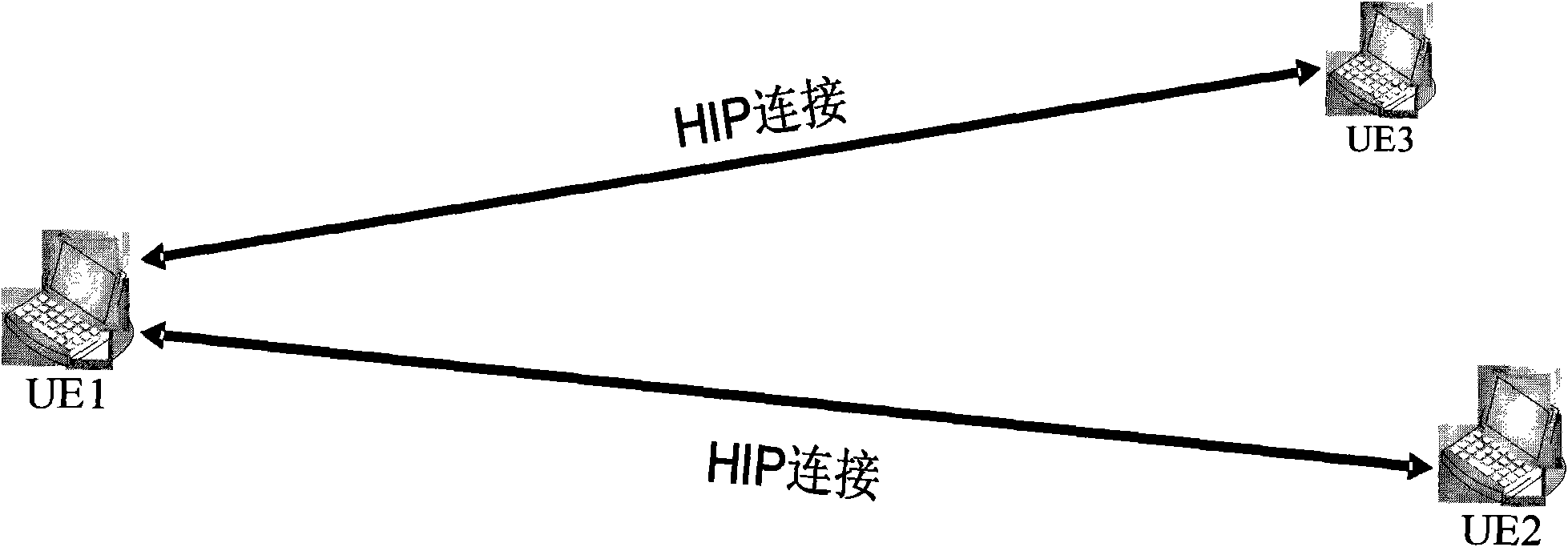
Patents
Literature
31 results about "Host Identity Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
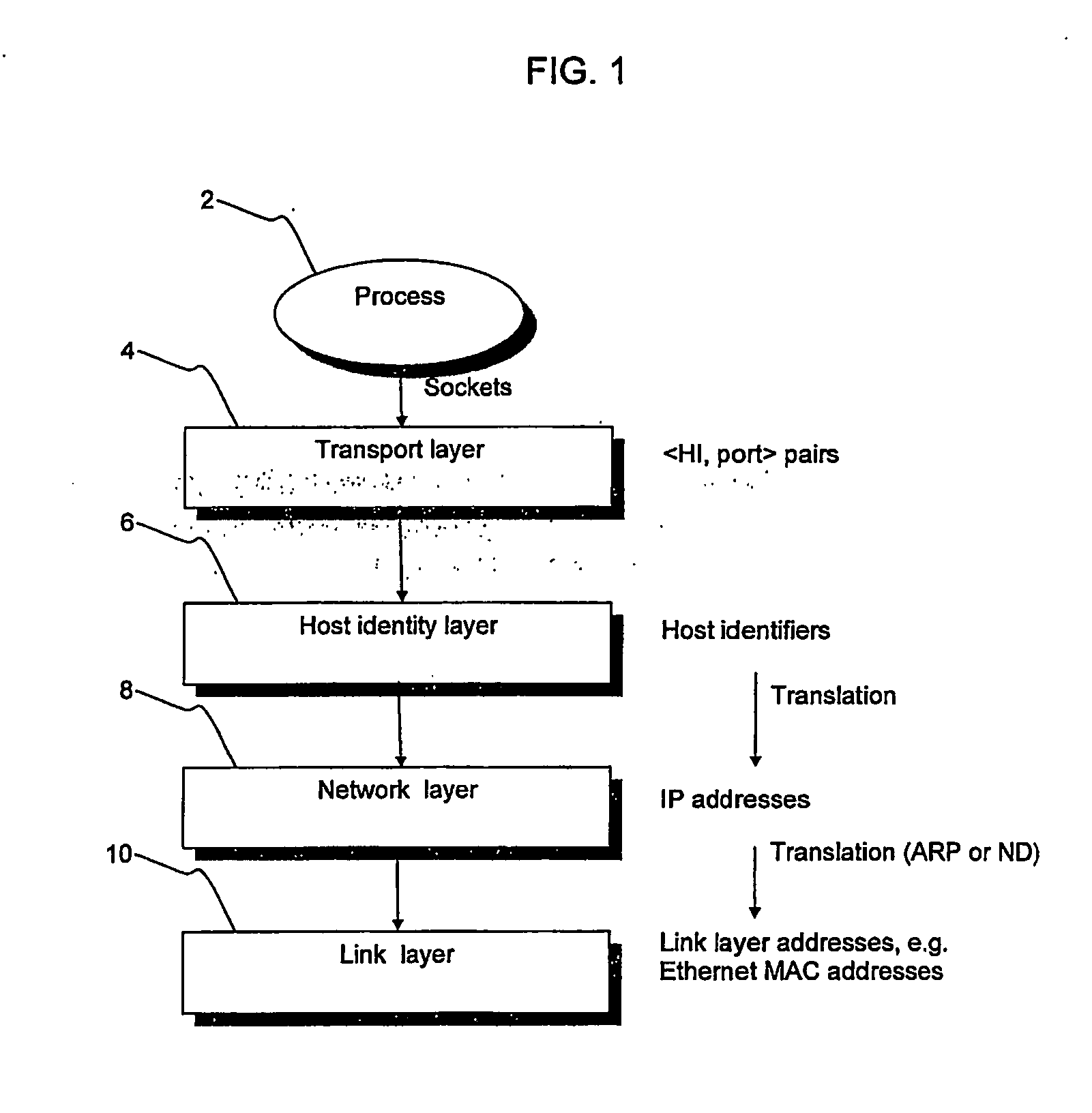
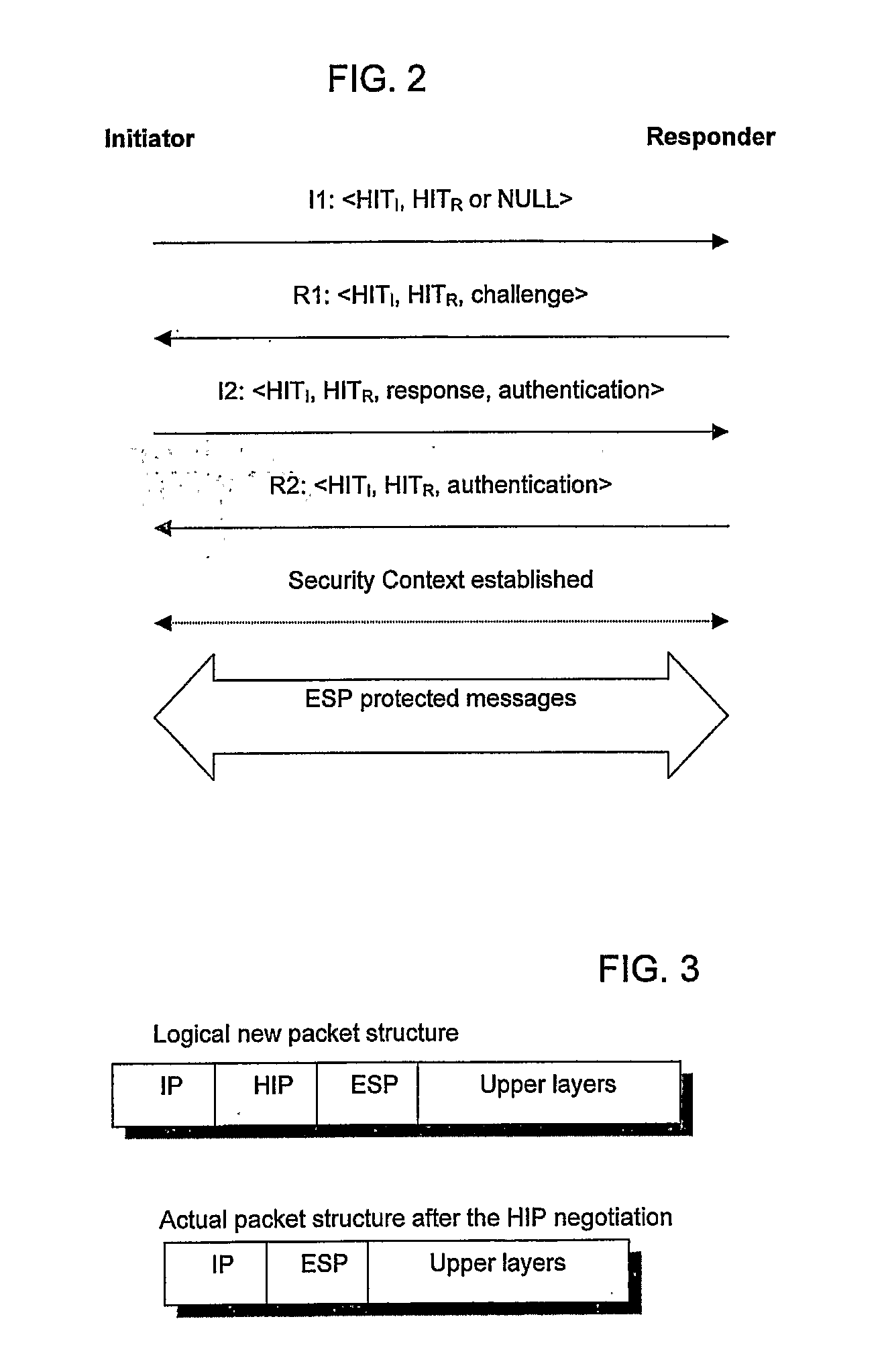
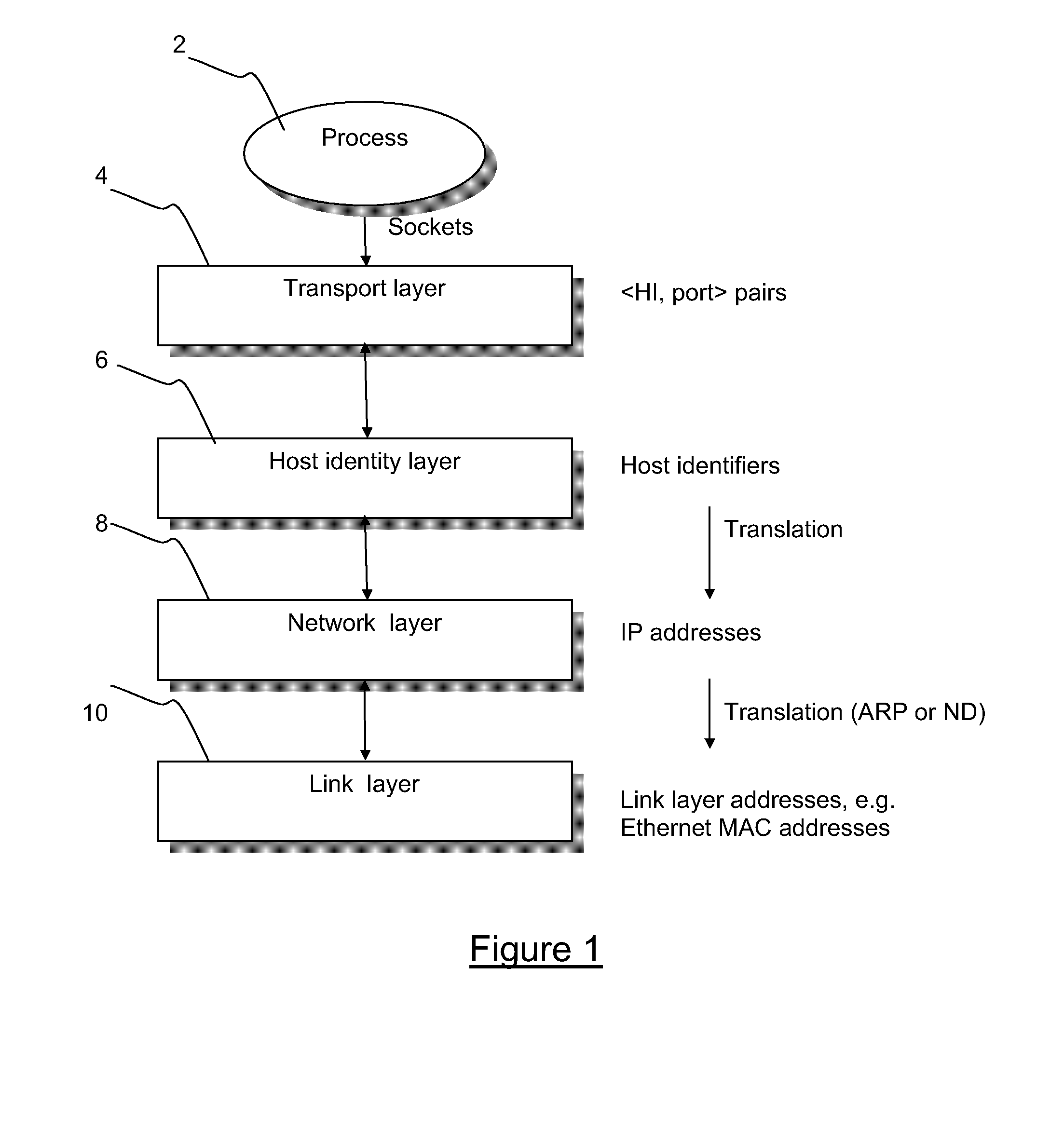
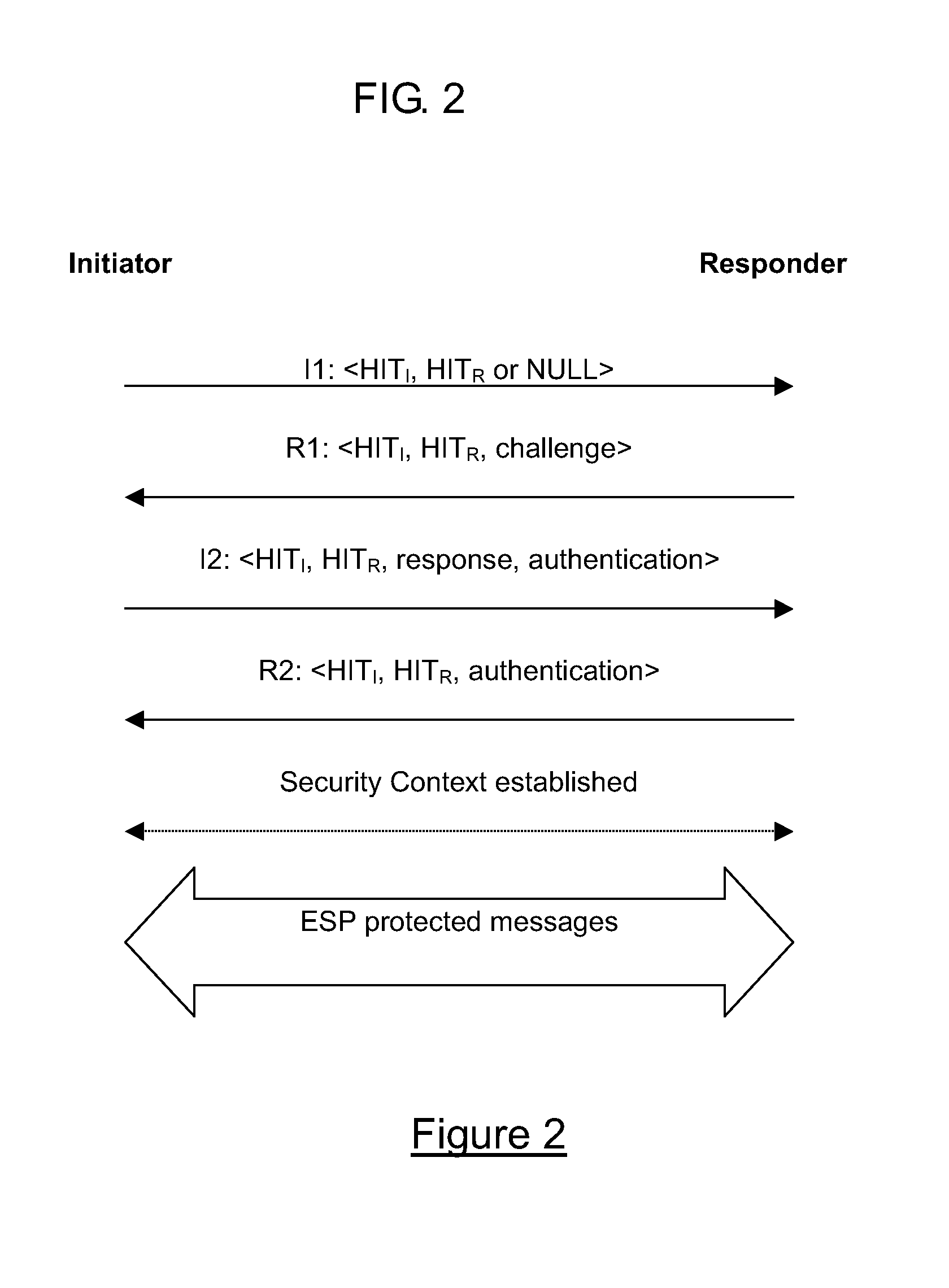
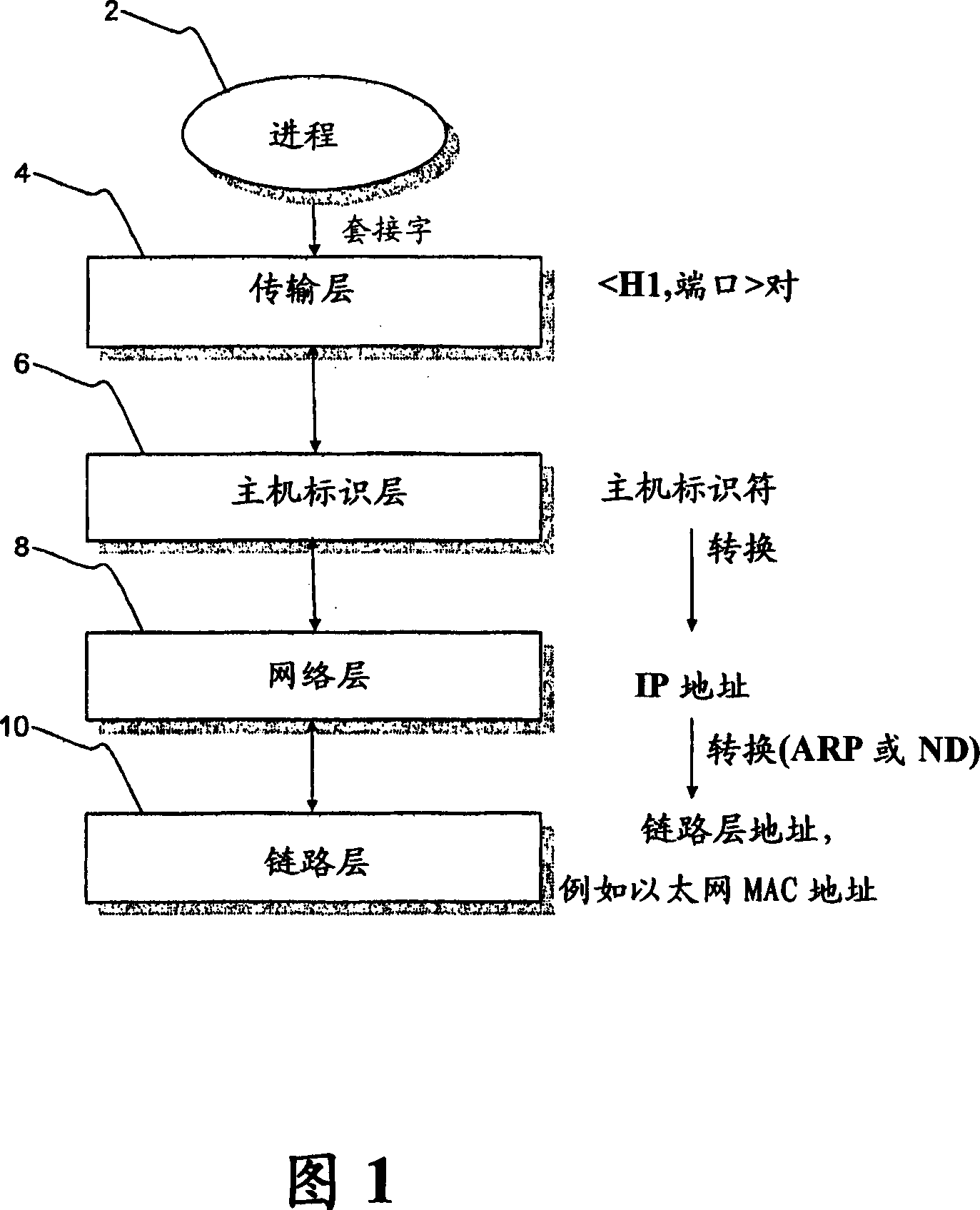
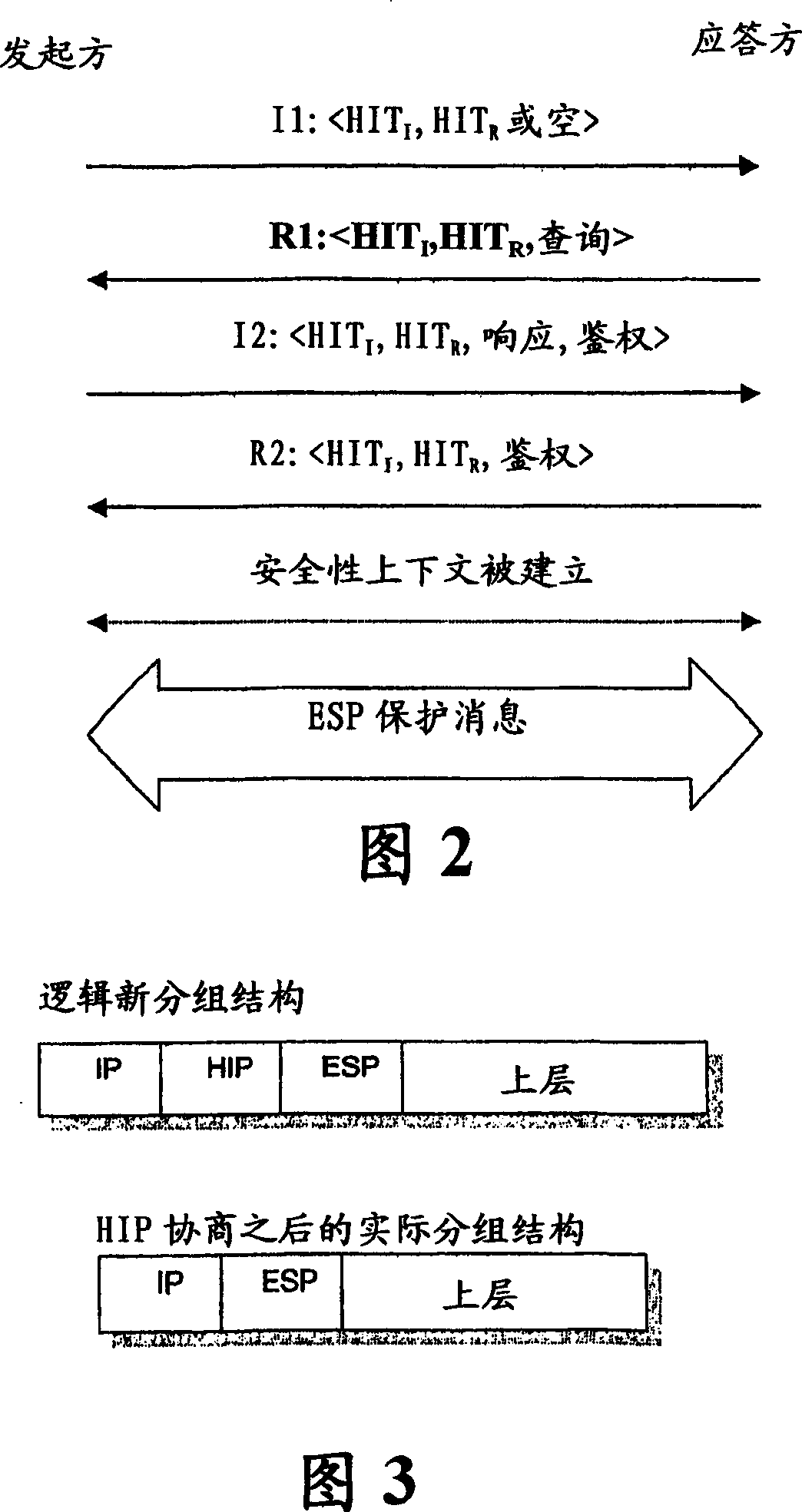
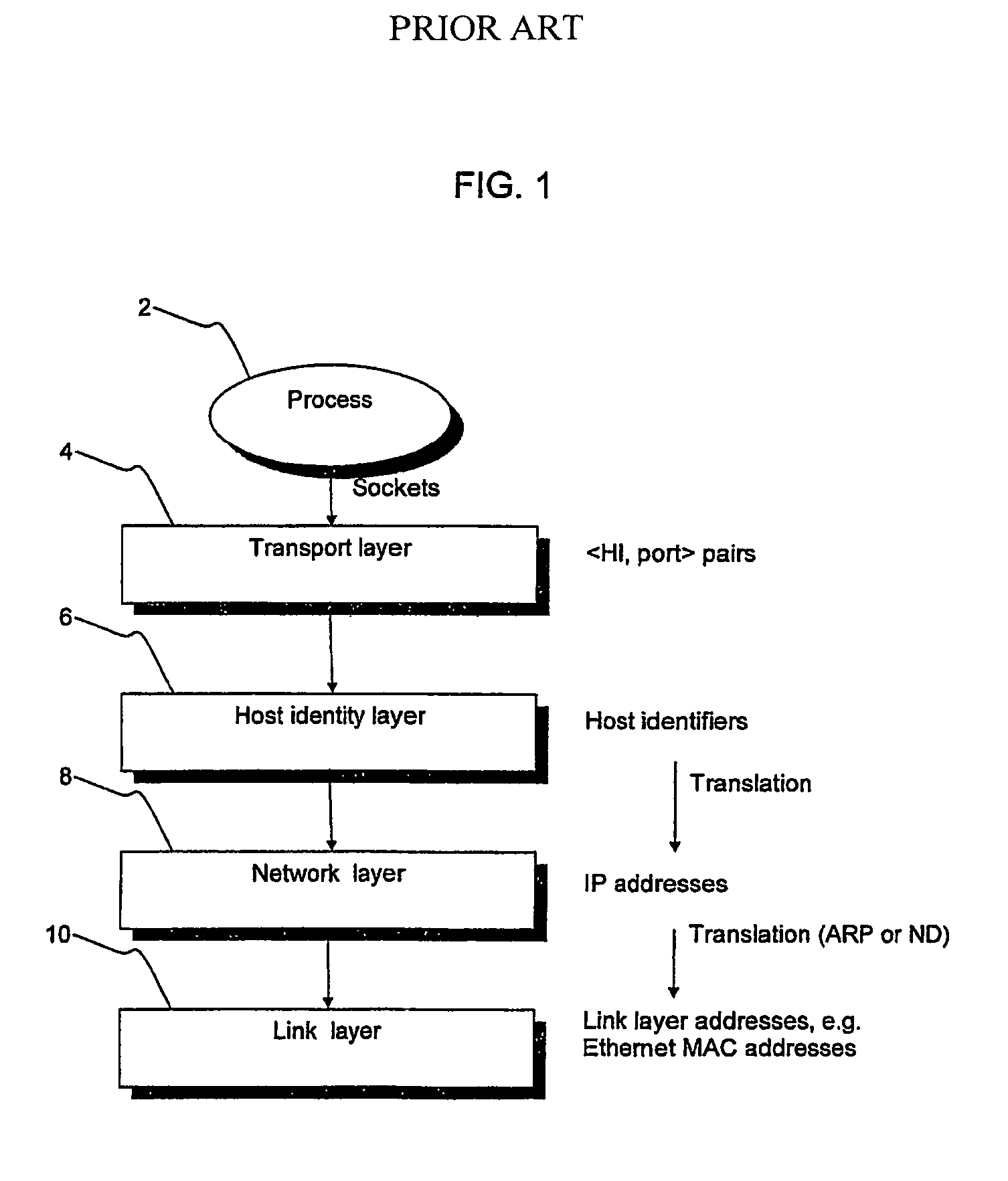
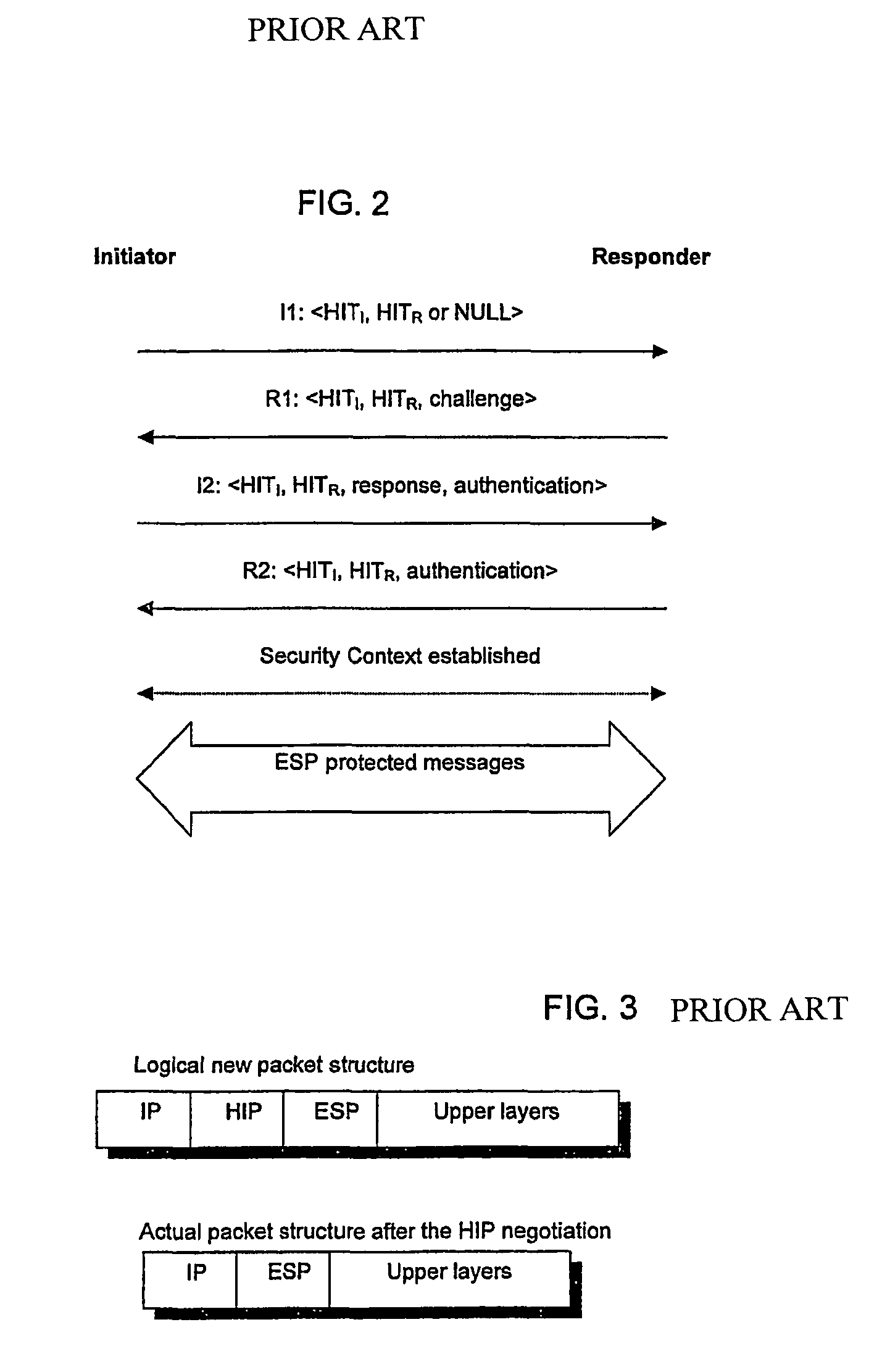
