ISP anomalous traffic detection method and system
A technology of abnormal traffic and detection method, applied in the field of information security, can solve the problems of low false positive rate, no adaptive ability, abnormal detection ability of network traffic, etc., and achieve the effect of reducing false positive rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] All features disclosed in this specification, or steps in all methods or processes disclosed, may be combined in any manner, except for mutually exclusive features and / or steps.
[0035] Any feature disclosed in this specification (including any appended claims, abstract and drawings), unless expressly stated otherwise, may be replaced by alternative features which are equivalent or serve a similar purpose. That is, unless expressly stated otherwise, each feature is one example only of a series of equivalent or similar features.
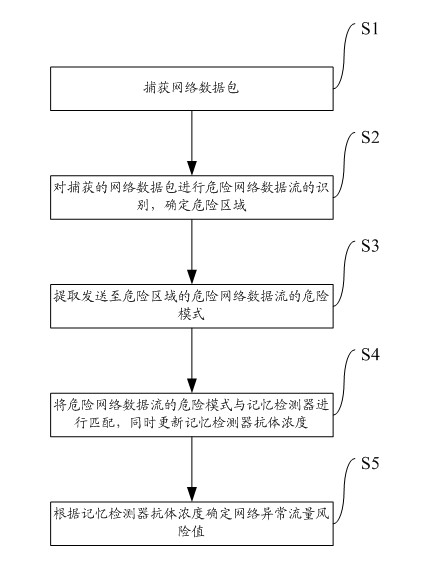
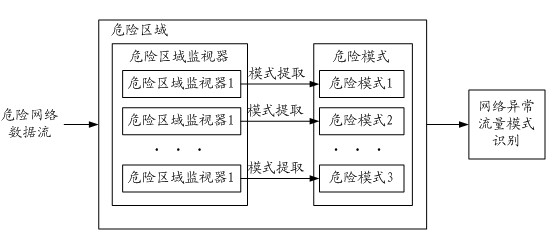
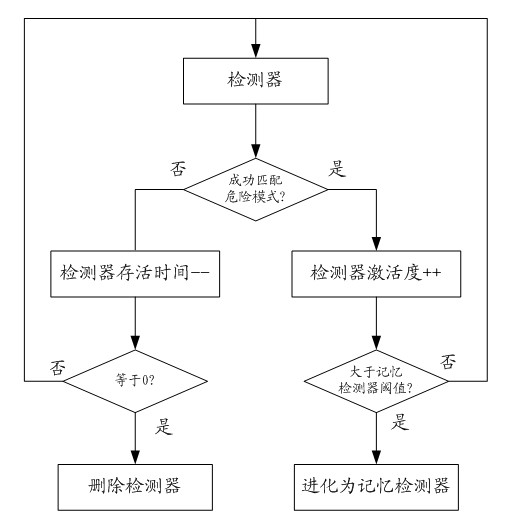
[0036] Before introducing the specific implementation technical solution of the present invention, first introduce a theory on which the present invention is based. The biological immune system danger theory points out that the biological immune system generates an immune response based on "danger signals" rather than self / non-self identification. The immune protection mechanism of organisms can effectively protect the safety of organisms, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com