Security assurance method and security management server of host identity tag
A technology for managing server and host identification, applied in the direction of digital transmission system, electrical components, transmission system, etc., can solve the problems of decreased security, failure to consider HIT security guarantee, security cannot be guaranteed, etc., to achieve safe use guarantee Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
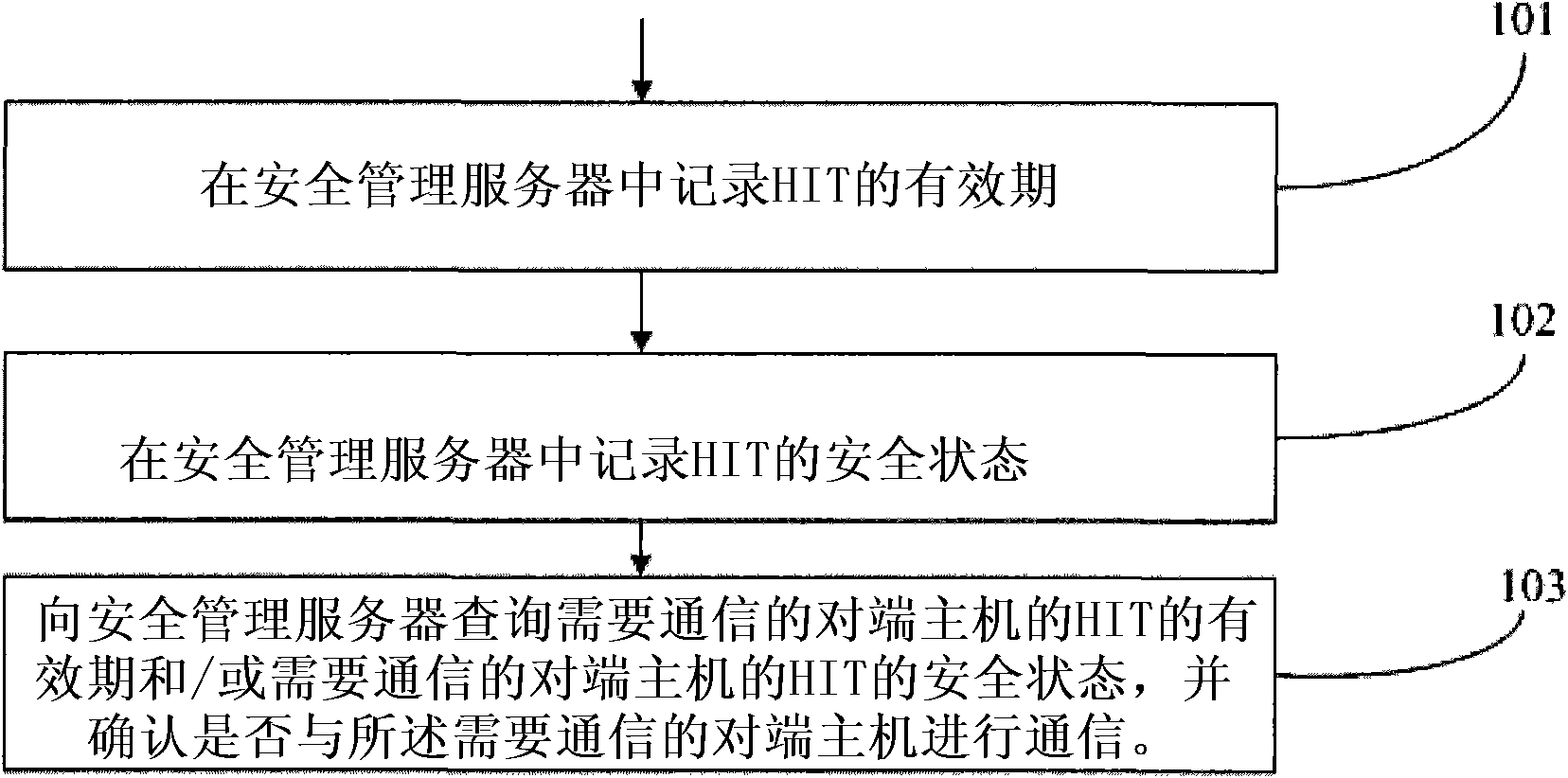
[0023] Such as figure 1 As shown, this embodiment provides a security guarantee method for a host identification tag, including:
[0024] Step 101: Record the validity period of the HIT in the security management server.
[0025] Step 102: Record the security state of the HIT in the security management server.
[0026] Step 103: query the security management server for the validity period of the HIT of the peer host that needs to communicate and / or the security status of the HIT of the peer host that needs to communicate, and confirm whether to communicate with the peer host that needs to communicate. .
[0027] In step 103, when communication is required, query the security management server for the validity period of the HIT of the peer host that needs to communicate and / or the security status of the HIT of the peer host that needs to communicate, and according to the peer host that needs to communicate The validity period of the HIT of the host and / or the security status...