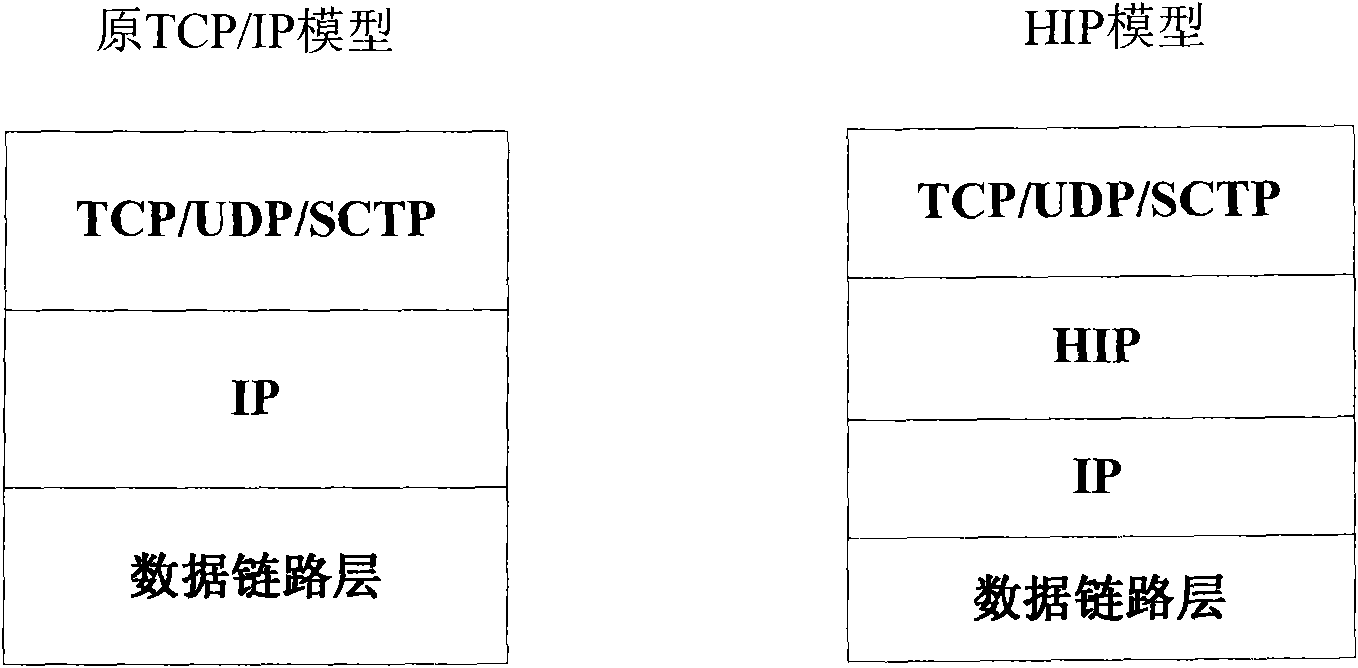
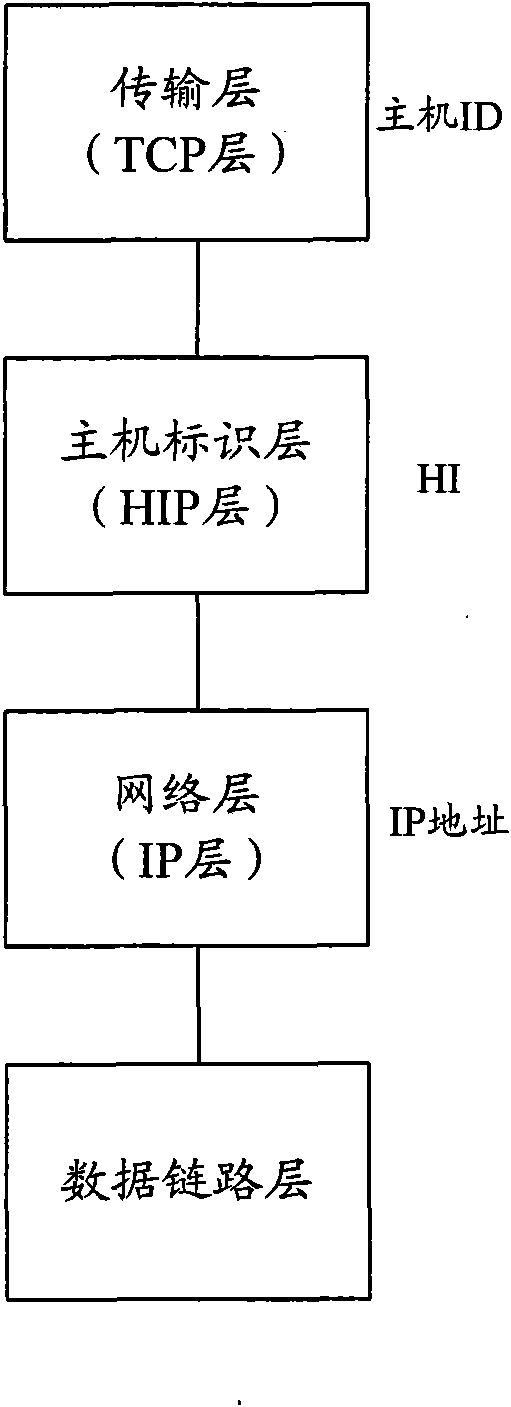
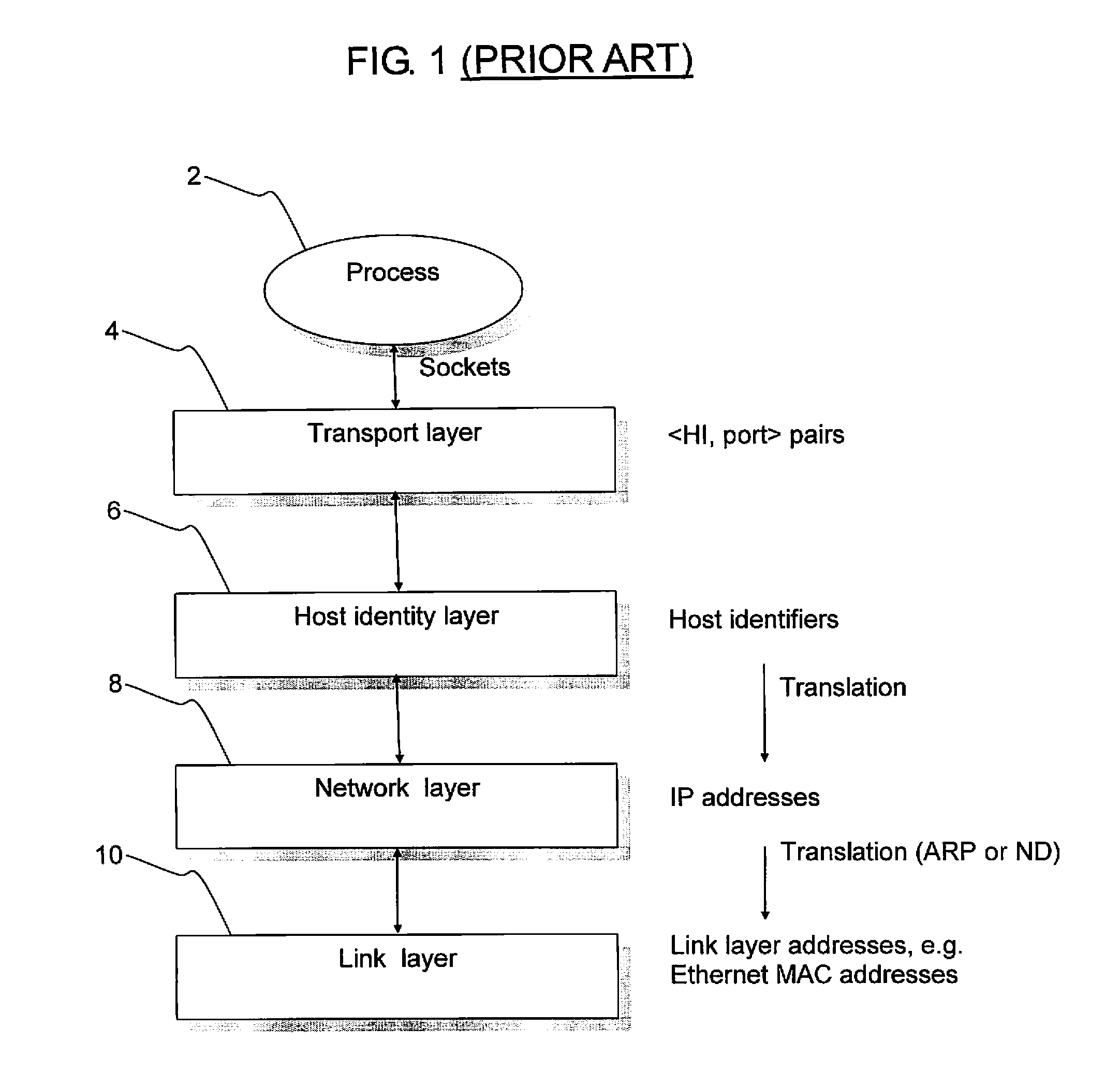
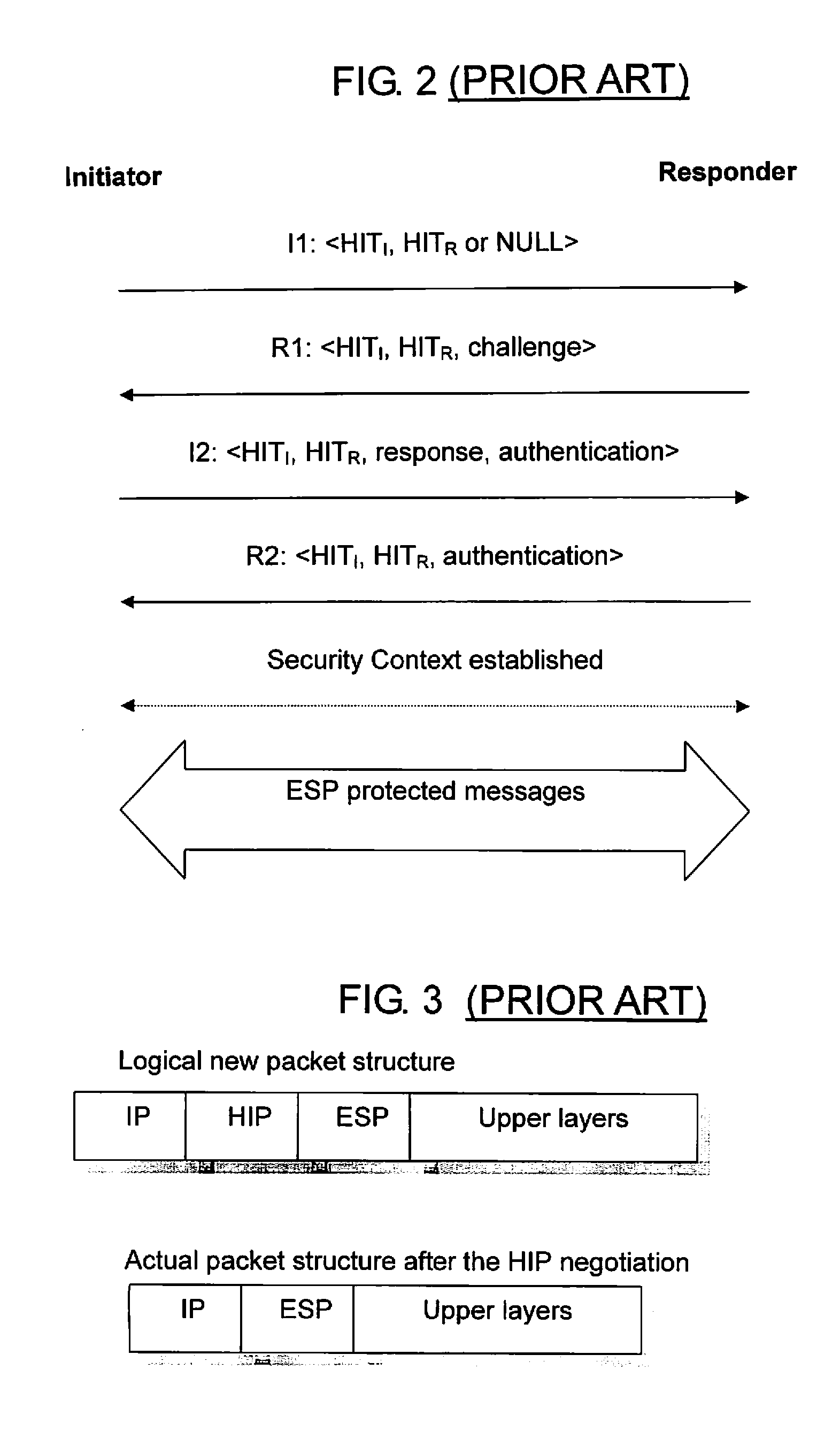
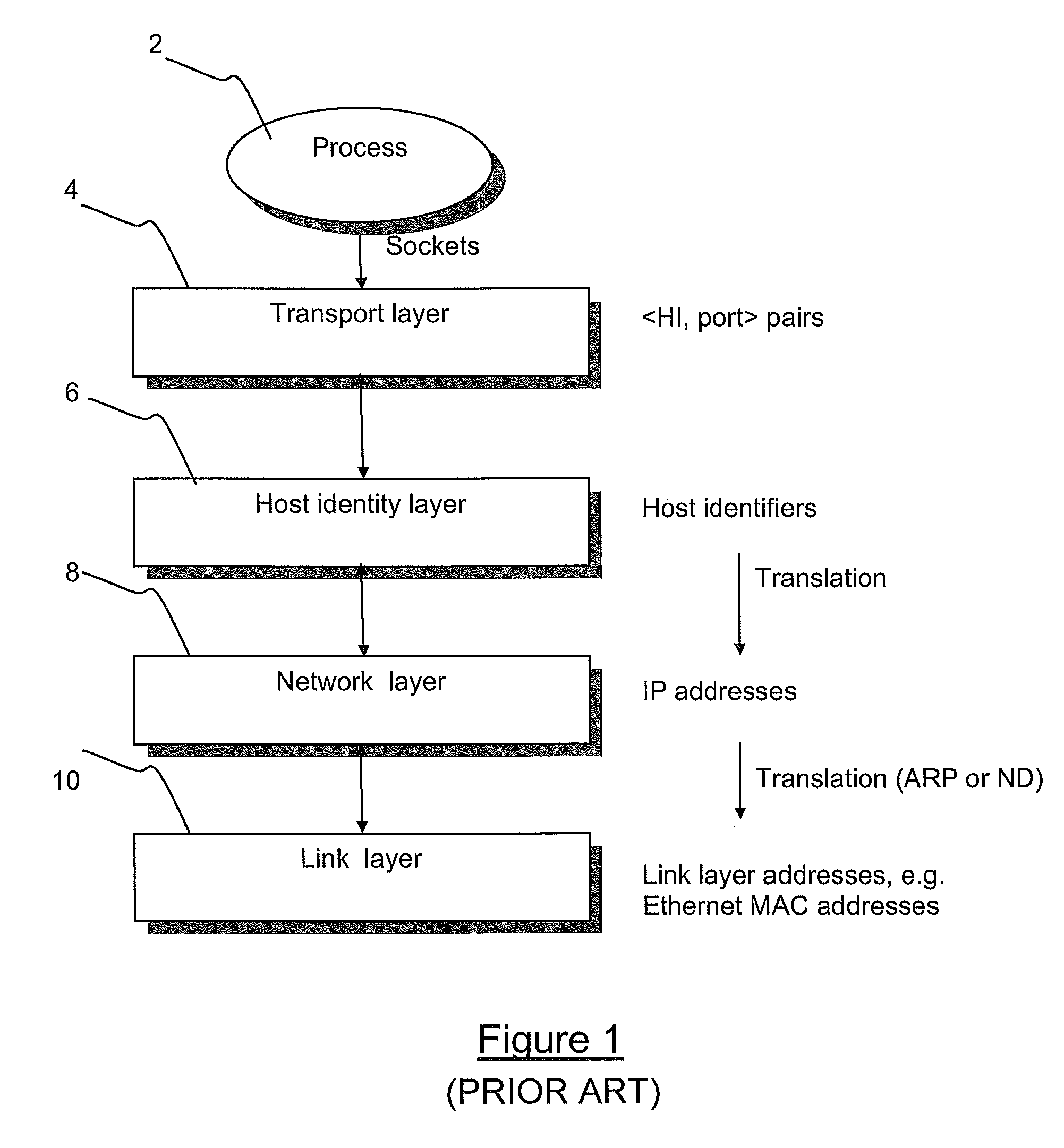
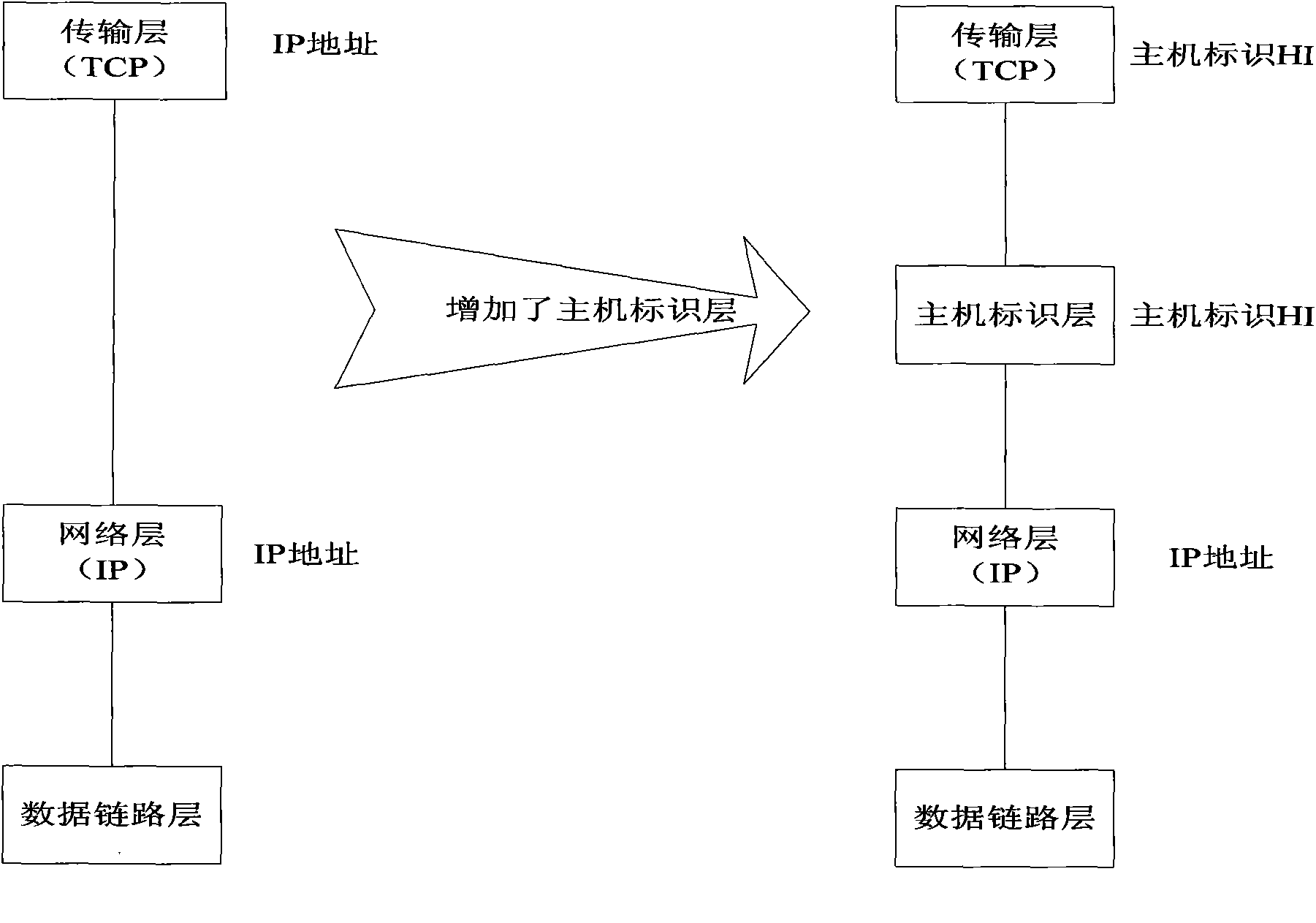
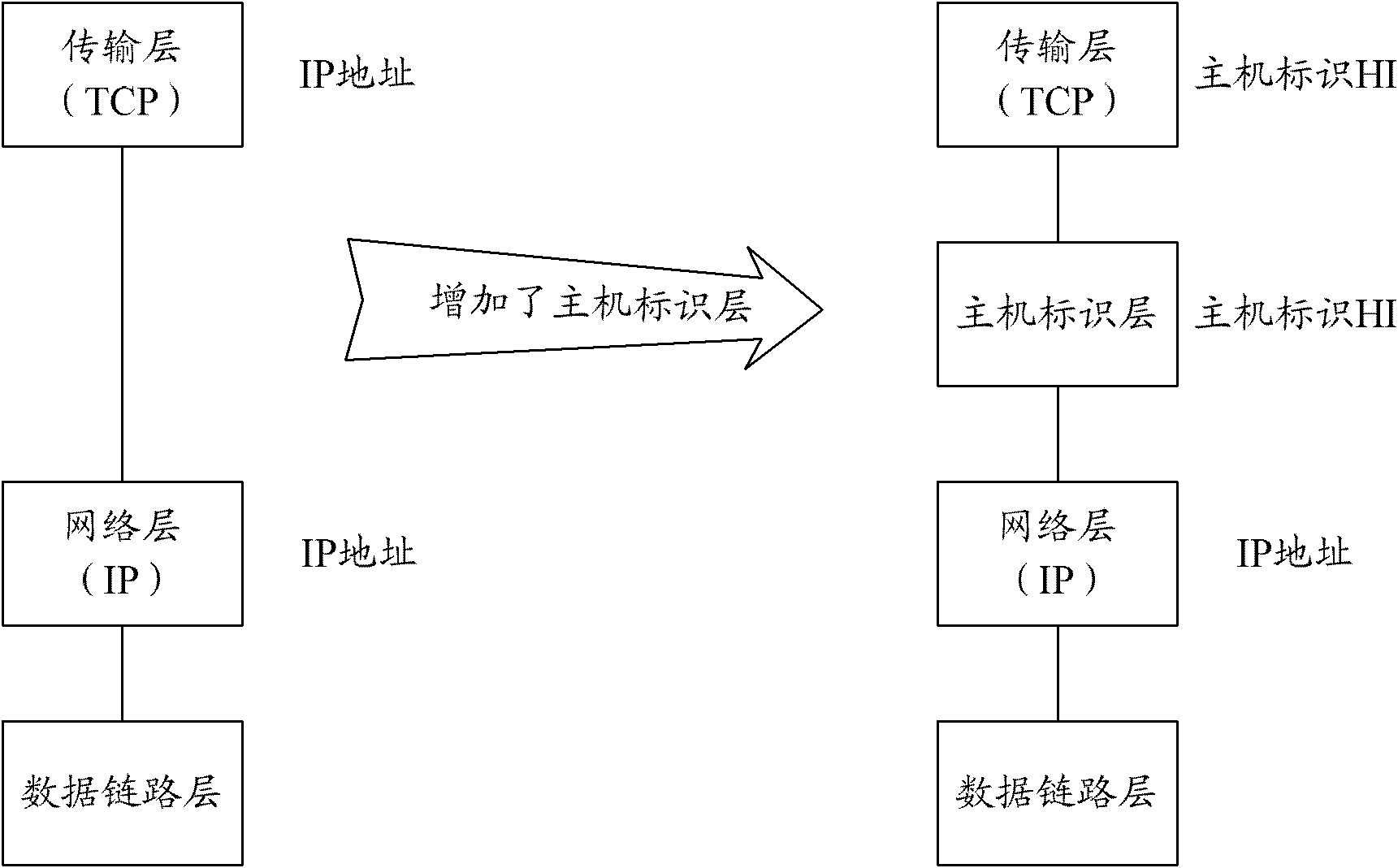
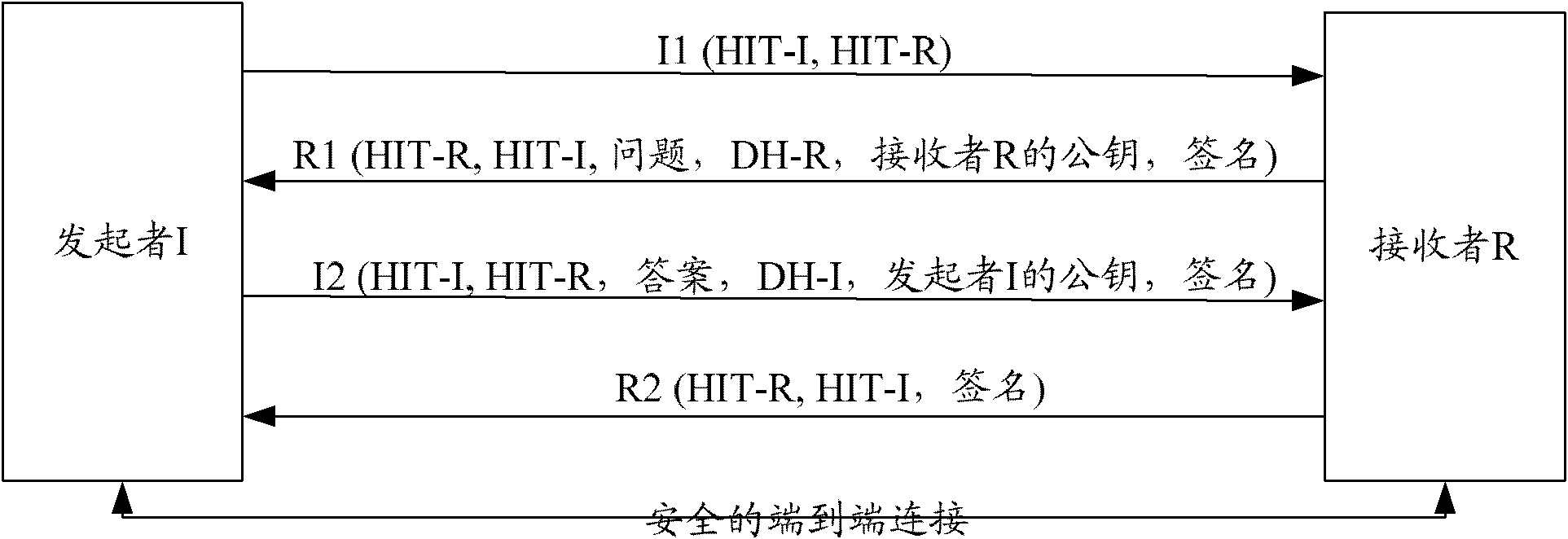
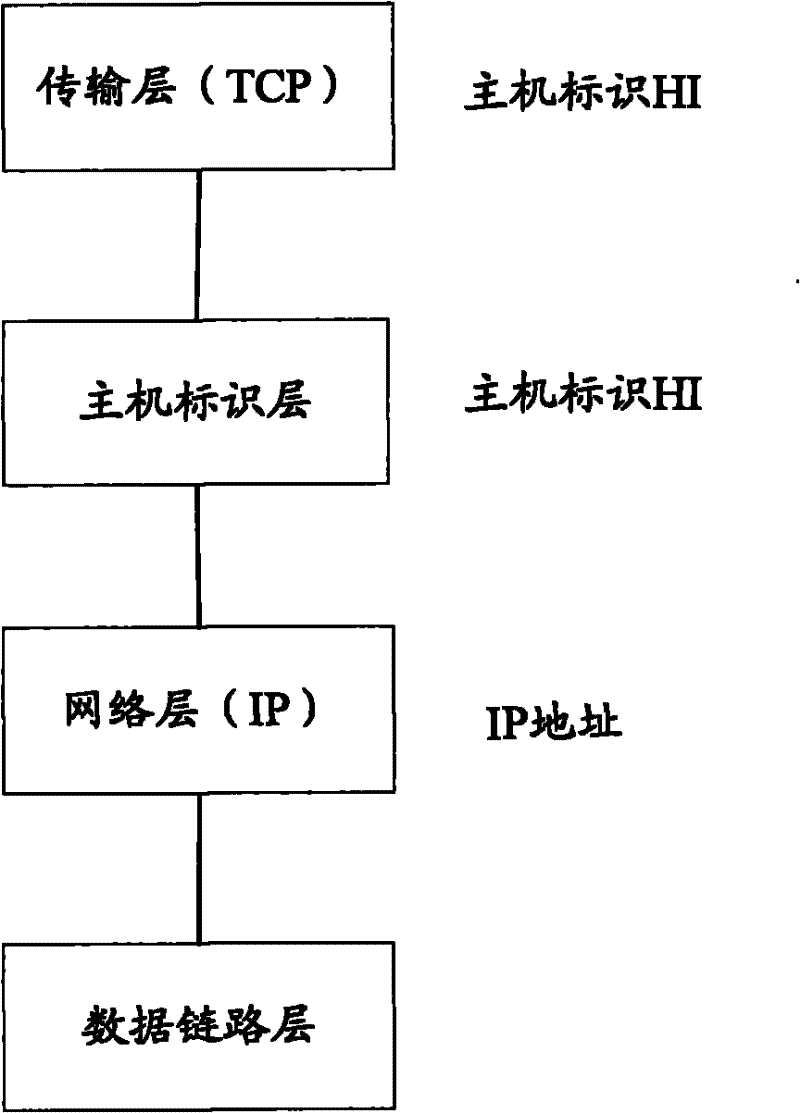
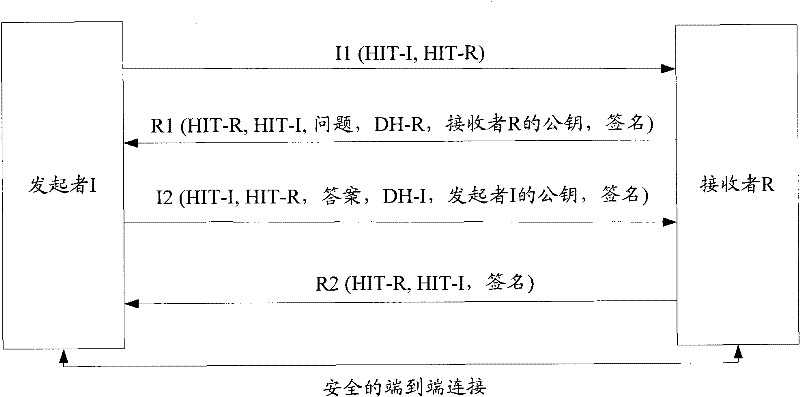
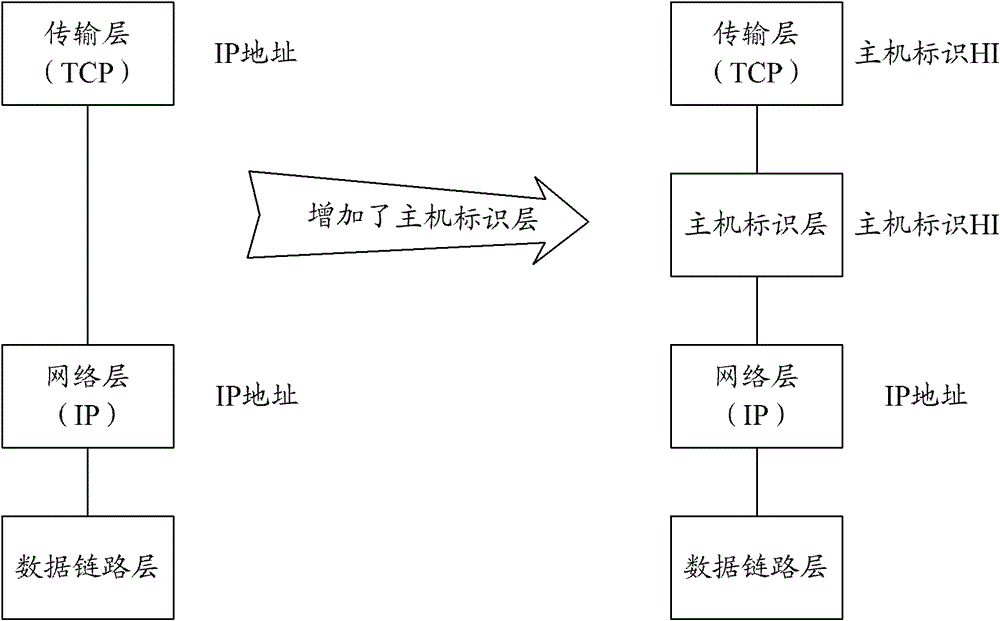
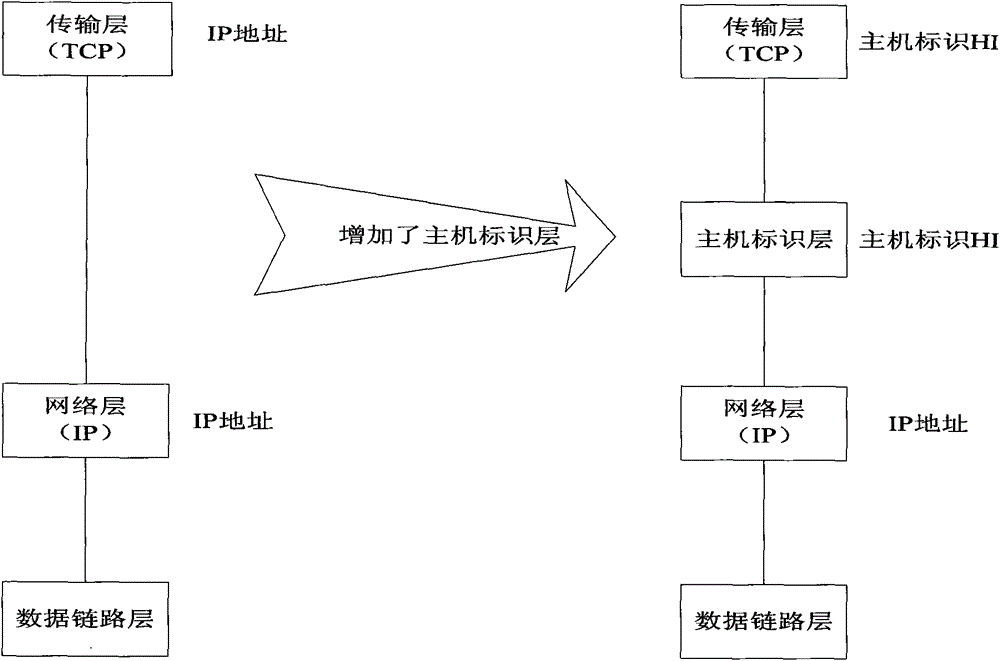
