P2P network SIP realizing method based on host machine mark protocol
A host identification protocol and implementation method technology, applied in the direction of electrical components, transmission systems, etc., can solve the problem of inconvenient and flexible central control servers that do not belong to the same network, client/server mode, etc., and achieve complex and widely mobile devices Sexual support and the effect of improving message utilization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
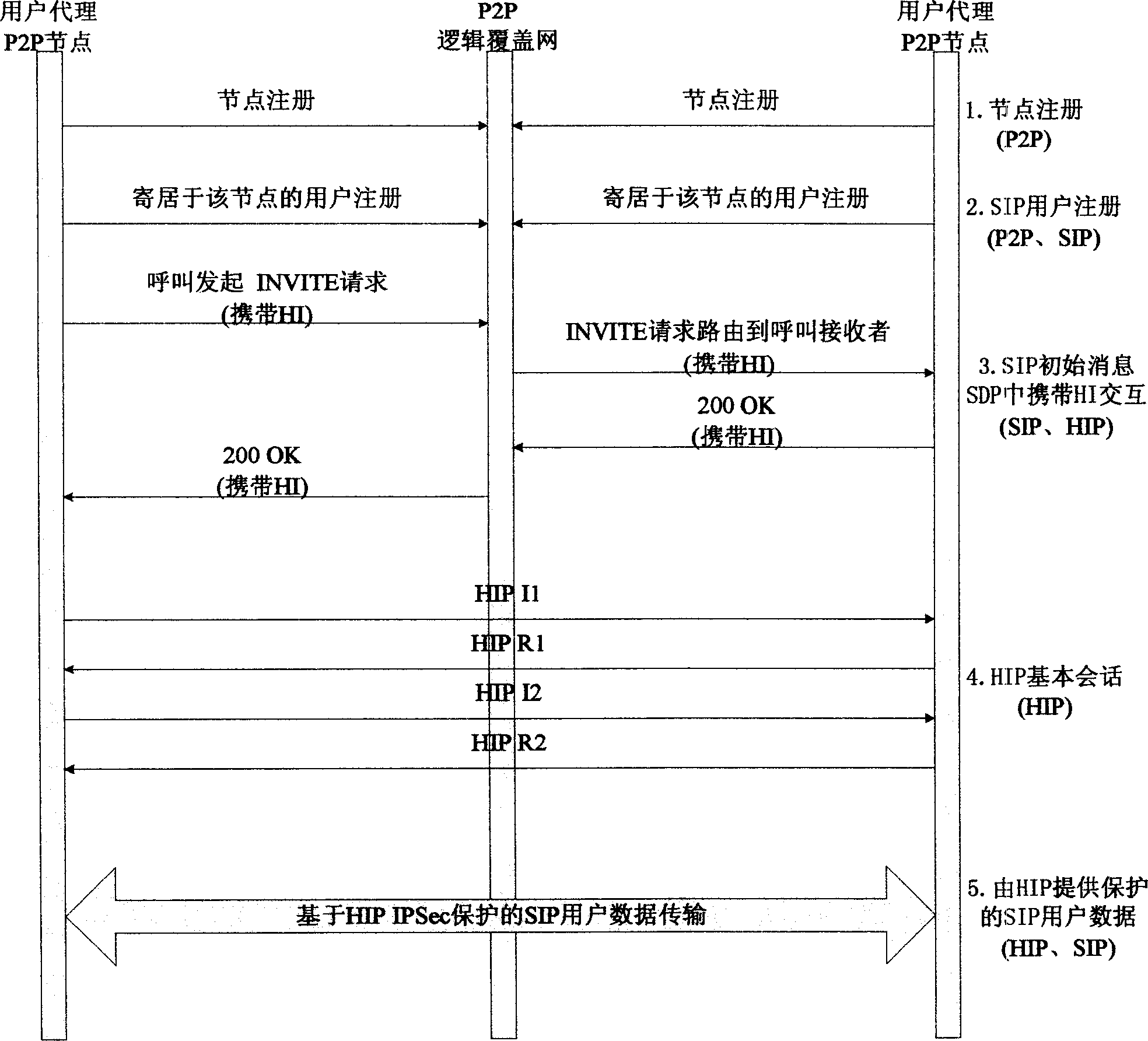
[0050] Embodiment 1, SIP implementation under the P2P environment:
[0051] In the P2P network environment, the process of SIP user information maintenance, SIP user location and SIP session establishment is as follows:
[0052] Step 1: Start the P2P participant node registration process. First, its IP address and port number are hashed to generate a node identification number.
[0053] Step 2: Send a registration message to the existing registration management node in the logical overlay network, requesting to join the logical overlay network.
