Method and system for protecting terminal reading contents
A reading content and terminal technology, applied in the protection method and system field of terminal reading content, can solve the problems of harming the legitimate rights and interests of content providers, creators, imperfect protection mechanisms, complex and complicated calculation methods, etc., to improve user-friendly experience , improve user experience, and save local resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be described more fully hereinafter with reference to the accompanying drawings, in which exemplary embodiments of the invention are illustrated.
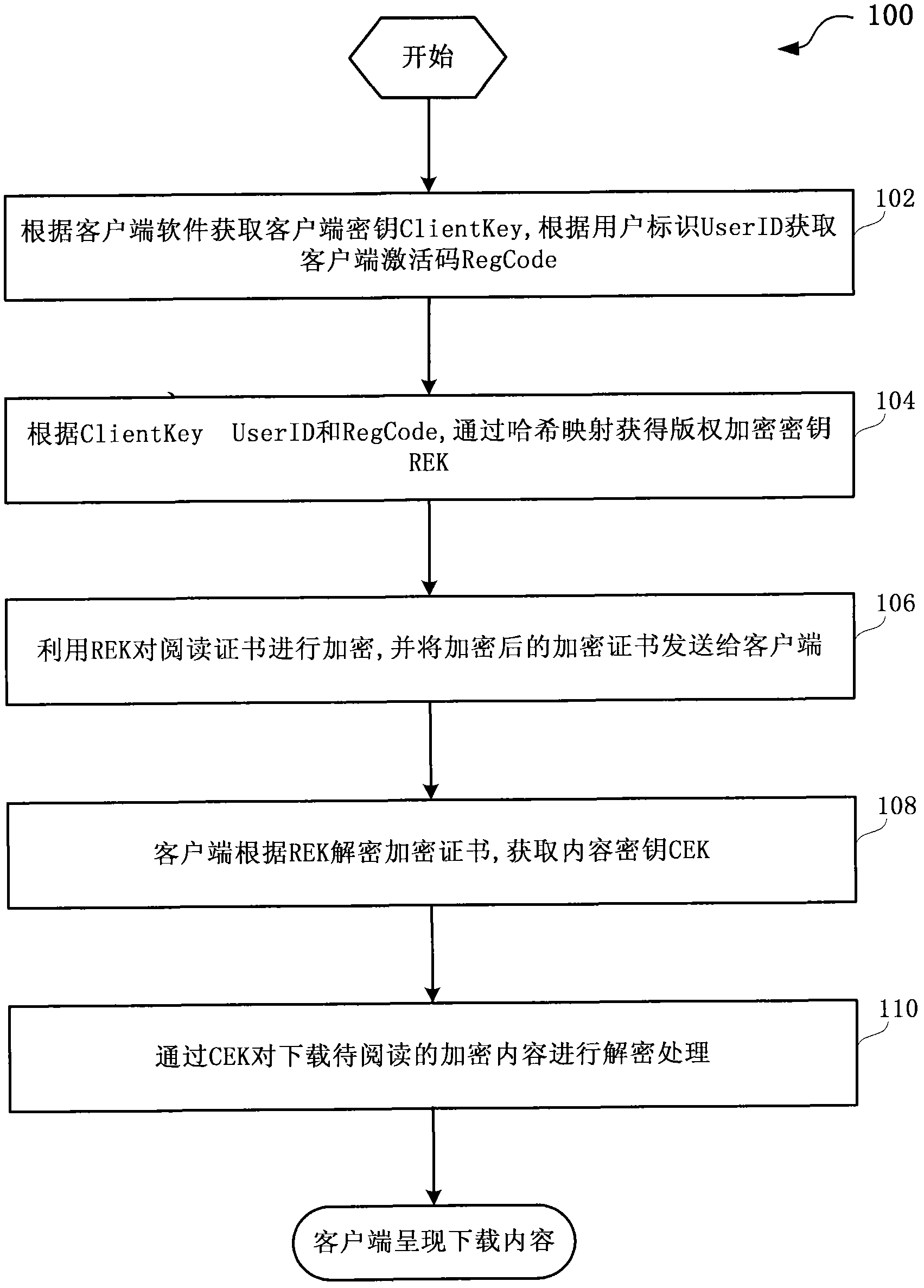
[0029] figure 1 A flowchart showing a method for protecting content read by a terminal provided by an embodiment of the present invention.