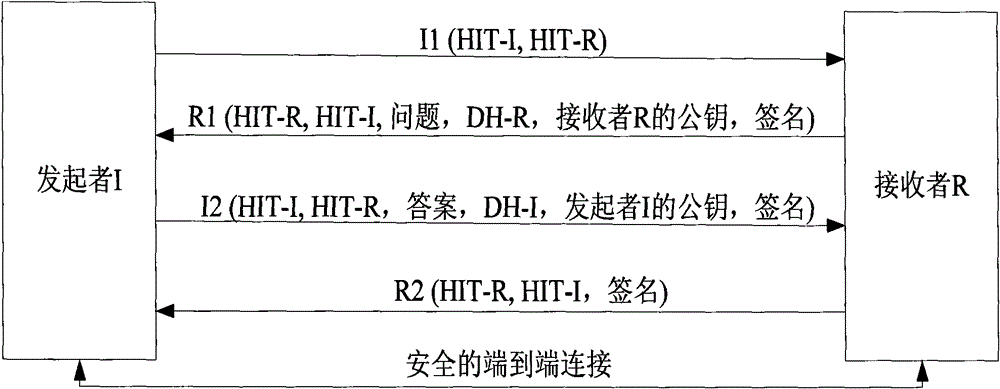
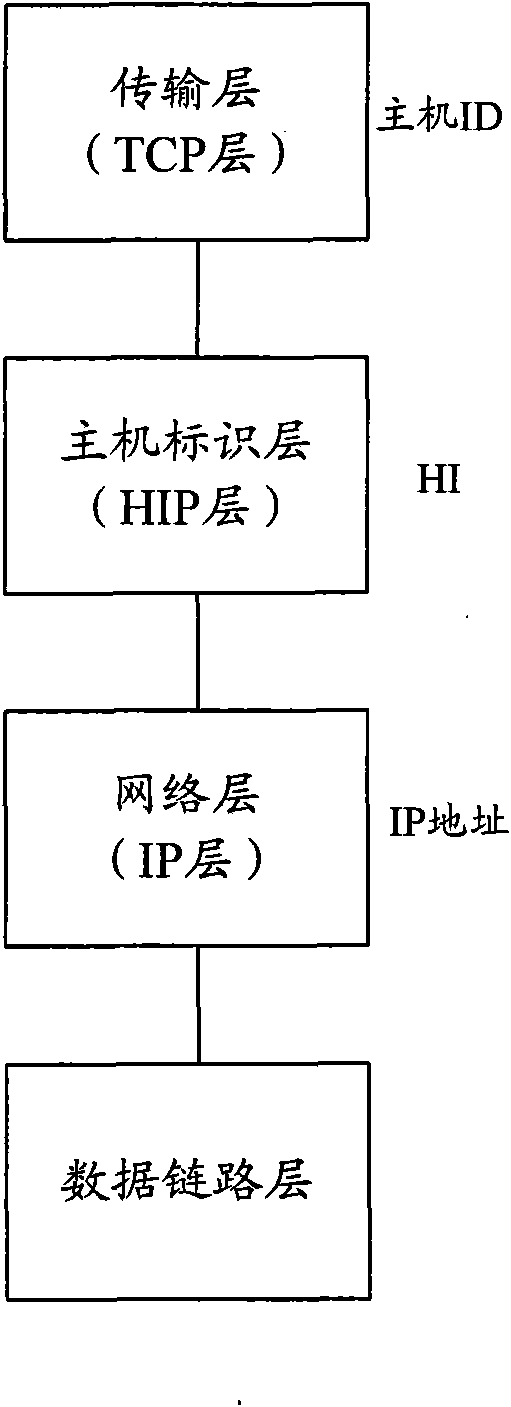
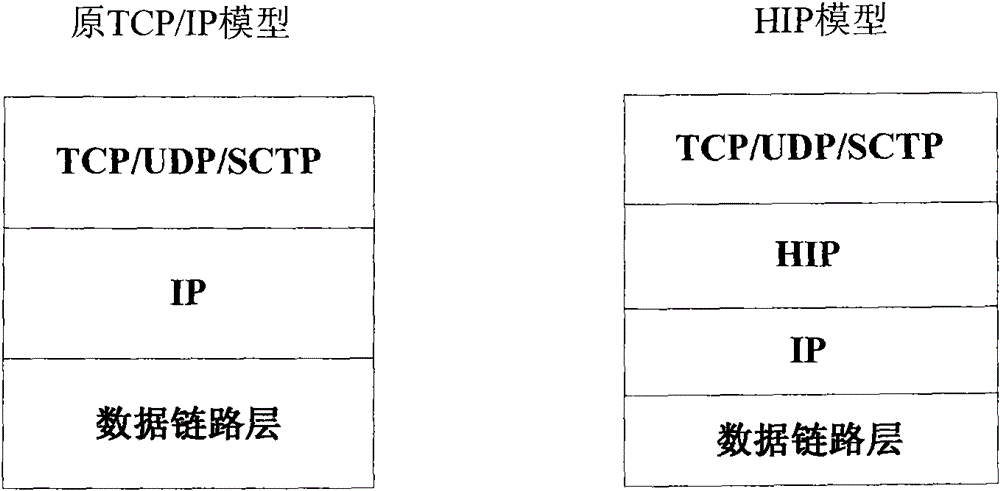
The Host Identity Protocol (HIP) is a host identification technology for use on Internet Protocol (IP) networks, such as the Internet. The Internet has two main name spaces, IP addresses and the Domain Name System. HIP separates the end-point identifier and locator roles of IP addresses. It introduces a Host Identity (HI) name space, based on a public key security infrastructure.
