Real-time monitoring method and device for webpage Trojan horse
A real-time monitoring and web Trojan technology, applied in computer security devices, data exchange networks, instruments, etc., can solve the problems of protecting computer security, poor real-time performance, and huge system resource consumption, avoiding browsers occupying too much memory, guaranteeing safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
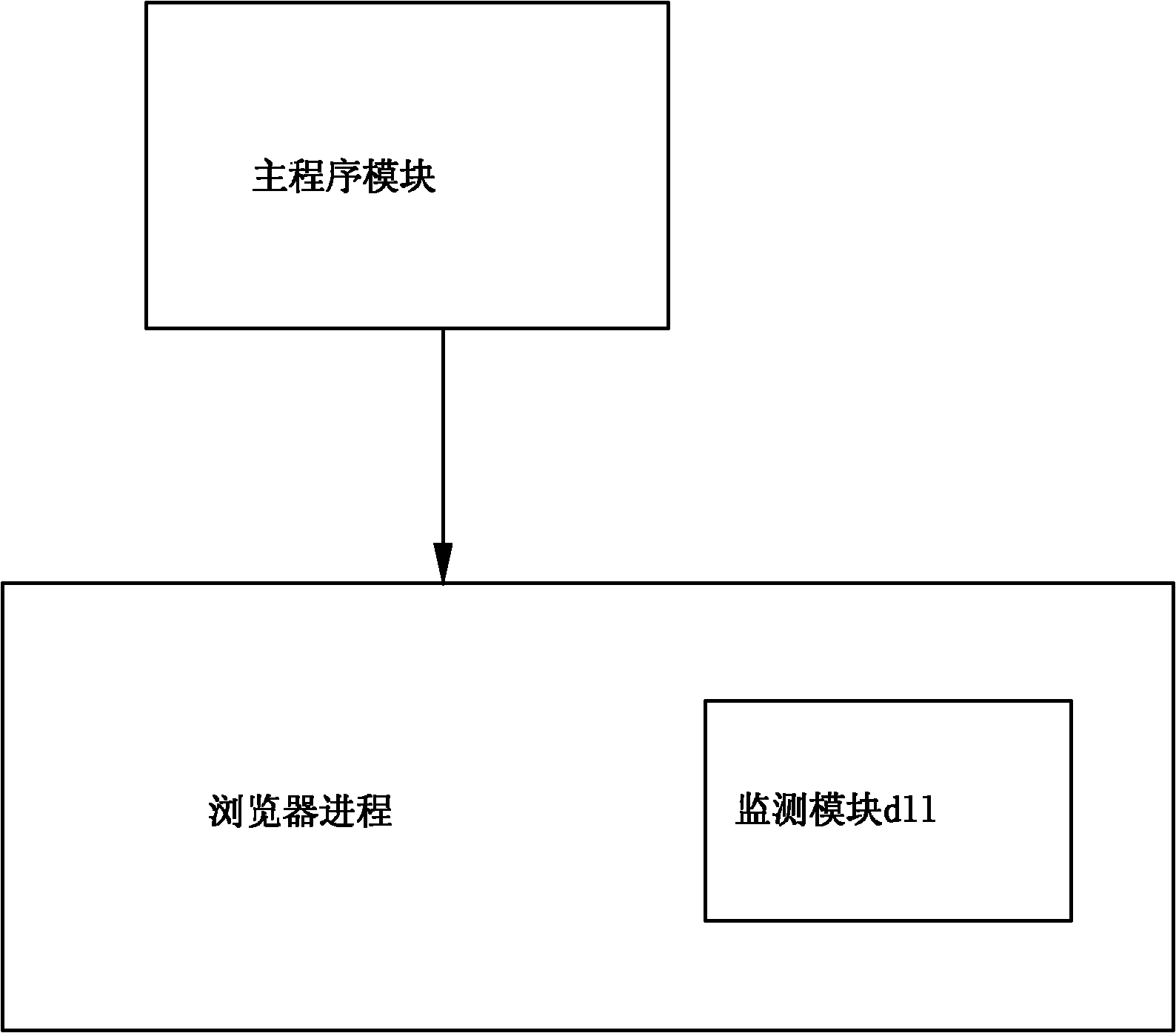