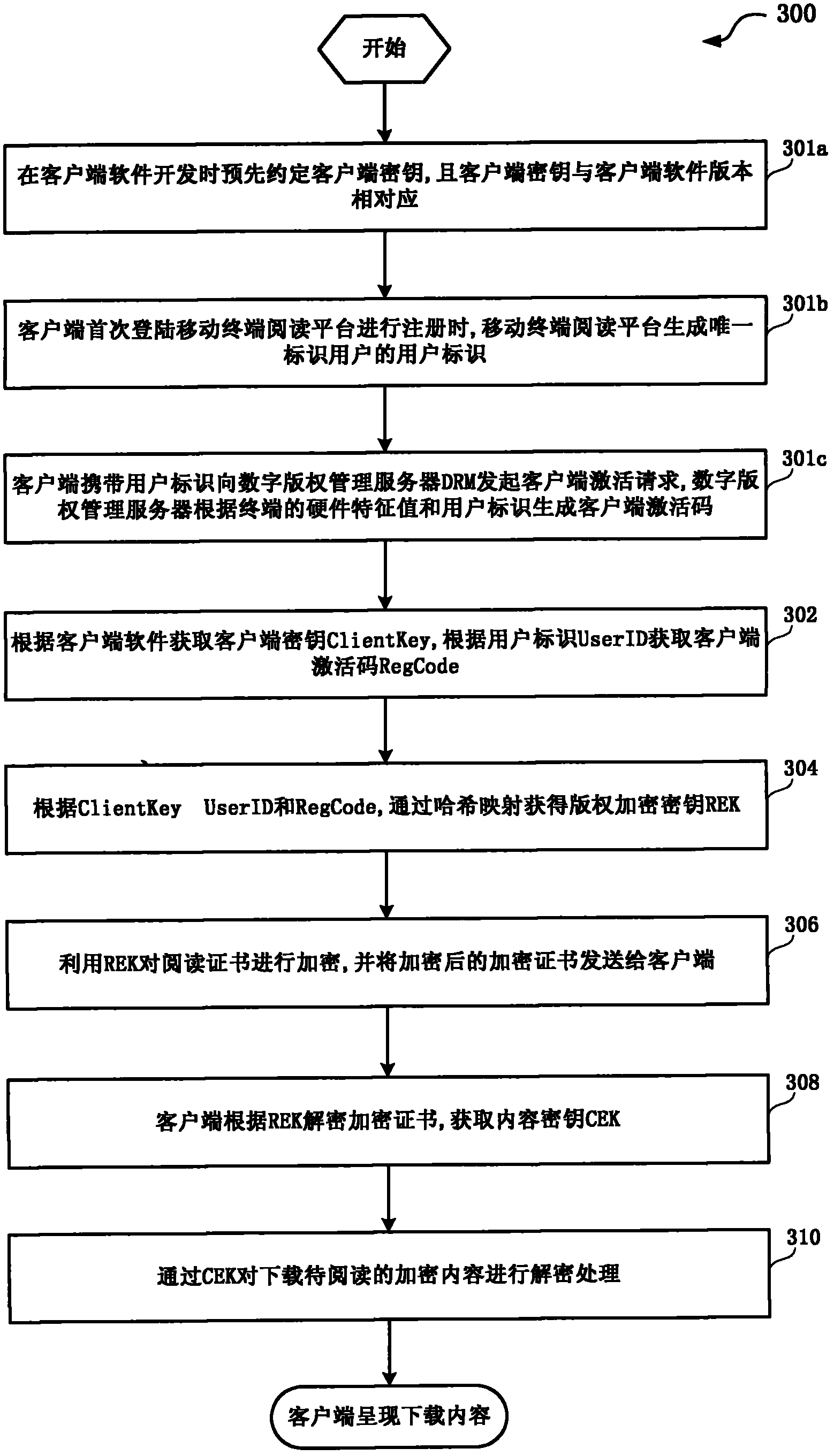
[0030] Such as figure 1 As shown, the method 100 for protecting content read by a terminal includes: step 102, obtaining the client key ClientKey according to the client software, and obtaining the client activation code RegCode according to the user ID UserID. For example, in one embodiment of the protection method for terminal reading content provided by the present invention, the client key is pre-agreed when the client software is developed, and different versions of the client use different ClientKeys (i.e., the client key is the same as the client key). corresponding to the software version). Further, in the present invention, the ClientKey can be mut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com