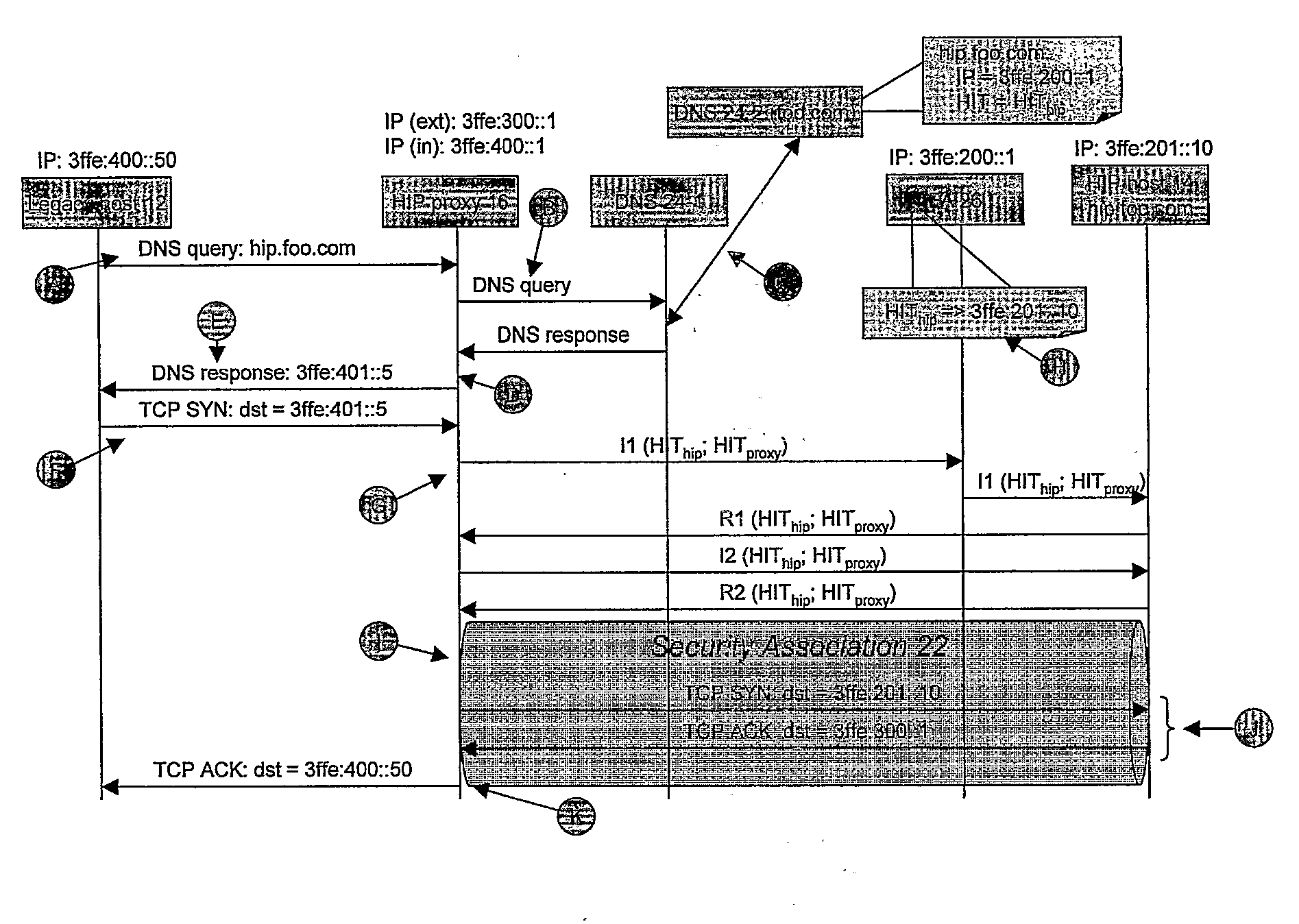
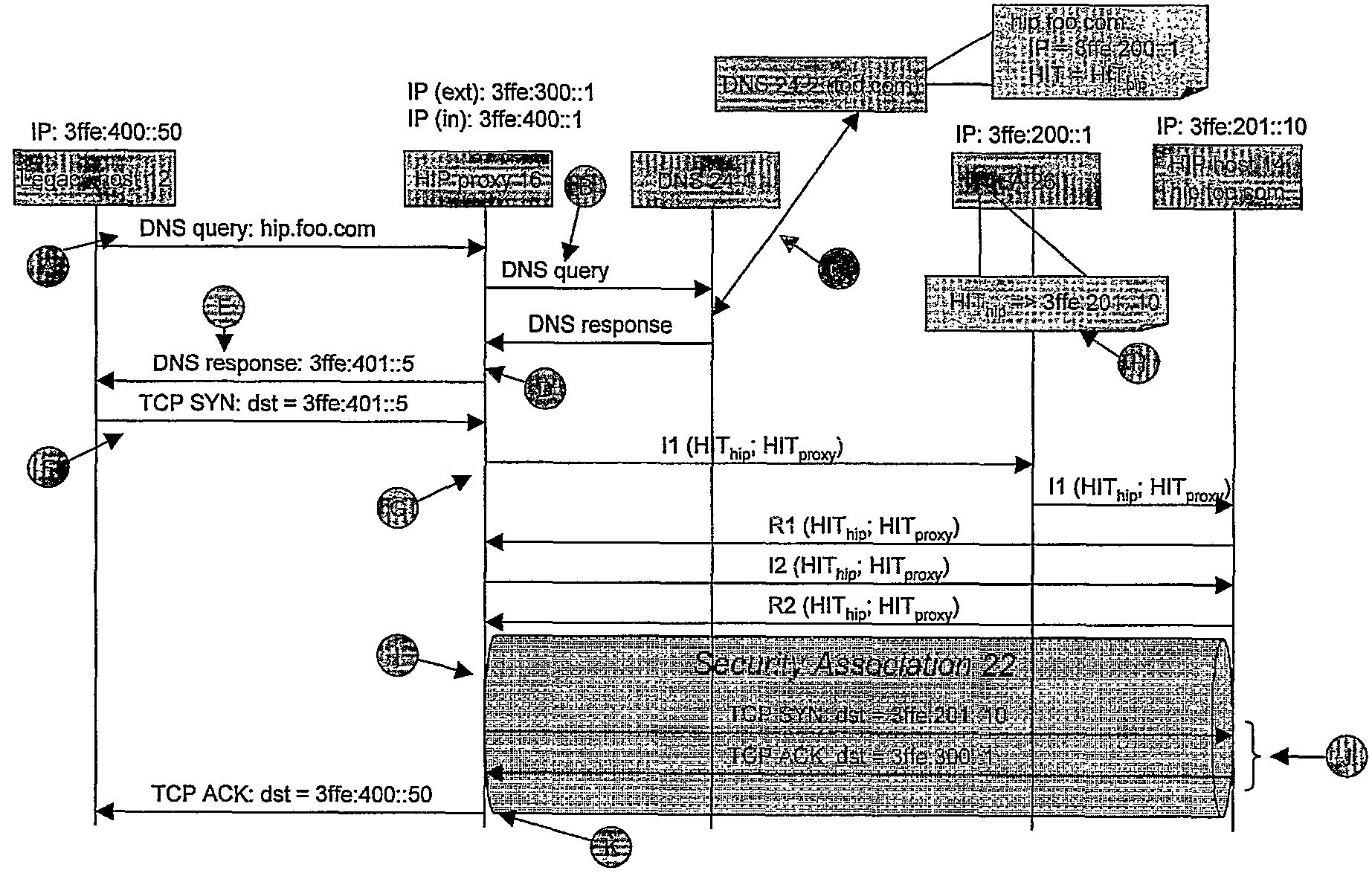
Addressing Method and Method and Apparatus for Establishing Host Identity Protocol (Hip) Connections Between Legacy and Hip Nodes
InactiveUS20070274312A1Data switching by path configurationWireless network protocolsSecure communicationIp address
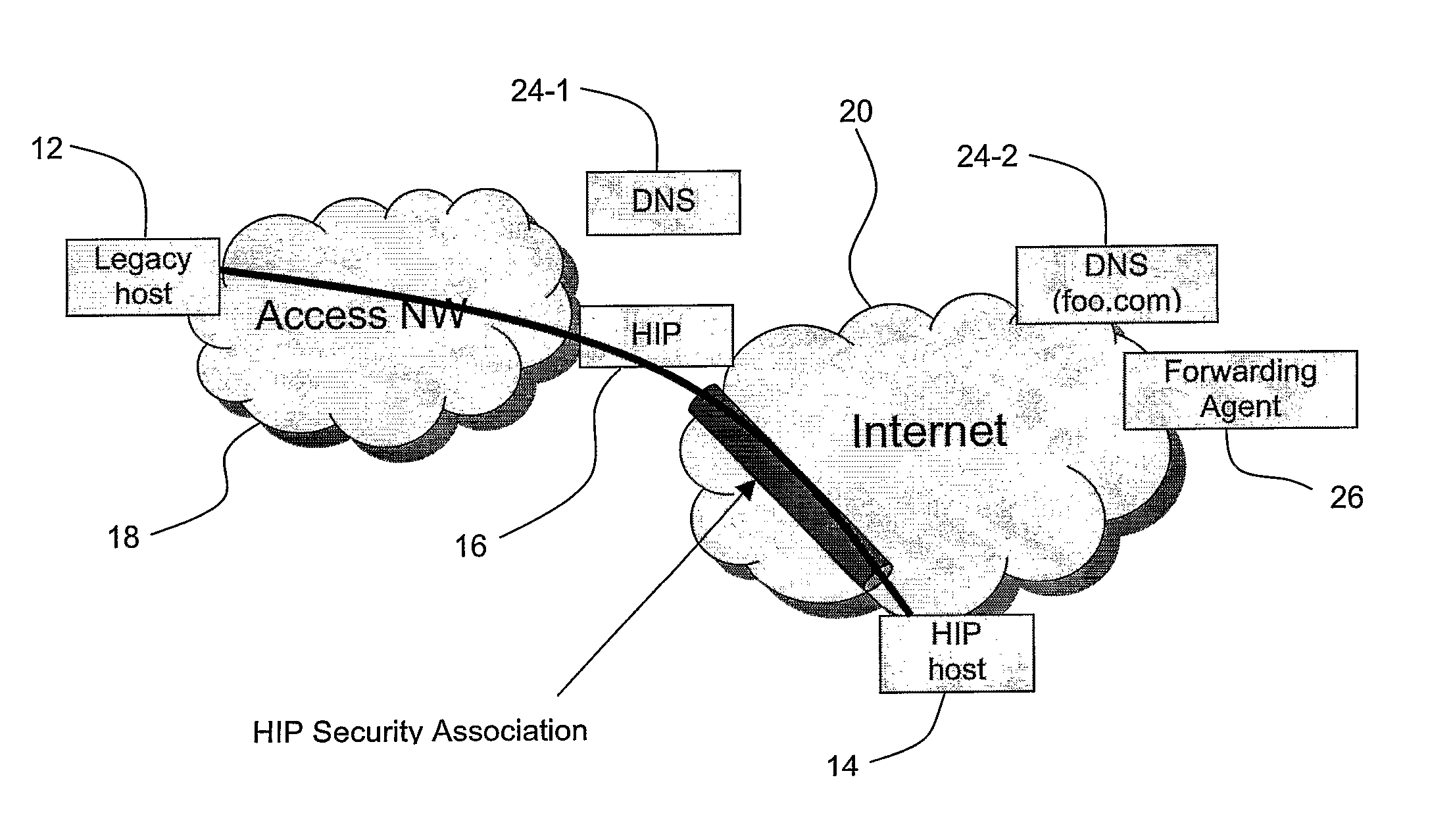
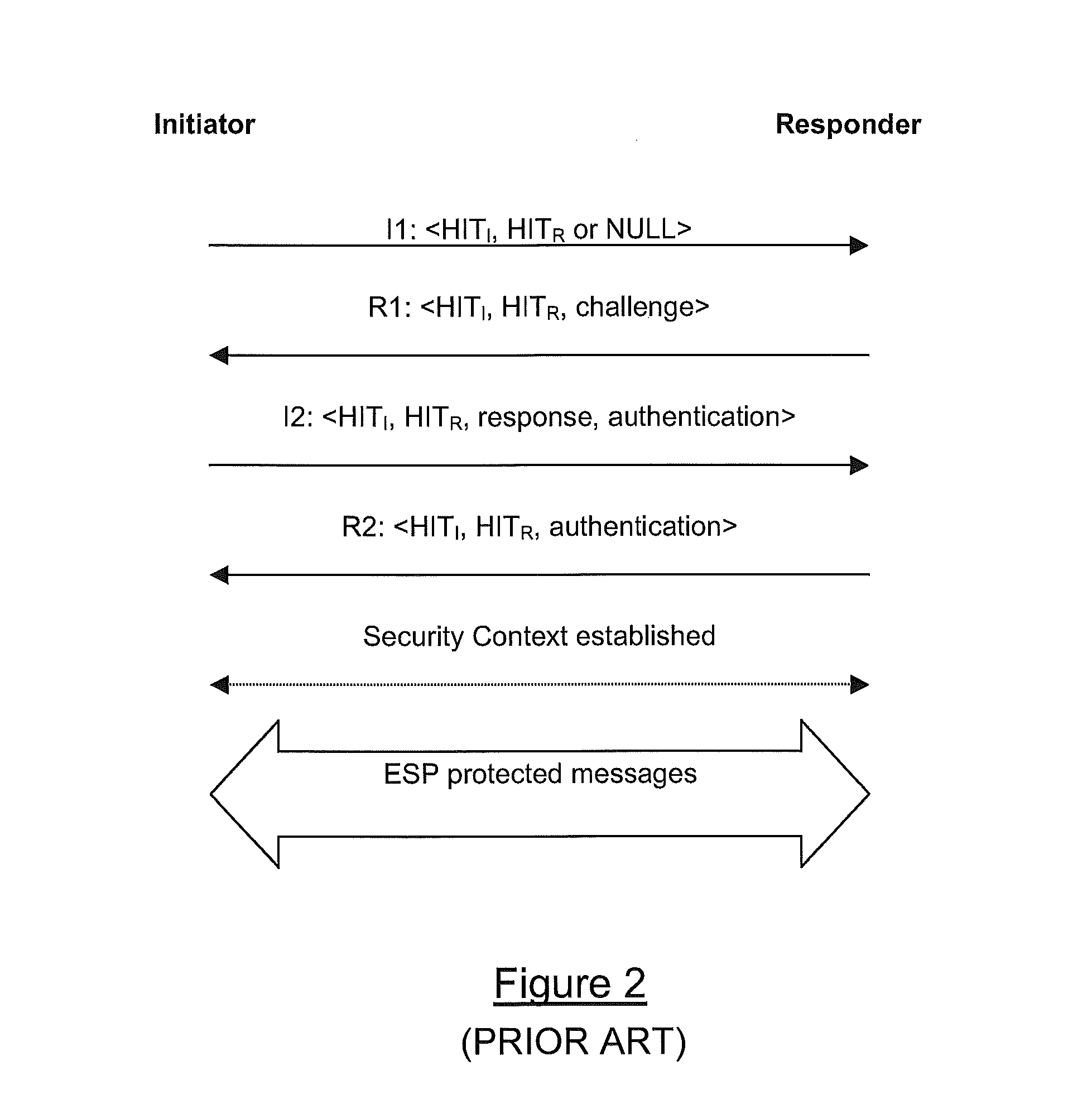
A method is provided of at least partially securing communications, via a HIP proxy (16), between a first host (12) which is not HIP enabled and a second host (14) which is HIP enabled, the method comprising: sending (A) a query from the first host (12) to resolve the IP address of the second host (14); in response to said query, retrieving (B, C) an IP address (IPfa) and HIT (HIThip) associated with the second host (14), returning (E) from the proxy (16) a substitute IP address (IPres) associated with the second host (14), and maintaining (D) at the proxy (16) a mapping between the substitute IP address (IPres), the retrieved IP address (IPfa) and the retrieved HIT (HIThip); and upon receipt (F) of a session initiation message (TCP SYN) at the proxy (16) from the first host (12) including as its destination address the substitute IP address (IPres), using the mapping to negotiate a secure HIP connection (22) between the proxy (16) and the second host (14).
Owner:TELEFON AB LM ERICSSON (PUBL)
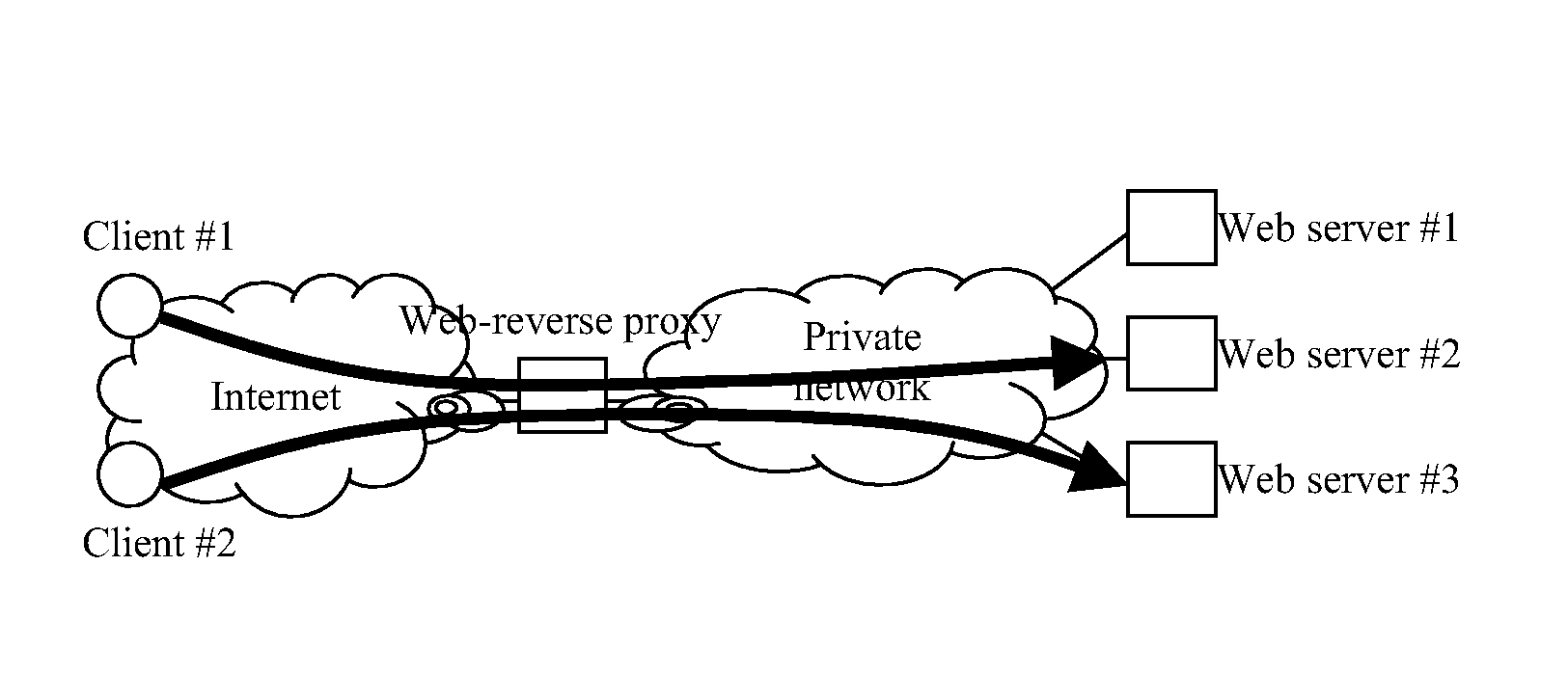
Addressing and routing mechanism for web server clusters
InactiveUS20090265541A1Good for load balancingUser identity/authority verificationTransmissionReverse proxyWeb service
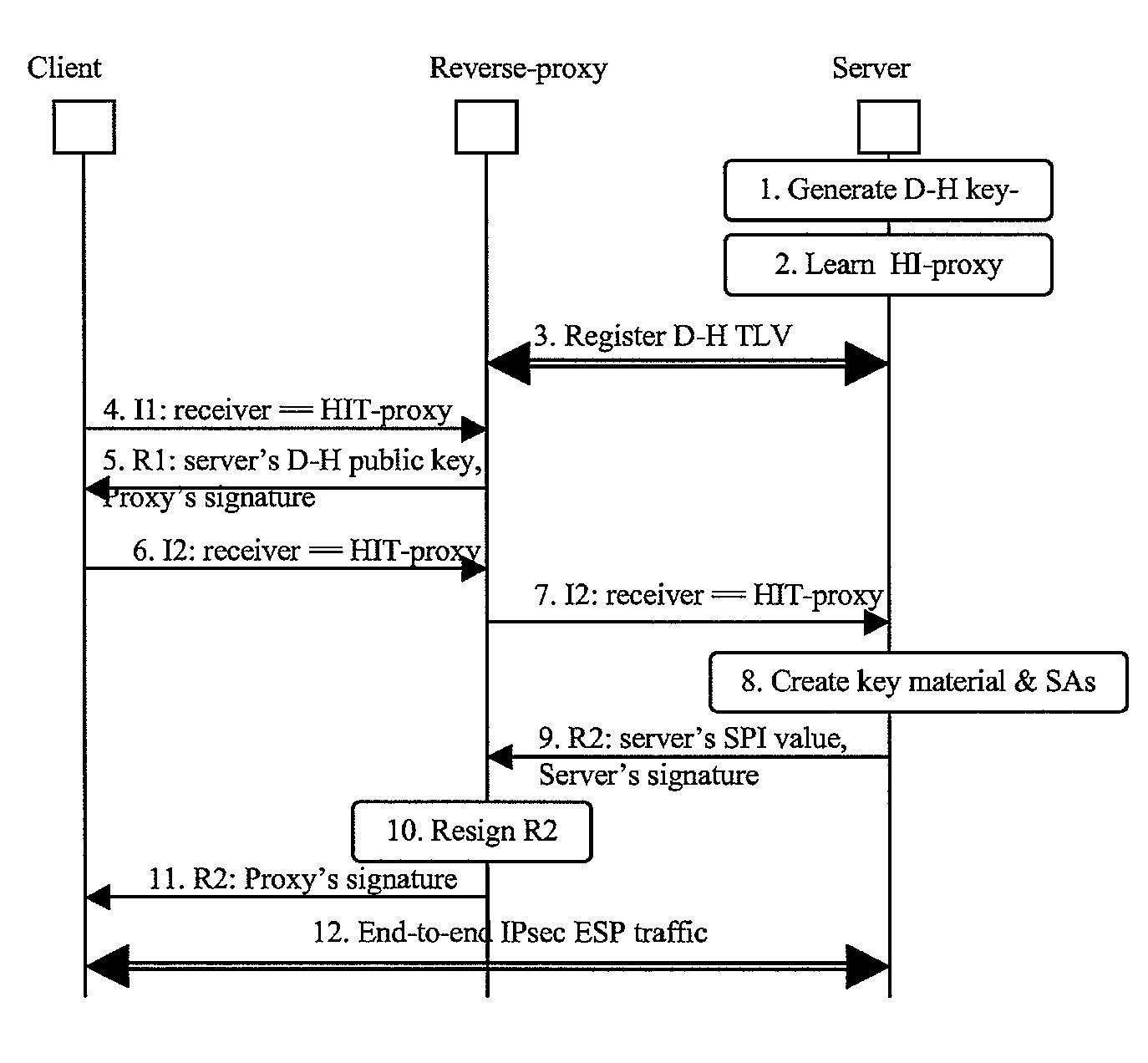
A method of establishing a Host Identity Protocol session between first and second Host Identity Protocol enabled hosts, where at least said second host is located behind a reverse-proxy. The method comprises providing the reverse-proxy with Diffie-Hellman public keying material of the second host, sending said Diffie-Hellman public keying material from the reverse-proxy to the first host as part of the Host Identity Protocol base exchange procedure, this material being bound to the Host Identity of the reverse-proxy for the purpose of the Host Identity Protocol session, and, at the first host, using the Host Identity of the reverse-proxy as the correspondent Host Identity for the Host Identity Protocol session, and, at the second host, using the Host Identity of the reverse-proxy as the originating Host Identity for the Host Identity Protocol session.
Owner:TELEFON AB LM ERICSSON (PUBL)
Identification method and apparatus for establishing host identity protocol (hip) connections between legacy and hip nodes
InactiveCN1939000AWireless network protocolsData switching networksSecure communicationComputer network
A method is provided of using the Host Identity Protocol (HIP) to at least partially secure communications between a first host (102) operating in a first network environment and a second, HIP-enabled, host (122) operating in a second network environment, with a gateway node (114) forming a gateway between the two environments. In the method, an identifier is associated with the first host (102), stored at the gateway node (114), and sent to the first host (102). The identifier is then used as a source address in a subsequent session initiation message sent from the first host (102) to the gateway node (114), having an indication that the destination of the message is the second host (122). The stored identifier at the gateway node is then used to negotiate a secure HIP connection to the second host. The first network environment may bc a UMTS or GPRS environment, in which case the gateway node may be a Gateway GPRS Support Node (GGSN).
Owner:TELEFON AB LM ERICSSON (PUBL)
P2P network SIP realizing method based on host machine mark protocol
InactiveCN1801822AChange complexityChange cycleTransmissionSession managementCommunications software
Present invention relates to Conversation initialisation protocol SIP which is most widely used appliance session management protocol. It contains operating SIP protocol in peer network and overcomes the shortage of high development cost in traditional client server mode. Based mainframe identify protocol, said invention can provides safety transmission for SIP user data. It can provide more complete network layer movability support. Due to SIP is the most basic protocol composition in instant communication software, IP multimedia subsystem IMS etc network service and application, said invention has wide application.
Owner:BEIJING JIAOTONG UNIV
Addressing method and method and apparatus for establishing host identity protocol (HIP) connections between legacy and HIP nodes
InactiveUS7827313B2User identity/authority verificationMultiple digital computer combinationsSecure communicationInternet privacy
A method is provided of at least partially securing communications, via a HIP proxy (16), between a first host (12) which is not HIP enabled and a second host (14) which is HIP enabled, the method comprising: sending (A) a query from the first host (12) to resolve the IP address of the second host (14); in response to said query, retrieving (B, C) an IP address (IPfa) and HIT (HIThip) associated with the second host (14), returning (E) from the proxy (16) a substitute IP address (IPres) associated with the second host (14), and maintaining (D) at the proxy (16) a mapping between the substitute IP address (IPres), the retrieved IP address (IPfa) and the retrieved HIT (HIThip); and upon receipt (F) of a session initiation message (TCP SYN) at the proxy (16) from the first host (12) including as its destination address the substitute IP address (IPres), using the mapping to negotiate a secure HIP connection (22) between the proxy (16) and the second host (14).