Image
Examples
Embodiment Construction
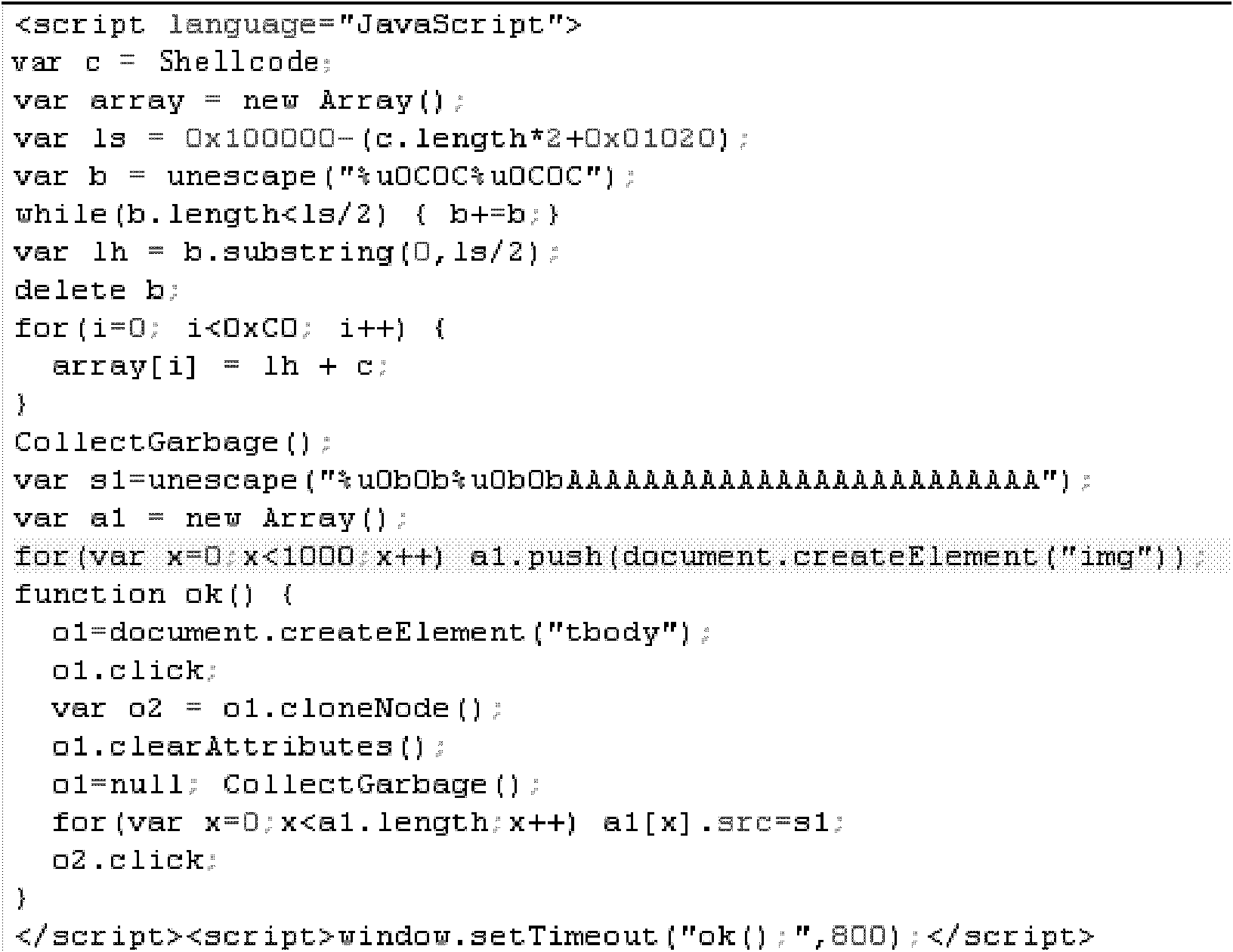
[0053] As shown in the attached figure, since the principle of most webpages to hang horses at present is to use browser or third-party control vulnerabilities, combined with heap spray (heap spray) technology, open up a large amount of memory and write shellcode, so as to achieve the execution of shellcode to download Trojans and purpose of execution.