[0054] Step 3: The registration management node searches for the node that it knows is closest to the node identification number of the node to be joined, replies to the node to be joined with a 302 message, and redirects its query target to this closer node.
[0055] Step 4: The node to be joined repeats the above process until a node including the node to be joined in the maintained name space is found, which is called the managem...
Embodiment 2
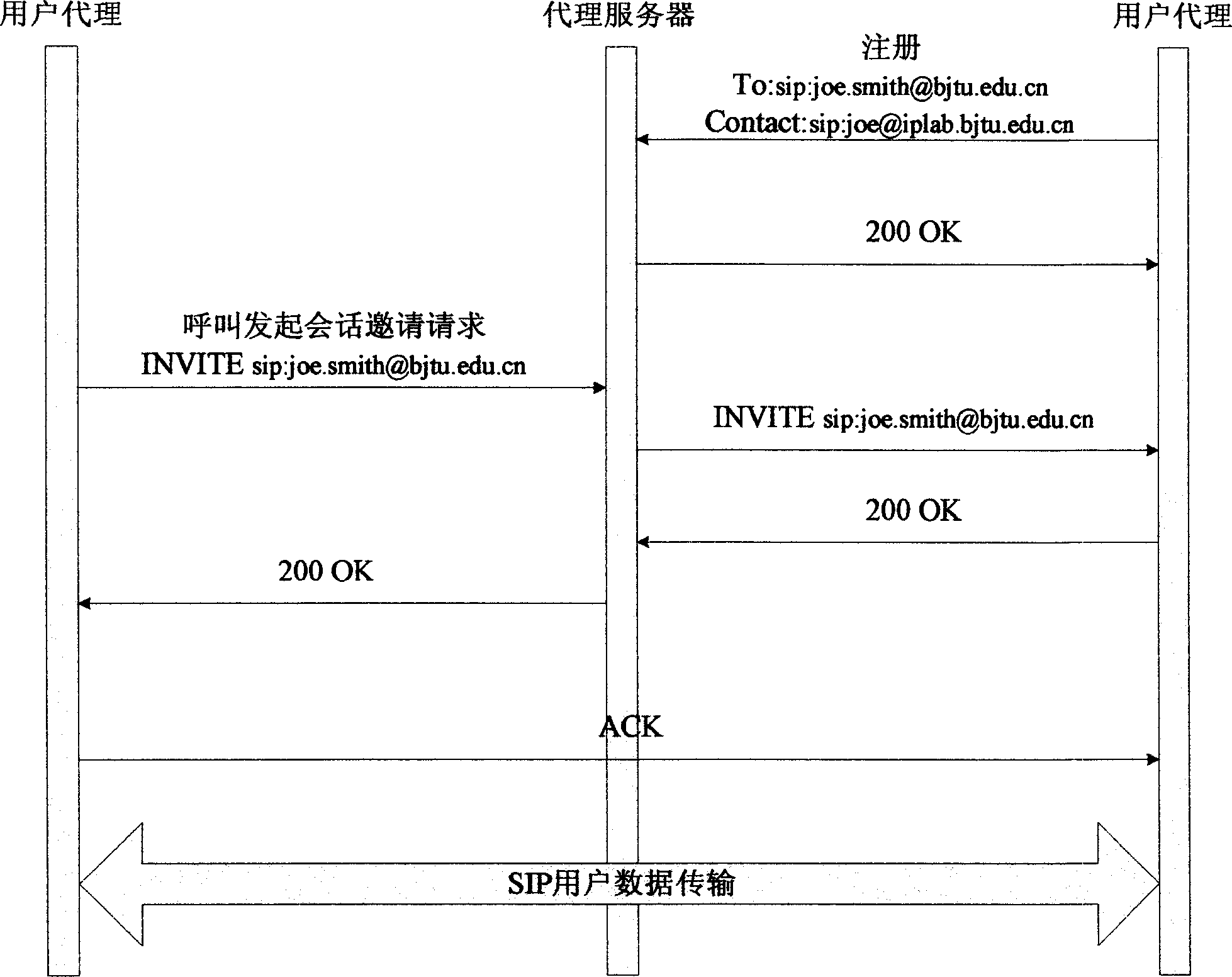
[0067] Step 16: After the caller resends the message to that node, the call is established in the form of traditional SIP. Embodiment 2, the binding realization of SIP and HIP:
[0068] In order to perform a basic HIP exchange, a given host needs to know the IP address and HIT of the remote host. In the bundled implementation of SIP and HIP, the IP address can be obtained through the Contact header in the SIP message, but HIT cannot be obtained directly.