Owner:TELEFON AB LM ERICSSON (PUBL)
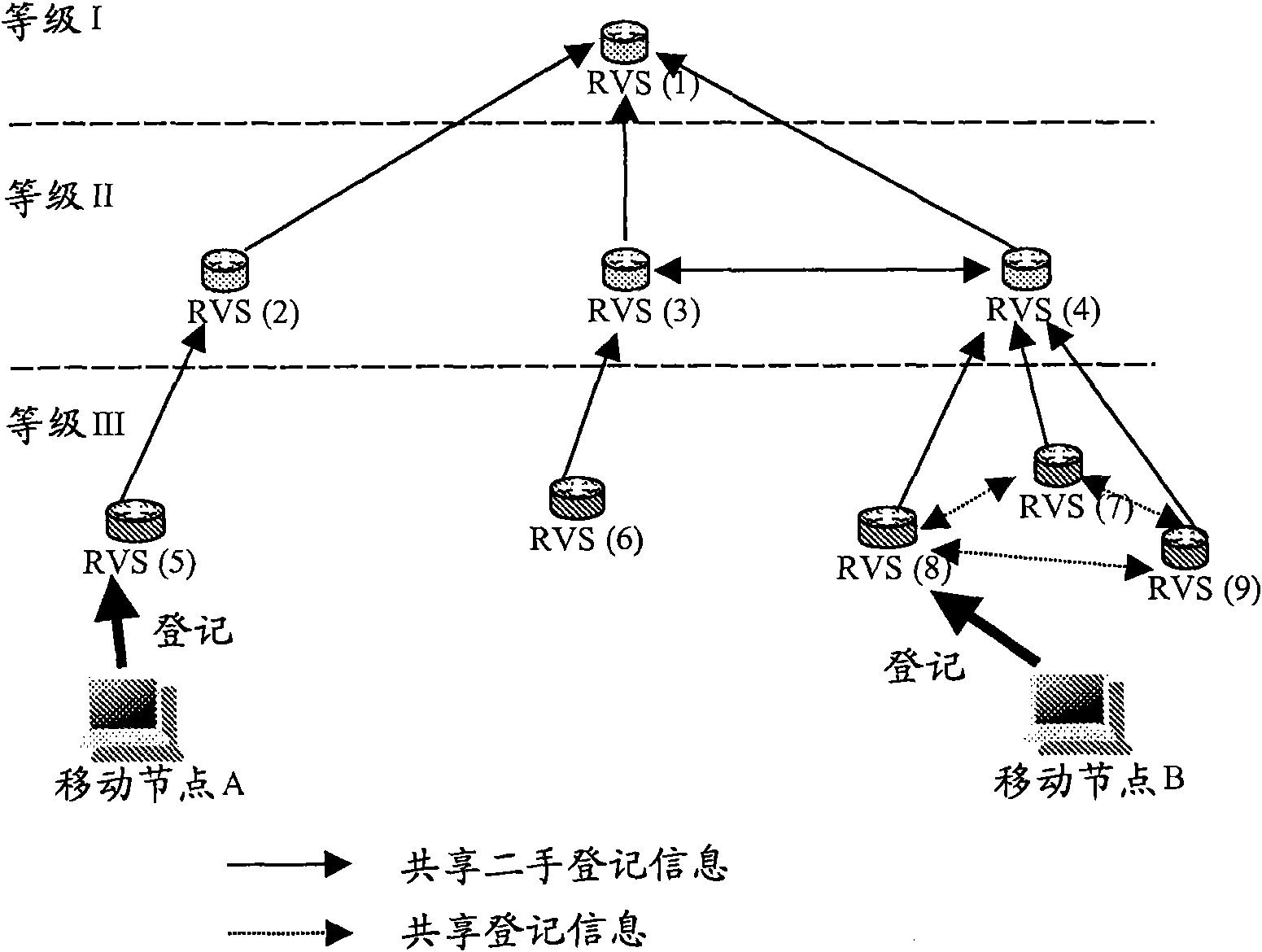
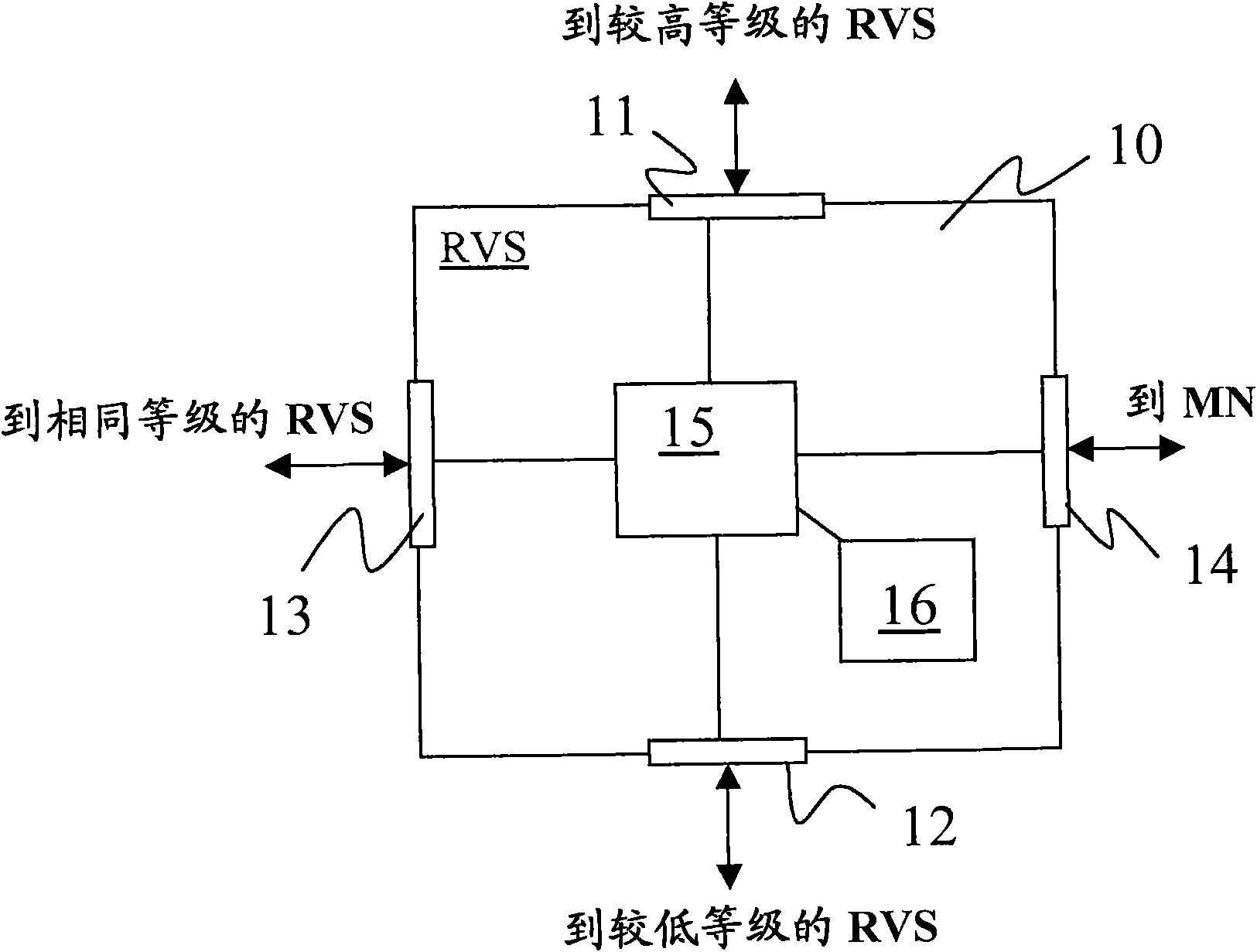
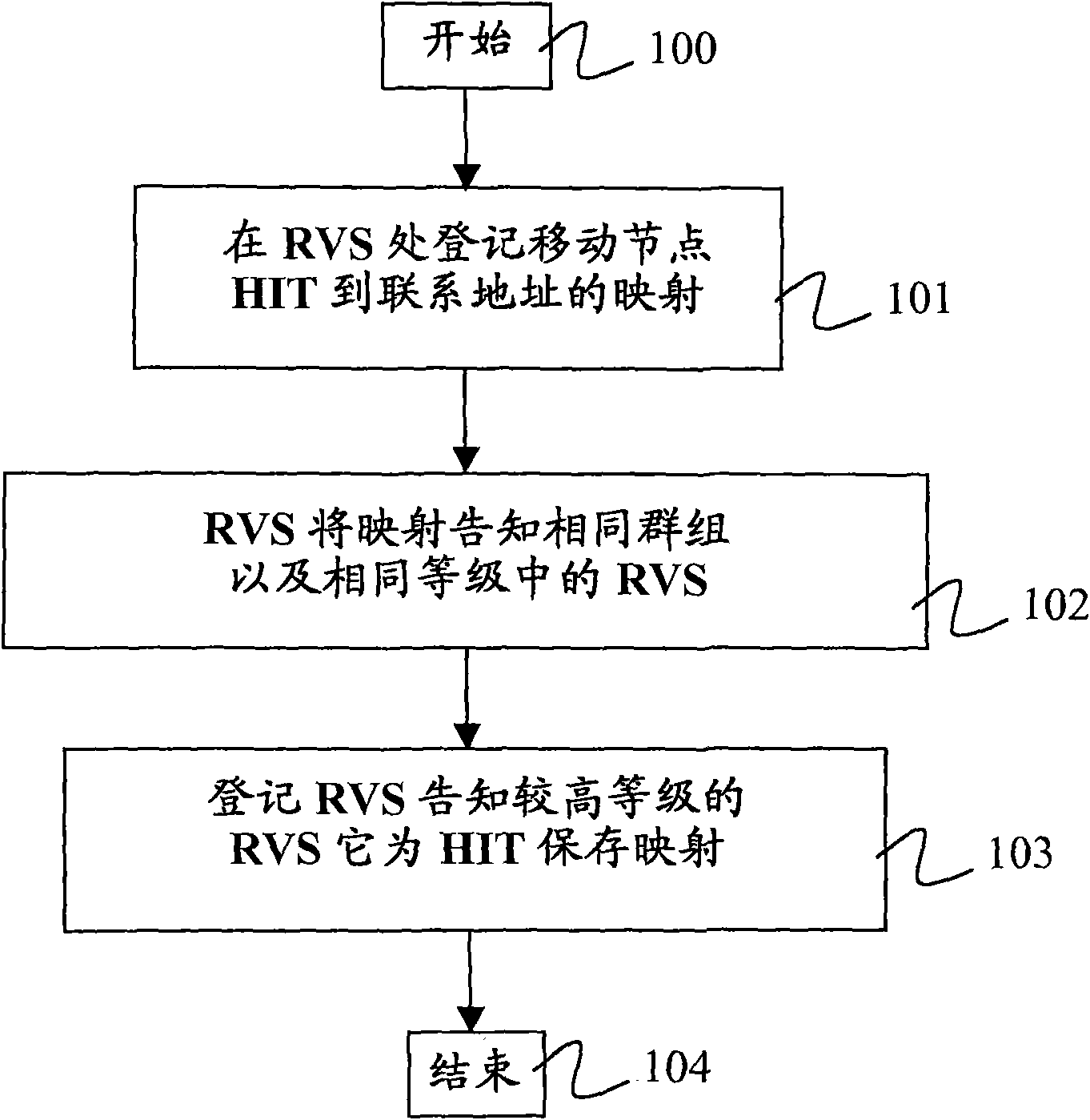
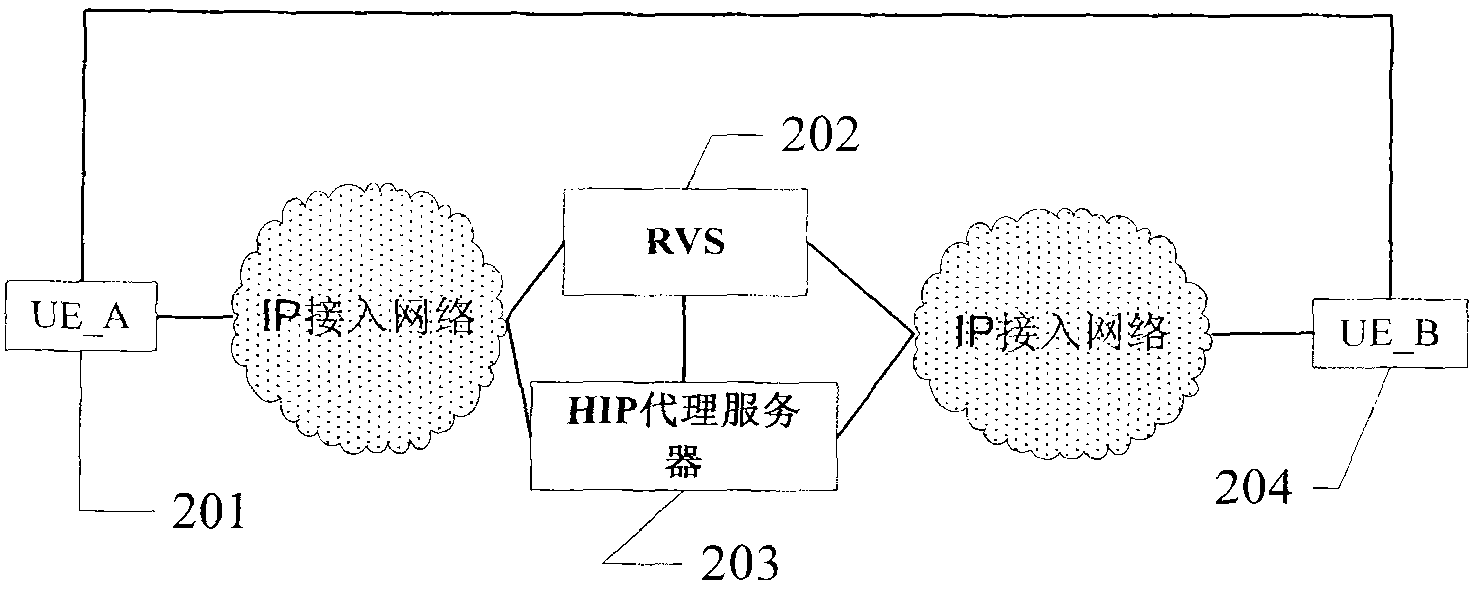
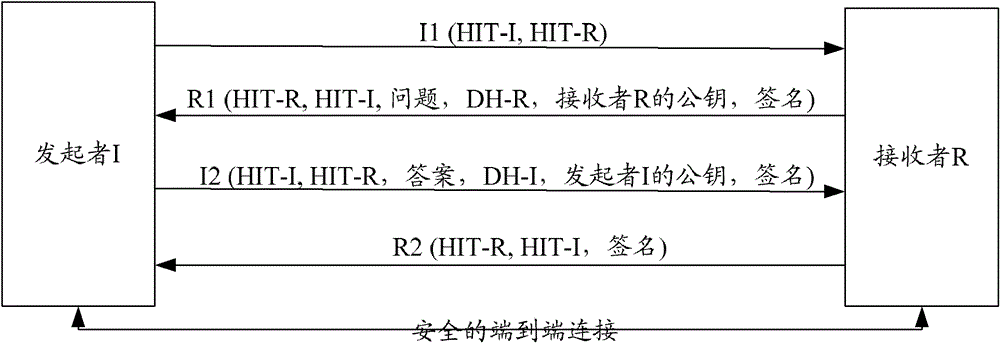
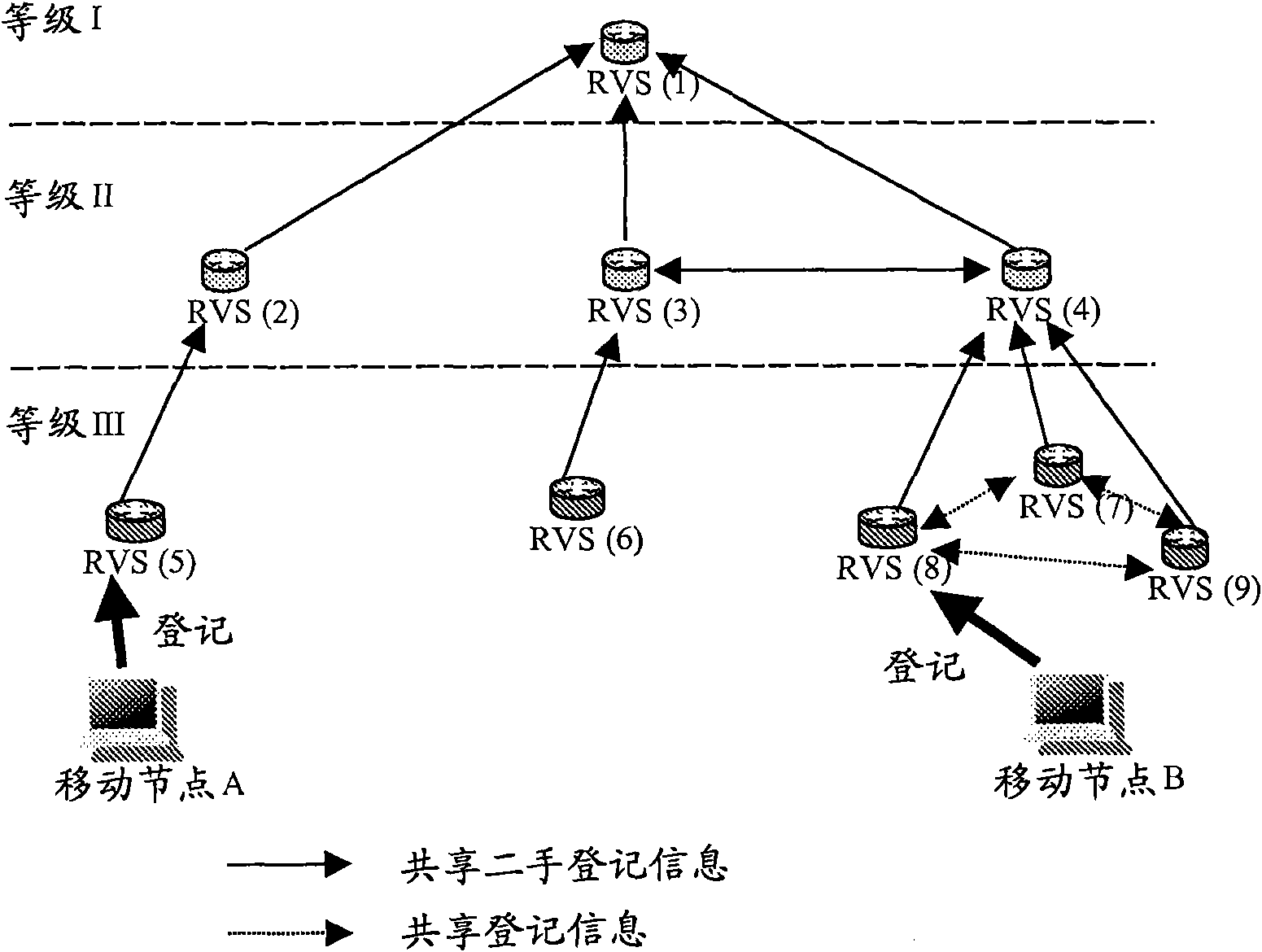
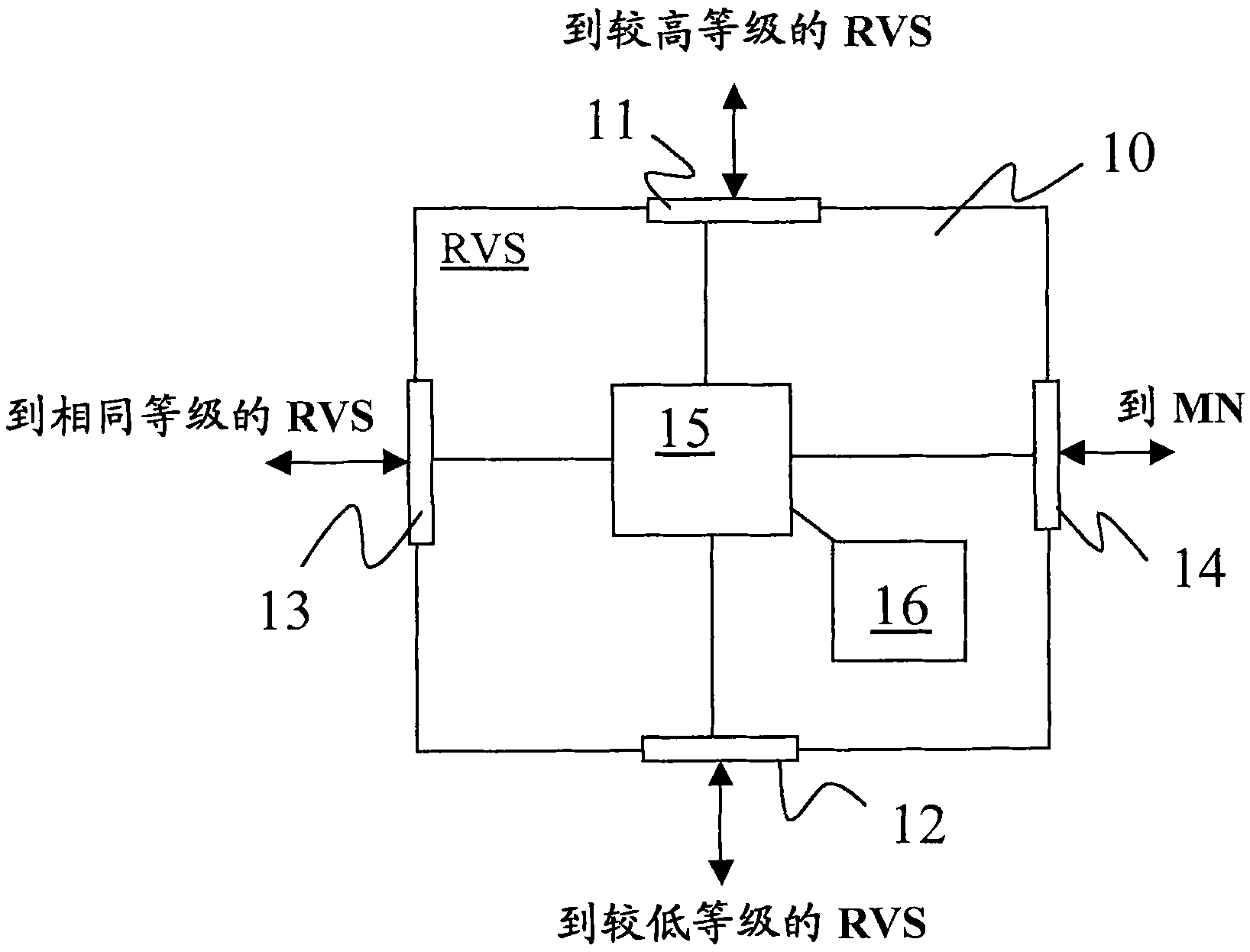
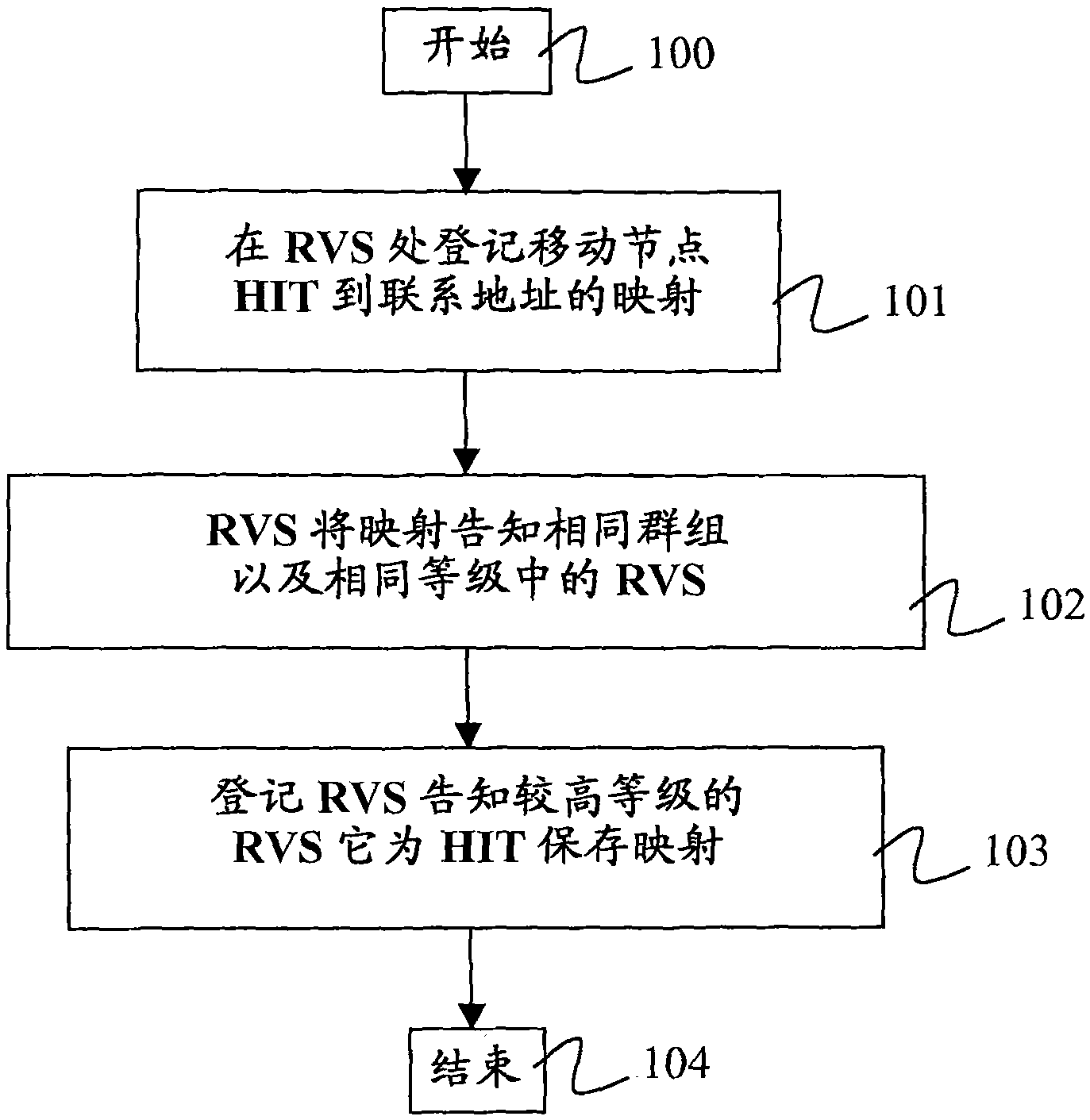
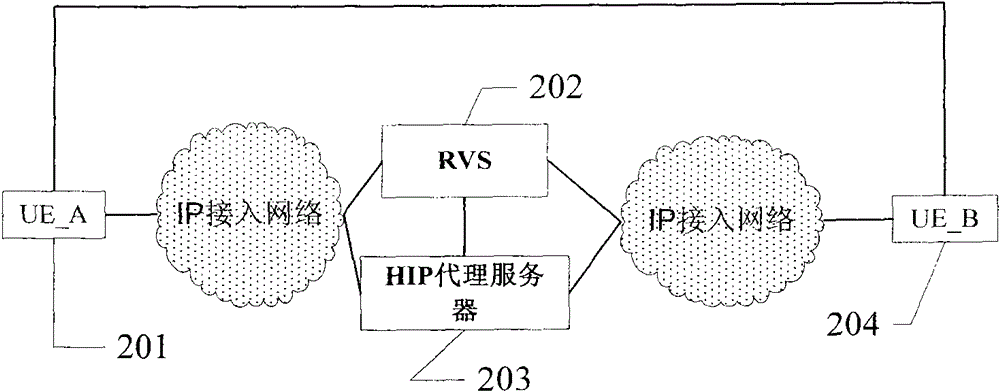
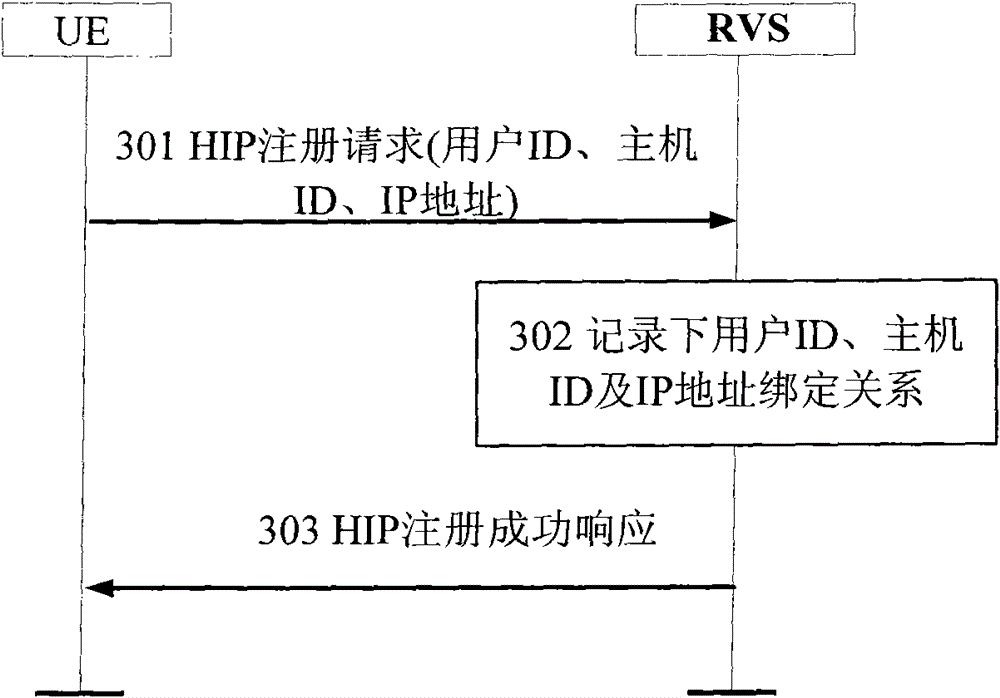
HIP node reachability
The invention relates to a method of configuring a plurality of rendezvous servers to provide a Host Identity Protocol, HIP, based mobility service to HIP nodes, where the servers are arranged in a hierarchical branching structure. For each HIP node, a Host Identity Tag, HIT,- and contact address mapping is registered with a rendezvous server (101). That server then identifies itself and the HIT to each higher level server within the same branch, without explicitly identifying the contact address to those higher level servers (103) wherein, in use, when a first rendezvous server receives a HIPcontact message addressed to a given HIT (201), if that first server is unaware of the destination HIT, it forwards the message to a higher level server within the same branch (204), and if the firstserver is not the server at which the HIT is registered but is aware of the HIT, it forwards the contact message to the neighbouring rendezvous server corresponding to the HIT (203).
Owner:OPTIS WIRELESS TECH LLC
HIP (Host Identity Protocol) based method and system for achieving user mobility
InactiveCN101931611ASupport mobilityWireless network protocolsTransmissionHost Identity ProtocolComputer science
The invention relates to a HIP (Host Identity Protocol) based method for realizing user mobility, comprising the following steps of: a registration step: the host equipment initiates a registration process to a set server, and the set server stores the mapping relation between user identification of a host equipment user and the host identification and the location identification of the host equipment; and a connection establishment step: the host equipment queries the set server according to the user identification of an opposite end user and establishes connection with the host equipment of the opposite end user by adopting the HIP according to a query result. The HIP based method and system for realizing the user mobility can realize the mobility taking the user as a centre.
