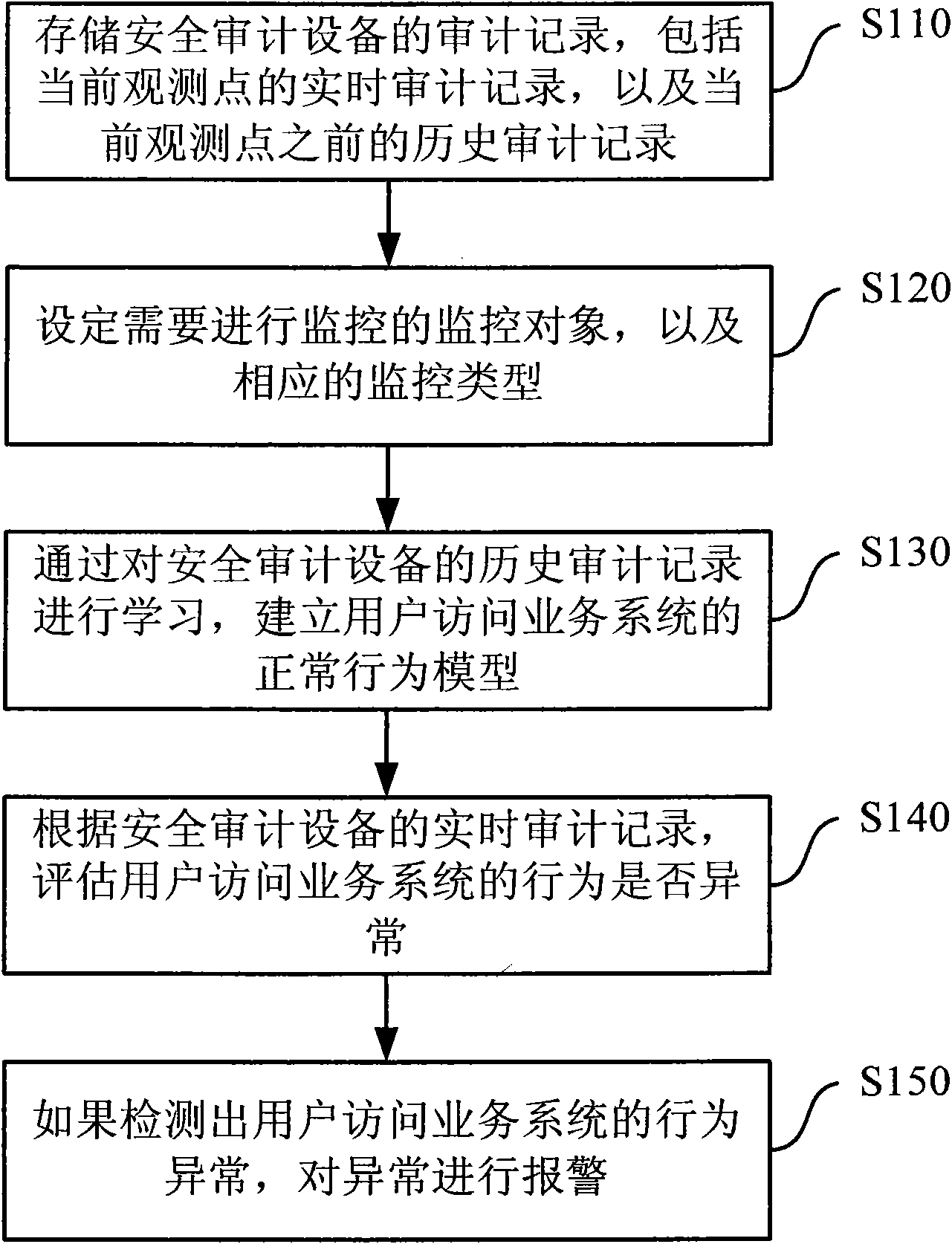
The invention provides a method for detecting abnormal service behaviors, which comprises the following steps of: establishing a model of normal service system access behaviors of users according to historical audit records prior to a current detection point of safety audit equipment; and analyzing real-time audit records of the safety audit equipment, comparing the real-time audit records with the normal behavior model, and judging whether the service access behaviors of the users are abnormal or not. The invention also provides a system for detecting abnormal service behaviors. The method and the system for detecting abnormal service behaviors can detect attack behaviors, which are legal in terms of service flow, but still bring about destruction to a service system actually, according to audit records of the safety audit equipment.
Description
A method and system for abnormal business behavior detection technical field The invention relates to the field of information security, in particular to a method and system for detecting abnormal business behavior. Background technique With the development of information technology, Internet-oriented business systems with database servers as the core have been increasingly widely used, such as online banking systems and electronic ticket booking systems. Since the key data of the business system is stored in the database server and is closely related to the entire business process, it is particularly important to ensure the information security of the database server. In order to better protect the database server, network security audit equipment has been widely used. It can monitor and record the user's access information to the server in real time, and once any illegal access behavior (such as unauthenticated access and unauthorized access) is found, the violation can...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L12/26H04L12/24H04L29/06
Inventor 周涛叶润国刘晖姚熙
Owner BEIJING VENUS INFORMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com