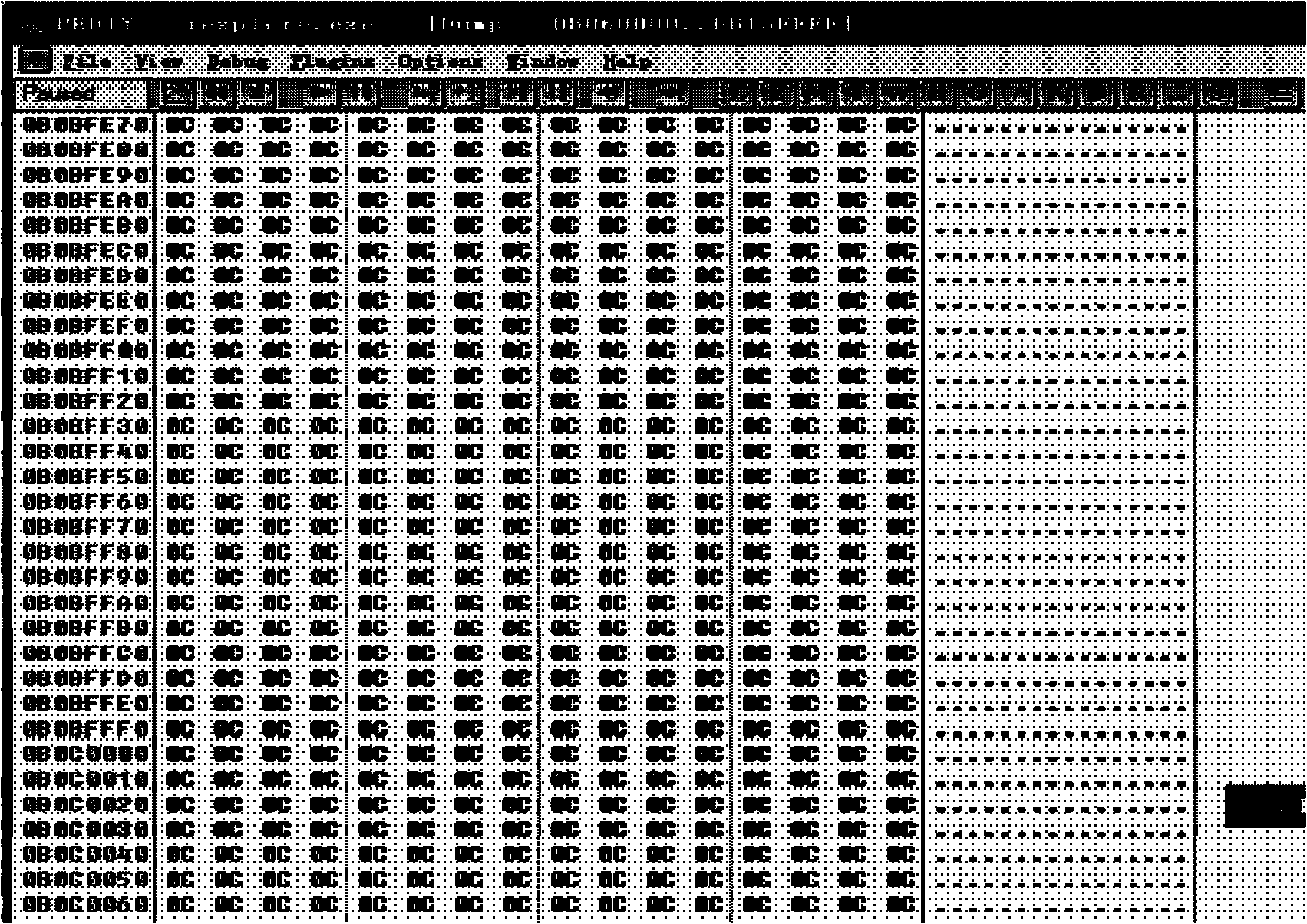
[0054] The principle of using the heap spray technology is to write a lot of useless codes in the memory. When the EIP pointer of the program is hijacked and executed to these useless codes, it will not have any impact on the execution of the subsequent Shellcode. These codes often also play a role. It acts as the return address of the function, so it has certain characteristics, such as 0x0A0A0A0A, 0x0B0B0B0B, 0x0C0C0C0C, 0x90909090. By detecting a large area with similar characteristics in the memory, it can effectively avoid the execution of malicious code, which can help detect some web Trojan horses aggressive behavior. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com