Owner:ZTE CORP
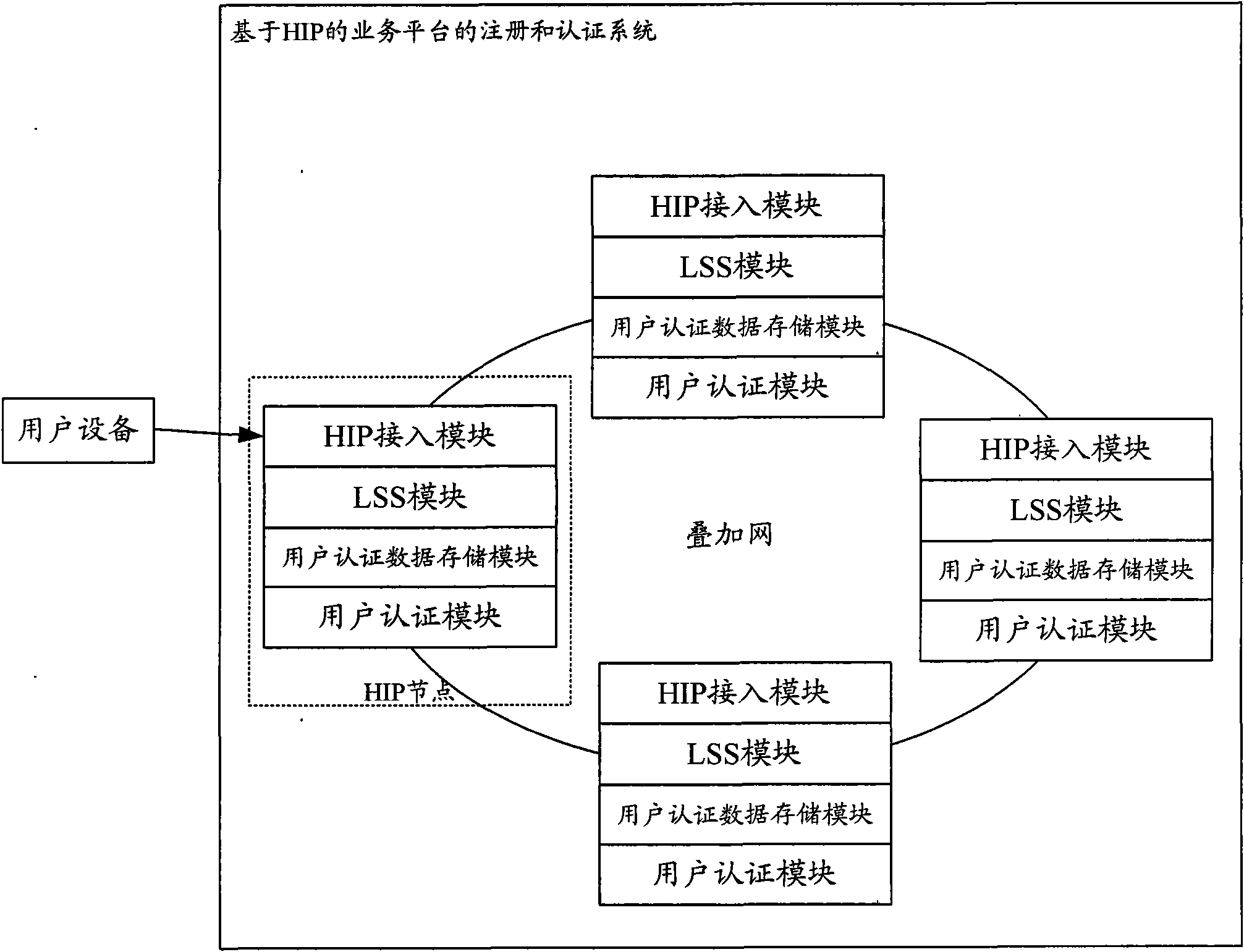
Registration and authentication method and system based on HIP (host identity protocol)
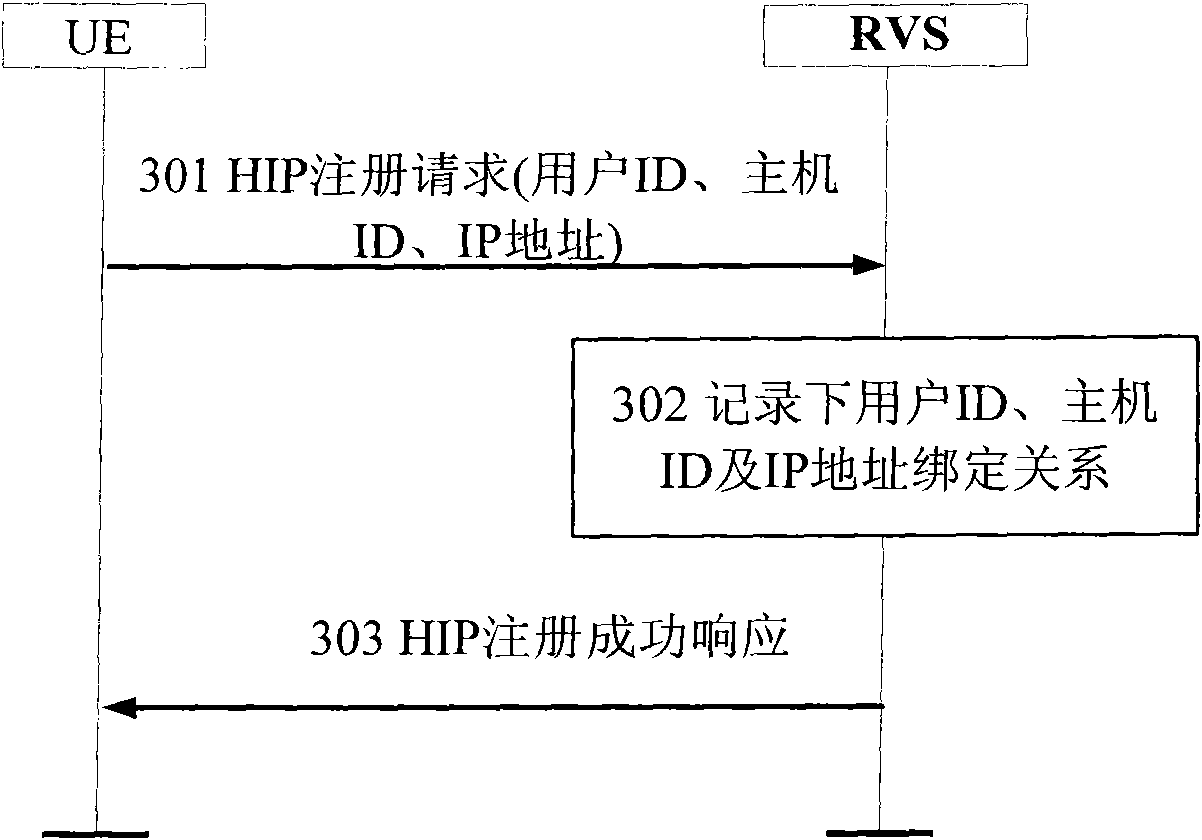
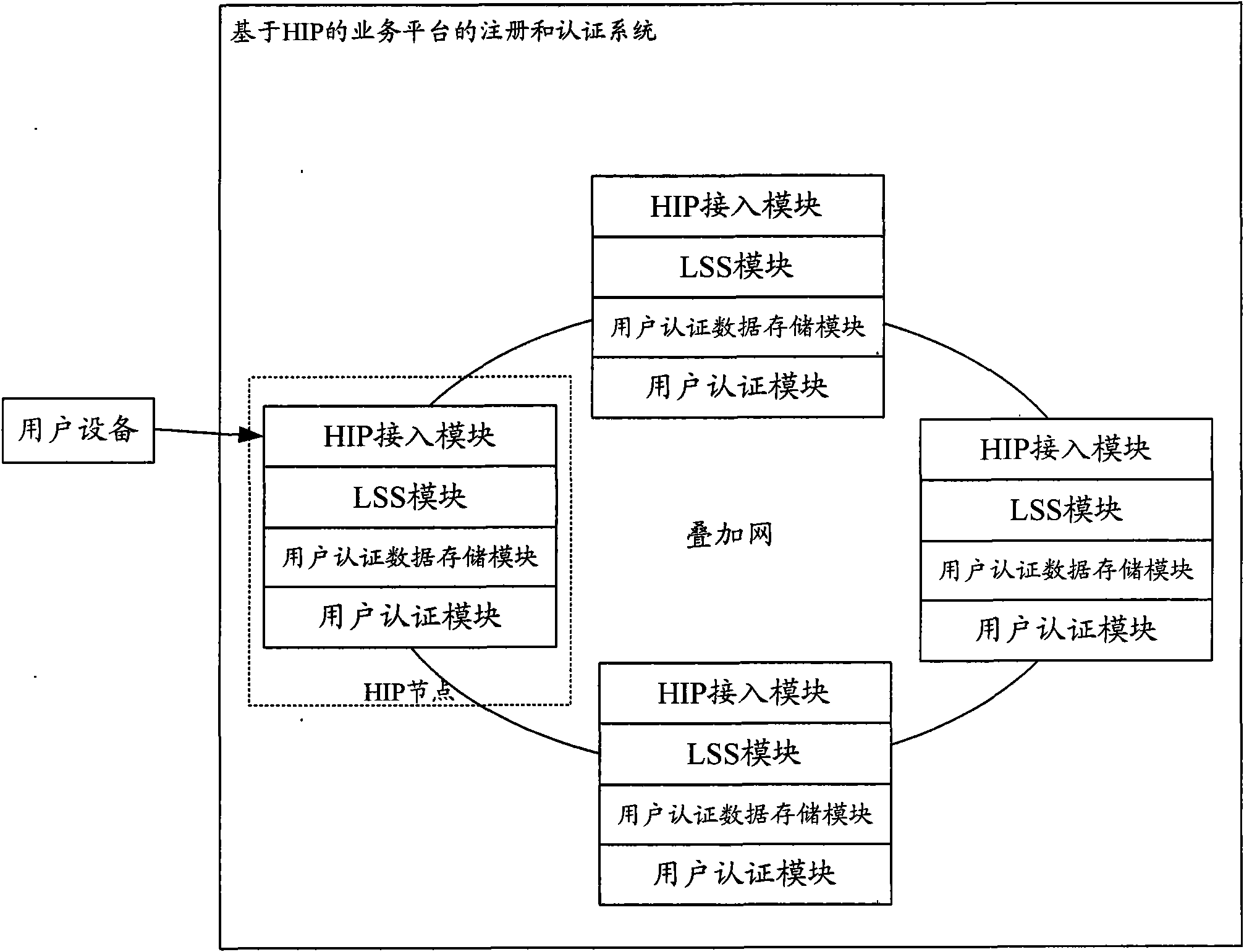
ActiveCN102123391ASave resourcesSave reasonable expensesTransmissionSecurity arrangementTelecommunications networkIp address
The invention provides a registration and authentication method and system based on HIP (host identity protocol). User equipment is accessed into a distributed telecommunication service platform based on HIP by an HIP node, and an authentication method in a telecommunication network is adopted to authenticate the user equipment; and after the user equipment passes authentication, association information between a user identification of the user equipment and the HIP node and association information between the user identification of the user equipment and the current IP (internet protocol) address of the user equipment are stored in the HIP node. The invention provides a service platform with unified user management, transparent support mobility and multi-cavity performance, and new service income is acquired; and in addition, due to use of the original authentication system of the communication network, the resources of the network and the terminal are saved, the investment is reduced, and the reasonable overhead of mobile equipment and the network is guaranteed. Simultaneously, an application provider does not need to carry out investment construction of user management, support mobility and multi-cavity performance so as to save the capital expenditure, therefore, the win-win situation of the application provider and a network operator is achieved.
Owner:ZTE CORP
Host identity protocol method and apparatus
InactiveUS7873825B2Safe handlingAvoid widespread disseminationMultiple digital computer combinationsWireless network protocolsSecure communicationComputer network
A method of using the Host Identity Protocol (HIP) to at least partially secure communications between a first host operating in a first network environment and a second, HIP-enabled, host operating in a second network environment, with a gateway node forming a gateway between the two environments. An identifier is associated with the first host, stored at the gateway node, and sent to the first host. The identifier is then used as a source address in a subsequent session initiation message sent from the first host to the gateway node, having an indication that the destination of the message is the second host. The stored identifier at the gateway node is then used to negotiate a secure HIP connection to the second host. The first network environment may be a UMTS or GPRS environment, in which case the gateway node may be a Gateway GPRS Support Node (GGSN).
Owner:TELEFON AB LM ERICSSON (PUBL)
Addressing and routing mechanism for web server clusters
InactiveUS8041939B2Good for load balancingUser identity/authority verificationReverse proxyWeb service
A method of establishing a Host Identity Protocol session between first and second Host Identity Protocol enabled hosts, where at least said second host is located behind a reverse-proxy. The method comprises providing the reverse-proxy with Diffie-Hellman public keying material of the second host, sending said Diffie-Hellman public keying material from the reverse-proxy to the first host as part of the Host Identity Protocol base exchange procedure, this material being bound to the Host Identity of the reverse-proxy for the purpose of the Host Identity Protocol session, and, at the first host, using the Host Identity of the reverse-proxy as the correspondent Host Identity for the Host Identity Protocol session, and, at the second host, using the Host Identity of the reverse-proxy as the originating Host Identity for the Host Identity Protocol session.
Owner:TELEFON AB LM ERICSSON (PUBL)
Host identification protocol (HIP) safe channel multiplexing method and device thereof
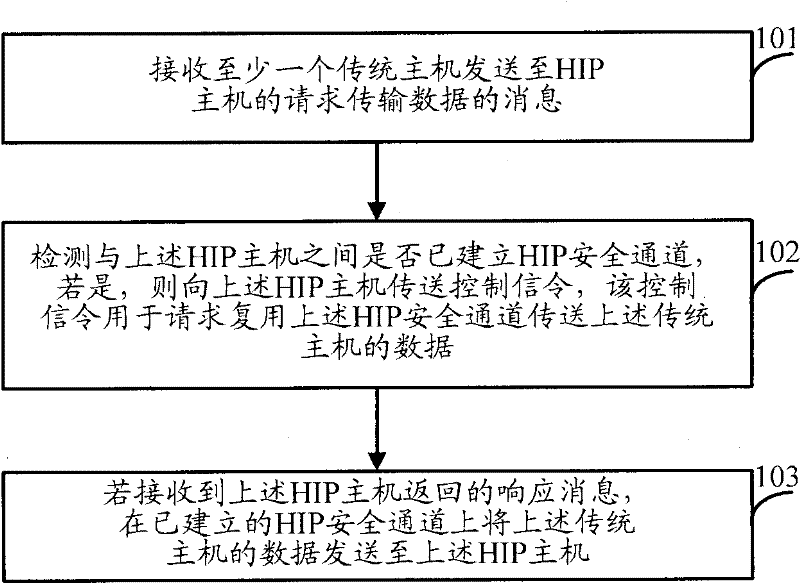
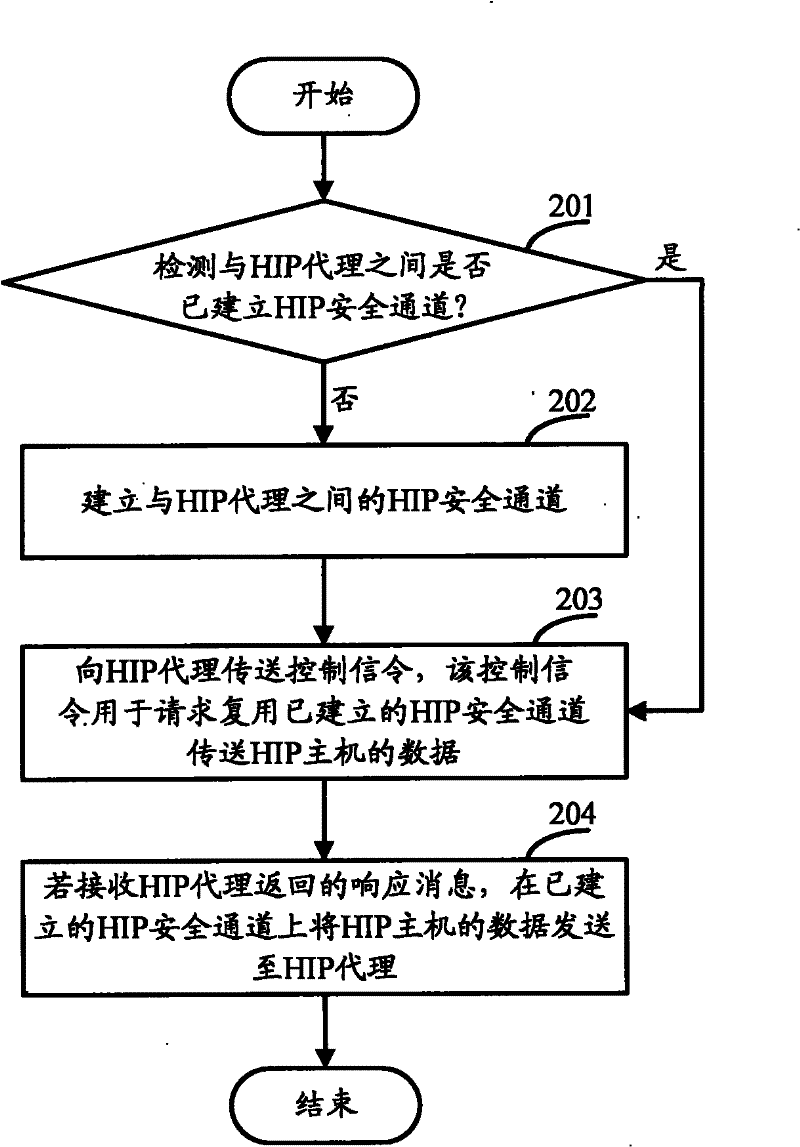
InactiveCN102223353AReduce in quantityReduce the burden onMultiplex communicationSecuring communicationMultiplexingControl signal
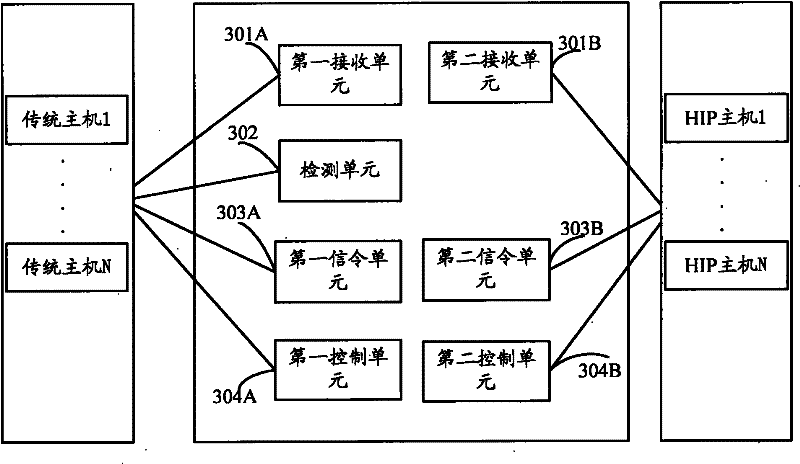
The embodiment of the invention relates to the field of safe channel multiplexing, and discloses a host identification protocol (HIP) safe channel multiplexing method and a device thereof, and is used for reducing the number of HIP safe channels and the maintenance cost. The method comprises the following steps: receiving a data transmission message request transmitted to HIP hosts by at least one traditional host; detecting whether the HIP safe channels are set up among the HIP hosts or not; if so, transmitting control signaling to the HIP hosts, wherein the control signaling is used for requesting to multiplex data transmitted to the traditional host by the HIP safe channels; and if response messages returned by the HIP hosts are received, transmitting the data of the traditional host to the HIP hosts through the HIP safe channels. The embodiment of the invention can reduce the number of the HIP safe channels set up among the HIP hosts and the cost for maintaining the safe channels, and improves the utilization rate of the HIP safe channels.
Owner:HUAWEI TECH CO LTD
Secure multi-party network communication platform and construction method and communication method thereof
InactiveCN101997875AFlexible and convenient managementLow costPublic key for secure communicationUser identity/authority verificationOpen sourceNetwork communication
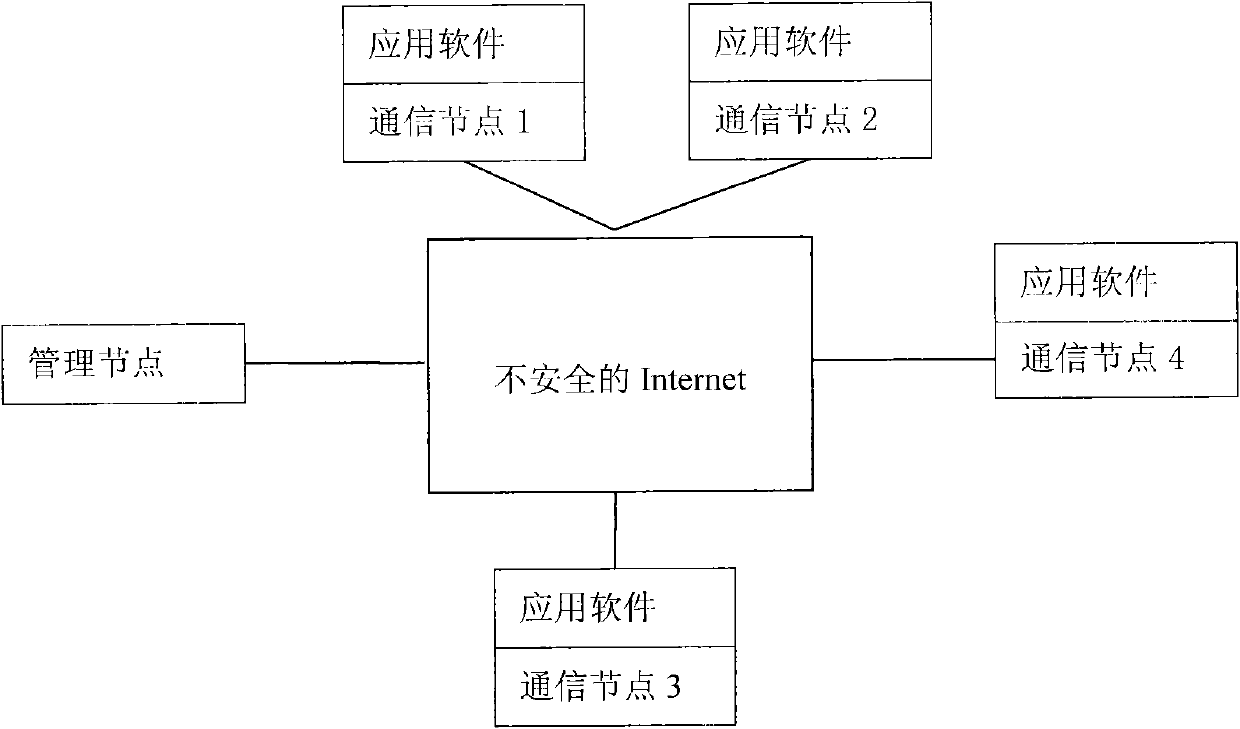
The invention relates to a secure multi-party network communication platform and a construction method and a communication method thereof, and belongs to the fields of distributed systems and computer networks. The multi-party communication platform consists of a management node and a group of host nodes needing intercommunication; by Internet connection, the multi-party communication platform can realize secure and efficient multi-party communication and provide a secure channel for network application software deployed on the communication nodes; the security of the communication layer is realized by using a host identification protocol, and authentication security is realized by using a public key / secret key system on management; the protocol is realized by an open source and supports multiple common operating systems, so the cost of the scheme is very low; centralized member management adopted by the method is flexible and convenient; different from multi-hop forwarding and layer-upon-layer encryption of an onion router protocol, the data of a host marking protocol are finished in one hop between double communication parties and encrypted at one time, so the efficiency is greatly improved, and the data are totally transparent for upper application.
Owner:PEKING UNIV
Host identity protocol method and apparatus
InactiveUS7849195B2Multiple digital computer combinationsSecuring communicationSecurity associationHost Identity Protocol
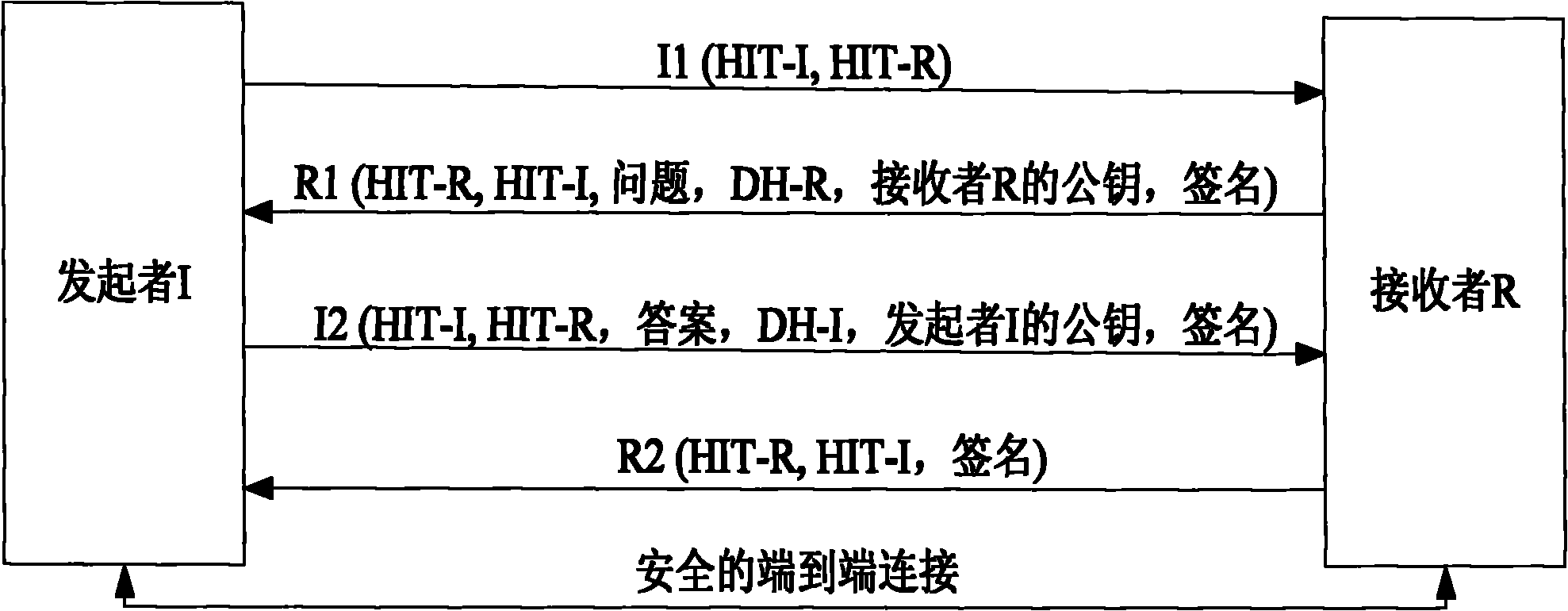
A method of establishing a connection between a second host and an application socket on a first host. The method utilizes the Host Identity Protocol (HIP). The method includes the steps of establishing either a new or a selected existing HIP Security Association between the first and second hosts; creating a new or selecting an existing Tube Association between the application socket and the Security Association; and forming an association for the connection between the application socket, the Security Association, and the Tube Association. This establishes a connection between the second host and the application socket on the first host through the Security Association and the Tube Association.