Embodiment 2
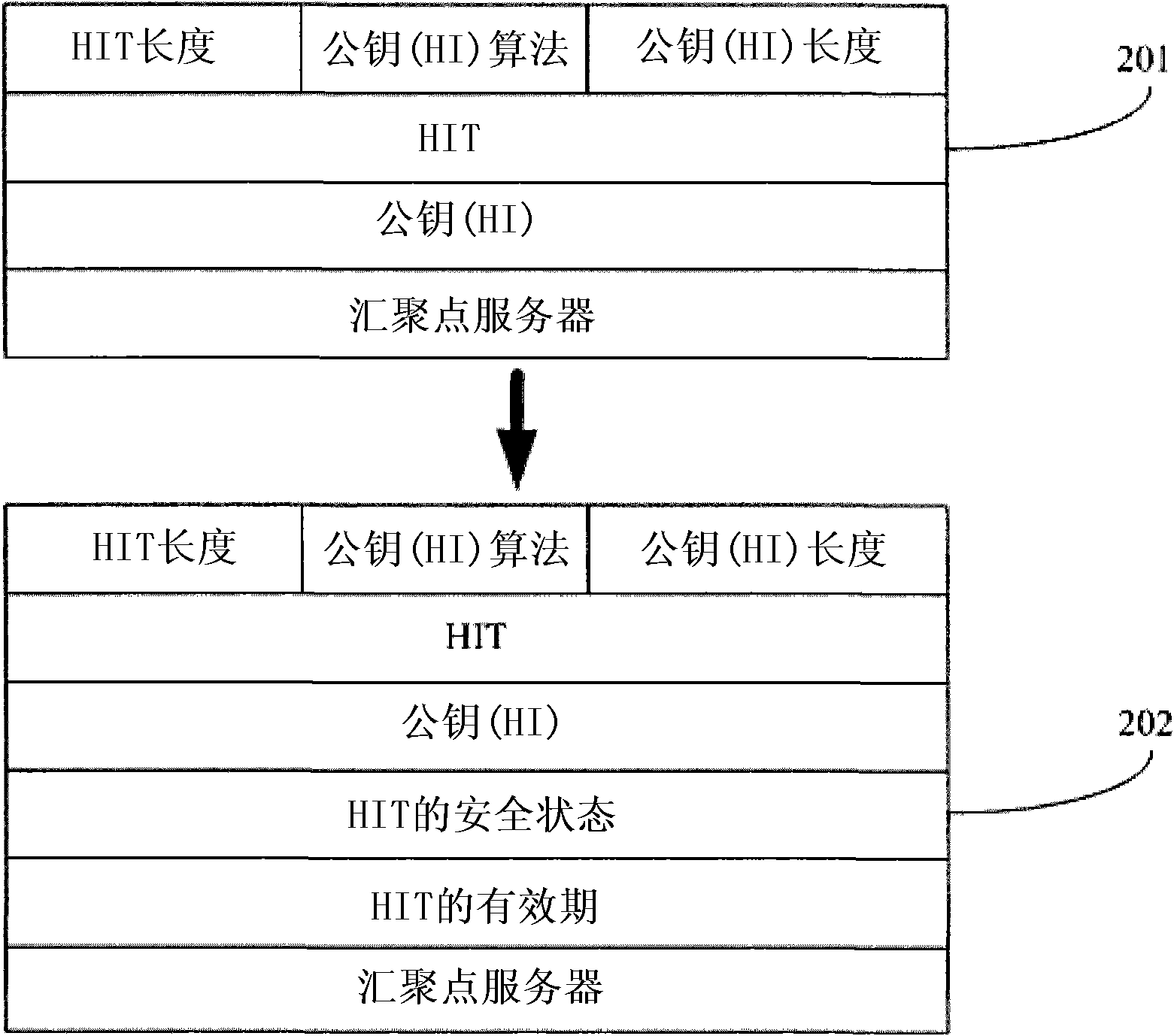
[0033] The present embodiment provides a security guarantee method for a host identification label, by extending a DNS resource record (DNS Resource Record, DNSRR) on a DNS (Domain Name Server, domain name server) server to record the validity period of the HIT and / or the security status of the HIT , and provide a query mechanism for the validity period of the HIT and / or the security status of the HIT. Preferably, a HIP resource record (HIPResource Record, HIP RR) can be extended or redefined in the DNS RR. Such as figure 2 As shown in 201, the original type of HIP RR includes: HIT length, public key (HI) algorithm, public key (HI) length, HIT, public key (HI) and rendezvous point server and other resource record types. Preferably, on the basis of the original resource record type in the HIP RR, the validity period of the HIT and / or the security status of the HIT can be increased, and the resource record type can be added to the DNS RR. Extended resource record types such a...