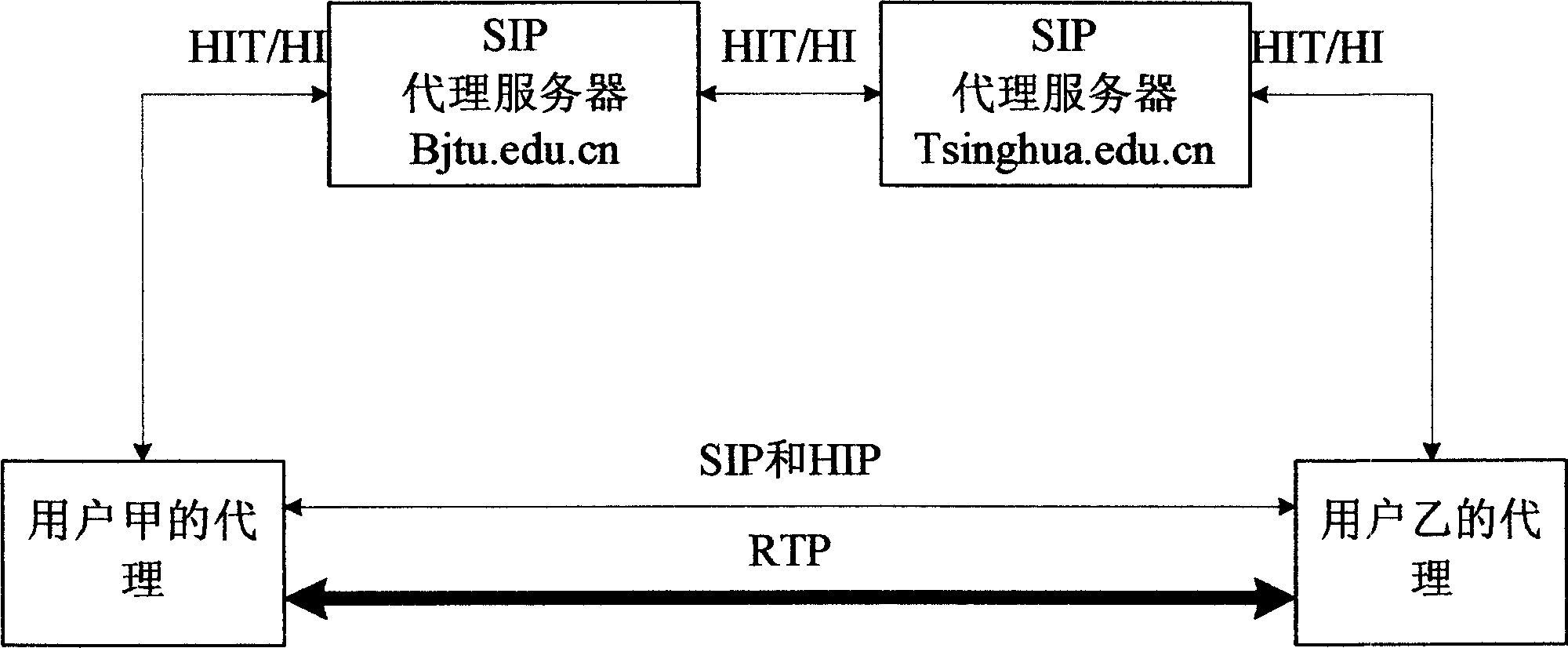
[0069] How to securely obtain HI is very important. Traditional HIP is implemented through DNS or DHT (Distributed Hash Table) used in P2P networks.
[0070] This embodiment is used to describe how to implement the exchange of the host HIT before basic HIP interaction by extending the SIP message. One item in the SIP packet is the Via header, which is used to record the address of the server that the SIP packet passes through during transmission. Due to the uncertain number of servers passed, there may be multiple Via hea...
Embodiment 3
[0096] Embodiment 3: The overall message flow that the peer-to-peer network SIP based on HIP realizes:
[0097] The following will take a simple network as an example to illustrate the entire application process. Using a 3-bit hash space, the corresponding namespace scale is 2 3 =8, the size of the query pointing table item is 3, and the value range of the node identification number and the resource identification number is 0 to 7. The logical overlay network constructed according to the above data is as follows: Figure 4 As shown, the positions with node identification numbers 1 and 3 have registered participating nodes.
[0098] According to the Chord algorithm, a node is responsible for maintaining resources whose resource identification number is less than or equal to the node identification number (modulo operation). Then node 1 is responsible for resources 4-7 and 0-1; node 3 is responsible for resources 2-3.
[0099] There are 3 items in the query pointing table, e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com