Owner:OPTIS WIRELESS TECH LLC
Denomination service scheme for network communicating system and communication method using the same
InactiveCN101510892AEffectively stealEffective defense against theftPublic key for secure communicationUser identity/authority verificationCommunications systemName binding
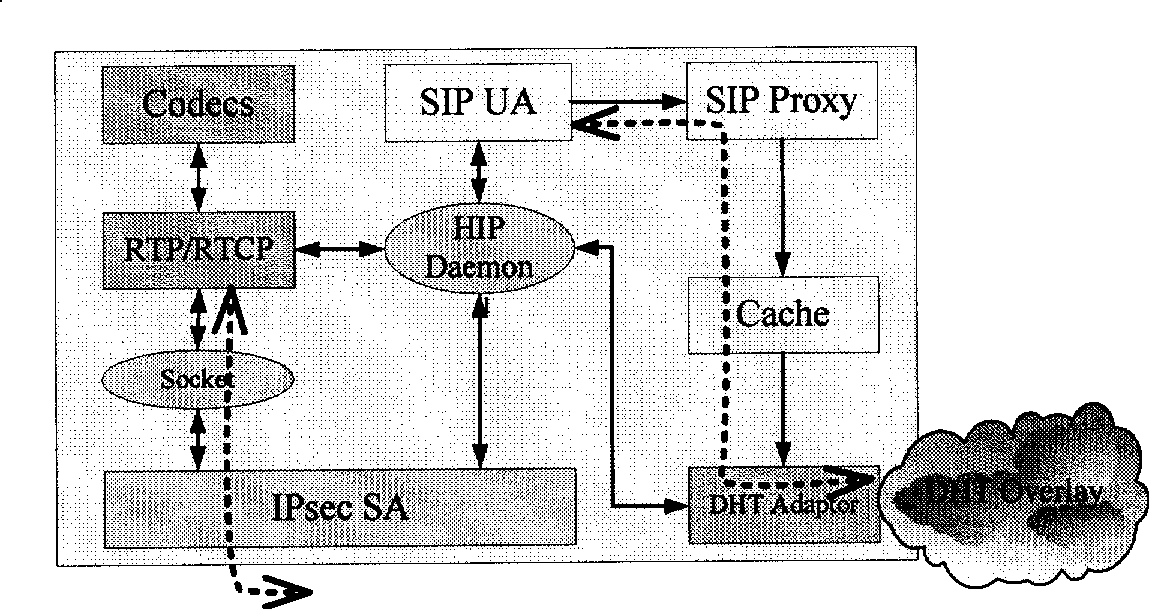
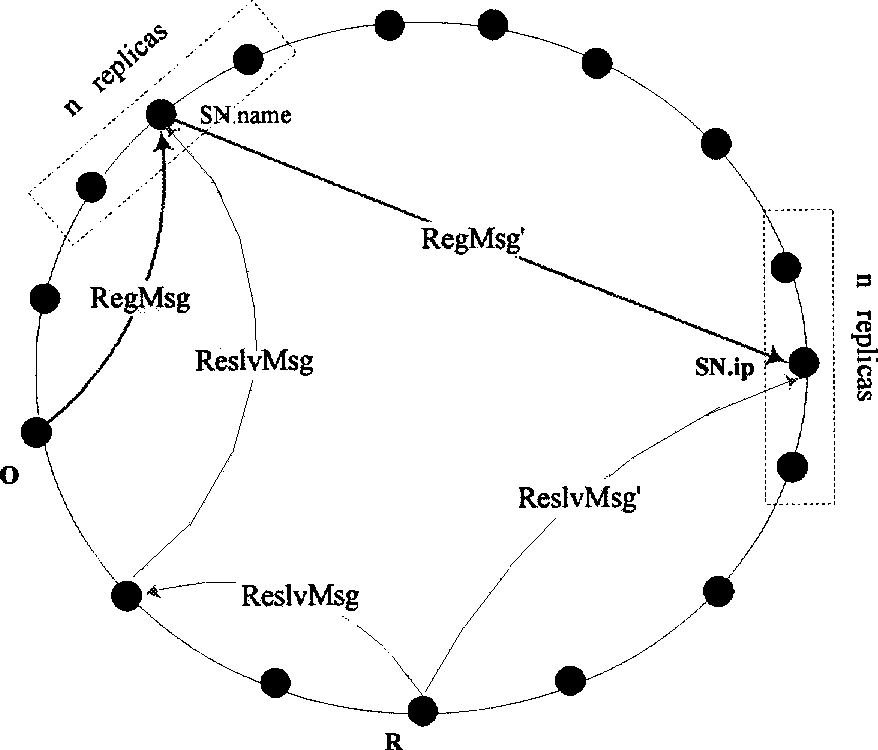
The invention relates to an IP network multimedia communication technique, in particular to a naming service proposal applied to a network communication system and a communication method realized by utilizing the proposal, which aim at solving the name binding problem of SIP, URI, HI / HIT and transmission address when a system integrates Host Identity Protocol (HIP), and realize such naming services as registration, updating and search of a user in a complete peer-to-peer manner on a Distributed Hash Table (DHT) overlay network; by using the proposal, the user uses an SIP URI for binding one or more HIs; each HI is used for binding one or more transmission addresses; the user can use the SIP URI and a private key for logging the system and conducting SIP call according to the HI / HIT, thereby finishing HIP base exchange continually and establishing a safe media data transmission channel; the distributed safety mechanism can effectively ensure the uniqueness of the verification of the user, prevent such attacks as service refusal and protect the storage and updating of name binding; and the invention utilizes the DHT overlay network to realize naming service and the transmission of standard SIP signaling information, is easy to realize and arrange and causes the user to enjoy simple and safe network communication services.
Owner:ZHONGYUAN ENGINEERING COLLEGE
Communication method, system and equipment based on host identity protocol (HIP)
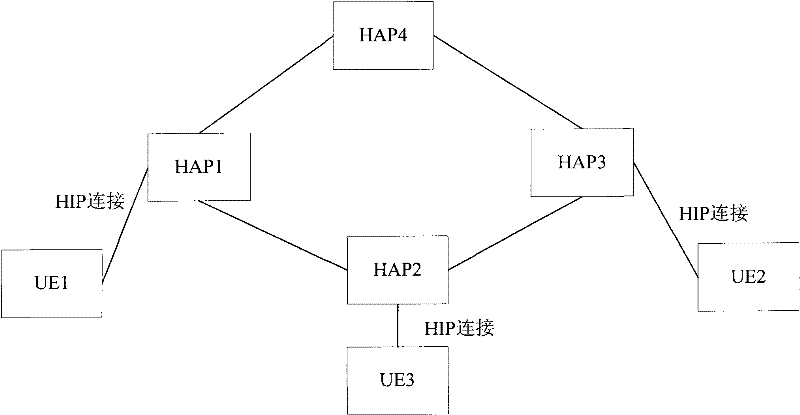
The invention relates to a communication method, system and equipment based on a host identity protocol (HIP). The method is realized on the basis of HIP equipment and a HIP equipment access point (HAP) and comprises the following steps: source-end HIP equipment and source-end HAP build HIP connection; the source-end HIP equipment sends a data packet to the source-end HAP by the HIP connection; and the source-end HAP receives the data packet and forwards according to the HIP connection relationship or the internet protocol (IP) address of destination-end equipment. According to the communication method, system and equipment based on the HIP, cost for building the HIP connection can be reduced.
Owner:苏州医疗器械产业发展集团有限公司
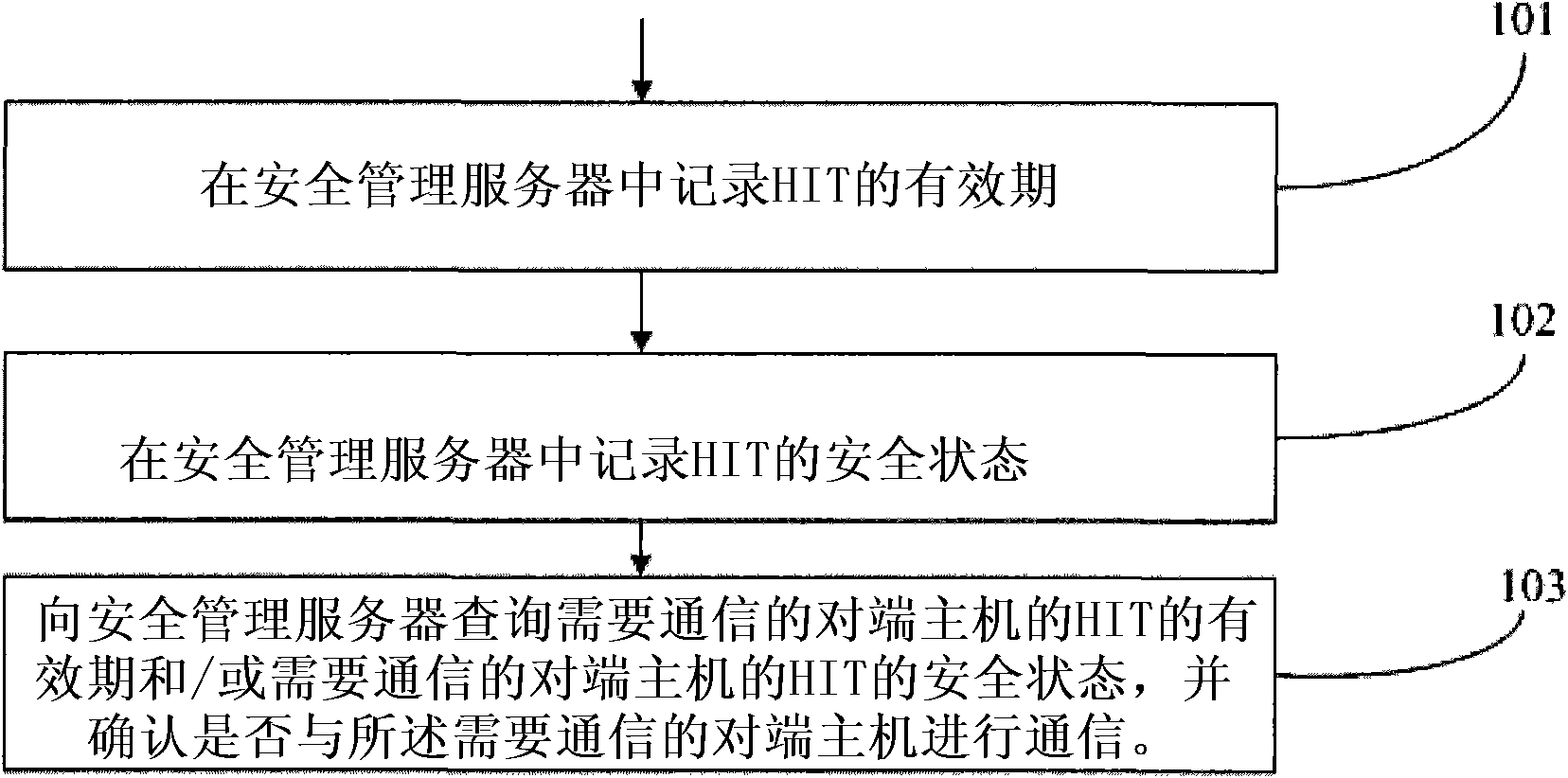
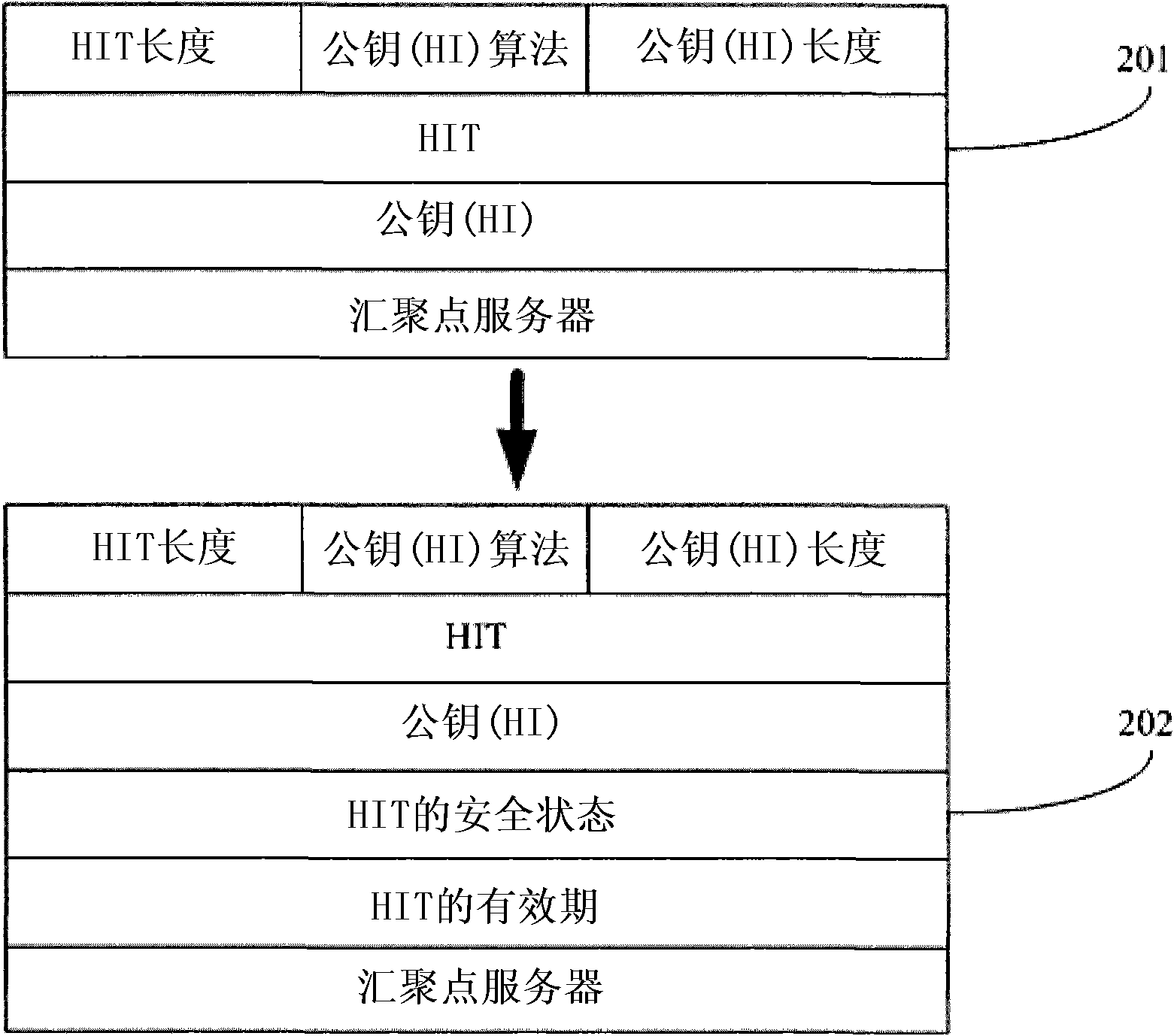
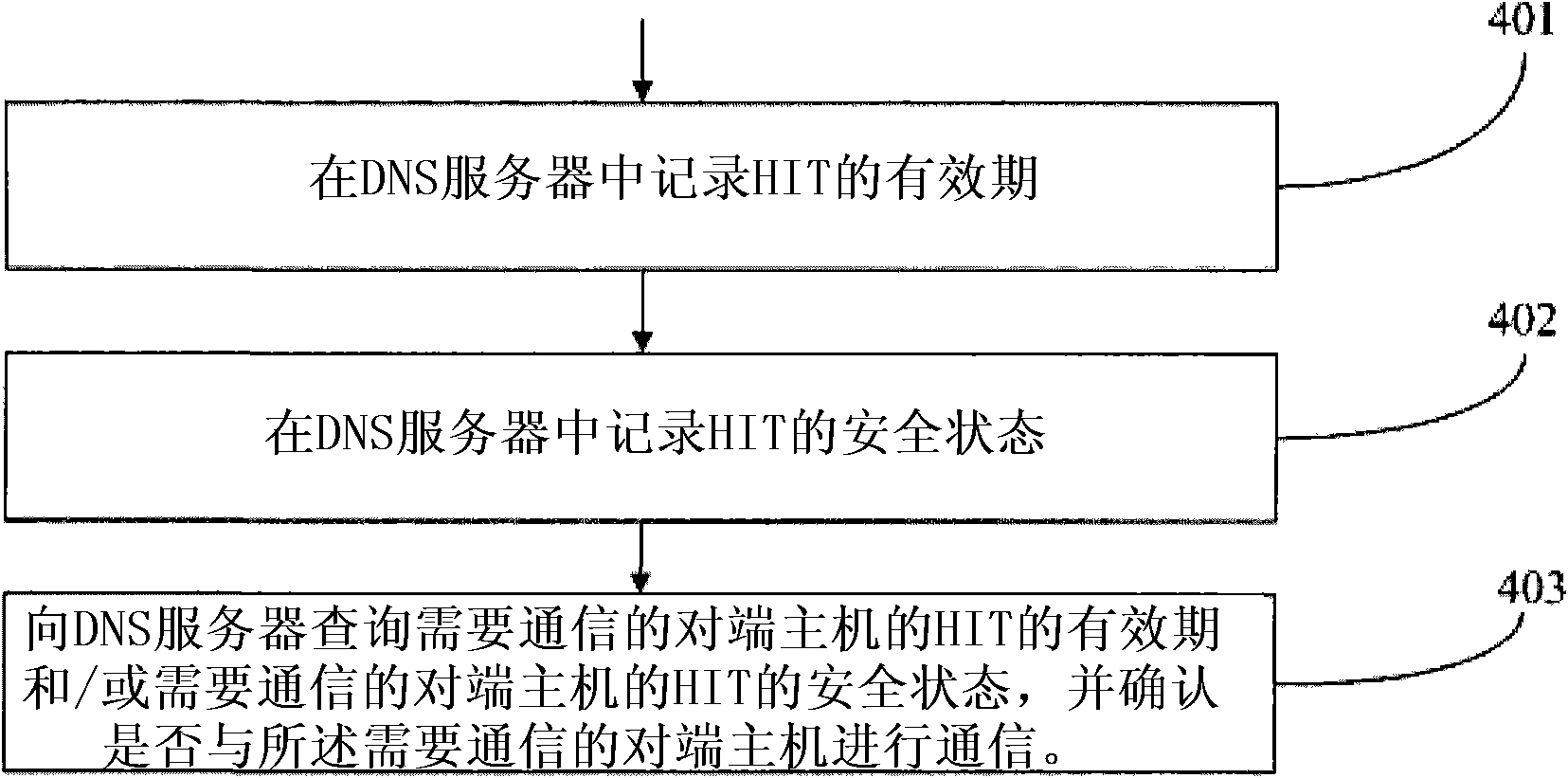
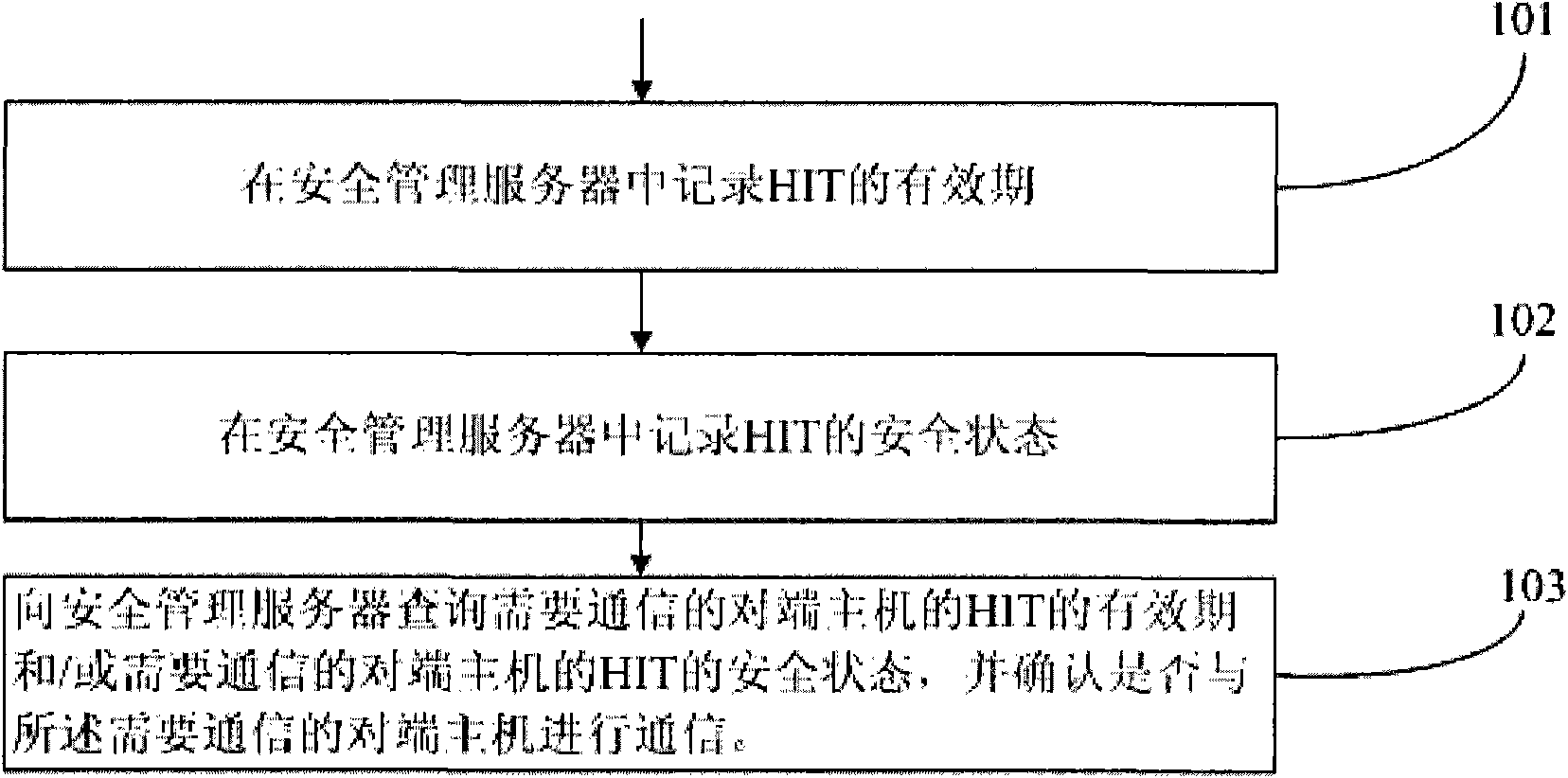
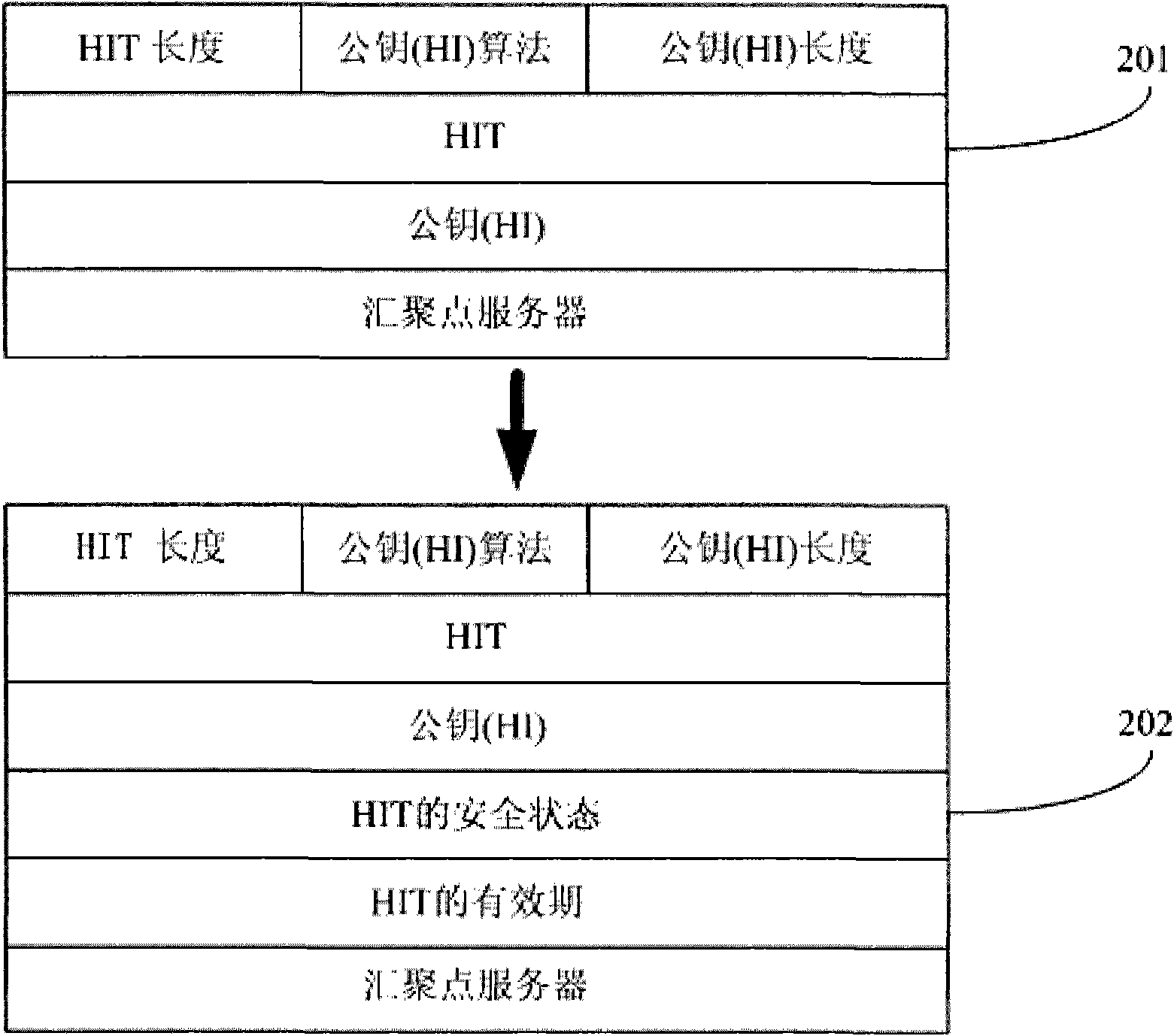
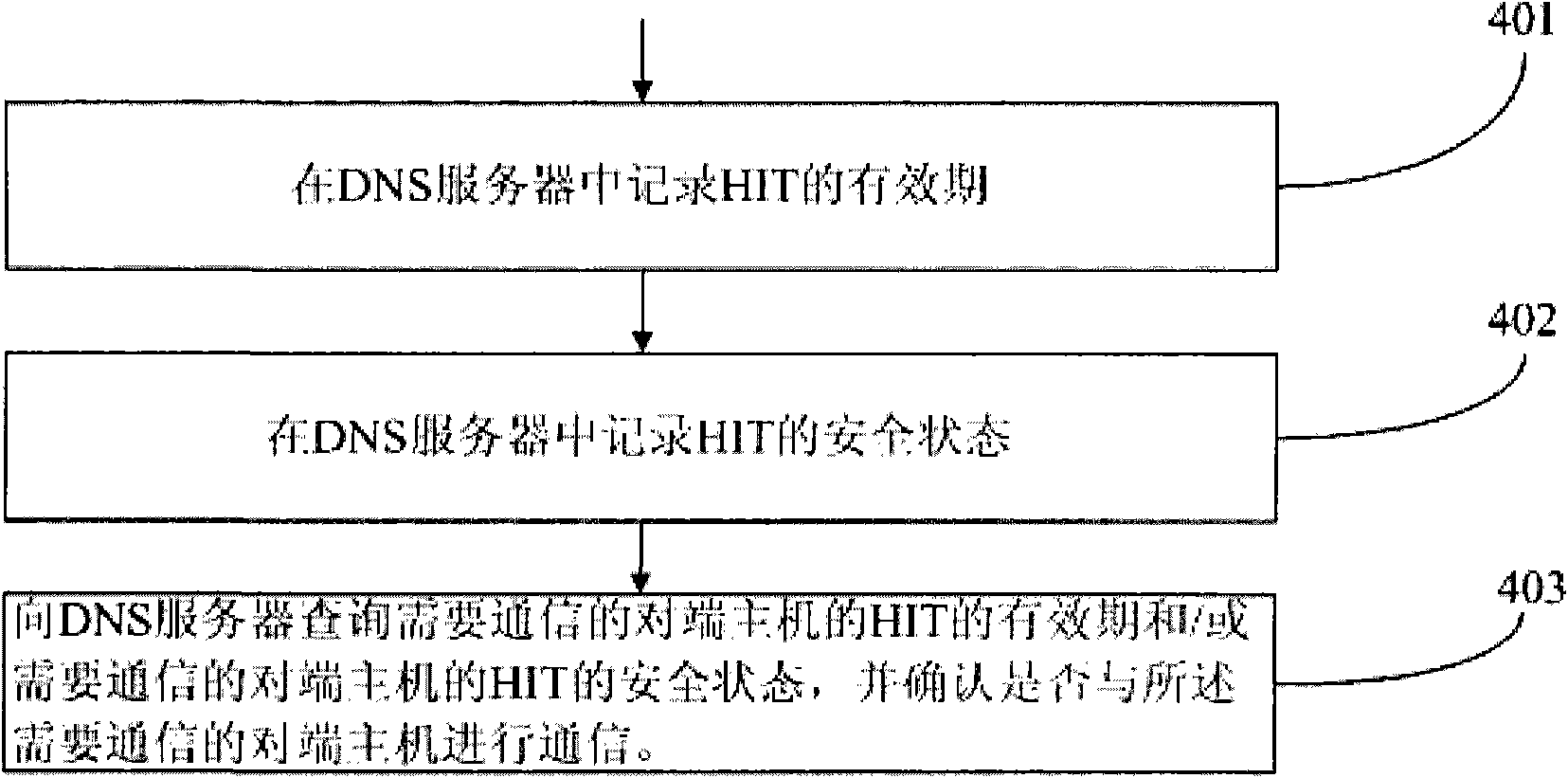
Security assurance method and security management server of host identity tag
The embodiment of the invention provides a security assurance method of a host identity tag (HIT). The method comprises the following steps of: recording a valid period and / or a security state of the HIT in a security management server; when communication is needed, inquiring the valid period and / or the security state of the HIT of a peer end host needing the communication from the security management server; and determining whether to communicate with a host according to the valid period and / or the security state of the HIT of the host. The invention also provides the security management server, which comprises a record unit used for recording the valid period and / or the security state of the HIT and an inquiry unit used for providing inquiry into the valid period and / or the security state of the HIT for the peer end host needing the communication. The security assurance method and the security management server can avoid that the HIT is stilled used when the safety is reduced and provide a security assurance for the HIT of a host identity protocol.