Embodiment 3
[0048] The security guarantee method for the host identification tag provided in this embodiment is based on a hierarchical routing architecture (Hierarchical Routing Architecture, HRA). The management domain in the HRA has a server ID-Server responsible for registering the host identity HI. The ID-Server is responsible for the registration and maintenance of the host identity. The ID-Server can be used to manage and maintain the validity period of the HIT and / or the HIT The security status of the HIT, and provide query services for the validity period of the HIT and / or the security status of the HIT.
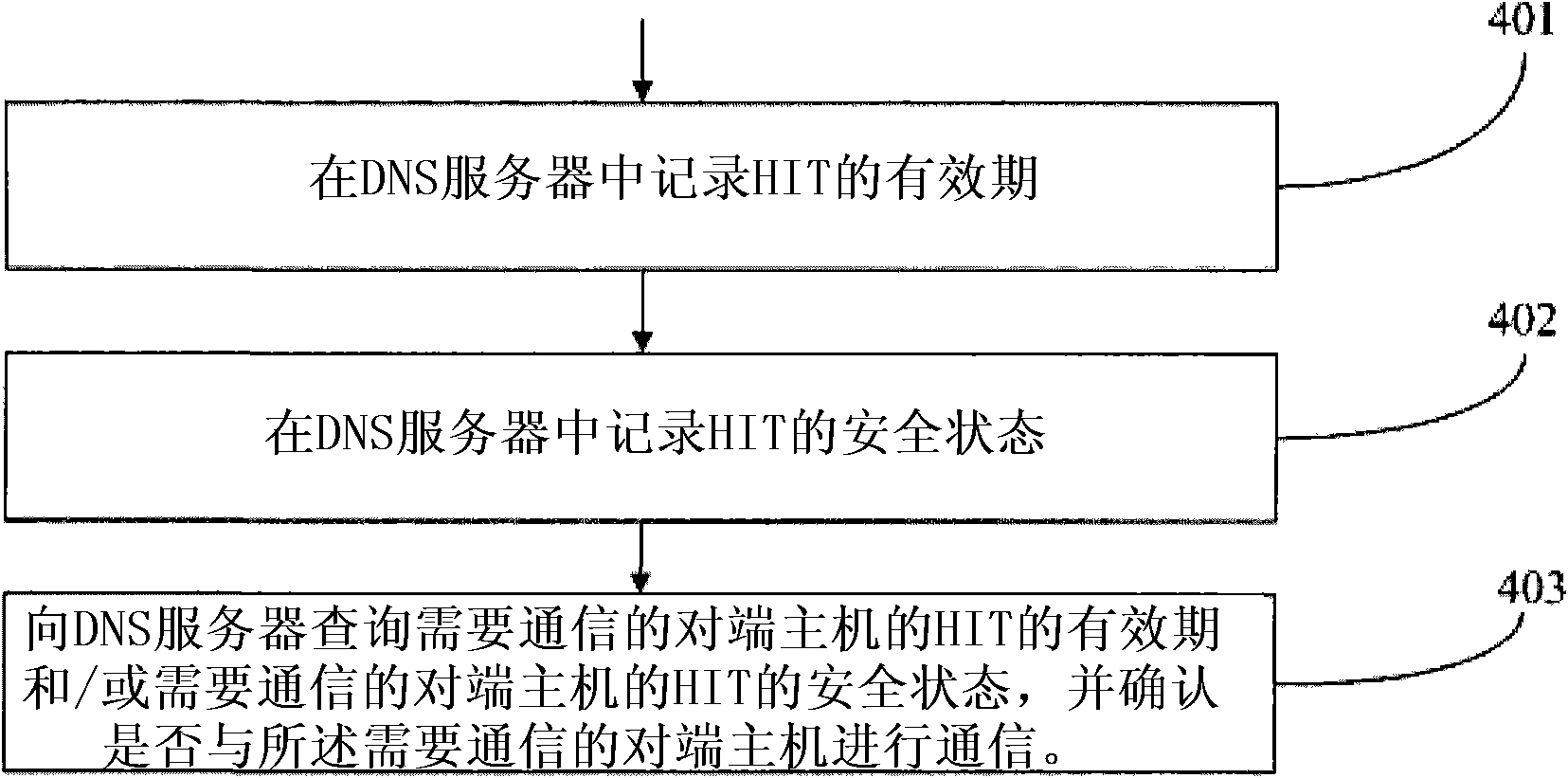
[0049] Such as Figure 4 As shown, the security guarantee method of the host identification label provided in this embodiment includes:
[0050] Step 401: Record the validity period of the HIT in the ID-Server.
[0051] In step 401, if the public key (HI) itself has a validity period, the validity period of the HIT should not exceed the validity period of the public key (HI);...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com