Owner:HUAWEI TECH CO LTD
Method and system for HAP (Host Access Point) switching
ActiveCN102457510AImprove experienceReduce data sendingNetwork topologiesWireless network protocolsIp addressHost Identity Protocol
The invention discloses a method and system for host access point (HAP) switching of a host identification protocol. The method comprises the following steps that: when an IP (Internet Protocol) address of host identification protocol (HIP) equipment is changed, the HIP equipment determines whether to switch HAP based on acquired smaller HAP information of RTT (round trip time) or the original HAP of the HIP equipment determines whether to switch the HAP according to acquired HAP information with smaller RTT between the HAP and the HIP equipment; when the HAP switching is determined to be executed, an HIP association is established between the HIP equipment and the HAP and the association between the HIP equipment with the original HAP is closed; and the original HAP transmits data of the HIP equipment to the new HAP. With the adoption of the method and the system provided by the invention, the problem that a time delay of the interaction between UE (User Equipment) and the HIP equipment is longer is solved, wherein the problem is caused by that the RTT between the UE and the HAP is increased after the UE is moved.
Owner:ZTE CORP
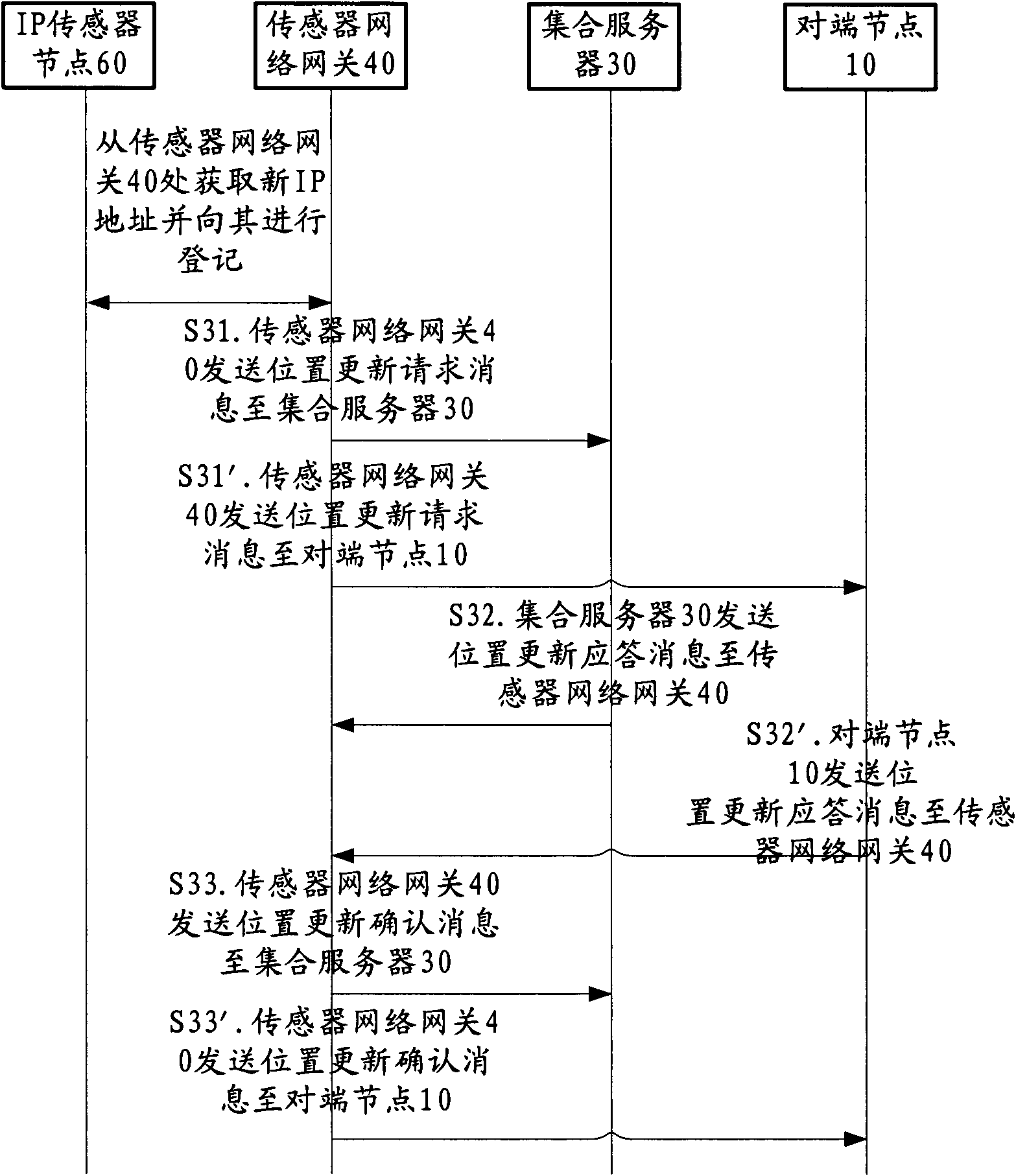
Method and device for performing mobility management on sensor network by using HIP (host identity protocol)
The invention provides a scheme for performing mobility management on a sensor network by using a host identity protocol. According to the technical scheme provided by the invention, signaling overhead, handover delay and data packet dropout can be reduced, and the cost of data packet headers can be avoided. In addition, the mobility management scheme based on the host identity protocol, provided by the invention, further has the advantages of providing safety protection for a mobile sensor network, supporting power-limiting sensor nodes, being easy to configure and the like.
Owner:ALCATEL LUCENT SHANGHAI BELL CO LTD
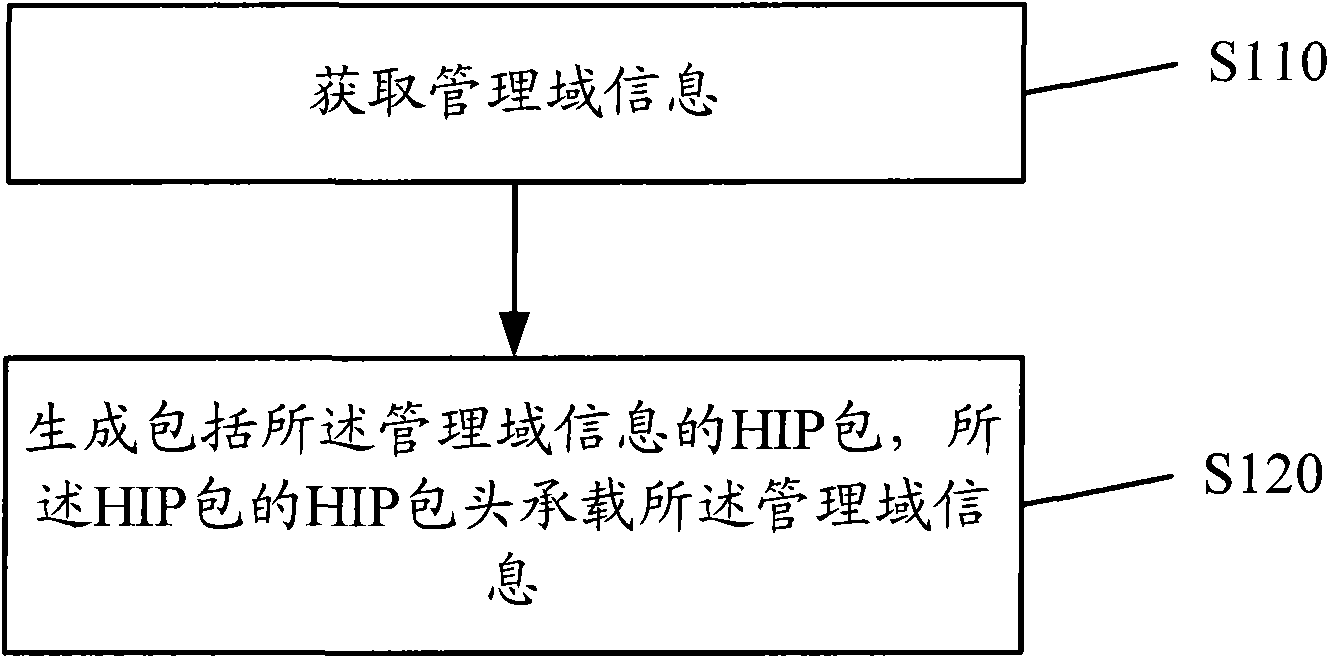
Method and device for generating host identity protocol package
InactiveCN101888372AAchieve global uniquenessEasy distribution managementTransmissionAdministrative domainSoftware engineering
The embodiment of the invention discloses a method and a device for generating a host identity protocol package. The method of the embodiment of the invention comprises the following steps: acquiring management domain information and generating an HIP package including the management domain information, wherein the HIP package head of the HIP package loads the management domain information. The communication device of the embodiment of the invention comprises an acquiring module for acquiring the management domain information and a generating module for generating the HIP package including the management domain information, wherein the HIP package head of the HIP package loads the management domain information. In the method and the device of the embodiment of the invention, the HIP package head loads the management domain information, so that the global uniqueness of a host identify mark can be realized and allocation management and search of the host identify mark are facilitated, and the management domain information and the host identify mark are separately indicated, so the protection of the privacy of the host identify mark can be enhanced.
Owner:HUAWEI TECH CO LTD
Data transmission method and data transmission system based on HIP devices
The invention discloses a data transmission method based on HIP (Host Identity Protocol) devices, when a source HIP device needs to send data to a target HIP device, a HAP (HIP device Access Point) associated with the source HIP device is selected for data sending. The invention further discloses a data transmission system based on the HIP devices, correspondingly. With the method and the system, when a certain HAP is failed, the HIP device associated with the failed HAP can choose other associated HAP for sending data, and the data sent to the HIP device also can be forwarded by other HAP associated with the HIP device, so that time delay of data sending of the HIP device caused by failure of a certain HAP is reduced, and data loss is avoided.
Owner:ZTE CORP
A method and system for hap switching
ActiveCN102457510BImprove experienceReduce latencyNetwork topologiesTransmissionIp addressHost Identity Protocol
The invention discloses a method and system for switching a Host Identification Protocol (HAP) device access point (HAP). The method includes: when the IP address of a Host Identification Protocol (HIP) device changes, the HIP device uses the obtained packet round-trip time ( The HAP information with smaller RTT) determines whether to switch HAP, or the original HAP of the HIP device determines whether the HIP device performs HAP switching based on the obtained HAP information with smaller RTT with the HIP device; when deciding to perform HAP switching , the HIP device establishes a HIP association with the new HAP and closes the association with the original HAP; and the original HAP forwards the data sent to the HIP device to the new HAP. Through the present invention, the problem of long interaction time delay between the UE and the HIP device caused by the RTT between the UE and the HAP changing from small to large after the UE moves is solved.
Owner:ZTE CORP
A method of providing hip-based mobility services to hip nodes
A method of configuring a plurality of rendezvous servers to provide a Host Identity Protocol, HIP, based mobility service to HIP nodes, where the servers are arranged in a hierarchical branching structure. For each HIP node, a Host Identity Tag, HIT, and contact address mapping is registered with a rendezvous server. That server then identifies itself and the HIT to each higher level server within the same branch, without explicitly identifying the contact address to those higher level servers wherein, in use, when a first rendezvous server receives a HIP contact message addressed to a given HIT, if that first server is unaware of the destination HIT, it forwards the message to a higher level server within the same branch and if the first server is not the server at which the HIT is registered but is aware of the HIT, it forwards the contact message to the neighbouring rendezvous server corresponding to the HIT.
Owner:OPTIS WIRELESS TECH LLC
Secure multi-party network communication platform and construction method and communication method thereof
InactiveCN101997875BImprove communication efficiencyImprove communication securityTransmissionOperational systemOpen source
The invention relates to a secure multi-party network communication platform and a construction method and a communication method thereof, and belongs to the fields of distributed systems and computer networks. The multi-party communication platform consists of a management node and a group of host nodes needing intercommunication; by Internet connection, the multi-party communication platform can realize secure and efficient multi-party communication and provide a secure channel for network application software deployed on the communication nodes; the security of the communication layer is realized by using a host identification protocol, and authentication security is realized by using a public key / secret key system on management; the protocol is realized by an open source and supports multiple common operating systems, so the cost of the scheme is very low; centralized member management adopted by the method is flexible and convenient; different from multi-hop forwarding and layer-upon-layer encryption of an onion router protocol, the data of a host marking protocol are finished in one hop between double communication parties and encrypted at one time, so the efficiency is greatly improved, and the data are totally transparent for upper application.
Owner:PEKING UNIV
communication method, system and device based on hip
Disclosed is a method and system of communication based on HIP, and HIP device and HIP access point, wherein the method is based on the Host Identity Protocol (HIP) device and the HIP access point (HAP). The method comprises: the HIP device establishes connection with HAP; source HIP device sends data package to source HAP via HIP connection; and the source HAP receives the data package and forwarding the data package based on HIP connection relationship or IP address of the destination device. The present invention can improve user experience by reducing HIP connection required and time delay by the HIP device.
Owner:苏州医疗器械产业发展集团有限公司
Registration and authentication method and system based on HIP (host identity protocol)
ActiveCN102123391BSave resourcesSave reasonable expensesTransmissionSecurity arrangementTelecommunications networkIp address
The invention provides a registration and authentication method and system based on HIP (host identity protocol). User equipment is accessed into a distributed telecommunication service platform based on HIP by an HIP node, and an authentication method in a telecommunication network is adopted to authenticate the user equipment; and after the user equipment passes authentication, association information between a user identification of the user equipment and the HIP node and association information between the user identification of the user equipment and the current IP (internet protocol) address of the user equipment are stored in the HIP node. The invention provides a service platform with unified user management, transparent support mobility and multi-cavity performance, and new service income is acquired; and in addition, due to use of the original authentication system of the communication network, the resources of the network and the terminal are saved, the investment is reduced, and the reasonable overhead of mobile equipment and the network is guaranteed. Simultaneously, an application provider does not need to carry out investment construction of user management, support mobility and multi-cavity performance so as to save the capital expenditure, therefore, the win-win situation of the application provider and a network operator is achieved.
Owner:ZTE CORP
HIP (Host Identity Protocol) based method and system for achieving user mobility
InactiveCN101931611BSupport mobilityWireless network protocolsTransmissionHost Identity ProtocolComputer science
The invention relates to a HIP (Host Identity Protocol) based method for realizing user mobility, comprising the following steps of: a registration step: the host equipment initiates a registration process to a set server, and the set server stores the mapping relation between user identification of a host equipment user and the host identification and the location identification of the host equipment; and a connection establishment step: the host equipment queries the set server according to the user identification of an opposite end user and establishes connection with the host equipment of the opposite end user by adopting the HIP according to a query result. The HIP based method and system for realizing the user mobility can realize the mobility taking the user as a centre.
Owner:ZTE CORP
An encrypted tunnel communication method based on hip protocol
ActiveCN108234497BHigh degree of security and confidentialityTransmissionTelecommunicationsConfidentiality
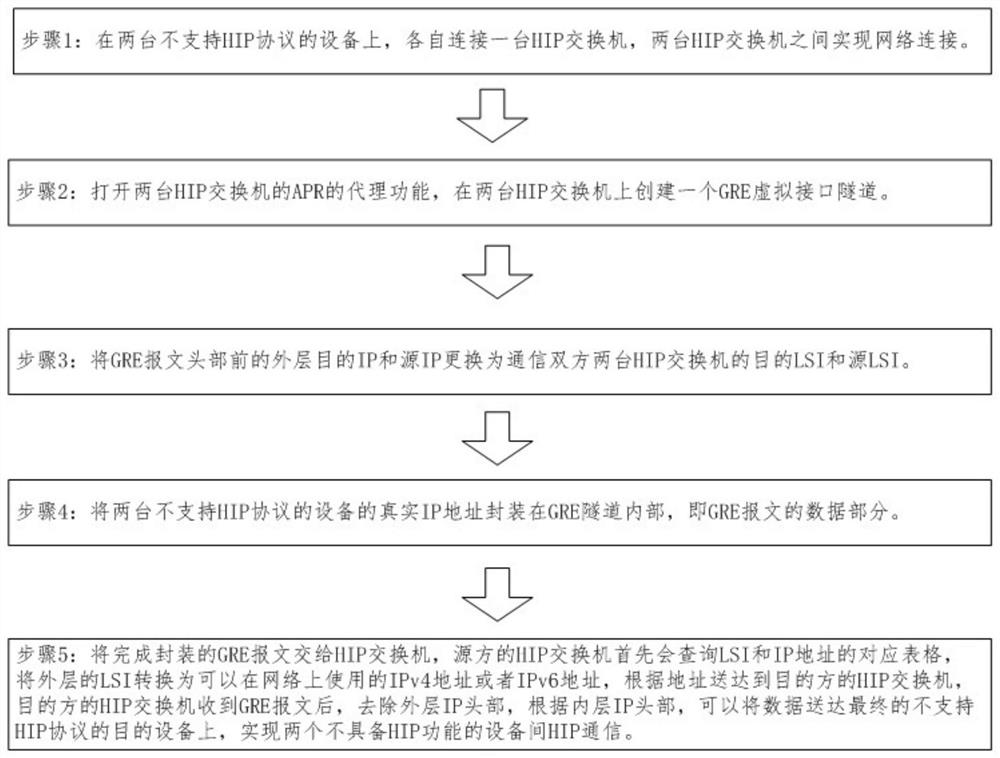
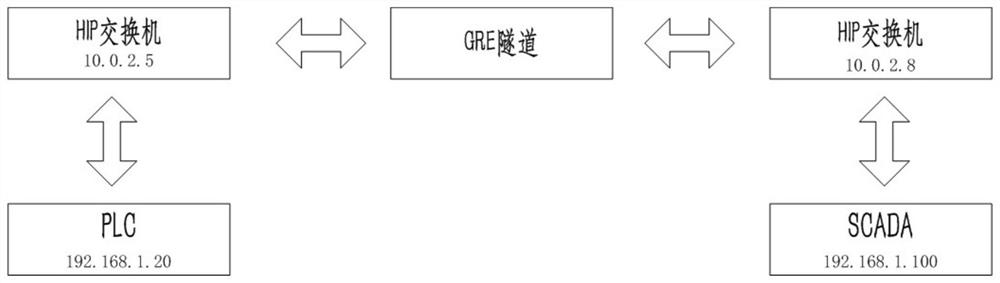
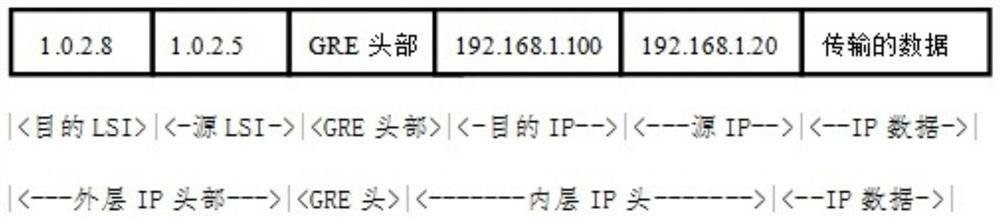
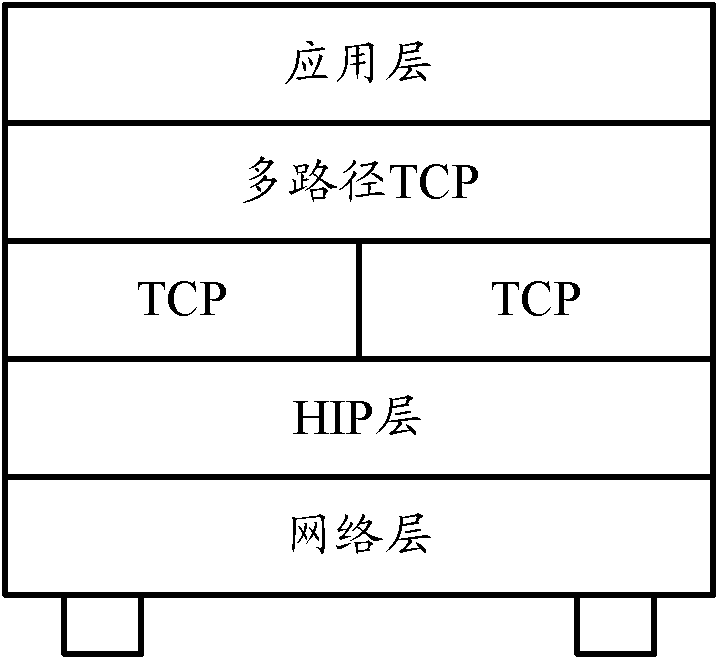
The invention provides an encrypted tunnel communication method based on a host identity protocol (HIP). Two pieces of equipment not supporting the HIP are separately connected with an HIP switch, andthe two HIP switches are connected via a network; agent functions of APR of the two HIP switches are opened, and a GRW virtual interface tunnel is built on the two HIP switches. According to the encrypted tunnel communication method based on the HIP provided by the invention, matched with the HIP switches and the GRE virtual interface tunnel technologies, the HIP communication can be achieved between the equipment without HIP functions, mobile interconnection networking between the equipment without mobile interconnection functions and mutual networking between the different networks are achieved, and the characteristics of wide application range and high security and confidentiality degree are provided.
Owner:宝牧科技(天津)有限公司
Connection establishment method, device and communication system
ActiveCN102714617BImprove utilization efficiencyData switching networksCommunications systemHost Identity Protocol
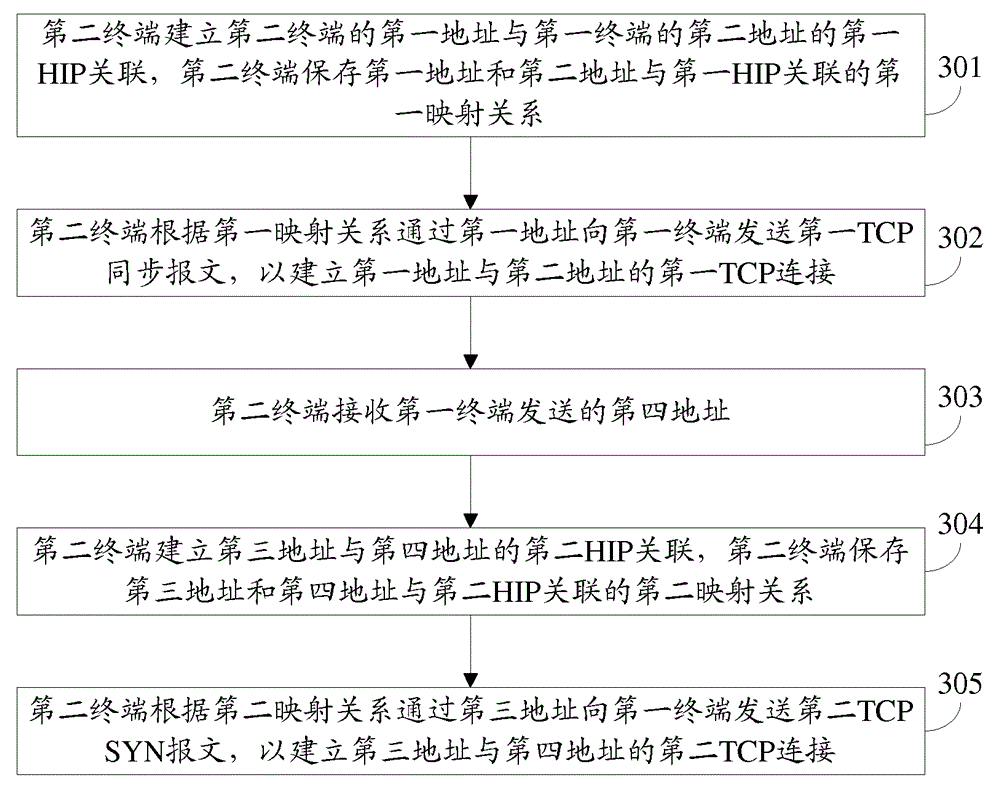
A method for establishing a connection includes: after establishing a first host identity protocol(HIP) association between a first address of a second terminal and a second address of a first terminal, the second terminal saves a first mapping relation among the first address, the second address and the first HIP association; a first transmission control protocol(TCP) connection between the first address and the second address is established, and a first TCP SYN message includes connection identity(CID) information; the second terminal establishes a second HIP association between a third address and a forth address of the second terminal, and saves a second mapping relation among the third address, the forth address and the second HIP association; a second TCP connection between the third address and the forth address is established, and a second TCP SYN message includes CID information which is the same with that of the first TCP SYN message. An apparatus for establishing a connection and a communication system corresponding to the method for establishing a connection are also provided. The multi-access of the terminal in the HIP network can be realized.
Owner:HUAWEI TECH CO LTD
Method and device for mobility management of sensor network using hip
The invention provides a scheme for performing mobility management on a sensor network by using a host identity protocol. According to the technical scheme provided by the invention, signaling overhead, handover delay and data packet dropout can be reduced, and the cost of data packet headers can be avoided. In addition, the mobility management scheme based on the host identity protocol, provided by the invention, further has the advantages of providing safety protection for a mobile sensor network, supporting power-limiting sensor nodes, being easy to configure and the like.
Owner:ALCATEL LUCENT SHANGHAI BELL CO LTD
Security assurance method and security management server of host identity tag
A Host Identity Tag (HIT) security ensuring method is provided, which includes: recording validity periods of HITs and / or security states of HITs in a security management server; when a communication is required, querying the security management server for a validity period of a HIT of an opposite end host required to be communicated with and / or a security state of the HIT of the opposite end host required to be communicated with; and determining, according to the validity period of the HIT of the host and / or the security state of the HIT of the host, whether to communicate with the host. A security management server is also provided, which includes: a recording unit, configured to record validity periods of HITs and / or security states of HITs; and a querying unit, configured to provide a query for a validity period of a HIT of an opposite end host required to be communicated with and / or a security state of the HIT of the opposite end host. Through the method and the server, it is avoided that the HIT is still used when its security declines, thereby providing security ensuring for the HIT of a Host Identity Protocol.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com